Welcome to Pwn2Own Vancouver 2023! We’ll be updating this blog in real time as results become available. We have eight attempts for today, including a SharePoint RCE and a Tesla exploit. We’re excited to say that all unique winning entries will receive the full payout during this year’s contest. We’ll update this blog throughout the day with results as they come in.
All results current as of 1200 Pacific (GMT -7)
SUCCESS - AbdulAziz Hariri (@abdhariri) of Haboob SA (@HaboobSa) completed his attack against Adobe Reader using a 6-bug logic chain exploiting multiple failed patches which escaped the sandbox and bypassed a banned API list. He earns $50,000 and 5 Master of Pwn points.

FAILURE - last_minute_pwnie was unable to get their Ubuntu exploit working within the time allotted.
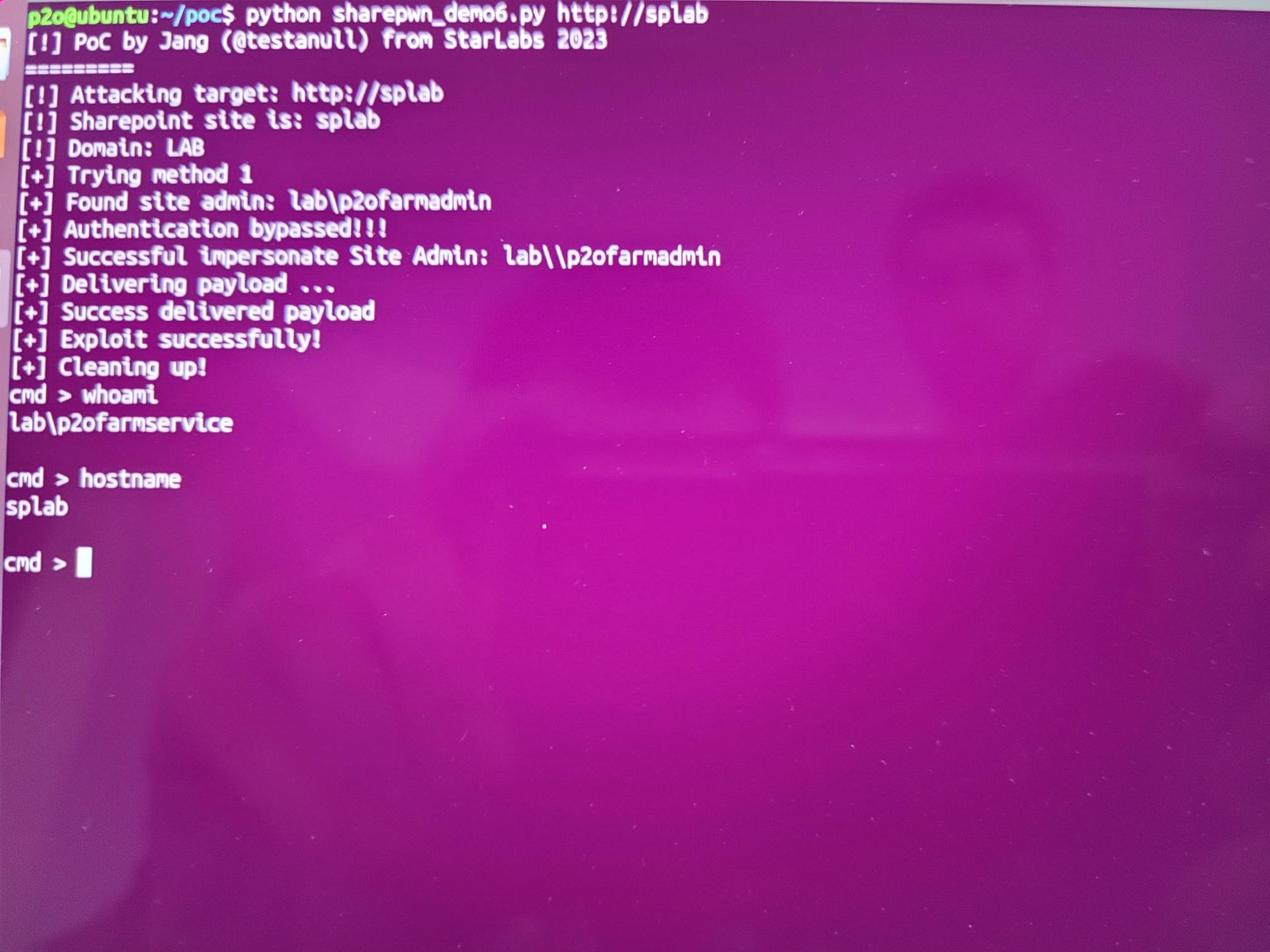
SUCCESS - STAR Labs was able to execute a 2-bug chain against Microsoft SharePoint. They earn $100,000 and 10 Master of Pwn points.
如有侵权请联系:admin#unsafe.sh