2023-4-4 06:7:35 Author: blog.qualys.com(查看原文) 阅读量:24 收藏
Qualys Blog Series – Threat Research Unit Report
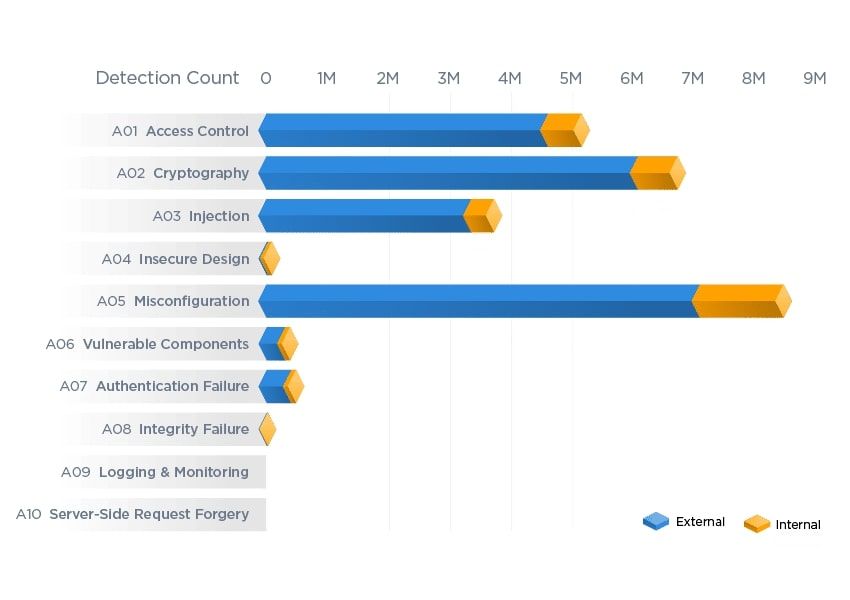
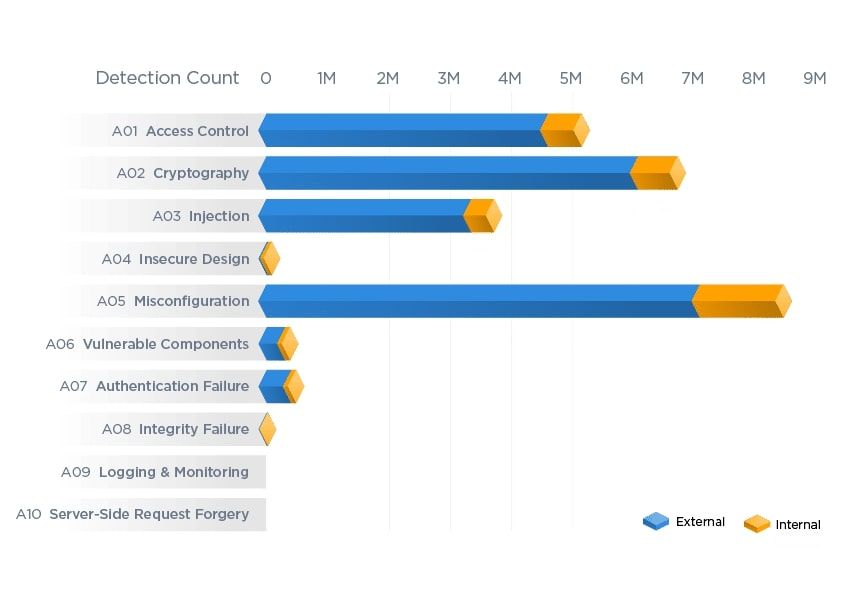
In this last blog of our series describing the top Risk Facts discovered in the 2023 Qualys TruRisk Research Report, we go under the hood to better understand Risk Fact #5: Cloud misconfigurations open the door to ransomware.
Misconfigurations are errors that are unintended actions by an internal party; they make up a large part of weaknesses in web applications and are one of the main reasons for data breaches. We see this, for example, in the regular cadence of news around data leakage because of storage buckets or databases that were mistakenly left accessible without passwords or encryption. So, let’s dive in and explore how the evidence shows users are doing with misconfigurations of controls for AWS, GCP, and Azure.
Previous blog in this series: Misconfigurations Still Prevalent in Web Applications
Gauging Control Misconfigurations on AWS, GCP, and Azure
Misconfigurations profoundly affect the security of an organization’s cloud infrastructure. Findings for Risk Fact #5 begin with how Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure controls are performing against the Center for Internet Security (CIS) benchmarks. These control benchmarks help guide organizations to secure their part of the shared security responsibility model.
