2023-6-30 14:59:55 Author: blog.elcomsoft.com(查看原文) 阅读量:16 收藏
A while ago, we introduced an innovative mechanism that enabled access to parts of the file system for latest-generation Apple devices. The process we called “partial extraction” relied on a weak exploit that, at the time, did not allow a full sandbox escape. We’ve been working to improve the process, slowly lifting the “partial” tag from iOS 15 devices. Today, we are introducing a new, enhanced low-level extraction mechanism that enables full file system extraction for the iOS 16 through 16.3.1 on all devices based on Apple A12 Bionic and newer chips.
TL&DR
The previously announced partial file system extraction mechanism that, at the time, allowed low-level access to third-party app data for devices running iOS 16.0 through 16.1.2, has been refined. The enhanced process now delivers full unrestricted file system extraction (currently without a keychain) for a set of devices with iOS/iPadOS 16.0 through 16.3.1. iPhone Xs/Xr and newer devices are supported, including the iPhone 14 and 14 Pro range as well as iPad models based on the latest M1 and M2 chips.
Still no keychain (but coming soon)
We pushed this release as forensic experts do have a backlog of Apple devices with iOS 16.3.1 and older. The new extraction process enables low-level access to the file system, which includes access to sandboxed app data, system databases and other information available in the file system. We are working on bringing full keychain decryption support, which is scheduled for one of upcoming releases. We are also working on iOS 16.4 support.
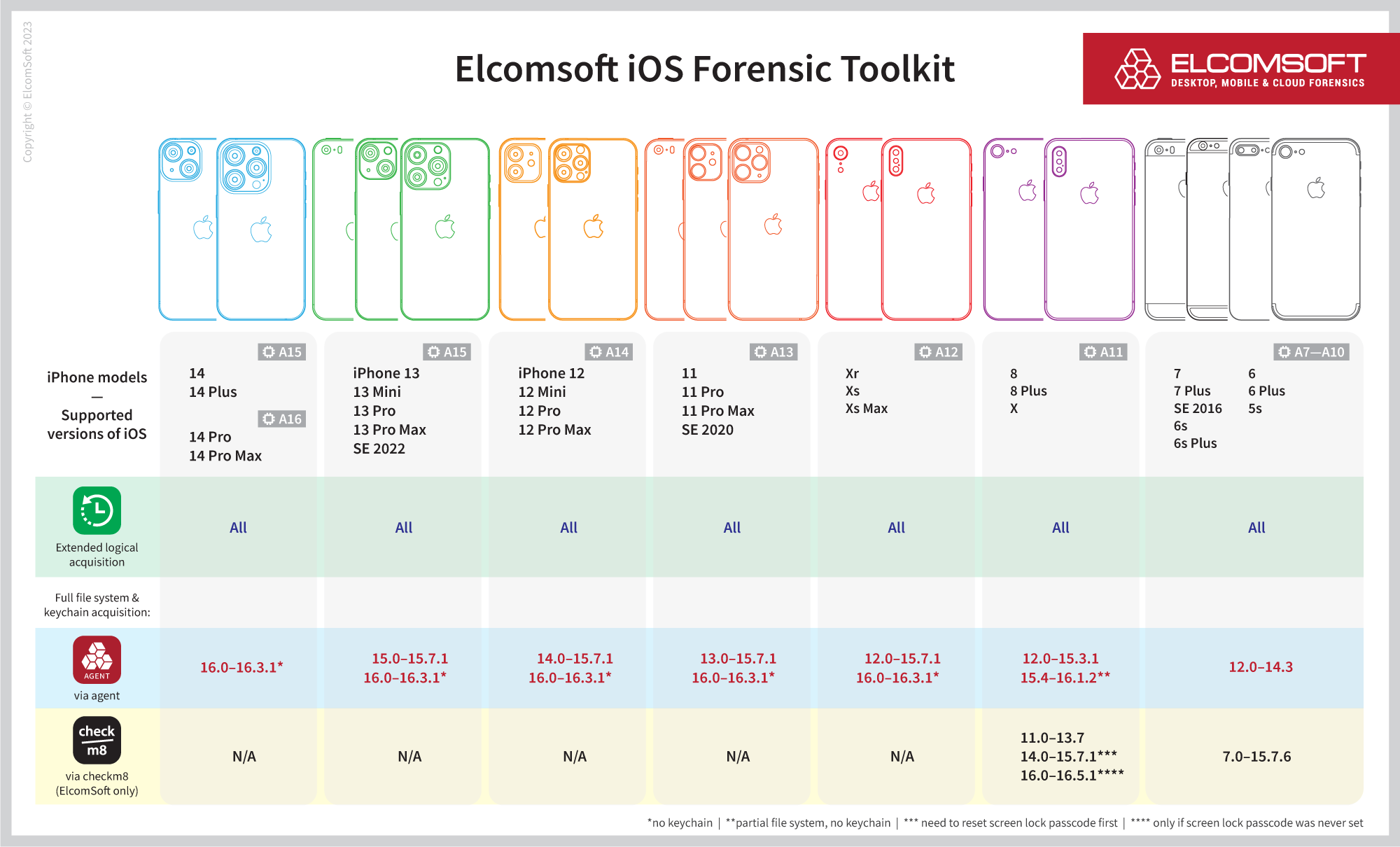
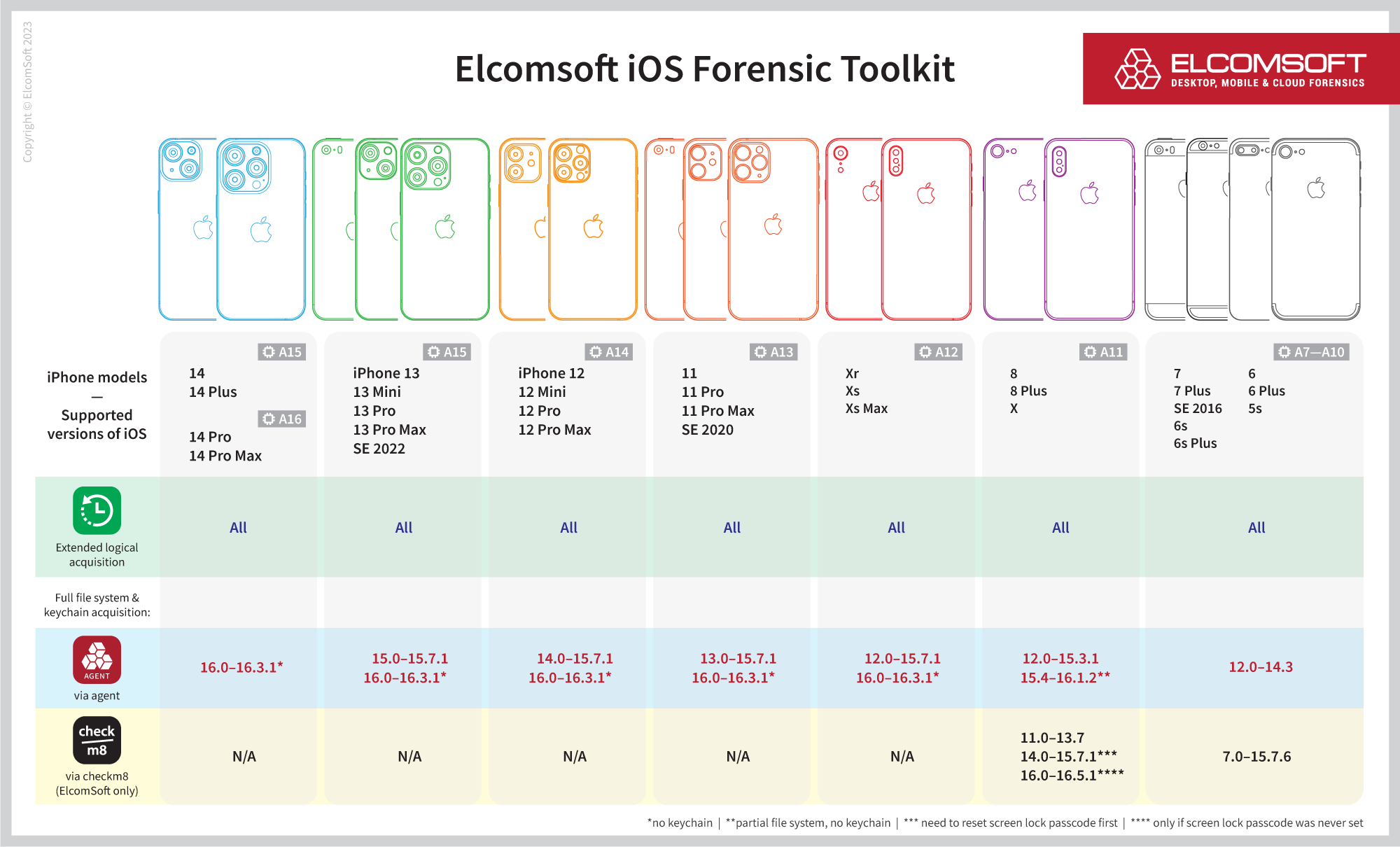
The updated compatibility matrix:
Before: partial file system extraction for iOS 16.0-16.1.2
iOS Forensic Toolkit comes with a custom low-level extraction agent. Technically, the extraction agent is an app that, when installed on an iOS device, attempts privilege escalation by attempting to exploit one or more vulnerabilities in the operating system. For the most part, the exploits used in the extraction agent are kernel-level exploits allowing full sandbox escape with low-level access to the file system and keychain records.
