
2023-7-3 20:18:20 Author: www.sentinelone.com(查看原文) 阅读量:42 收藏
In partnership with vx-underground, SentinelOne recently ran its first Malware Research Challenge, in which we asked researchers across the cybersecurity community to submit previously unpublished work to showcase their talents and bring their insights to a wider audience.
Today’s post marks the start of a series highlighting the best entries, beginning with the winner from Pol Thill.
This in-depth and meticulous research into a cybercrime threat actor targeting thousands of clients of financial institutions makes a significant contribution to our understanding of the cybersecurity landscape and is the worthy winner of our challenge.

Executive Summary
- Neo_Net has been conducting an eCrime campaign targeting clients of prominent banks globally, with a focus on Spanish and Chilean banks, from June 2021 to April 2023.
- Despite using relatively unsophisticated tools, Neo_Net has achieved a high success rate by tailoring their infrastructure to specific targets, resulting in the theft of over 350,000 EUR from victims’ bank accounts and compromising Personally Identifiable Information (PII) of thousands of victims.
- The campaign employs a multi-stage attack strategy, starting with targeted SMS phishing messages distributed across Spain and other countries, using Sender IDs (SIDs) to create an illusion of authenticity and mimicking reputable financial institutions to deceive victims.
- Neo_Net has established and rented out a wide-ranging infrastructure, including phishing panels and Android trojans, to multiple affiliates, sold compromised victim data to third parties, and launched a successful Smishing-as-a-Service offering targeting various countries worldwide.
Introduction
An extensive eCrime campaign has been observed targeting clients of prominent banks around the world from June 2021 to April 2023. Notably, the threat actors have predominantly focused on Spanish and Chilean banks, with 30 out of 50 targeted financial institutions headquartered in Spain or Chile, including major banks such as Santander, BBVA and CaixaBank. Banks targeted in other regions include Deutsche Bank, Crédit Agricole and ING. A complete list can be found in Appendix A at the end of this post.
Despite employing relatively unsophisticated tools, the threat actors have achieved a high success rate by tailoring their infrastructure to their specific targets. The campaign has resulted in the theft of over 350,000 EUR from victims’ bank accounts, along with the compromise of a significant amount of Personally Identifiable Information (PII), including telephone numbers, national identity numbers, and names from thousands of victims.
The mastermind behind this operation, known as Neo_Net, has established and rented out a wide-ranging infrastructure, including phishing panels, Smishing software, and Android trojans to multiple affiliates, sold compromised victim data to interested third parties, and has even launched a successful Smishing-as-a-Service offering that targets various countries worldwide. This report will provide a detailed overview of the campaign and delve into the background of Neo_Net, shedding light on his operations over the years.
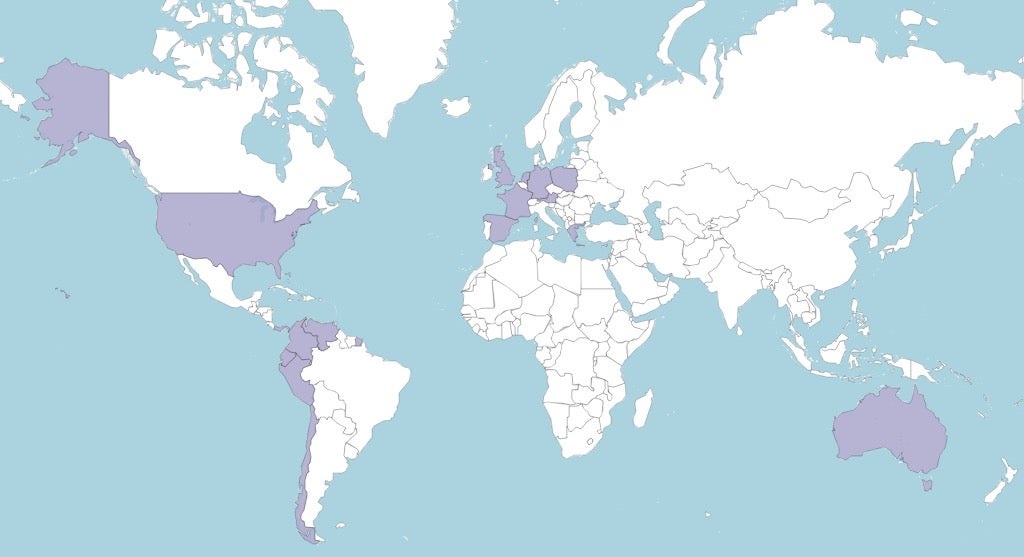
eCrime Campaign against Financial Institutions
The campaign employed a sophisticated multi-stage attack strategy that commenced with targeted SMS phishing messages distributed across Spain using Neo_Net’s proprietary service, Ankarex. These messages leveraged Sender IDs (SIDs) to create an illusion of authenticity, mimicking reputable financial institutions in an attempt to deceive the victims.
