2023-6-2 21:0:59 Author: www.sentinelone.com(查看原文) 阅读量:31 收藏
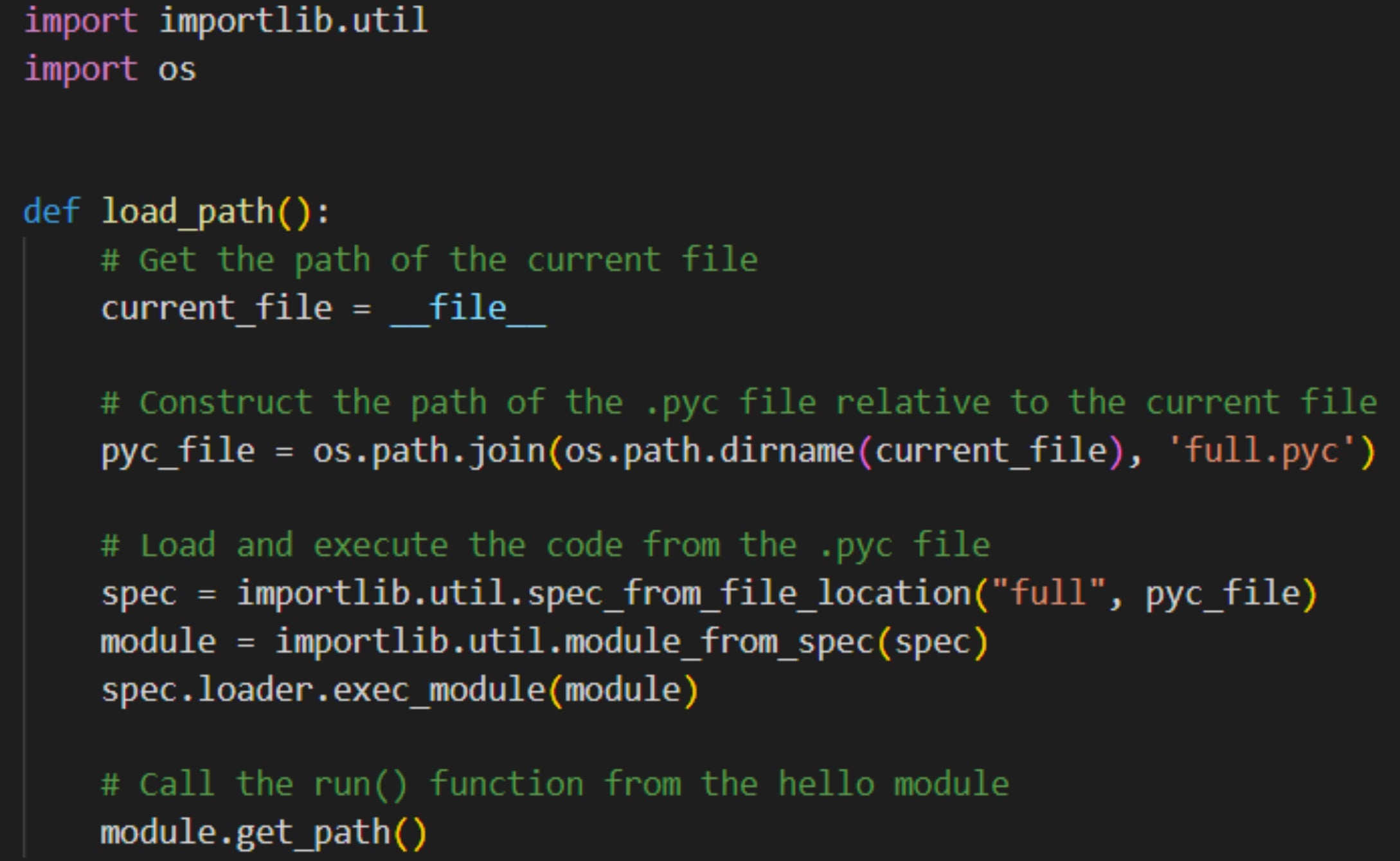
Breached | Data of 478,000 RaidForum Users Exposed Online
The tables turned on cybercriminals this week when private user information from the notorious RaidForums was leaked online to another hacker forum. This newer forum called “Exposed” was launched just earlier this month, making the news of this data leak their first big splash in the darknet ecosystem.
