2023-3-12 22:59:21 Author: perception-point.io(查看原文) 阅读量:23 收藏
The security researchers on Perception Point’s IR team have recently observed a new phishing campaign that aims to trick Facebook users into giving scammers their account credentials and Personal Identifiable Information (PII).
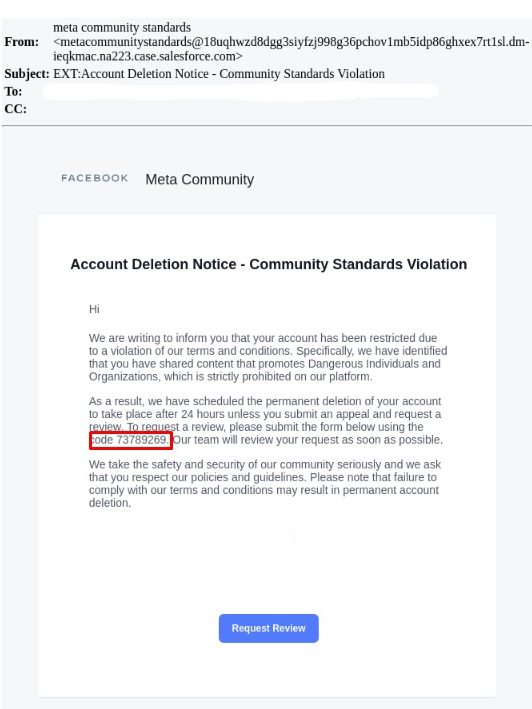
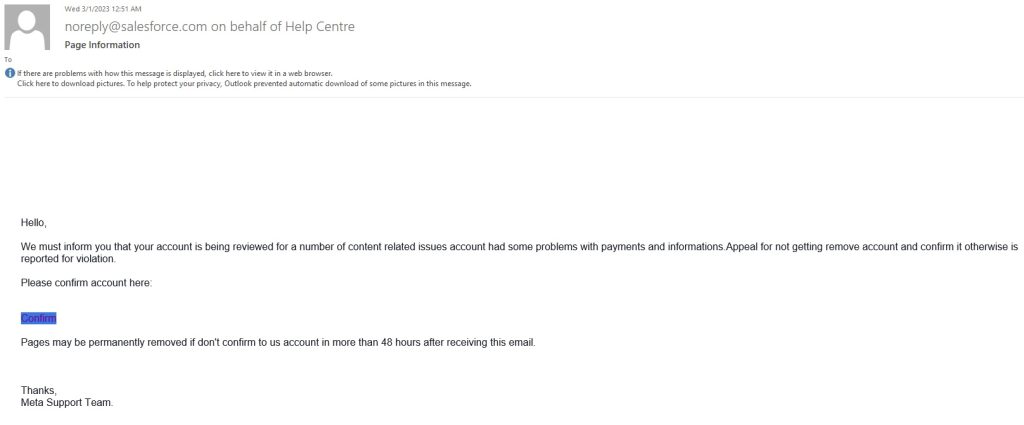
This attack begins when an attacker sends their target a phishing email, with a message impersonating Facebook/Meta. In the body of email, users either receive a supposed “Account Deletion Notice” due to a “violation of the terms and conditions” or they are informed that their account is being reviewed because of an issue with payment or information. The messages claim that the user’s account has been restricted due to the aforementioned reasons and that the account is scheduled for permanent deletion within 24 to 48 hours if the user fails to submit an appeal or a review request.
