
2023-1-25 06:41:28 Author: sandflysecurity.com(查看原文) 阅读量:18 收藏
Sandfly 4.3.0 features an external credential provider interface. Using our new integration you can get Sandfly to work with an external key vault such as Cyberark, Thycotic, Hashicorp and more.
We have also added in new checks for process hiding, suspicious SSH process activity, cron persistence attacks plus others. Improvements have also been made to better handle containers running inside the btrfs and zfs file systems. Finally, we have major upgrades for database performance, enhanced filtering, custom views inside the UI, and improved graphing.
External Credential Provider/Key Vault Integration
Although Sandfly uses strong elliptic key cryptography to protect system credentials, customers have often wanted us to integrate with their key vault provider such as Hashicorp, Cyberark, Thycotic and others. Now, we have an ability to integrate with these solutions using a simple but innovative service module architecture.
Once integration is done, Sandfly will obtain credentials securely from your key vault and they are encrypted fully in transit so even the Sandfly server itself cannot read them at any time. Credentials are used on demand and not stored.
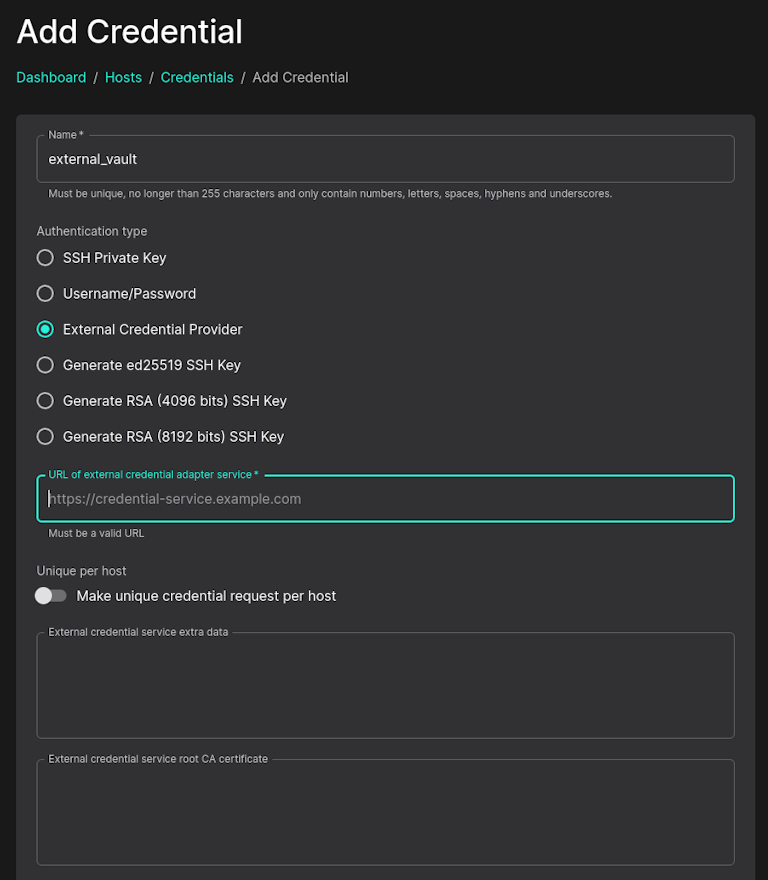
You can work with us to integrate into your key vault of choice. Please contact us for more details and help us understand your needs.
New Process Hiding, SSH, and Persistence Attacks
We have added in multiple ways to find Linux processes being concealed by attackers trying to mount a file system over the process table entry. This tactic was demonstrated by Tim Brown in a Gist disclosure and we felt it viable enough to want to detect it for customers.
We also added in several new checks for artifacts from Linux backdoor activity which can include processes left running after spawning from old SSH connections, suspicious spawned shells, and processes left with no active TTY session. These can all indicate SSH initiated backdoor or similar activity and are useful for incident response or detecting active attacks.
Finally, we put in other checks for crontab tactics including attackers trying to drop schedules into .placeholder file names. We also added new checks inside other persistence checking modules.
Process File System Directory Spoofing Attack
This tactic uses a file system mount over top of a legitimate PID under /proc. By mounting a file system over the /proc entry, an attacker can create a file system that mimics what the process would normally have on Linux, but use forged data to hide process activity and more.