Amazon Web Services (AWS)
For example, Amazon S3 cloud data storage buckets have oft-weakened access controls leading to many high-profile breaches. Within the CIS Benchmark, there are four controls measuring security for public access to data in S3 buckets. During 2022, each of these successfully passed 48% of the time they were checked, meaning more than half of S3 buckets were potentially exposed to public access. For two controls, “Ensure that Object-level logging for write events is enabled for S3 bucket” and “Ensure that Object-level logging for read events is enabled for S3 bucket audit read and write events,” benchmark scans passed just 15% of the time. Meanwhile, “Ensure MFA Delete is enabled on S3 buckets” was enabled in less than 1% of the scans.
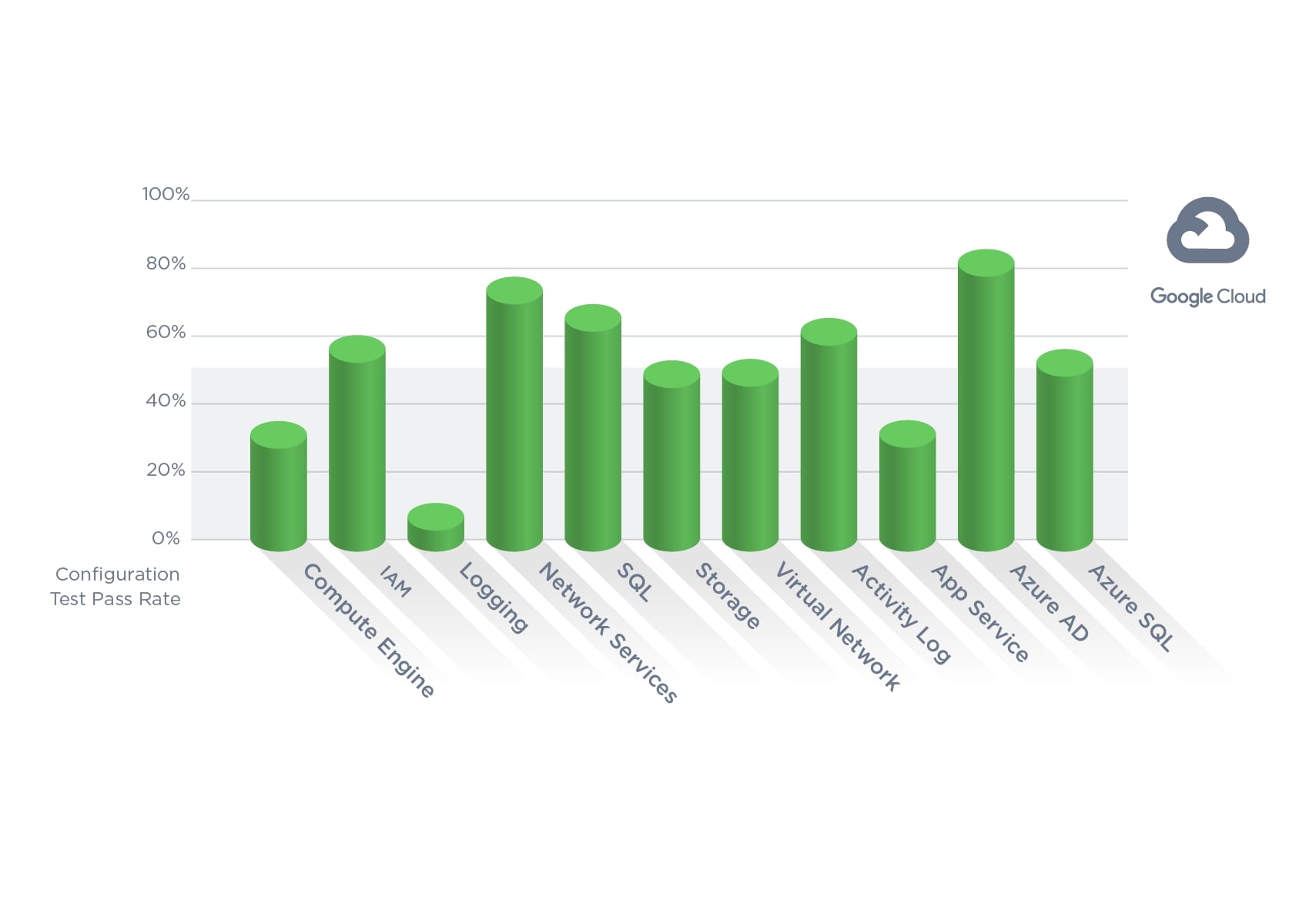
Google Cloud Platform (GCP)
Within GCP, the data show concerns with BigQuery configurations. The large cloud data sets housed in BigQuery are often used for AI/ML model training, which can contain sensitive information that could be exposed like S3’s scenario described above. During 2022, 99% of the checks passed, ensuring that BigQuery datasets are not anonymously or publicly available.