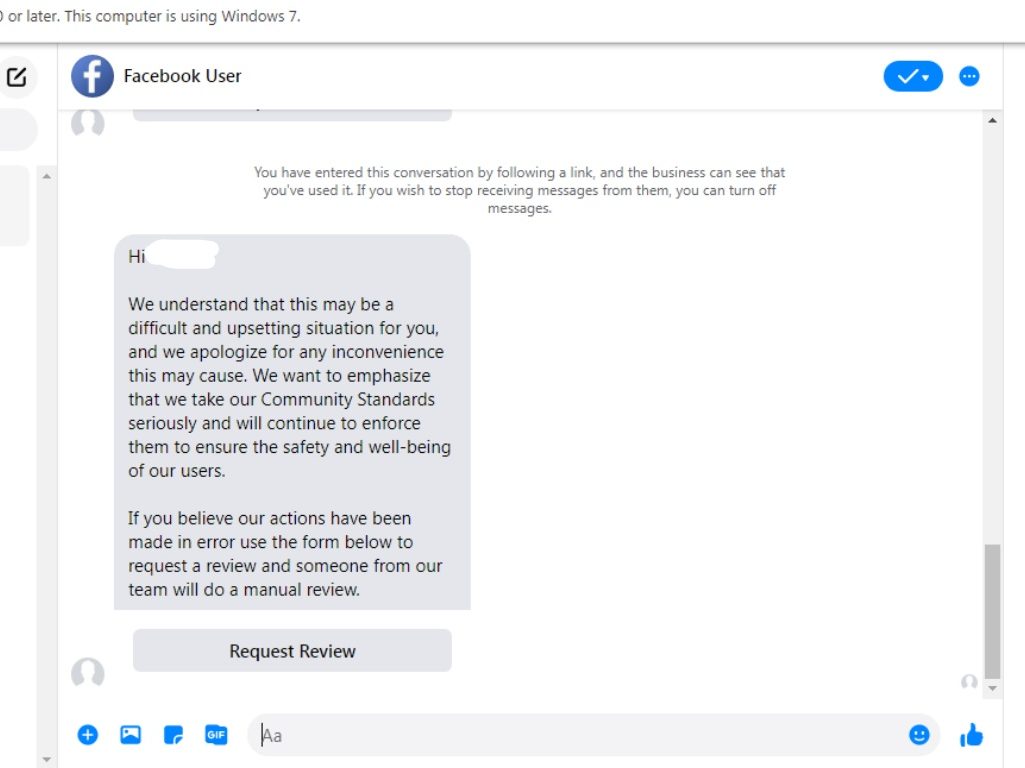
The user is then prompted to click on a button within the email, which redirects them to the Facebook Messenger. A new chat opens up with a bot, appearing to be called “Facebook User” with the Facebook logo as the profile picture. Once the user clicks on the “Get Started” button, they receive an automatic response, inviting them to request review for their account deletion.
Another variation of this attack flow is that from the email, the user is redirected to a Facebook post, impersonating Facebook’s “Restriction Centre” with a link to submit an appeal. At first glance, the page seems legitimate, however the link provided leads to an external domain.