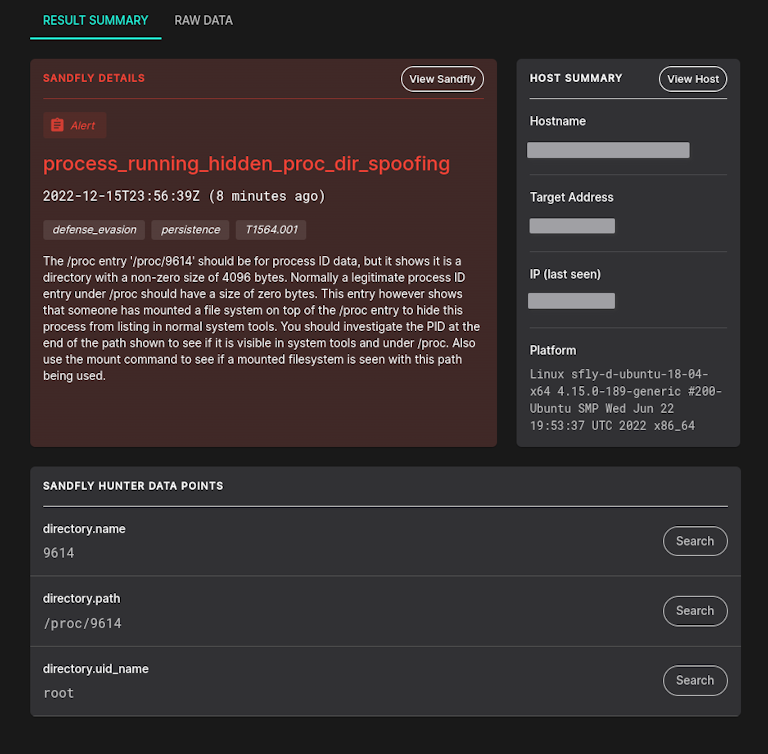
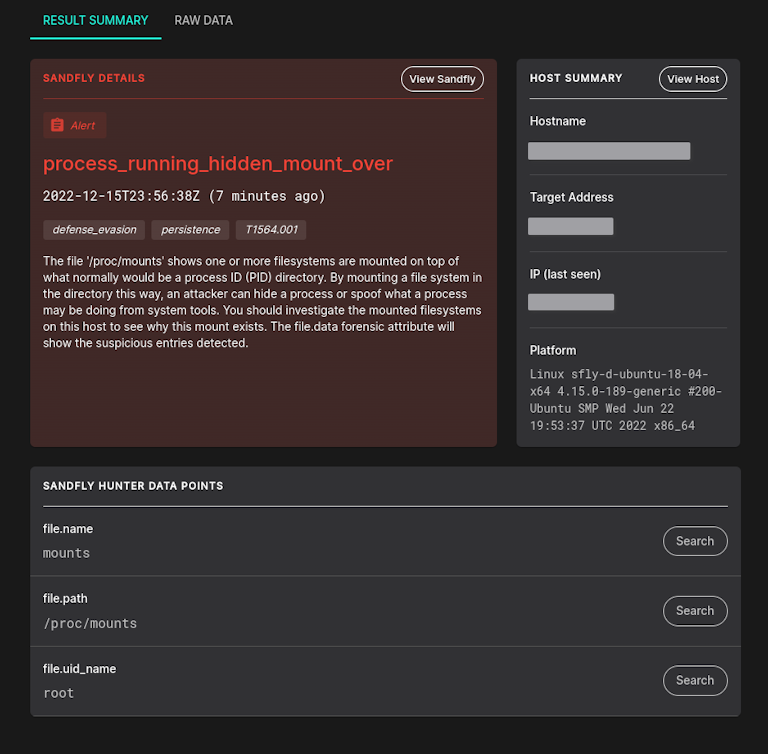
Process Mount Over Attack
Related to the above is a second artifact of the attack. Instead of flagging a directory mounted over a specific process, we'll also flag any file system mounted over portions of the /proc directory on Linux. This detection can find variants of the above attack.