What drives this GCP category down are checks for encryption with a customer-managed key. Scans for two related settings are failing at a staggering rate of more than 99%, both of which are in Google’s Compute Engine/Virtual Machine category. The first is the “Ensure that Compute instances have Confidential Computing enabled” setting, which encrypts data during processing time in addition to the defaults of encrypting data at rest and in transit. In a shared computing model, customers processing highly sensitive data would want to leverage a technology such as this to ensure confidentiality of their data. By default, this is disabled, so it is unclear if users are skeptical about the functionality of the feature or don’t consider this to be a viable attack vector.
The second setting failing more than 99% of its scans is the “Ensure ‘Block Project-wide SSH keys’ enabled for VM instances” setting, which is also disabled by default. This means by default, users can use the same SSH key to log into all instances within a project, which increases the risk of all assets being impacted should a key be stolen. The danger of enabling this is that users may lose access to all their instances, which would have a negative impact to the business. We can see clearly here that there are some misconfigurations that organizations are willing to accept to minimize the impact on the overall business.
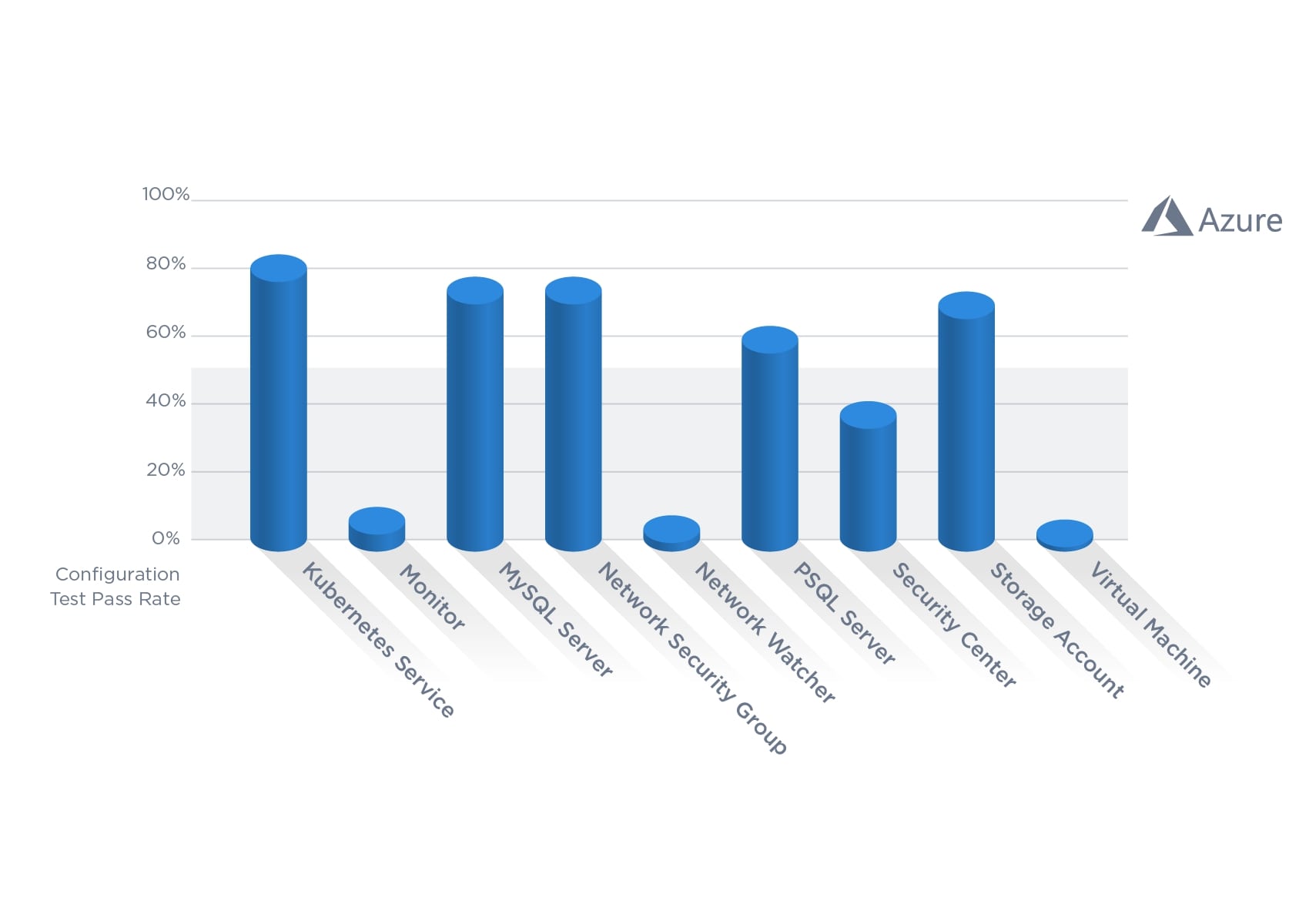
Microsoft Azure
Similarly with Microsoft Azure, encryption is a group of controls that often fails. The Disks category has two checks failing 99% of its scans. These two settings are: “Ensure that ‘OS and Data’ disks are encrypted with Customer Managed Key” and “Ensure that all unattached VM disks are encrypted.” Besides SQL Database Encryption (97.8% passing) and Web Apps using the latest version of TLS (85.4% passing), encryption checks are failing more than half of the time across the board.
