2023-6-16 04:37:53 Author: blog.sucuri.net(查看原文) 阅读量:19 收藏
When we think about website malware, visible infection symptoms most often come to mind: unwanted ads or pop-ups, redirects to third party sites, or spam keywords in search results. However, in some cases these very symptoms are the results of hacktools, a diverse and often insidious category of software designed to exploit vulnerabilities and compromise website security.
According to our latest threat report, in 2022 alone, a staggering 23.63% of infected client websites were found to have at least one hack tool at the point of infection, highlighting the importance of being aware of (and protecting your site from) different types of malware.
In today’s post, we’ll explore the mysterious world of hacktools, uncover their purpose, delve into the reasons they are left behind on hacked websites, examine the risks they pose to both website owners and visitors, and learn the steps you can take to detect and protect against them.
Contents:
- What is a hacktool?
- Types of hacktools
- Threats posed by hacktools
- How to check your site for malware
- Prevention techniques
At its core, a hacktool is a software application or script designed to exploit vulnerabilities and gain unauthorized access to computer systems, networks, websites, or assist hackers perform a specific illicit related task. These tools are often created by skilled programmers and hackers, who share a deep understanding of the intricacies of various systems and the potential weaknesses that can be exploited.
While there are numerous hacktools in existence, some of the most common types our research team find on hacked websites include:
| Exploit kits | These kits are collections of exploits targeting multiple vulnerabilities in popular software applications, such as browsers, plugins, and content management systems. They are often used as part of automated attacks, scanning websites for known vulnerabilities and delivering payloads when a suitable target is found. |
| Web shells | Web shells are scripts that provide attackers with remote access to a compromised website or server. They often come with a user-friendly interface, allowing attackers to execute commands, upload or download files, manage the server with ease and can be tailored to specific needs or ends that the hacker chooses. Sucuri classifies most web shells as backdoors. |
| Brute force tools | Brute force tools are designed to systematically guess usernames and passwords, attempting to gain unauthorized access to accounts and systems. They often come with pre-built dictionaries of commonly used passwords and can be customized to target specific services, such as email or content management systems. |
| Confidential information stealers | As the name suggests, these tools are designed to steal sensitive information, such as login credentials or credit card details, from targeted systems. This can be accomplished through various means, including keylogging, phishing attacks, or exploiting known vulnerabilities in software applications. |
| DDoS tools | Distributed denial of service (DDoS) tools are used to overwhelm a target website or server with a massive amount of traffic, rendering it inaccessible to legitimate users. These tools often leverage botnets – networks of infected computers – to amplify the attack and make it more difficult to trace back to the source. |
| Mailers | Mailers are hacktools that let an attacker send out large amounts of malspam or phishing emails from a compromised website’s web server. It contains various text fields that allow the attacker to input custom data for email fields like email address, sender name, reply-to, subject lines, and body content. |
While not all hacktools are created equal, they are typically used to target and exploit target websites. And they’re often packed with a range of features that make it easy for an attacker to compromise an environment and exploit any available resources.
Why do attackers leave a hacktool on a website?
To better comprehend the threats posed by hacktools, let’s examine five key reasons why attackers choose to leave these tools on hacked websites.
Malware propagation
Hacktools often serve as a means for attackers to spread malware to other systems, both within the target network and beyond. By leaving these tools behind, they can use the compromised website as a distribution platform for their malware campaigns, whether it’s discovering other sites that can be infected on the same server, searching for resources that can be abused (ie. mail servers or databases), or using the website as a stepping stone to infiltrate other networks.
Monetize illegal activities
The presence of hacktools on a compromised website can be indicative of an attacker’s intent to profit from illegal activities, such as spamming, phishing, or distributing denial of service attacks. By leveraging the website’s resources and reputation, attackers can potentially generate revenue from their illicit actions, all while remaining hidden behind the cloak of the hacked site.
Espionage and data theft
Hacktools can be instrumental in facilitating cyber espionage and data theft. Attackers who manage to infiltrate a target website or server may use these tools to exfiltrate sensitive information, such as customer data, intellectual property, or trade secrets. In some cases, this information can be used for financial gain, while in others, it may serve as a means of exerting control or inflicting damage on the target organization.
Threats posed by hacktools
The presence of hacktools on a website poses a significant risk to both website owners and their visitors. One of the most immediate concerns is the compromise of website security, leading to unauthorized access and potential data breaches. This can result in the loss of sensitive information, such as customer data, which can have severe legal and financial repercussions for the website owner.