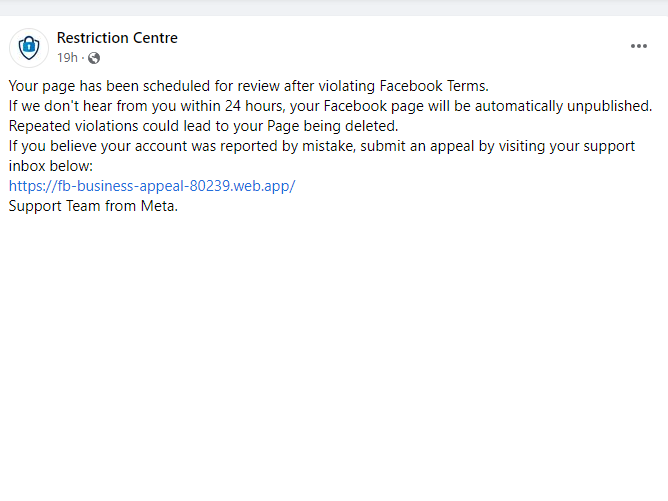
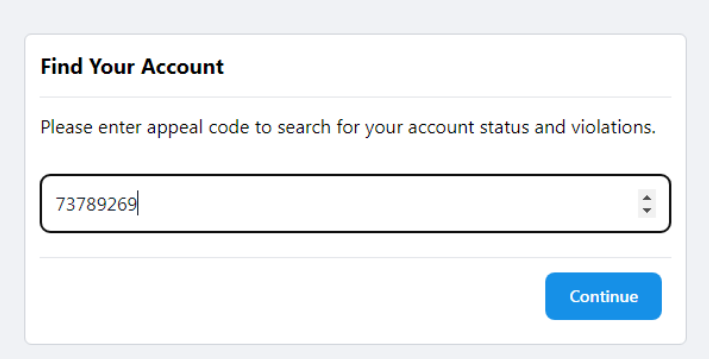
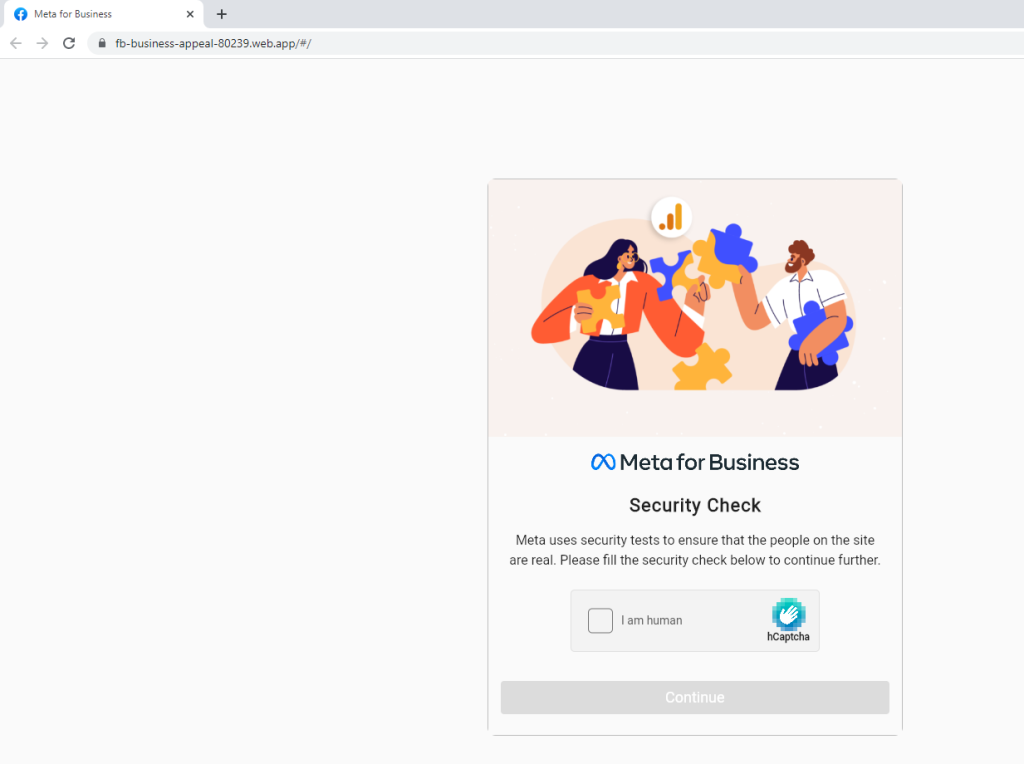
Once the user clicks on the link to submit an appeal, they are redirected again to a site that no longer contains a domain associated with Facebook, Meta, or Messenger. Rather, the new domain is suspicious and obfuscated. To convince the user that the site is legitimate, the user is then presented with a verification/security check. Some of these steps contain “I am human” CAPTCHA-like buttons, while others require the user to enter an appeal code that was included in the initial email.