For a long time, no usable exploit was available for any version of iOS 16. When one was finally discovered, it turned to be a weak exploit that was not quote up to the task of enabling full access to the file system, let alone decrypt the keychain. When we initially used that exploit, we’ve been unable to fully escape the sandbox, as some protective mechanisms were still in place. As a result, we’ve been only able to offer access to parts of the file system, mostly with data of third-party apps. Obviously, that approach left many kinds of data out, so we continued our research that lead us to today’s release.
Now: full file system extraction for iOS 16.0-16.3.1
We are proud to release an update to iOS Forensic Toolkit with full file system extraction support for iOS/iPadOS 16.0 through 16.3.1. We’ve been able to fully escape the sandbox and gain access to previously inaccessible types of data, which includes the full file system. Currently, we do not support keychain decryption for these versions of iOS, but an update is coming soon.
The list of supported devices includes:
- A12: iPhone Xr, iPhone Xs, iPhone Xs Max
- A13: iPhone 11, iPhone 11 Pro, iPhone 11 Pro Max, iPhone SE (2nd gen)
- A14: iPhone 12, iPhone 12 Mini, iPhone 12 Pro, iPhone 12 Pro Max
- A15: iPhone 13, iPhone 13 Mini, iPhone 13 Pro, iPhone 13 Pro Max, iPhone SE (3rd gen), iPhone 14, iPhone 14 Plus
- A16: iPhone 14 Pro, iPhone 14 Pro Max
- All corresponding iPad models including iPad Air 5 and iPad Pro 5 (Apple M1), iPad Pro 6 (Apple M2)
Coming soon: keychain decryption and iOS 16.4 support
Certain data remains inaccessible without the complete chain of exploits. Secure messaging platforms, in particular, often necessitate specific keychain information for successful extraction. We are working hard to improve the extraction agent with additional features and expanded supported OS range. The next planned update will include iOS 16.4 support and keychain decryption for the entire iOS 16.0 – 16.4 range. Stay tuned!
Escalating complexity in iOS forensics
In an era defined by rapid technological advancements, the battle between digital security and forensic experts who seek legal access to incriminating evidence grows increasingly complex. The interplay between exploit chains, extended development timelines, and lagging support for iOS updates from vendors of forensic software poses significant challenges for both security experts and forensic specialists.
Data extraction stands as a primary stage of any forensic investigation. The success of subsequent analysis and evidence collection hinges on the effectiveness of this initial step. Therefore, it is crucial to employ reliable and comprehensive data extraction techniques.
With the advent of newer devices, starting from the iPhone 12, traditional methods for passcode recovery have become increasingly ineffective, even in high-end forensic tools. As a result, investigators must explore alternative, non-technical methods to obtain passcode information to enable access to the data. Device security measures have become increasingly complex, incorporating multiple layers of defense. Exploit chains required for bypassing these protections have grown longer, making the task of gaining access to secure devices more challenging than ever before.
There is often a significant time gap between the release of iOS versions and the availability of corresponding data extraction support from forensic tools. This delay can extend several months, impacting investigations. For example, iOS 16.3.1 supported in this release of iOS Forensic Toolkit was released on February 13th, while version 16.4 was released on March 27th. In addition to the delays in version releases, subsequent updates and patches quickly follow major iOS versions. For instance, while we are currently finalizing support for iOS 16.4, the already patched versions of iOS 16.4.1, 16.4.1a, 16.5, 16.5.1, and even a beta version 16.6 are already out. This rapid succession of updates poses ongoing challenges for forensic experts.
So what about those currently unsupported versions of iOS? For those newer iOS builds, the only viable option remains advanced logical extraction. This method allows the extraction of media files, including metadata, shared app data, and valuable diagnostic logs. However, it is important to note that this approach, while valuable, does not return many crucial bits and pieces such as email messages or conversation histories in most popular instant messaging apps.
Using the extraction agents is inherently safe for the device itself; however, it is not as clean and forensically sound as checkm8, and may compromise forensic soundness due to the alterations (however minor) introduced during extraction. However, despite not being classified as a “physical” extraction, the low-level extraction technique employed by the extraction agent yields as much data as that obtained through physical extraction methods like checkm8. We recommend exercising due caution when using this extraction method though, as installing and launching the extraction agent may require online connectivity in certain cases, which presents potential risks. We have a solution for this, which requires a Raspberry Pi device with custom firmware.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh