On March 22nd, 2023 a critical vulnerability was discovered within the WooCommerce Payments plugin – an extremely popular eCommerce payment plugin for WordPress with over half a million active installations. Thankfully the vulnerability was discovered by white hat security researcher Michael Mazzolini and responsibly disclosed through HackerOne, giving websites time to install the patched version 5.6.2 before full details of the exploit are released on April 6th.
Although what we know at this time is limited, what we do know is that the vulnerability allows for unauthenticated administrative takeover of websites. Website administrators using this plugin are advised to issue the patch as soon as possible and check for any suspicious activity within their WordPress websites such as any administrative actions performed from unrecognized IP addresses.
What we know
The vulnerability appears to be within the following file:
./wp-content/plugins/woocommerce-payments/includes/platform-checkout/class-platform-checkout-session.php
According to the plugin change history it appears that the file and its functionality was simply removed altogether:
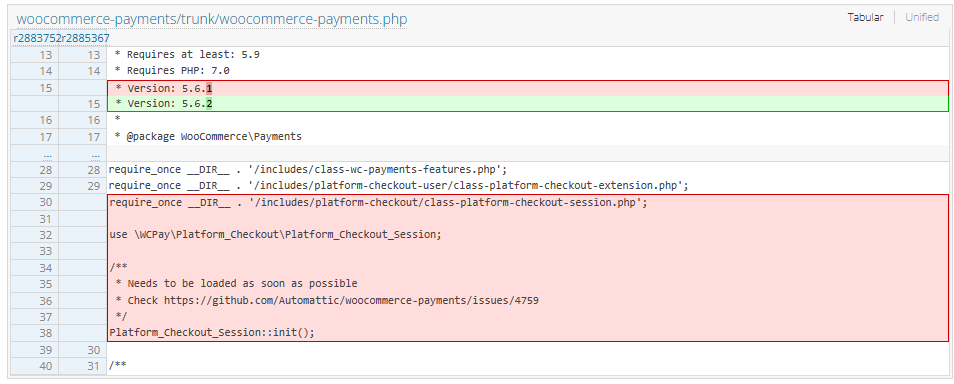
Automattic – the company behind WordPress and WooCommerce – is issuing automatic/forced updates of all websites using this plugin within their wordpress.com websites.
What should I do?
As per the official WooCommerce press release, if you operate a WooCommerce / WordPress website with this plugin you are advised to take the following actions:
- Update woocommerce-payments to version 5.6.2 immediately
- Change all administrator passwords
- Rotate your payment gateway and WooCommerce API keys
It’s unlikely that the passwords themselves were compromised, however if you reuse passwords across multiple websites it would be prudent to get those changed as well just in case. You can also take the additional measure of changing the salts within your wp-config.php file if you want to take extra precautions.
WooCommerce itself is – of course – still safe to use. Unfortunately vulnerabilities like this do pop up from time to time and are a great reminder of why automatic updates are prudent to have enabled.
The WooCommerce security team fortunately has acted very quickly to address this issue, so hats off to them.