On-premises Misconfigurations
Security practitioners must also assess risks for on-premises misconfigurations. Qualys Cloud Platform controls enable the assessment of more than 100,000 potential misconfigurations that could weaken cloud security. Urgent attention should be given to the most prevalent misconfigurations. During 2022, the top 10 failing controls (see Table 5 in the 2023 Qualys TruRisk Research Report) were for password settings, user permissions, and protocols for Windows Updates.
Linking Misconfigurations to Ransomware
In a joint effort between the MITRE Center for Threat Informed Defense and participating organizations, security controls were linked to MITRE ATT&CK Techniques and Mitigations to better understand their security coverage against threats outlined in the ATT&CK knowledge base. For the Qualys study, TRU examined all controls failing more than 50% of their scans and the associated MITRE ATT&CK techniques linked to those specific controls.
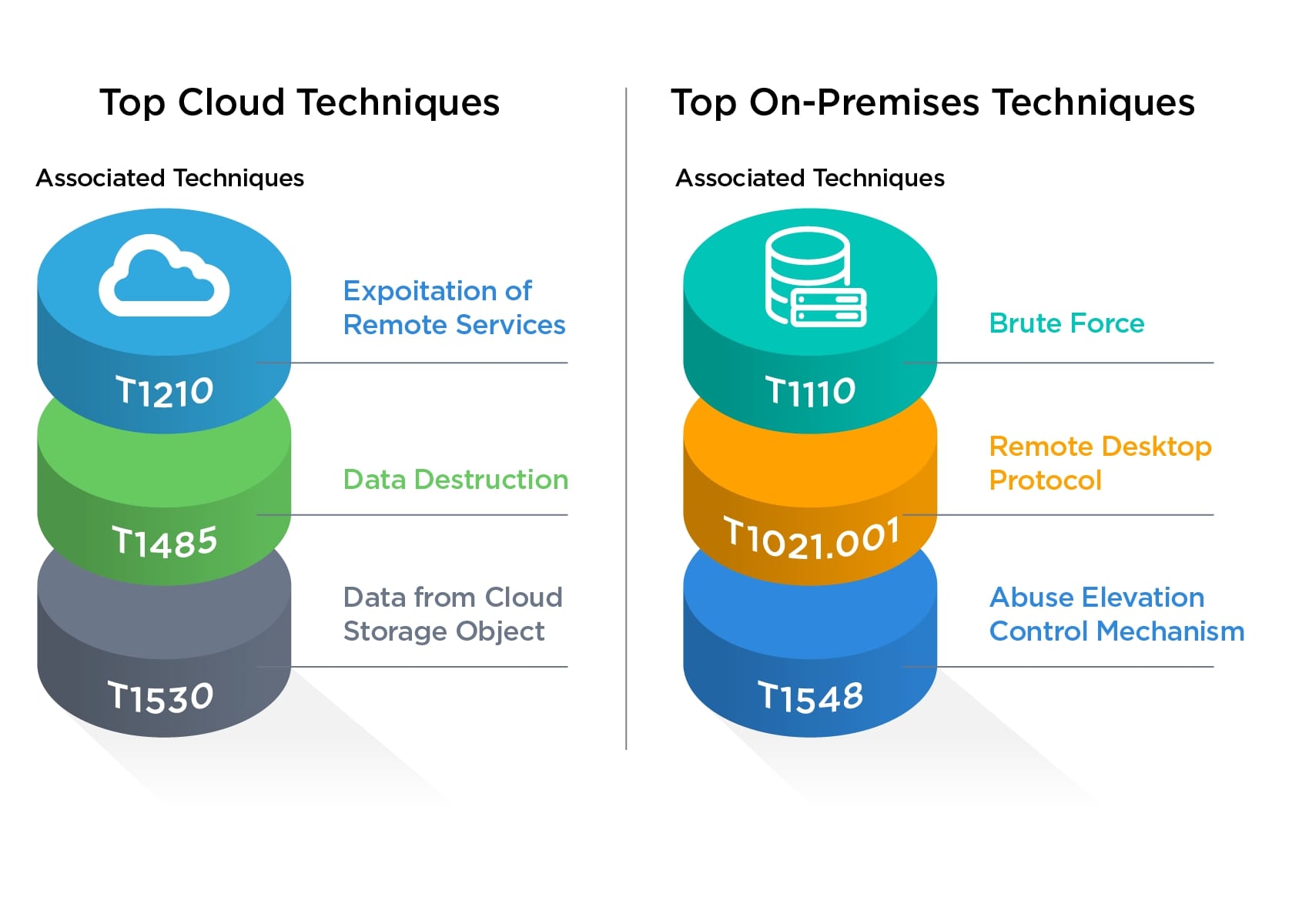
For cloud misconfigurations, the top three techniques associated with failing controls were T1210: Exploitation of Remote Services, 1485: Data Destruction, and 1530: Data from Cloud Storage Object. This indicates misconfigurations in the cloud are exposing organizations to exploitation, encryption, and exfiltration. These three techniques describe exactly how ransomware operates today.
Failing on-premises misconfigurations are associated with T1110: Brute Force, T1021.001: Remote Desktop Protocol, and T1548: Abuse Elevation Control Mechanism. When combined, these enable an attacker using guessed or stolen passwords to log into an exposed Remote Desktop Protocol (RDP) machine and elevate their privileges. This is a primary attack vector for Initial Access Brokers as an entry point into their intended victims.
Ransomware Specific Misconfigurations
Configuration checks to prevent ransomware are useful when using the Qualys Best Practice Controls for Reducing Risk Related to Malware/Ransomware policy. During 2022, these misconfigurations failed half of their scans with a pass rate of 49.4%. Surprisingly, nearly a quarter of the tests received a 100% pass rate, which is great news. Failing misconfigurations are associated with enabling threat actors to move laterally within an organization.