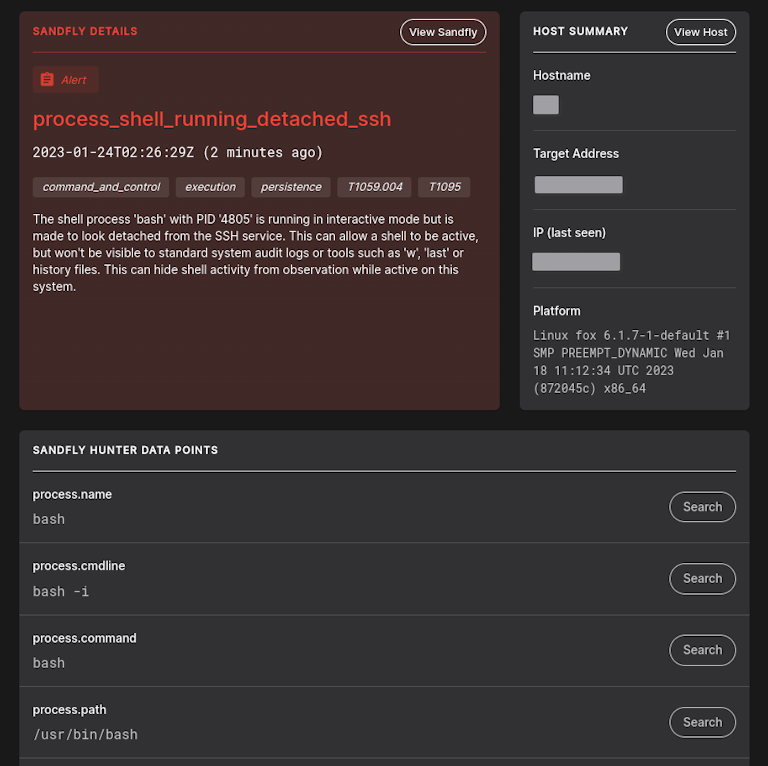
Shell Running From Detached SSH Session
Shells spawned in interactive mode (e.g. bash -i) but from a detached SSH session can hide activity on Linux. When we see a shell running in this state it is often Linux backdoor activity and will be flagged.
SSH known_hosts Under root and Default Users
The root user and default users on Linux (e.g. bin, nobody, www) are frequently targeted for attack with successful intruders then leveraging them for lateral movement. Part of this process involves using SSH which will often leave behind a known_hosts file under their respective directory. When we see a critical user like root or a default user with a known_hosts file we will flag it as an alert to investigate.
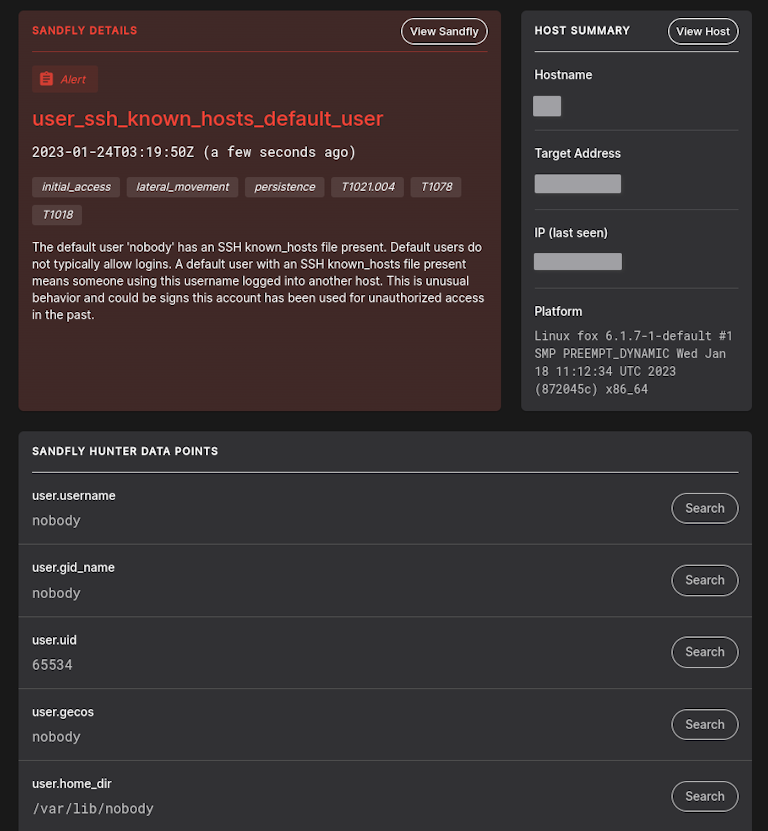
Other SSH Checks
We have added additional checks for processes left over from prior SSH sessions, those without a TTY, and more. These can be used for incident response to help identify suspicious processes spawned by SSH across systems. Customers can search for all our SSH related checks by using the filter in the sandfly list and simply searching for "ssh" in the name field.