Though RaidForums was infamously frequented by cybercriminals, threat gangs, and other such unsavory parties, it was also accessed by a wide range of hackers and, of course, law enforcement. The leaked database reportedly contained the registration information of just over 478,000 members including signup dates, emails, hashed passwords, and usernames. It is currently unknown why the leaked data, in the form of a single SQL file, was generated in the first place.
Before it was shut down by in an international joint operation across numerous law enforcement agencies in April 2022, RaidForums had built up a reputation as one of the top go-to forums for buying, selling, and dumping stolen data such as bank routing and account numbers, credit card information, login credentials, and social security numbers. The data leak doesn’t provide any new information to law enforcement but can prove useful to security researchers and their investigations.
Though there is a touch of poetic justice in seeing malicious hackers and cybercriminals having their data leaked onto a forum they visit, the existence of new forums like Exposed underscores how prevalent the demands are for trading in illicit and stolen data. After RaidForums was seized, another site called “BreachForums” was on track to become RaidForums’ would-be successor before it shut down in response to the arrest of their founder. As new forums like Exposed continue to quickly fill the void and gain traction, businesses must remain vigilant with protecting their sensitive data.
Malicious Python Libraries | Novel PyPi Malware Takes Aim at Digital Supply Chains
Observing a spike in malicious submissions to the PyPi (Python Package Index) repository, security researchers this week released a report on what may be the first supply chain attack to exploit Python byte code (PYC) files. Since these files can be directly executed, this novel attack method raises yet another concern in digital supply chains.
The package, called fshec2, was discovered in April and promptly removed from the repository on the same day, though the PyPi team told researchers that this type of attack was not previously seen before. According to their report, researchers were able to note a suspicious combination of behaviors from the fshec2 package which contained the following three Python source files:
__init__.py– the entry point of the package with the purpose of importing a function from main.pymain.py– container for the Python source code with the purpose of loading the compiled module infull.pycfull.pyc– the malicious file capable of downloading commands from a remote server.
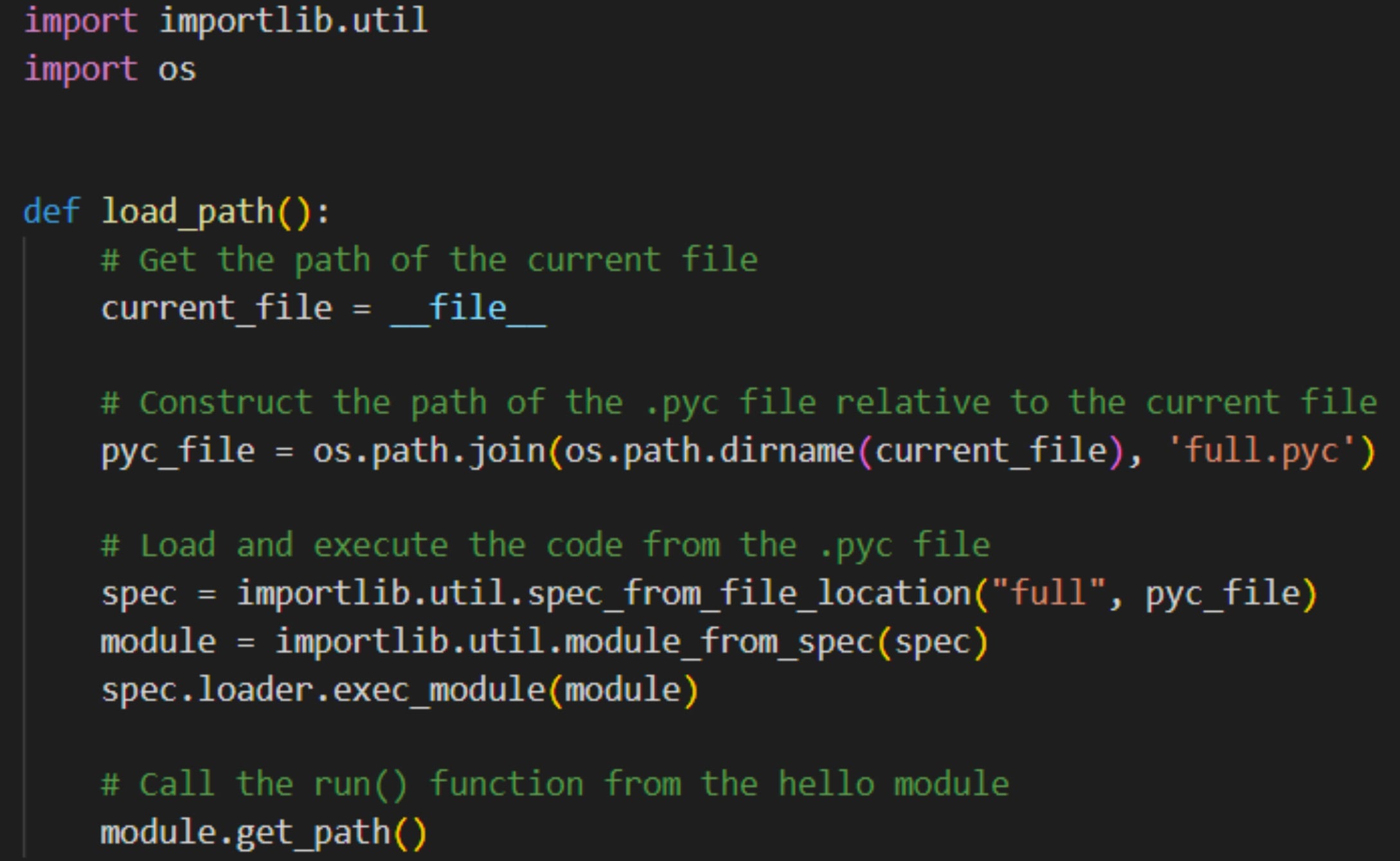