The study applied this ransomware policy to a default installation of Windows 10 to compare it to the overall status across the Qualys global customer base. A default Windows 10 installation had a passing rate of 34%, so Qualys users have improved their security posture by an average of 15 percentage points.
TRU’s evaluation discovered there are five settings securely configured in a default Windows 10 installation with a fail rate of more than 50%, meaning many organizations have intentionally misconfigured these settings. The top two failing controls were settings specific to Attack Surface Reduction, which indicates organizations are likely relying on other security tools to help prevent phishing-related attacks. The remaining three are password and RDP settings, which align with the overall failure rates of on-premises controls; these allow passwords to be used longer and changed less often while exposing RDP. While a valuable tool for administrators, there is potential for abuse – especially if connected directly to the internet.
The good news is there are more settings that organizations are intentionally configuring correctly. These include 16 settings that are otherwise misconfigured by default – settings that organizations are correctly configuring more than 50% of the time to be more secure. We can see quite a few configurations dealing with passwords, even though a few are intentionally misconfigured. At a high level, many of these are dealing with brute force/password stealing and lateral movement. Controls such as Universal Naming Convention (UNC) paths, Network Access, and Windows Firewall will reduce the ability of threat actors to laterally move within the environment. The password settings enable protections to prevent a threat actor from successfully achieving brute force of passwords by increasing the complexity and having thresholds automatically locking out the process upon invalid login attempts.
Overall, the lesson for Risk Fact #5 is user configurations for the three major cloud service providers are still an issue requiring urgent attention. Some configurations are being correctly set to enable more secure operations, but many are not. To get more details about which configurations are most at risk, download and read the 2023 Qualys TruRisk Research Report.
Get full 2023 Qualys TruRisk Research Report and learn about all five Risk Facts now.
Free Trial
如有侵权请联系:admin#unsafe.sh