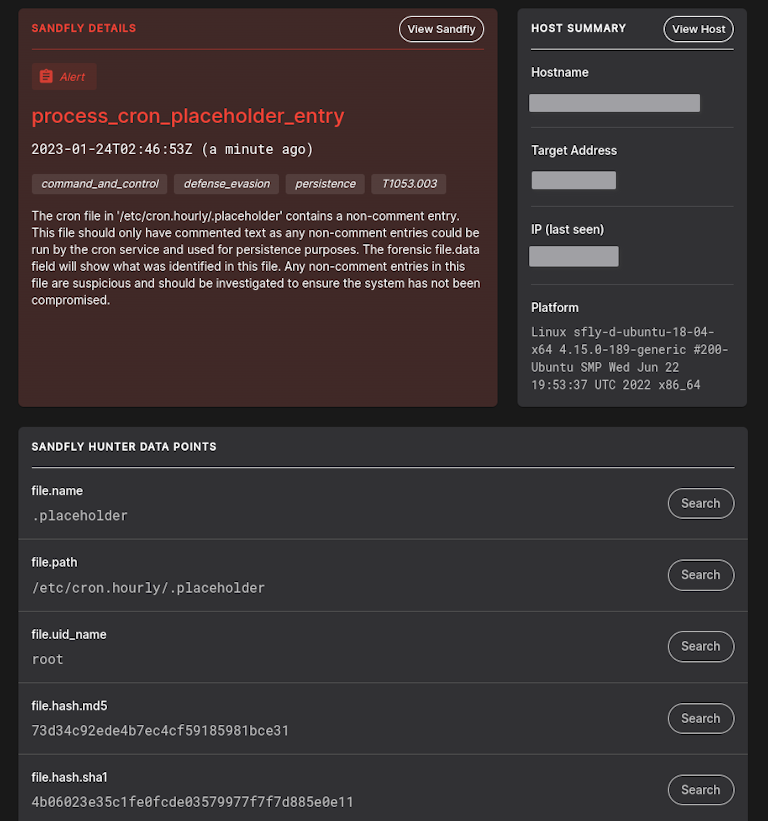
Cron Placeholder and Other Persistence Checks
We have improved and added in new checks for cron and other areas of persistence across system boot files and more. New checks include searching for non-comment entries under cron .placeholder files plus improved search patterns for other persistence attacks.
Unauthorized Account Custom Sandfly Template
By customer request, we added in a new template called user_unauthorized_account to the sandfly inventory. This template can be modified such that you can put in a list of known-good account names on your systems. It will generate an alert if a username shows up that was not in the known-good list you provided. Below we see the account for a user called php being flagged for alert that was not in the known-good list.
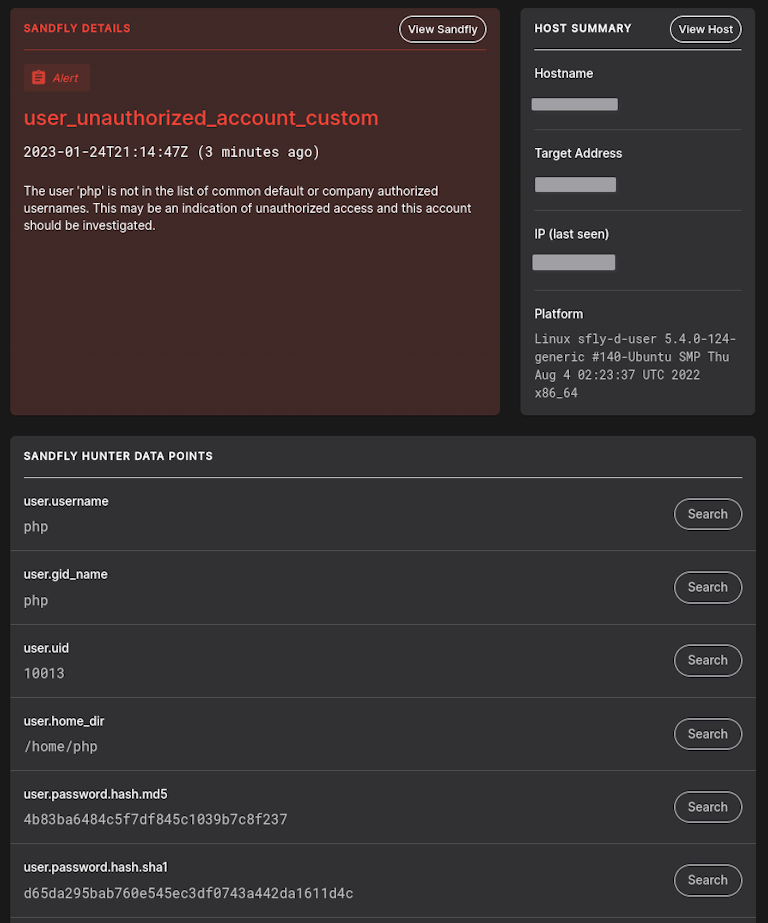
Licensed users can find this new check in the list of available templates. Customers can clone it to a new name and modify it with the usernames you choose. Activate the sandfly after cloning and it will begin running on normal schedules.