The fshec2 malware was observed using the import to trigger a novel loading technique instead of using an import directive to load a Python compiled module – a commonly detectable method seen in attacks. Upon analysis, the researchers found a number of mistakes in the malware’s initial configuration suggesting that it was not the work of advanced persistent threat (APT) groups nor a state-sponsored actor.
While this malware was spotted early, it’s a reminder that threat actors are increasingly targeting public code repositories in an effort to breach companies via third-party dependencies. Consequently, supply chain security must continue to be a main priority for enterprises.
Zero-Day Vulnerability | Flaw In Popular File Transfer Tool Used to Steal Data
MOVEit Transfer, a widely-used file transfer automation solution, disclosed a vulnerability this week that gives attackers unauthorized access to users’ systems. Designed to securely transfer data and assets between customers and their business partners through SFTP-, SCP-, and HTTP-based uploads, MOVEit is currently used worldwide by thousands of organizations. CISA warned this week that mass exploitation of the flaw has already been observed in the wild and data from a number of users’ systems has been stolen.
The zero-day, not yet assigned a CVE, is a severe SQL-injection vulnerability that allows privilege escalation and potential unauthorized access to the environment. Depending on the database engine being targeted (MySQL, Microsoft SQL Server, or Azure SQL), an attacker can gather valuable intel about the infrastructure and the contents of the database before executing SQL statements to alter or delete the database elements. The developers of MOVEit Transfer have since released patches for the vulnerability and urged customers to patch immediately.
News of the zero-day vulnerability in MOVEit is the latest in a rising trend of attacks on file transfer solutions such as Accellion’s File Transfer Appliance , GoAnywhere’s file transfer utility (CVE-2023-0669), and IBM’s Aspera Faspex file transfer tool to name a few. As the global managed file transfer market continues to grow in demand from a reported $1.3 billion in 2022, avenues of cyberattack for the industry will also widen with threat actors doubling down on ways to obtain unauthorized access to vulnerable systems.
如有侵权请联系:admin#unsafe.sh