- Blacklisting: Hacktools can cause domain and server IP blacklisting due to spamming, brute force attacks, or DDoS assaults. This can result in legitimate emails being blocked by spam filters, and certain APIs may cease to function as firewalls block requests from the affected IP address.
- Mass compromise: These tools enable mass compromises of sites sharing the same server. A hacktool exploiting flaws in server configurations on an unrelated third-party site could infect an otherwise secure website.
- Increased resource usage: Hacktools can increase resource usage, placing a strain on the CPU or generating large amounts of traffic. This can slow down the site and server, deplete quotas, and potentially incur additional costs for cloud platforms that charge based on resource usage.
- Indicator of compromise: The presence of a hacktool is an indication of a compromised site. In addition to hacktools, compromised sites often contain other types of malware, including SEO spam and visitor-targeted malware like unwanted redirects and drive-by downloads.
Moreover, the reputation and trust built by the website owner can be severely damaged, as hacktools can potentially disrupt website functionality and user experience, further deterring visitors and tarnishing your site’s credibility.
How to check your site for hacktools
Detecting hacktools on your website is a crucial step in maintaining a secure and trustworthy online presence. To effectively identify and neutralize these threats, follow these steps.
1 – Perform regular website security scans
You’ll want to perform regular, extensive scans of your website’s files to identify vulnerabilities and rule out a compromise or infection.
You can leverage free tools like SiteCheck to scan your website for malicious code, but keep in mind that remote scans won’t be able to detect anything lurking on the server level.
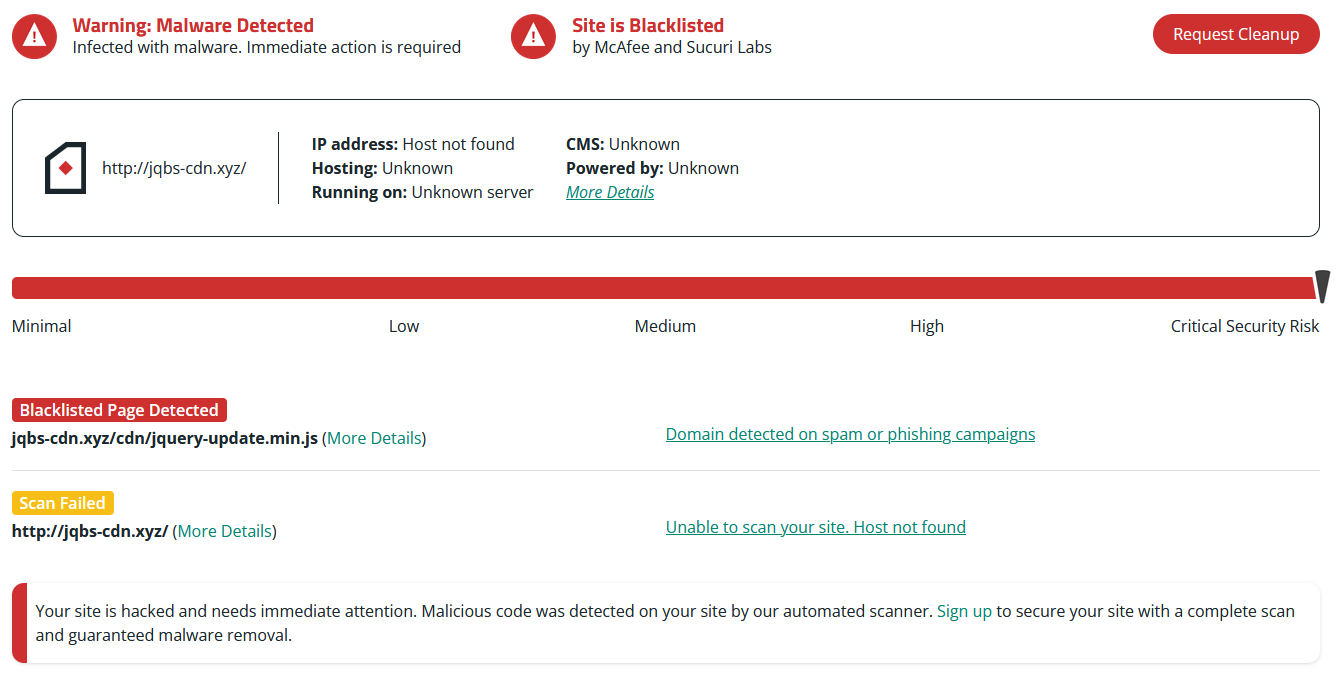
You can complement external scans with server-side scans, which can help identify hidden hacktools or other malicious files within your website’s infrastructure.