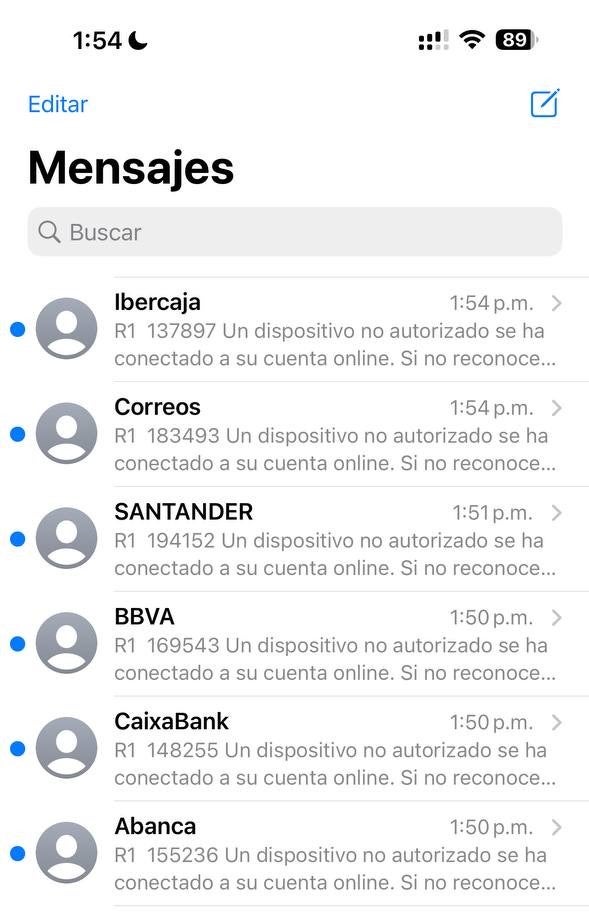
The SMS messages employed various scare tactics, such as claiming that the victim’s account had been accessed by an unauthorized device or that their card had been temporarily limited due to security concerns. The messages also contained a hyperlink to the threat actor’s phishing page.