Improved Container Scanning on btrfs and zfs
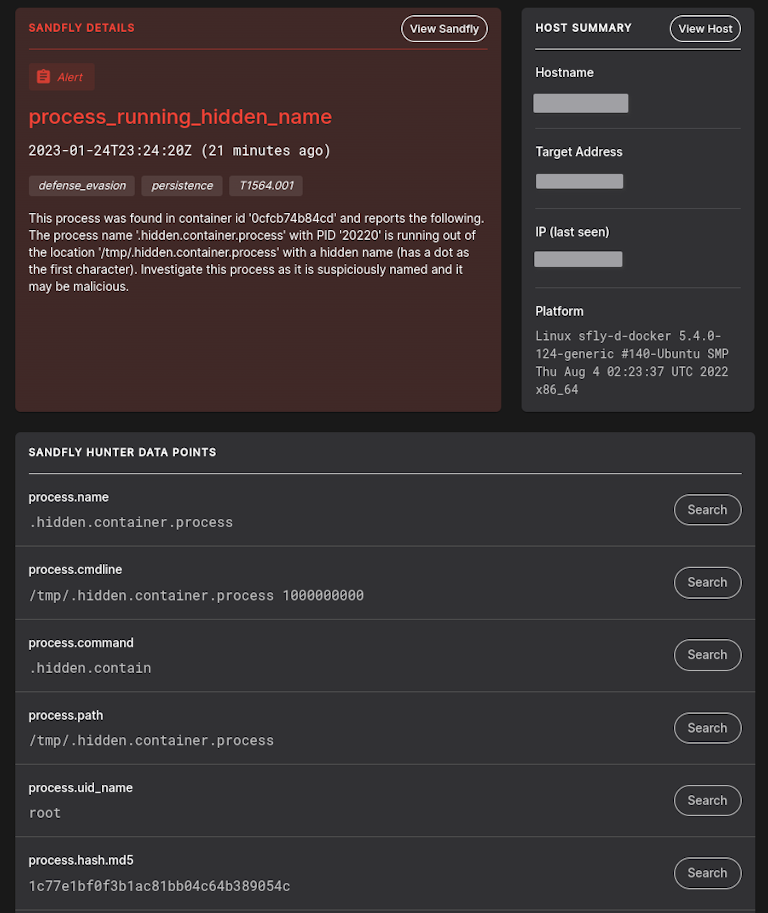
We have implemented changes to how we manage the btrfs and zfs file systems on Linux. Process and file detection engines have been updated to lower false alarm risk and provide more accurate results for containers if they are found running on these file systems.
Optimized Database Performance
We have made major optimizations to the database resulting in speed improvements for real-time statistics and more. Dashboard and result views are all faster and we can handle even higher loads than ever. Even on modest hardware, Sandfly is able to protect many thousands of Linux endpoints concurrently without loading any agents across your fleet.
UI Filtering and View Improvements
The UI has had many improvements to the search filters for results and now you can save custom views. With this new feature you can build a new filter (such as for SSH alerts like below) and save it for later use.
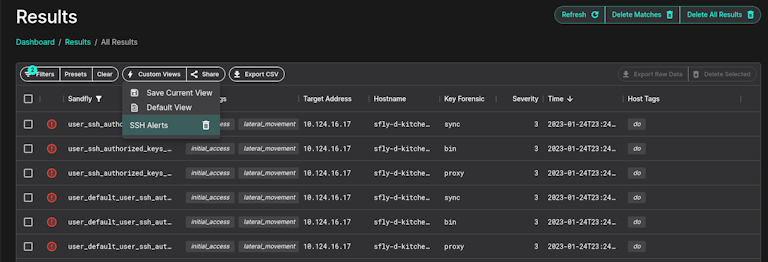
Other UI Changes
The UI has had many significant enhancements such as the following:
Improved graphing.
Timeline scrubbers optimized and improved.
Clicking on an IP address copies it to your clipboard.
Tags are now case-insensitive.
Column switches are clearer.
SSH Key Hunter timeline cleanups and optimizations.
Upgrading Sandfly
Customers wishing to upgrade can follow the instructions here:
If you have any questions, please reach out to us.
Thank you for using Sandfly.
如有侵权请联系:admin#unsafe.sh