2 – Check your domain and server IP against known blacklists
You can easily check an IP against a list of known blacklists by leveraging free scans found in Sucuri SiteCheck, Spamhaus, and AbuseIPDB.
SiteCheck
Sucuri’s own SiteCheck makes it easy to check a domain for malware, viruses, blacklisting status, and other malicious code. It checks domains against a wide number of blocklist authorities to identify if it’s engaged in any known sketchy behavior.
To scan a website, navigate to https://sitecheck.sucuri.net then enter a domain and click Submit.
Spamhaus
Spamhaus is an international nonprofit organization that has been combating spam and cyber threats like phishing, malware, and botnets since its inception in London in 1998. Spamhaus operates DNS-based blocklists responsible for blocking a significant portion of spam and malware on the internet.
Checking an IP or domain with this tool is easy. Simply navigate to https://check.spamhaus.org/ then enter the IP or domain URL into the search box and press Lookup.
AbuseIPDB
AbuseIPdb.com is an excellent resource that allows you to check if an IP has been reported for abusive activities like hacking, spamming, or other malicious behavior.
To scan your server IP, navigate to abuseipdb.com and enter your IP into the search box to query for known malicious behavior.
3 – Monitor your website’s logs
Regularly reviewing your server and website activity logs can help you detect unusual or suspicious behavior, such as repeated login attempts, unauthorized file uploads, or unexpected changes to website content.
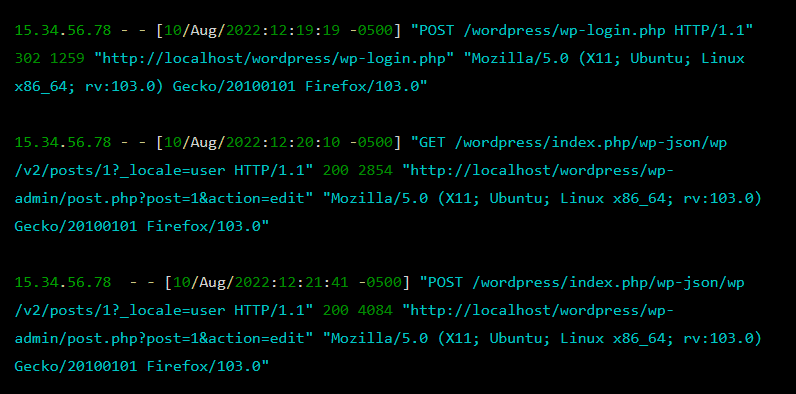
By catching anomalies and unexpected behavior early, you can take appropriate action to mitigate potential threats on your website.
4 – Use file integrity monitoring
Implementing a file integrity monitoring system can help you detect unauthorized changes to your website’s files, which may indicate the presence of hacktools or other forms of compromise.
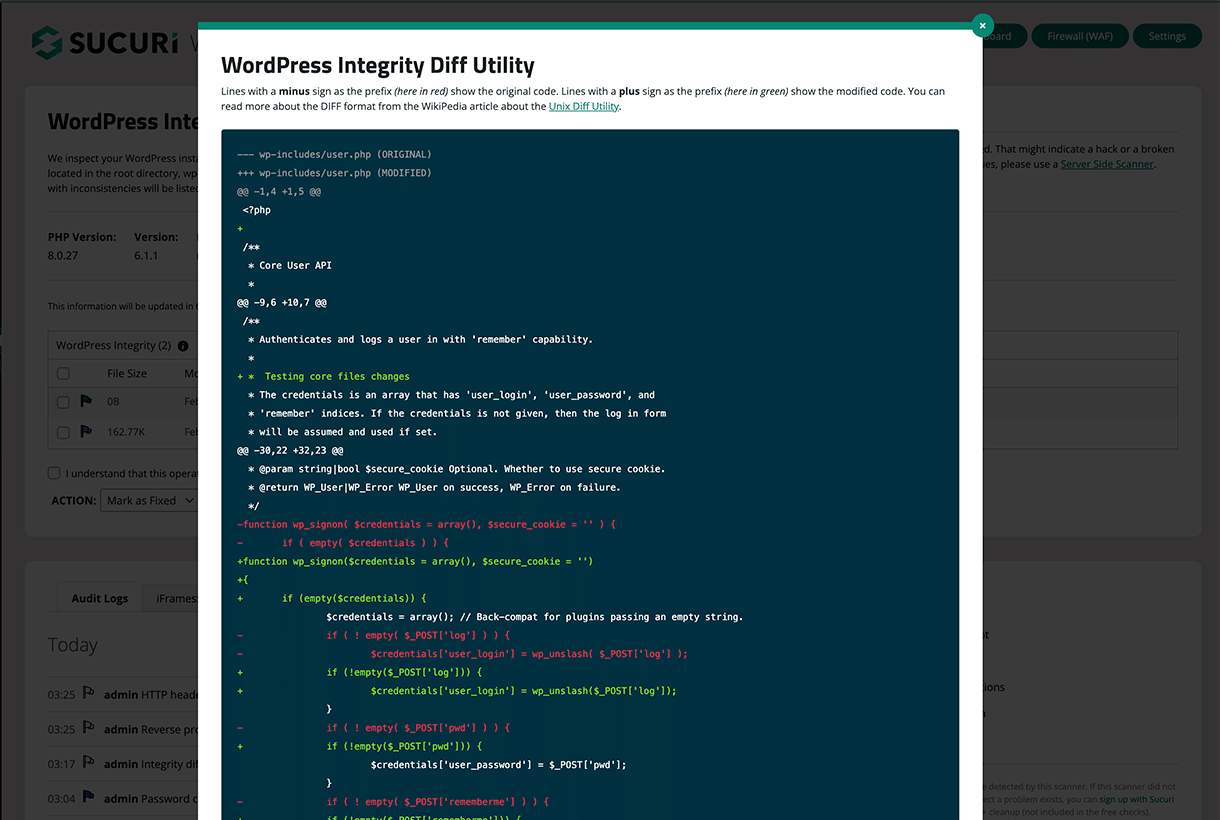
These systems typically work by comparing the current state of your files to a known, trusted baseline, alerting you to any discrepancies.
If you’re a WordPress user, you can leverage the Sucuri Security WordPress plugin which contains tools to check the integrity of your core WordPress files, including PHP, JavaScript, and CSS.
5 – Leverage intrusion detection systems (IDS)
Intrusion detection systems (IDS) can help identify and block potential threats before they can cause damage to your website. These tools monitor your network for signs of malicious activity and can be configured to automatically respond to threats, such as by blocking IP addresses or quarantining affected files.
The Sucuri Firewall bundles the best of a WAF (Web Application Firewall) and an IDS (Intrusion Detection System) to detect and protect against website threats and attacks.
6 – Analyze your website traffic for unusual patterns
