
2023-5-26 06:54:12 Author: blog.sucuri.net(查看原文) 阅读量:22 收藏
Welcome to another installment in helping website owners secure their digital assets, this time with a focus on the world of ecommerce. If you’re an ecommerce website owner, you’re likely aware that online stores face a unique set of challenges when it comes to security. Your success hinges on the trust customers place in your ability to protect sensitive data and provide a safe shopping environment.
In this latest post, we’ll delve into the world of securing ecommerce websites, from the basics of understanding the software and platforms you’re working with, to critical actions for reducing the attack surface and ensuring secure payments. We’ll also touch on the key PCI DSS requirements, share best practices and steps you can take to protect your online store, and explain how to create an effective disaster recovery plan for when things go wrong.
So, if you’re running an ecommerce store and looking for practical tips and advice on enhancing your website’s security, you’re in the right place! Let’s get started on improving the safety and trustworthiness of your online business.
Contents:
- Common threats facing ecommerce websites
- Reduce your attack surface
- Importance of secure payments and PCI-DSS
- Protect your online store
- Create a Disaster Recovery Plan (DRP)
Common threats facing ecommerce websites
Ecommerce stores, being treasure troves of sensitive user data, are prime targets for a range of exploits. Before we touch on how to secure your store, let’s quickly examine some of the most prevalent threats facing ecommerce businesses today to arm you with knowledge to better defend your online store.
| Credit Card Skimmers | One of the most significant concerns for ecommerce sites is credit card skimmers and Magecart attacks. In these attacks, cybercriminals inject malicious code into your site’s checkout page, scooping up credit card details from unsuspecting shoppers. |
| Cross-Site Scripting (XSS) | Cross-site scripting, commonly referred to as XSS, takes place when hackers execute malicious JavaScript within a victim’s browser. During the initial injection phase, the attacker attaches their malicious code on top of a legitimate website, effectively deceiving browsers into running their malware whenever the site is accessed. |
| Malware | The generic malware term covers a range of malicious code including SEO spam, backdoors, phishing, hack tools, and defacements. Infected files from numerous sources can introduce malware, which can wreak havoc by erasing data, stealing customer information, infecting site visitors, or even holding your site ransom. |
| SQL Injection (SQLi) | SQL injection attacks exploit backend databases by injecting malicious SQL code into existing SQL statements. As the main culprit behind large-scale data breaches, SQLi poses a genuine threat to ecommerce sites. |
| Distributed Denial of Service (DDoS) | DDoS attacks flood ecommerce servers with massive, orchestrated traffic, shutting out genuine customers. |
| Fraud | Chargeback fraud comprises customers who purchase goods, receive the items, then open disputes with the banks, claiming that transactions were illegitimate. |
Understanding the myriad of threats facing ecommerce businesses today is crucial for implementing an effective defense strategy. From credit card skimmers and XSS attacks to malware, SQL injections, DDoS assaults, and chargeback fraud, each exploit poses a unique challenge that requires tailored solutions.
Reduce your attack surface
As an ecommerce business owner, you’ve likely put a considerable amount of time and effort into designing your website and organizing your content; but have you thought about the intricacies of designing a robust security framework?
Think of your online store as a fortress, with potential vulnerabilities scattered throughout. The “attack surface” represents all the points in your store where malicious actors could attempt to exploit weaknesses. To better defend your online store, it’s crucial to understand the landscape and reduce its attack surface as much as possible. Remember, a smaller attack surface ultimately means fewer opportunities for cybercriminals to exploit.
Assess third-party components
Most people running self-hosted ecommerce stores utilize open-source Content Management Systems (CMS) like Magento, WooCommerce, or a custom-coded platform. These CMS solutions provide extensive flexibility and can be tailored to meet the unique needs of an online store. However, each plugin, module or extension added to the core CMS increases the attack surface and potential risks.
The key is in ensuring that each added component truly benefits your store’s operation without adding unnecessary vulnerabilities. Before incorporating a new extension or plugin, make sure that you consider the following questions:
- Do I really need this component?
- Does the vendor have a plan in place in case a vulnerability is disclosed?
- Are my developers prioritizing security measures?
- Do I have a reliable way to monitor and apply updates as they are released?
Analyzing these questions will help you make informed decisions about which extensions to use and trust in your online store. It’s essential to find a balance between enhanced functionality and maintaining a secure environment. Opt for core CMS functionality where possible, and when necessary, choose third-party options with a proven track record of security and ongoing support.
By reducing your online store’s attack surface, you are actively investing in a well-armed digital fortress capable of withstanding the barrage of cyber threats present in today’s interconnected world.