The phishing pages were meticulously set up using Neo_Net’s panels, PRIV8, and implemented multiple defense measures, including blocking requests from non-mobile user agents and concealing the pages from bots and network scanners. These pages were designed to closely resemble genuine banking applications, complete with animations to create a convincing façade:
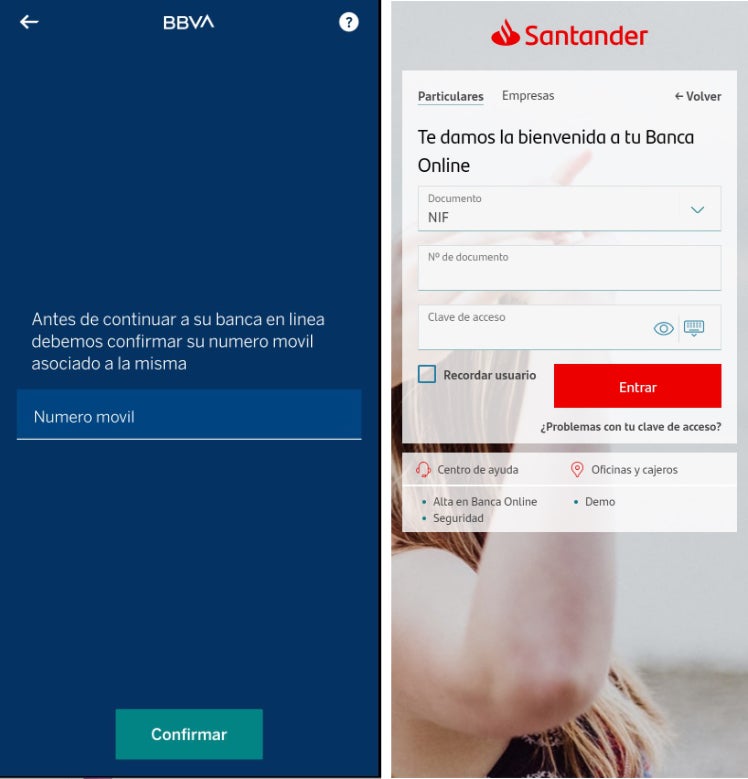
Upon submission of their credentials, the victims’ information was surreptitiously exfiltrated to a designated Telegram chat via the Telegram Bot API, granting the threat actors unrestricted access to the stolen data, including the victims’ IP addresses and user agents.
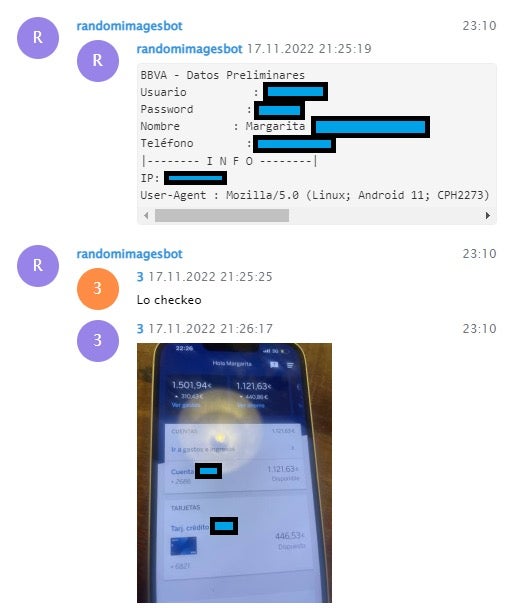
Subsequently, the threat actors employed various techniques to circumvent the Multi-Factor Authentication (MFA) mechanisms commonly employed by banking applications. One such approach involved coaxing victims into installing a purported security application for their bank account on their Android devices.

However, this application served no legitimate security purpose and merely requested permissions to send and view SMS messages.
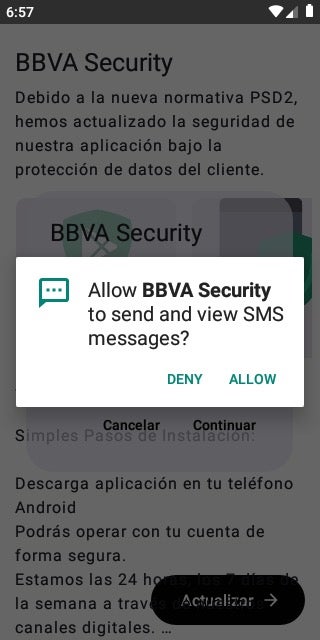
In reality, these Android trojans functioned as modified versions of the publicly available Android SMS spyware known as SMS Eye. Some threat actors further obfuscated the trojan using public packers to evade detection by anti-malware solutions. These Android trojans covertly exfiltrated incoming SMS messages to a distinct dedicated Telegram chat.