Monitoring your website traffic for unusual patterns or spikes can help identify potential hacktool-related activity, such as DDoS attacks or SEO spam campaigns. By recognizing these abnormalities, you can take swift action to investigate and address the issue, minimizing the impact on your website and its users.
How to prevent infection from hacktools and other malware
Protecting your website from hacktool infections requires a proactive and comprehensive approach to security. Here are some best practices to help you protect your site from hackers.
- Regularly update your website software and plugins: Keep your website software, plugins, and other components up-to-date to minimize potential vulnerabilities that could be exploited by hackers. Ensure that you apply security patches and updates as soon as they become available to reduce the risk of compromise.
- Employ strong and unique passwords: Use strong, unique passwords for all of your website accounts, including your content management system, hosting provider, and any other administrative access points. Avoid using easily guessable passwords or reusing the same password across multiple accounts.
- Implement multi-factor authentication: Enhance the security of your website by implementing multi-factor authentication (MFA) for your accounts. MFA requires users to provide additional proof of identity, such as a temporary code sent to a mobile device, in addition to their password, making it more difficult for unauthorized users to gain access.
- Limit user permissions and access: Restrict the number of users with administrative access to your website and assign the minimum necessary permissions to each user. This reduces the risk of unauthorized access through compromised accounts and helps to prevent the misuse of privileged access.
- Use a web application firewall: A web application firewall (WAF) adds another layer of security to your website by filtering and monitoring inbound and outbound traffic. A WAF can help detect and block malicious requests, such as SQL injection or cross-site scripting (XSS) attacks, before they reach your website. By using a combination of predefined rules and customizable settings, a WAF can be tailored to your specific security needs, providing an effective barrier against hacktools and other cyber threats.
Conclusion
Understanding and recognizing the threats posed by hacktools is a critical aspect of securing your website and protecting your visitors. By taking proactive measures to prevent, detect, and respond to malware-related incidents, you can minimize the potential impact and provide a safer online experience for your users.
If you believe your website has been infected by hacktools or other malware, don’t hesitate to chat with our website security specialists. We offer quick and thorough website malware removal to help restore your site and harden it against future attacks.
如有侵权请联系:admin#unsafe.sh