What’s hiding in the shadows?
It’s a well understood reality that unmanaged IT assets tend to be unmonitored IT assets, and that both introduce risk. Whether it’s a forgotten about application, or an unmanaged cloud storage volume, you can’t protect what you don’t know about. Attackers thrive on this fact, and specifically seek out such assets as points of entry. This is why it’s included in the OWASP APIsec Top-10 in the Improper Assets Management risk category – refer to API9:2019 and/or API9:2023 (RC).
As the Internet has shifted heavily towards APIs, the threat of unmanaged assets has shifted with it. Shadow APIs are, very simply, those that you don’t know about, and they put businesses at risk. They may expose functionality or data that shouldn’t be accessible to users. Attackers may also exploit vulnerabilities in shadow APIs to gain access to critical systems, steal valuable data, or disrupt operations.
Where do Shadow APIs come from?
Gartner predicts that “By 2025, less than 50% of enterprise APIs will be managed, as explosive growth in APIs surpasses the capabilities of API management tools.” If your organization develops and deploys APIs as part of an application or service, then you may have Shadow APIs that stem from your own development processes. Many organizations simply have too many teams and too many different technology stacks to effectively manage the APIs they develop and deploy. If your organization can deploy code without updating the relevant documentation, especially API specifications (or if your organization doesn’t produce API specifications at all), then Shadow APIs are likely to exist. Even where policy requires that all deployed APIs be documented, it may not always be followed. Additionally, many organizations deploy third-party products that include APIs. These products may also have undocumented Shadow APIs, which are now part of your environment and risk posture.
How can Wallarm help?
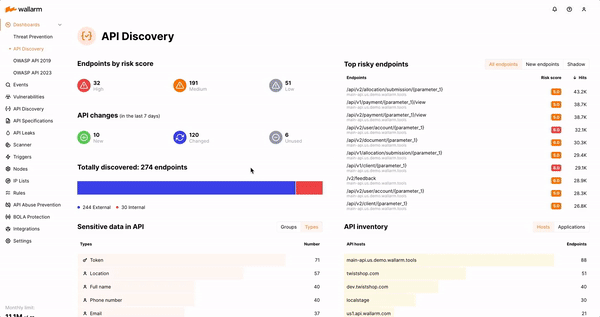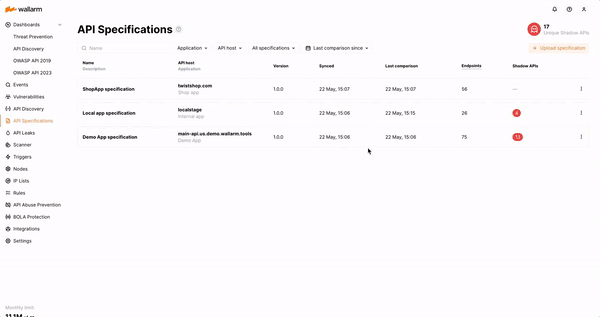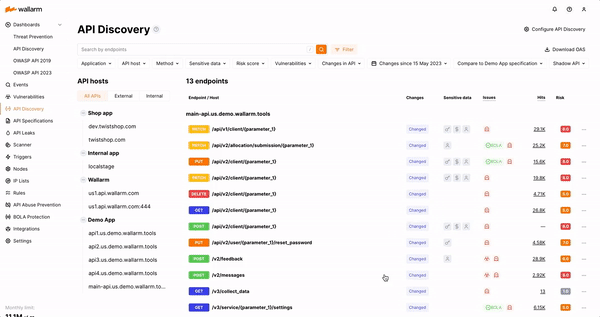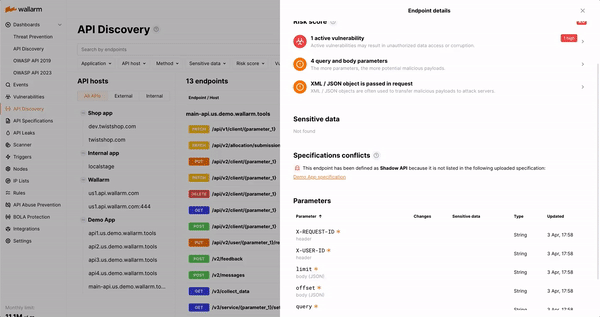
As part of our continuous improvement efforts to stay ahead of the rapidly evolving threat landscape, Wallarm has expanded its industry-leading API Discovery capability with new and improved Shadow API Detection, giving SecOps and Security Analysts the ability to identify undocumented and unmanaged APIs in the Wallarm console. Wallarm monitors all API traffic, identifying APIs and their endpoints with API Discovery, detecting and mitigating attacks with API Threat Prevention, and assessing risk with API Security Testing.

The addition of Shadow API Detection extends the API Discovery capabilities by comparing discovered API endpoints with corresponding API specifications to identify gaps. Wallarm analyzes any discrepancies between what should be present and what’s actually happening in production to identify shadow APIs, allowing security teams to take quick action to remediate risk.
To learn more, watch the Shadow API Demo video, review the changelog post, or read the documentation.
如有侵权请联系:admin#unsafe.sh