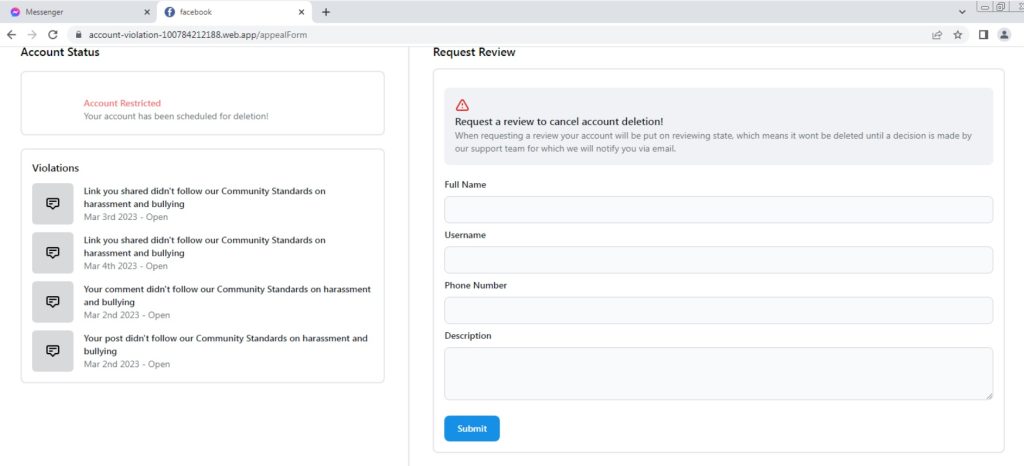
Next, the user is redirected to a page containing a form, asking for the user’s personal information that must be reviewed by Facebook. These phishing sites are made to appear like Facebook’s actual copyright appeal page, containing a form where victims are prompted to enter their full name, email address, phone number, and Facebook username.
An important detail to note is that throughout this process, the attackers created their forms in the same manner that regular developers would. User input validations and error messages are made to reduce the chances of victims recognizing the scam and increase the attack’s credibility.
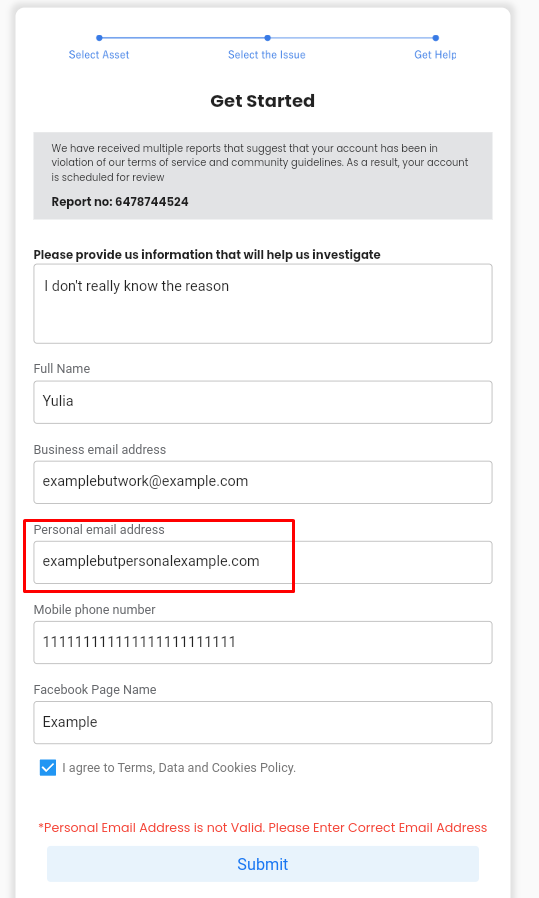
After the user has completed and submitted the form, a pop-up window appears, requesting the user’s Facebook account password as a necessary step in the submission process. As previously mentioned, attackers aim to make their attacks as convincing as possible, which may involve the inclusion of additional, but fake validation and verification steps to further deceive their targets.