Keep refining your store’s defenses and always stay vigilant — exercising caution in an ever-evolving landscape of online security threats.
Importance of secure payments and PCI-DSS
In the realm of ecommerce, cash is king, and facilitating secure transactions is one of the most critical responsibilities of an online store. Ensuring the proper handling of sensitive data, such as credit card information and customer’s personally identifiable information (PII), is not just good practice — it’s also part of mandatory compliance standards, such as the Payment Card Industry Data Security Standard (PCI DSS).
A common approach for secure payment processing is utilizing the services of reputable payment gateways. However, this doesn’t absolve your online store from adhering to PCI compliance requirements.
To maintain a secure environment and protect your customer’s data, it’s essential to pay close attention to the following considerations:
- What kind of sensitive information are you collecting? (credit cards, passwords, addresses)
- Who has access to this information, and who should have access?
- Are events logged and recorded when someone accesses this information?
- Are you protecting payment data during transit with an SSL?
- Do you have proper storage and monitoring practices for cardholder data?
- Are you aware of your business’s specific level of PCI compliance?
- Do you keep logs of changes made to your website (e.g., files, DNS)?
By understanding these crucial aspects, you can take steps towards satisfying PCI DSS requirements 8 & 10:
- Requirement 8 – Identify and authenticate access to system components.
- Requirement 10 – Track and monitor all access to network resources and cardholder data.
Maintaining secure payment processes significantly boosts customer trust and strengthens your online store’s overall security posture. Stay ahead of potential threats and consistently monitor payment processes to uphold the highest levels of security for both you and your customers.
How to protect your online store
Eliminating all risks in the world of ecommerce is virtually impossible. The goal, then, is to proactively reduce risk and fortify your store’s defenses.
In an environment rife with myriad cyber threats, taking a proactive stance towards your online store’s security is not an option — it’s an absolute must. In this section, we’re going to tackle the critical actions and tools you need to not only defend your ecommerce site but also align with essential PCI requirements.
Step 1: Install a Web Application Firewall (WAF)
To kickstart your security measures, consider employing a powerful and reliable Web Application Firewall (WAF). A well-configured WAF shields your online store from hacking attempts and other exploitations, providing an added layer of protection for your customers and your business reputation.
But that’s not all! WAFs play a critical role in meeting several PCI DSS requirements necessary for achieving compliance in your online store. In particular, WAFs can help you comply with PCI DSS requirements 1 & 2:
- Requirement 1: Build and Maintain a Secure Network – Install and maintain a firewall configuration to protect cardholder data.
- Requirement 2: Build and Maintain a Secure Network – Do not use vendor-supplied defaults for system passwords or other security parameters.
By leveraging a WAF’s capabilities, you are actively defending your ecommerce site against cyber attacks and significantly improving your security posture.
Additionally, WAFs can save you time and reduce the burden of constantly monitoring and applying changes yourself. Instead, you can focus on growing your business, with the confidence that your site’s protection is being handled by a reliable, proactive solution.
Step 2: Select a Secure Payment Gateway
Ensuring your customers’ financial data stays protected during transactions is of utmost importance. The use of a reputable payment gateway offers a secure method for encrypting credit card and other sensitive data, helping you achieve compliance with PCI DSS requirements.
Be cautious and deliberate when selecting a payment gateway for your ecommerce site to guarantee the security of all transactions, thereby building trust in your brand.
Step 3: Install an SSL Certificate to Encrypt Traffic
A Secure Socket Layer (SSL) certificate is an essential element of any online store’s security toolkit. SSL certificates encrypt your visitors’ personal information and credit card data, protecting both them and your reputation from potential fallout in the event of intercepted data.
Ensuring that a valid SSL certificate is installed for your ecommerce site plays a crucial role in adhering to the PCI DSS Requirements 3 and 4, focused on protecting cardholder data, stored or transmitted across open, public networks.
By adhering to these guidelines, your ecommerce store will not only satisfy a significant portion of PCI DSS requirements but, more importantly, provide customers with a secure shopping experience that fosters trust and confidence in your brand.
Create a Disaster Recovery Plan (DRP)
With everything we’ve covered so far, one question comes to mind – what do we do when the worst-case scenario comes to pass? Look, we can take all the precautions we have mentioned, but remember the golden rule: “There is no such thing as perfect security.”
The best we can do is minimize risk as much as possible. But, when things do go wrong — which, let’s face it, they sometimes do — you’ll be thankful that you prepared for the worst with a well-planned Disaster Recovery Plan (DRP).
Now, what should a good DRP for your ecommerce website consist of? We’re going to break down this crucial safeguard into four main actions that form a continuous workflow.