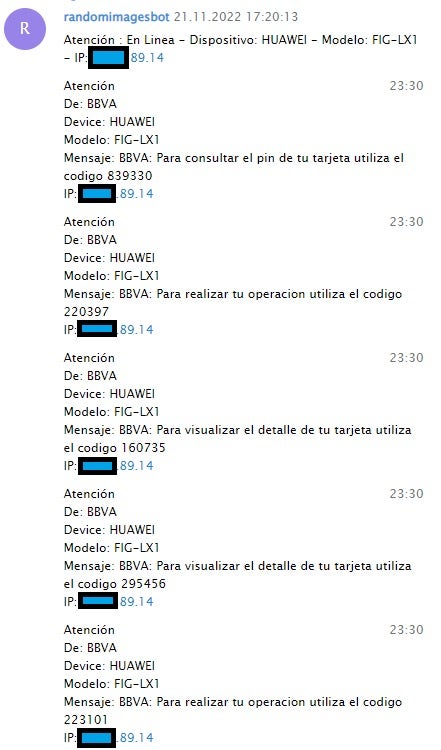
The exfiltrated messages could then be utilized to bypass MFA on the targeted accounts by capturing One-Time Passwords (OTPs). Additionally, the threat actors were also observed employing direct phone calls to victims, possibly to impersonate bank representatives and deceive victims into installing the Android spyware or divulging OTPs.
The threat actors employed this method to target clients of several prominent banks around the world.
The funds illicitly acquired from victims during the course of the year-long operation amounted to a minimum of 350,000 EUR. However, it is probable that the actual sum is significantly higher, as older operations and transactions that do not involve SMS confirmation messages may not be fully accounted for due to limited visibility.
Neo_Net
Neo_Net, the prominent actor responsible for the global cybercrime campaign, has been active in the cybersecurity landscape at least since early 2021. He maintains a public GitHub profile under the name “notsafety” and a Telegram account that showcases his work and identifies him as the founder of Ankarex, a Smishing-as-a-Service platform.
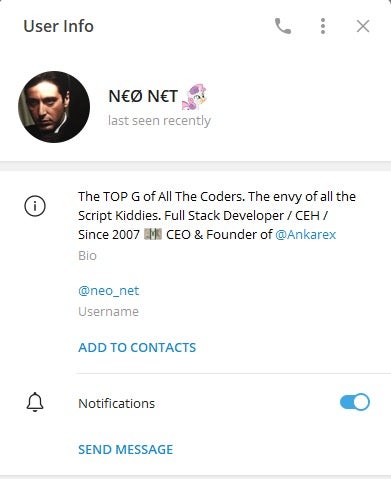
Through his contributions on Telegram, Neo_Net has been linked to the “macosfera.com” forum, a Spanish-language IT forum. Email addresses registered with the forum’s domain were found in relation to several phishing panels created by Neo_Net, targeting Spanish banks and other institutions. These email addresses were used as usernames for the panels, suggesting that Neo_Net may have collaborated with individuals from this forum to set up his infrastructure. The phishing panels also clearly indicate Neo_Net as the creator, with his signature on top of the php files.
![Fig 9: Phishing panels with links to macosfera[.]com (VirusTotal)](https://www.sentinelone.com/wp-content/uploads/2023/06/neo_net_8.jpg)
Ankarex
Neo_Net’s main creation is the Ankarex Smishing-as-a-Service platform, which has been active since at least May 2022. The Ankarex News Channel on Telegram, which advertises the service, currently has 1700 subscribers and regularly posts updates about the software, as well as limited offers and giveaways.

The service itself is accessible at ankarex[.]net, and once registered, users can upload funds using cryptocurrency transfers and launch their own Smishing campaigns by specifying the SMS content and target phone numbers. Ankarex currently targets 9 countries but has historically operated in additional regions.