For example, one tactic involves displaying an error message that suggests the user has entered their password incorrectly. Another tactic displays a landing page that appears to show that a process is being carried out, even though nothing is actually happening. The most concerning ploy, however, is when the attackers use a fake two-factor authentication process that involves using the user’s actual phone number that they had entered in the form. This tactic is especially dangerous because it can give the attackers access to sensitive information or allow them to take over the user’s account completely.
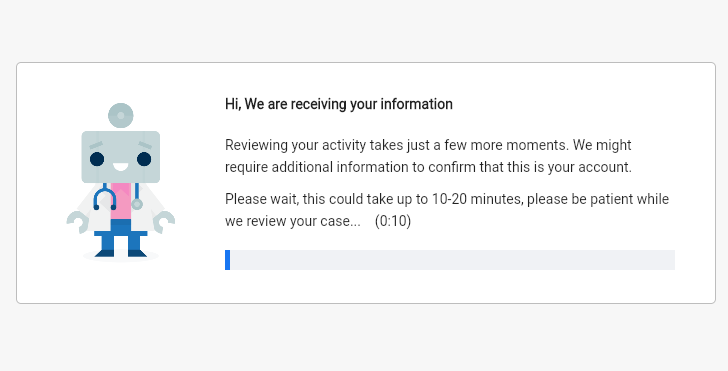
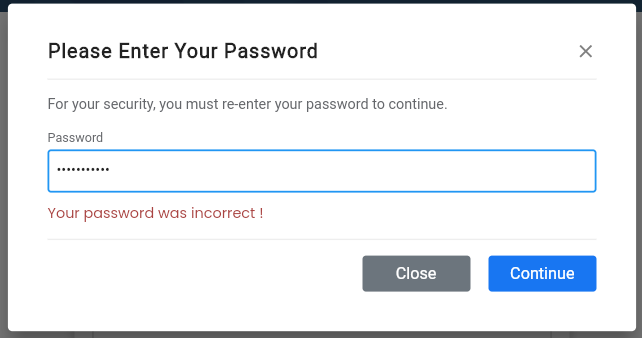
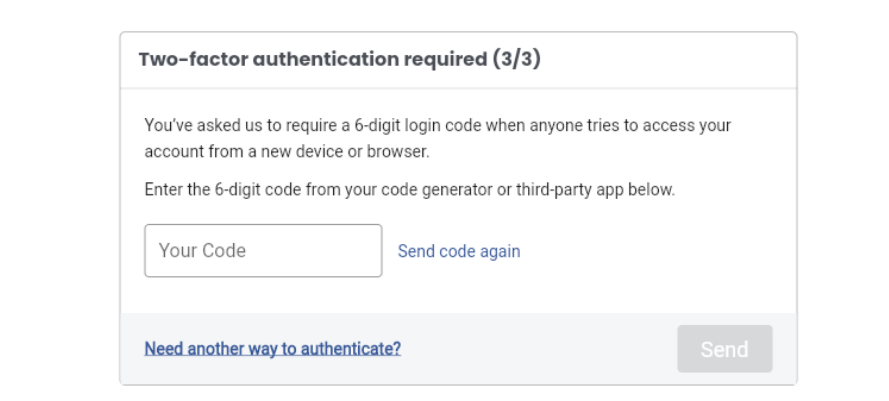
Once the user enters their password, the attacker will receive it along with the other information that the user included in the form submission. In some cases, attackers will conclude their attack by redirecting the user to a legitimate Facebook Help Center page, which can further enhance the illusion that the entire process was genuine and trustworthy from the beginning.
Equipped with all this new data, the attack can then take over the user’s account, potentially causing a range of negative consequences, such as stealing personal or financial information, making fraudulent purchases or transactions, spreading malware or ransomware, and damaging the user’s online reputation. This attack is just one example of why it is so imperative to be cautious when entering your login credentials online.
For more information on how you can protect your organization from phishing attacks like these, check out this blog.
如有侵权请联系:admin#unsafe.sh