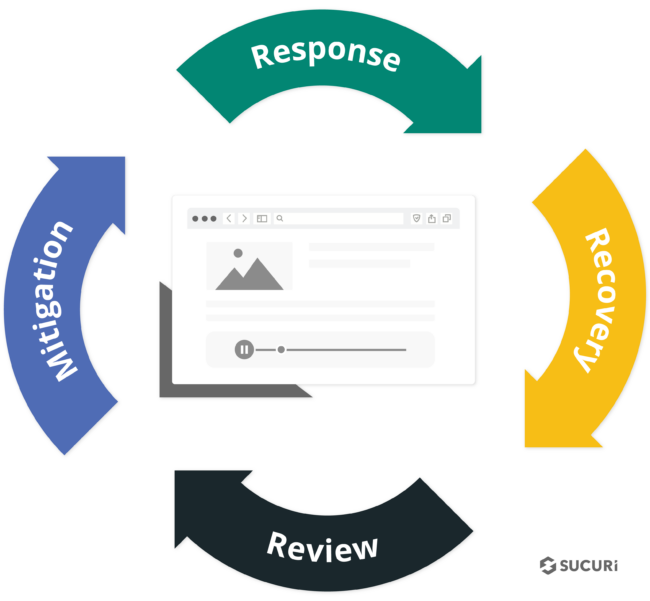
The beauty of this design highlights the ongoing efforts needed for a genuinely effective preventive strategy.
Response:
The first component of a solid DRP is prompt and effective response when an incident occurs. Whether that’s malware, data breaches, or denial of service attacks, you must be prepared to tackle these threats swiftly. Use resources like the free guides I’ve mentioned in my earlier blogs for cleaning various CMS platforms or have the contact information of a trusted vendor ready for immediate remediation services.
Recovery:
When disaster strikes, a rapid recovery is paramount to minimize the fallout. Key elements of your DRP’s recovery phase should include:
- Disclosure: Notify your customers if any data was compromised, especially if you’re operating within jurisdictions where timely reporting is required, such as the GDPR in the EU.
- Backups: Maintain offsite, regularly updated backups to protect your data in the event of ransomware attacks or catastrophic loss. This ensures a speedy return to functionality so you can get back to doing what your online store does best—selling products.
- Follow-ups: Collaborate with your security vendor, discuss the incident’s specifics, and identify areas for improvement in your existing security measures. This plugs potential vulnerabilities and prepares your store for future attacks.
Review:
Once the dust has settled, it’s crucial to review your store’s security and identify gaps or oversights. The more you know, the better decisions you can make to reduce risk. Use insights and recommendations from security professionals to implement changes that minimize your store’s exposure and further harden your security measures.
Mitigation:
Taking quick and decisive action is the name of the game when it comes to security mitigation. Implement the hardening measures and improvements you’ve identified at the Review stage and don’t hesitate to make necessary adjustments to your Web Application Firewall’s configurations.
Proactive planning and preparedness are your best allies in the fight against malicious activities targeting your online store. With a well-rounded strategy encompassing robust defenses, up-to-date security measures, and an ironclad Disaster Recovery Plan, you can rest assured that your ecommerce website is as fortified as it can be. Remember that risk can never be wholly eliminated — but a strong DRP ensures that you’re in the best position to weather the storm and bounce back even stronger.
Closing thoughts
As we wrap up this detailed look at securing your online store, it’s crucial to recognize that in the constantly evolving world of cybersecurity, awareness and adaptability are your strongest weapons. By implementing the strategies and practices outlined in this guide, you can significantly reduce your attack surface, protect your customers’ sensitive data, and build confidence in your ecommerce brand.
Embracing a proactive approach is key. Begin by identifying and addressing potential risks, ensure secure payment processing, and deploy a defensive strategy using technologies like Web Application Firewalls. And don’t forget the importance of PCI DSS requirements, which not only improve customer trust but also protect your business in the long run.
Even the most secure systems are not immune to threats. It’s vital to have a robust disaster recovery plan (DRP) in place — because how you respond to and recover from an incident is just as important as the measures taken to prevent it in the first place. A good DRP consists of quick response and remediation, transparent communication and disclosure, comprehensive data backups, thorough security reviews, and timely mitigation actions.
Remember, in the realm of cybersecurity, no one can afford complacency or stagnation. By continuously monitoring, updating, and refining your security practices and defenses, you’ll not only minimize risks and ensure PCI compliance but also foster trust among your customers and maintain the reputation of your online store.
Because at the end of the day, it’s your dedication to securing the fortress that ultimately keeps your online store thriving in the competitive landscape of ecommerce. Happy fortifying, folks!
如有侵权请联系:admin#unsafe.sh