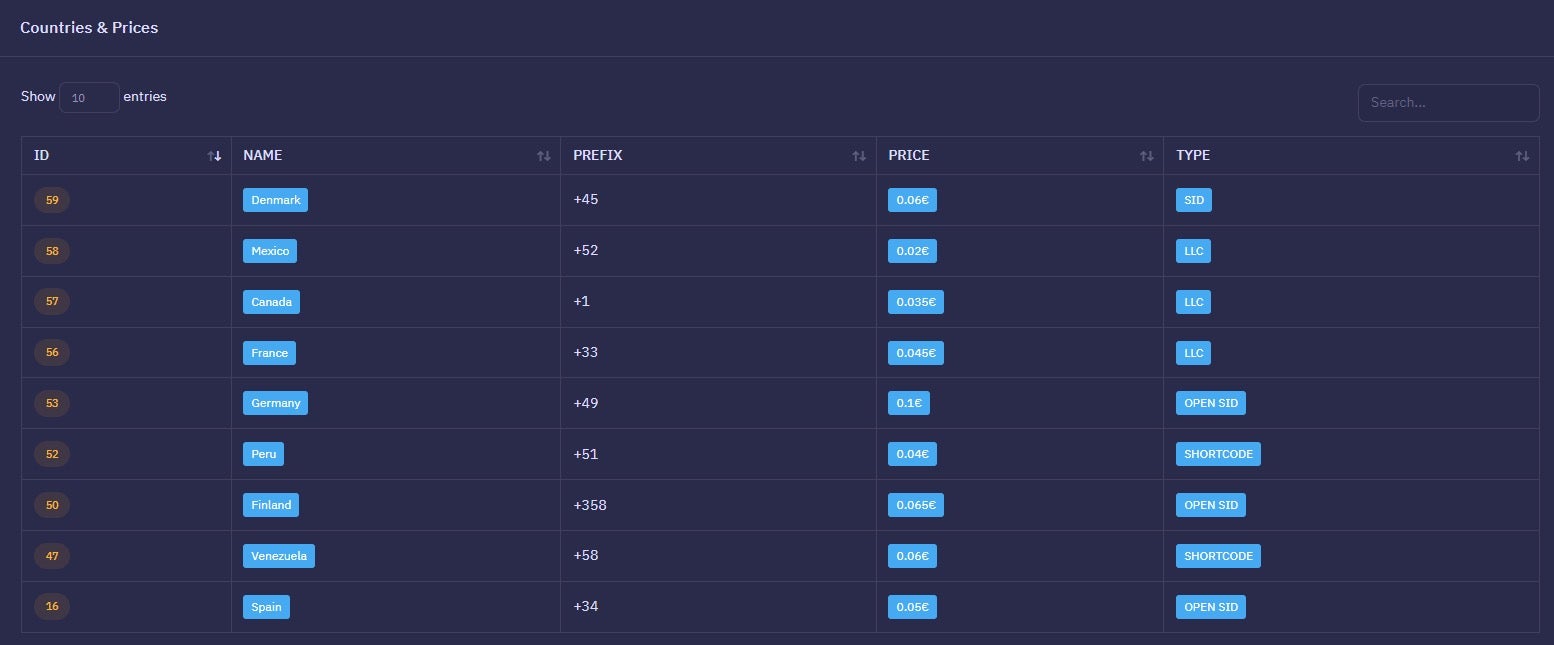
In addition to the Smishing service, Neo_Net has also offered leads, including victims’ names, email addresses, IBANs, and phone numbers for sale on the Ankarex Channel. He has also advertised his Android SMS spyware service to selected members. Notably, every channel created to exfiltrate the captured SMS messages has Neo_Net listed as an administrator, and several package names of the Android trojans allude to their creator with names such as com.neonet.app.reader. It is likely that Neo_Net rented his infrastructure to affiliates, some of whom have been observed working with him on multiple unique campaigns, allowing them to conduct phishing and funds transfers independently.

Throughout his year-long operation, Neo_Net has been traced back to several unique IP addresses, indicating that he currently resides in Mexico. Neo_Net primarily operates in Spanish-speaking countries and communicates predominantly in Spanish with his affiliates. Communication in the Ankarex channel is almost exclusively done in Spanish.
However, Neo_Net has also been observed collaborating with non-Spanish speakers, including another cybercriminal identified by the Telegram handle devilteam666. This particular operation involved the use of Google Ads targeting crypto wallet owners, and devilteam666 continues to offer malicious Google Ads services on his Telegram channel.
