2023-6-1 01:28:25 Author: www.horizon3.ai(查看原文) 阅读量:30 收藏
In early 2023, CISA launched their Ransomware Vulnerability Awareness Pilot (RVWP). It’s designed to warn critical infrastructure (CI) entities that their systems have exposed vulnerabilities that may be exploited by ransomware threat actors. The plan is to identify affected systems that may be prevalent in CI networks, then notify operators about potential risk of exploitation. The idea behind this is to enable timely mitigation measures before the damage is done in the context of ransomware attacks.
According to the RVWP website, “Once CISA identifies these affected systems, our regional cybersecurity personnel notify system owners of their security vulnerabilities, thus enabling timely mitigation before damaging intrusions occur.” However, almost any exploitable system could allow attackers to gain a foothold, and from there, ransomware is often the next likely outcome, especially if attackers are interested in nothing more than money.
Although CISA’s efforts are a step in the right direction, the real challenge comes from identifying what systems are truly vulnerable to exploitation, then evaluating the likelihood of these systems becoming targets of attackers. Just because a system may have a possible ransom-related vulnerability does not mean it’s exploitable for a host of different reasons, for example, being completely unreachable by attackers. As a result, CI entities will likely be chasing down low-level targets while high-level risks may not get adequately addressed.
Most successful ransomware attacks are primarily due to hidden vulnerabilities that have laid dormant within the inner bowels of a network for some time. For example, this endemic problem plaguing American cities (and organizations all over the world) won’t likely be resolved anytime soon until organizations accept the fact that yes, they are likely vulnerable to ransomware attacks.
For example, on May 4th news outlets broke the story about the city of Dallas under ransomware attack. On Friday, May 9th local news stations were still reporting:
- Computer dispatch was still down in the Dallas 911 call center.
- Police and firefighters were sent to calls by radio using paper and pencil for addresses.
- Code enforcement and other non-emergency responses to 311 calls were delayed.
- City water bill payments were impacted. Disconnections were canceled.
And as of May 17th, local new stations are still reporting that the City of Dallas Ransomware Attack Stretches into Day 15. Although technical details of how the attack progressed are not publicly available, most security savvy people suspect it was due to a vulnerable system lying in wait.
The real problem concerning ransomware is that too many people don’t really understand what causes a successful ransomware campaign. Most believe it’s some sort of extra skilled attacker but that is not always the case. At the very root of the problem is completely exploitable systems (hardware and software) going unchecked. But why is that the case?
Both public and commercial organizations often have no idea where those unchecked vulnerabilities lie. That’s why it’s imperative to get ahead of the game and find the vulnerabilities yourself by attacking your infrastructures the same way an attacker will. This is not a one-and-done proposition, or some periodic list of boxes that you check. You’ll never be able to manage your risk daily if you don’t know where you’re vulnerable. As a result, tools like NodeZero are readily available to perform this continuous function for you today.
The real key to shoring up security of not only CI entities, but also cities, education systems, banks, hospitals, and anything else deemed critical is to determine what is actually exploitable by scanning, testing, and simulating what threat actors would do if they obtained, then maintained a foothold in any network. Ransomware normally begins with a foothold!
This is where autonomous pentesting approaches like NodeZero can be used to simulate the actions that would likely be taken by a ransomware attacker. This involves identifying what is exploitable, what steps could be taken by attackers to move laterally and take over systems, how attackers could elevate permissions, etc., then ensuring remediation actions are performed as soon as possibly that are highlighted by the pentesting platform.
Once remediation is complete, regularly scheduled NodeZero pentests should be performed to validate remediations were successful and if new vulnerabilities are discovered. This is not a one-and-done activity. Instead, it must become second nature to all organizations as part of their ongoing governance and risk reduction programs.
