Web search is about to embark on a new journey thanks to artificial intelligence technology that online giants such as Microsoft and Google are experimenting with. Yet, there is a problem when it comes to malicious ads displayed by search engines that AI likely won't be able to fix.
In recent months, numerous incidents have shown that malvertising is on the rise again and affecting the user experience and trust in their favorite search engine. Indeed, Search Engine Results Pages (SERPs) include paid Google ads that in some cases lead to scams or malware.
One particularly devious kind of malvertising is brand impersonation where criminals are buying ads and going as far as displaying the official brand's website within the ad snippet. We previously reported several incidents to Google and it appeared that those ads using official URLs were no longer getting through. However, just recently we noticed a surge in new campaigns again.
Brand abuse: Scammers exploit users' trust
It only takes a few seconds between a search and a click on a result, and most of the time that click happens to be on whatever shows up first. This is why advertisers are buying ads on search engines, not only to drive traffic towards their brands but also to outpace potential competitors. Unfortunately, not all advertisers have good intentions and the worst of them will exploit anything they can to put out ads that are malicious.
For about a week we decided to pull some examples and focused on Amazon-related searches since it is a popular search term (although other popular brands are affected as well). The ads we found were not only claiming to be Amazon's official website, they also displayed the amazon.com URL in the ad.

Figure 1a: Malicious advert

Figure 1b: Related network traffic

Figure 2a: Malicious advert

Figure 2b: Related network traffic

Figure 3a: Malicious advert

Figure 3b: Related network traffic

Figure 4a: Malicious ad

Figure 4b: Related network traffic

Figure 5a: Malicious ad

Figure 5b: Related network traffic
Below is an animation showing what happens when a victim clicks on one of those ads:
 Figure 6: Malicious advert leads to phishing page
Figure 6: Malicious advert leads to phishing page
While most of the brand impersonations we have seen recently are pushing tech support scams, this is not the only threat facing consumers. For example, we saw an ad that pretended to be Amazon's login page but instead redirects users to a phishing site, first stealing their password before collecting their credit card number.

Figure 7: A malicious ad leading to a phishing site
How are these criminals evading detection?
Ad URL
Part of the problem here is that advertisers can be legitimate affiliates and associated with the Amazon brand. Here's an example of a seller that is advertising on Google and has their own page as an affiliate on Amazon:

Figure 8: An advertiser leveraging the Amazon brand correctly
The problem comes when an advertiser that displays a brand's official URL within the ad snippet (i.e. https://www.amazon.com) is allowed to submit an ad URL that has nothing to do with that brand. We have seen many examples that include URL shorteners, cloaking services or domains freshly registered for the sole purpose of malicious activity.

Figure 9: Incidents related to Amazon searches tracked in malvertising spreadsheet
The screenshot above is part of a document we have shared with Google where we and other researchers track new malvertising campaigns ranging from scams to malware distribution.
Anti-bot traffic funneling and cloaking
Threat actors often rely on traffic filtering services to push malicious content exclusively to intended victims. Practically all the malicious ads we showed earlier used a kind of traffic distribution and filtering system. This market is a bit of a gray area with some companies advertising as anti-bot or anti-fraud providers while others are shamelessly advertising in places frequented by online criminals.
The goal is to not only game Google's and other ad networks but also to ensure that only qualified traffic is allowed to come through. With most malvertising from click ads, the practice comes down to something called cloaking.
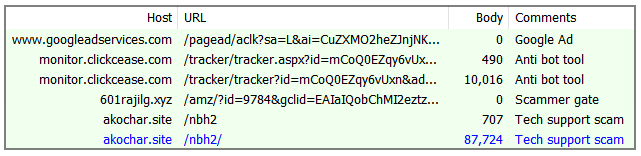
With cloaking, there are two types of URLs used: the legitimate URL (or decoy) and the money URL (the malicious one). In the picture below we see such parameters as well as the threat actor’s money page which contains folders for Amazon (amz) and YouTube - another keyword abused by malvertisers - (ytb) malvertising campaigns:

Figure 10: Cloaking parameters showing the money page
In this specific case we discovered a number of domains registered by the scammer, serving more or less the same purpose. One important thing to remember is that these domains are not immediately seen by Google. For example, the traffic filtering service will detect if a click is from a real user or a machine. It can then decide to forward the bogus click to Amazon's website and therefore maintain its cover.

Figure 11: Infrastructure used to redirect Google ads to tech support scams
For real traffic, these domains will act as intermediary to the payload pages which tend to be highly disposable and ever changing. There is a simple reason in that these are clearly malicious and will get reported and taken down. However, it is rare for the malvertising infrastructure to actually be disrupted because it is further upstream and rarely documented properly. This allows threat actors to continue with their malicious ad campaigns and simply swap payload pages.
Can Bard fix Google's malvertising problem?
We asked Google's AI chatbot Bard if it could fix the malvertising problem that seems to be plaguing its search engine. At first Bard said it was not able to solve this issue:

Figure 12: Bard answering a query about malvertising
However, on a second attempt Bard claimed it could after all help to fix the malvertising problem:

Figure 13: Bard answering the same question in a different way
Regardless, malvertising is a complex issue and given the billions of daily ad impressions, it's easy for someone nefarious to abuse any given platform. But we don't need AI to identify certain elements that allow threat actors to impersonate brands. Also, while educating users about malvertising is important, we can't blame them for clicking on paid ads that are supposedly verified as trusted.
Needless to say that these incidents will encourage users to install ad blockers at the chagrin of publishers whose revenues are heavily dependent on advertising. In the end, it comes down to the user experience and ensuring that it comes first, before anything else.
We then asked for some tips to protect against malvertising. We couldn't help but notice that Bard suggested using an ad blocker, although a small disclaimer at the bottom clearly states that Bard may display information that does not represent Google's views. Indeed, the ad industry accounts for almost 80% of Google’s revenues.

Figure 14: Bard offers some tips on how to protect from malvertising
Malvertising has been a problem for many years and it's unlikely to change any time soon. It's important for users to be aware that criminals can buy ads and successfully bypass security mechanisms all the while impersonating well-known brands. If you decide to type the URL in the address bar instead, remember to be careful not to make a typo. This is another area that is highly targeted by typosquatters and can also involve malvertising redirects.
All of the ads mentioned in this blog post have been reported to Google. We would like to thank the people working in the ad unit for their continued support.
Indicators of Compromise
Redirects:
tinyurl[.]com/amzs10
tinyurl[.]com/amz01111
Cloaking domains:
601rajilg[.]xyz
hesit[.]xyz
maydoo[.]xyz
pizz[.]site
ferdo[.]xyz
tableq[.]xyz
veast[.]site
amazonsell[.]pro
amaazoon[.]org
atzipfinder[.]com
Tech support scam domains:
ryderlawns[.]xyz
akochar[.]site
gerots[.]s3.eu-north-1[.]amazonaws[.]com
pay-pal-customer-helpline-app-tt6y3[.]ondigitalocean[.]app
micrwindow-app-38sqh[.]ondigitalocean[.]app
fekon[.]s3.ap-south-1[.]amazonaws[.]com
Malwarebytes Browser Guard provides additional protection to standard ad-blocking features by covering a larger area of the attack chain all the way to domains controlled by attackers. Thanks to its built-in heuristic engine it can also proactively block never-before-seen malicious websites.
We always recommend using a layered approach to security and for malvertising you will need web protection combined with anti-malware protection. Malwarebytes Premium for consumers and Endpoint Protection for businesses provide real-time protection against such threats.