Conclusion
Despite employing mostly unsophisticated tools and techniques, such as simple SMS spyware and phishing panels, Neo_Net and his affiliates have managed to steal hundreds of thousands of euros and compromise the personally identifiable information (PII) of thousands of victims worldwide. The success of their campaigns can be attributed to the highly targeted nature of their operations, often focusing on a single bank, and copying their communications to impersonate bank agents. Furthermore, due to the simplicity of SMS spyware, it can be difficult to detect, as it only requires permission to send and view SMS messages.
Neo_Net has also been observed reusing compromised PII for further profit. A significant amount of eCrime against mobile users in Spain over the past two years can be directly traced back to Neo_Net’s operation, including his phishing panels, Smishing-as-a-Service platform, and Android trojans.
These campaigns highlight that while Multi-Factor Authentication is robust, it can be circumvented if it relies on SMS, and that physical tokens or external applications would provide better protection in such cases.
Acknowledgments
Special thanks go to @malwrhunterteam who posted about several samples used in this campaign on his Twitter account.
Appendix A: Targeted Financial Institutions
- Spain: Santander, BBVA, CaixaBank, Sabadell, ING España, Unicaja, Kutxabank, Bankinter, Abanca, Laboral Kutxa, Ibercaja, BancaMarch, CajaSur, OpenBank, Grupo Caja Rural, Cajalmendralejo, MoneyGo, Cecabank, Cetelem, Colonya, Self Bank, Banca Pueyo
- France: Crédit Agricole, Caisse d’Epargne, La Banque postale, Boursorama, Banque de Bretagne
- Greece: National Bank of Greece
- Germany: Sparkasse, Deutsche Bank, Commerzbank
- United Kingdom: Santander UK
- Austria: BAWAG P.S.K.
- Netherlands: ING
- Poland: PKO Bank Polski
- Chile: BancoEstado, Scotiabank (Cencosud Scotiabank), Santander (officebanking), Banco Ripley, Banco de Chile, Banco Falabella, Banco de Crédito e Inversiones, Itaú CorpBanca
- Colombia: Bancolombia
- Venezuela: Banco de Venezuela
- Peru: BBVA Peru
- Ecuador: Banco Pichincha
- Panama: Zinli
- USA: Prosperity Bank, Greater Nevada Credit Union
- Australia: CommBank
Appendix B
Indicators of Compromise
| APK SHA1 Hashes | Main Activity Name | Impersonated Institution |
| de8929c1a0273d0ed0dc3fc55058e0cb19486b3c | com.neonet.app.reader.MainActivity | BBVA |
| b344fe1bbb477713016d41d996c0772a308a5146 | com.neonet.app.reader.MainActivity | Laboral Kutxa |
| 8a099af61f1fa692f45538750d42aab640167fd2 | com.neonet.app.reader.MainActivity | Correos |
| ab14161e243d478dac7a83086ed4839f8ad7ded8 | com.neonet.app.reader.MainActivity | BBVA |
| ded2655512de7d3468f63f9487e16a0bd17818ff | com.neonet.app.reader.MainActivity | CaixaBank |
| a5208de82def52b4019a6d3a8da9e14a13bc2c43 | com.neonet.app.reader.MainActivity | CaixaBank |
| 21112c1955d131fa6cab617a3d7265acfab783c2 | com.neonet.app.reader.MainActivity | Openbank |
| 6ea53a65fe3a1551988c6134db808e622787e7f9 | com.neonet.app.reader.MainActivity | Unicaja |
| 62236a501e11d5fbfe411d841caf5f2253c150b8 | com.neonet.app.reader.MainActivity | BBVA |
| 7f0c3fdbfcdfc24c2da8aa3c52aa13f9b9cdda84 | com.neonet.app.reader.MainActivity | BBVA |
| f918a6ecba56df298ae635a6a0f008607b0420b9 | com.neonet.app.reader.MainActivity | Santander |
| ffbcdf915916595b96f627df410722cee5b83f13 | com.neonet.app.reader.MainActivity | BBVA |