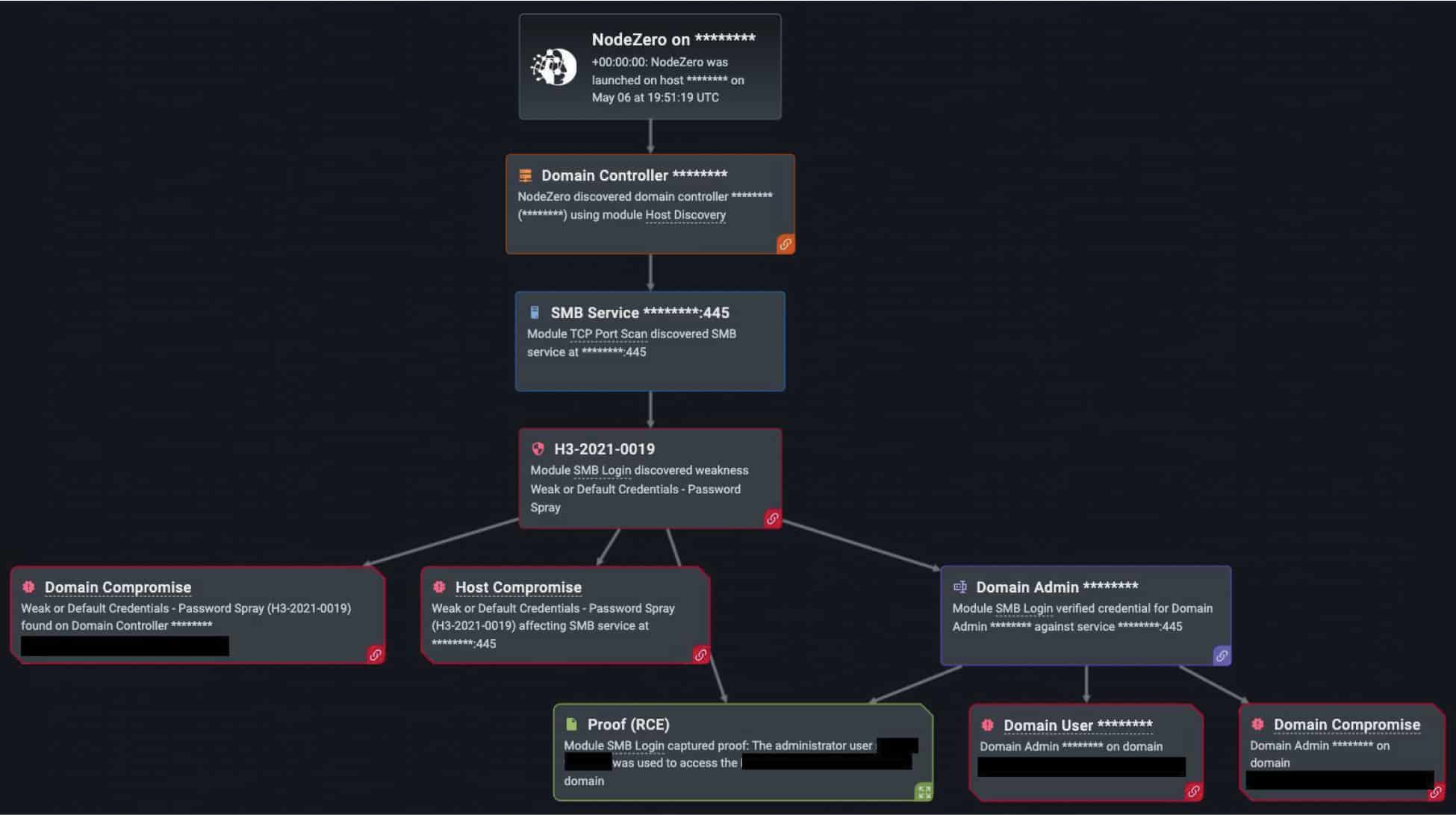
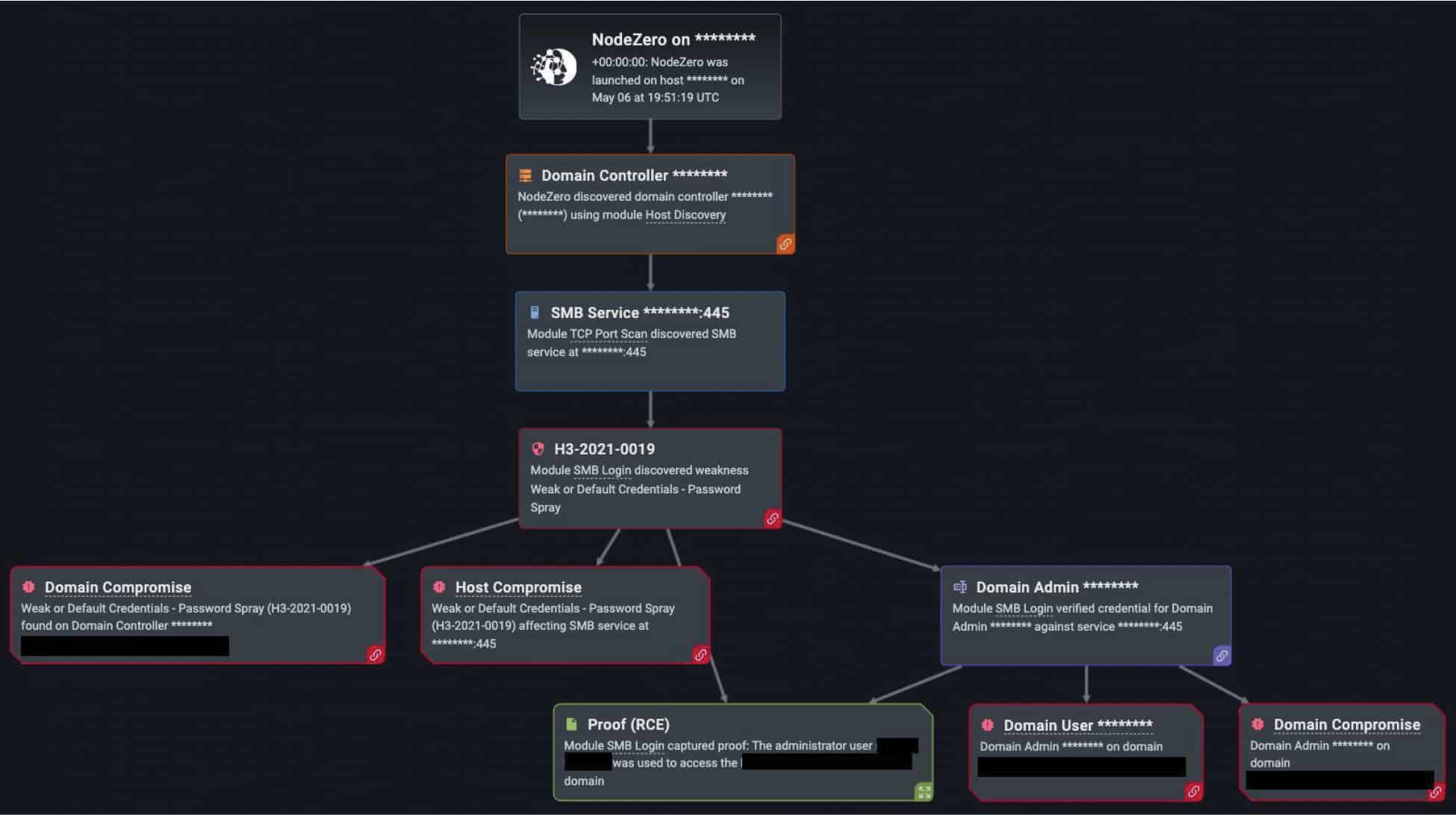
Horizon3.ai’s Year in Review for 2022 report highlights a NodeZero pentest by a North Carolina-based medical clinic. The clinic found that its systems were exploitable after NodeZero conducted open-source intelligence on the company’s name, scraped potential employees from LinkedIn, then executed the password spraying technique to find a potential logon name with a common, weak, or publicly available password.
Just as an actual cyber threat actor would do, NodeZero chained other weaknesses with the successful password spray to achieve multiple critical impacts. In this case, over 1,600 credentials were captured and used to access services and infrastructure. As a result, our customer learned that NodeZero compromised one domain, almost 50 hosts, and two domain users, while discovering nearly 50 data stores to ransom. Below, you can see proof of the successful attack.
In the report, you can see additional examples of NodeZero achieving a critical impact including domain compromise, host compromise, sensitive data exposure, critical infrastructure compromise, or ransomware exposure.
To learn more about how Horizon3.ai can help you avoid ransomware attacks in your networks,
如有侵权请联系:admin#unsafe.sh