| 7b4ab7b2ead7e004c0d93fe916af39c156e0bc61 | com.neonet.app.reader.MainActivity | CajaSur |
| 34d0faea99d94d3923d0b9e36ef9e0c48158e7a0 | com.neonet.app.reader.MainActivity | BBVA |
| e6c485551d4f209a0b7b1fa9aa78b7efb51be49b | com.neonet.app.reader.MainActivity | BBVA |
| 1df3ed2e2957efbd1d87aac0c25a3577318b8e2a | com.neonet.app.reader.MainActivity | BBVA |
| 6a907b8e5580a5067d9fb47ef21826f164f68f3f | com.neonet.app.reader.MainActivity | Grupo Caja Rural |
| 5d1c7ff3d16ec770cf23a4d82a91358b9142d21a | com.neonet.app.reader.MainActivity | Grupo Caja Rural |
| 86ad0123fa20b7c0efb6fe8afaa6a756a86c9836 | com.neonet.app.reader.MainActivity | Grupo Caja Rural |
| 14a36f18a45348ad9efe43b20d049f3345735163 | com.neonet.app.reader.MainActivity | Cajalmendralejo |
| b506503bb71f411bb34ec8124ed26ae27a4834b9 | com.neonet.app.reader.MainActivity | BBVA |
| afe84fa17373ec187781f72c330dfb7bb3a42483 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 445468cd5c298f0393f19b92b802cfa0f76c32d4 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 8491ff15ad27b90786585b06f81a3938d5a61b39 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 2714e0744ad788142990696f856c5ffbc7173cf4 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 1ce0afe5e09b14f8aee6715a768329660e95121e | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 96a3600055c63576be9f7dc97c5b25f1272edd2b | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 9954ae7d31ea65cd6b8cbdb396e7b99b0cf833f4 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 07159f46a8adde95f541a123f2dda6c49035aad1 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| ab19a95ef3adcb83be76b95eb7e7c557812ad2f4 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| db8eeab4ab2e2e74a34c47ad297039485ff75f22 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| dbf0cec18caabeb11387f7e6d14df54c808e441d | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 69d38eed5dc89a7b54036cc7dcf7b96fd000eb92 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| c38107addc00e2a2f5dcb6ea0cbce40400c23b49 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 279048e07c25fd75c4cef7c64d1ae741e178b35b | com.uklapon.mafin.chinpiling.actividades | Bankinter |
| ef8c5d639390d9ba138ad9c2057524ff6e1398de | BBVA | |
| e7c2d0c80125909d85913dfb941bdc373d677326 | ING | |
| 145bd67f94698cc5611484f46505b3dc825bd6cd | BancoEstado |
Phishing Domains
bbva.info-cliente[.]net
santander.esentregas[.]ga
bbva.esentregas[.]ga
correos.esentregas[.]ga
Appendix C: MITRE ATT&CK Tags
| ID | Technique | Explanation |
| T1406.002 | Obfuscated Files or Information: Software Packing | Some APK files are packed and drop the unpacked dex file once executed |
| T1633.001 | Virtualization/Sandbox Evasion: System Checks | Some APK files have been modified and initially check for common sandbox names before unpacking |
| T1426 | System Information Discovery | The Sms Eye trojan collects the brand and model of the infected phone |
| T1636.004 | Protected User Data: SMS Messages | The Sms Eye trojan collects incoming SMS messages |
| T1437.001 | Application Layer Protocol: Web Protocols | The Sms Eye trojan exfiltrates SMS messages over HTTPS |
| T1481.003 | Web Service: One-Way Communication | The Sms Eye trojan uses the Telegram Bot API to exfiltrate SMS messages |
| T1521.002 | Encrypted Channel: Asymmetric Cryptography | The C2 channel is encrypted by TLS |
| T1646 | Exfiltration Over C2 Channel | The SMS messages are exfiltrated over the C2 channel |
如有侵权请联系:admin#unsafe.sh