
2023-7-31 15:0:0 Author: blog.nviso.eu(查看原文) 阅读量:68 收藏
NVISO enjoys an excellent working relationship with SANS and has been involved as Instructors and Course Authors for a variety of their courses:
- For SEC511, Continuous Monitoring and Security Operations, Maxim Deweerdt is a Certified Instructor
- For SEC575, iOS and Android Application Security Analysis and Penetration Testing, Jeroen Beckers is the Course Author
- For SEC598, Security Automation for Offense, Defense, and Cloud, Jeroen Vandeleur is the Course Author
- For SEC599, Purple Team Tactics & Kill Chain Defenses, Michel Coene is a Certified Instructor and Erik Van Buggenhout is the Course Author
- For SEC699, Purple Team Tactics – Adversary Emulation for Breach Prevention & Detection, Erik Van Buggenhout is the Course Author
As technology continues to evolve, so do the tactics and techniques used by cyber criminals. This means that staying up to date as a red team operator is crucial for protecting customers against the constantly changing threat landscape. Red team operators are tasked with simulating real-world attacks on a customer’s system to identify weaknesses and vulnerabilities before they can be exploited by malicious actors. By staying informed about the latest attack methods and trends, red team operators can provide more effective and relevant testing that accurately reflects the current threat landscape. Additionally, keeping up with emerging technologies and security measures can help red team operators develop new tactics and strategies to better protect customers from potential cyberattacks.
While red teams are primarily responsible for simulating attacks and identifying vulnerabilities, blue teams play a critical role in defending against these attacks and protecting an organization’s assets. Attending trainings that are typically attended by red teams can provide valuable insights and knowledge that blue teams can use to better defend their organization. By understanding the latest attack methods and techniques, blue teams can develop more effective defense strategies, identify potential vulnerabilities and patch them before they can be exploited by attackers. Additionally, attending these trainings can help blue teams better understand the tactics and tools used by red teams, allowing for more effective collaboration and communication between the two teams. Overall, attending red team training can help blue teams stay informed and prepared to defend against the constantly evolving threat landscape.
TL;DR;
If you do not have much time at hand, do not worry, the following tables may provide you a quick overview:
| Certification Name | Beginner | Intermediate | Expert |
|---|---|---|---|
| Red Team Ops (CRTO1) | 🔑 | ||
| Red Team Ops II (CRTO2) | 🔑 | ||
| Certified Red Team Professional (CRTP) | 🔑 | ||
| Certified Red Team Expert (CRTE) | 🔑 | ||
| Certified Red Team Master (CRTM) | 🔑 | ||
| Certified Az Red Team Professional (CARTP) | 🔑 |
Disclaimer:
It is important to note that the certifications and trainings included in the review are not an exhaustive list of all the options available and are not in a specific order.
While the ones highlighted in the review are all excellent and worth considering, there may be other certifications and trainings that could also be beneficial for your specific needs and goals.
It is always essential to do your own research and carefully consider your options before deciding. Ultimately, the best certification or training for you will depend on your individual circumstances, interests, and career aspirations.
Certifications
Red Team Ops – CRTO1
The Red Team Ops 1 course is a very well done certification that teaches you the basic red team operator principles, adds handy tools for the beginning and shows techniques you will use as a red team operator.
You will learn how to start and configure the team server (in the course of the certification Cobalt Strike from FORTRA) as well as how to manage the listeners and touch the base of payload generation.
The certification is a must for beginners who want to learn how to go from the initial compromise, to moving laterally and in the end take over the whole domain.
Of course, Microsoft Defender (not Defender ATP/MDE), application whitelisting are also part of the course to prepare you for the much-needed evasion in the customer environments by using the artifact and resource kit available with Cobalt Strike.
Who should take this course?
If you are new to the game, this course is made for you! If you already have infrastructure security assessment experience, this course adds new attack paths to your inventory and includes some important tips for OPSEC which is a lot different in red team engagements to what you are known from an internal security assessment, where stealth is optional.
I enjoyed the exam a lot and in comparison to the price of SANS certifications, this is also a great opportunity for someone with a tighter budget, thanks Zeropoint Security!
Associated costs
365 GBP = 415,32 EUR = 452,89 USD (as of 04/04/2023)
The price includes the course materials as well as a voucher for the first exam attempt.
The RTO lab is sold as a subscription to those who have purchased the course.
The price is 20/40/60 GBP per month for 40/80/120 hours of runtime respectively.
Red Team Ops II – CRTO2
The Red Team Ops 2 course aims to build on the foundation of the Red Team Ops course in order to help you improve your OPSEC skills and show you ways to bypass more defense mechanisms.
Important to note here is, that this course is NOT a newer version or replacement of the first course.
The course will introduce the concept of public redirectors and rewrite rules to you, which can then be applied in the wild.
To help you understand the evasion techniques, some common Windows APIs are being covered as well as P/Invoke and D/Invoke which allow you to dynamically invoke unmanaged code and avoid API hooks.
Other indicators such as RWX memory regions and suspicious command lines will be treated with PPID and Command Line Spoofing.
Since Microsoft upped their game for security quite a bit, the Attack Surface Reduction should not be missed out on and as such is also included in this course with examples of how to bypass a subset of the default rules.
If you have struggled with Applocker in the past, welcome to the game. The bigger brother “Windows Defender Application Control (WDAC)” is waiting for you and allows the blue team to even better protect the environment.
The cherry on top of the course is the chapter treating different types of EDR hooks, syscalls and how to integrate goodies into the artifact kit.
Who should take this course?
If you already have completed the Red Team Ops 1 course this is a great addition to extend the knowledge gathered in the first round. In more mature environments you will face WDAC, EDRs from different providers and better blue team responses. Similar to the first course the price is very attractive and the hands-on experience in a lab and not just on paper is worth every dime.
If you think you already cover the first course with your knowledge, you can also jump to this one directly. The exam can cover parts of the first course to allow reconnaissance and privilege escalation/lateral movement, so I would not recommend going for CRTO2 without prior red teaming knowledge.
Associated costs
399 GBP = 453,86 EUR = 495,07 USD (as of 04/04/2023)
The price includes the course materials as well as a voucher for the first exam attempt.
The RTO II lab is sold as a subscription to those who have purchased the course.
The price is 15 GBP per month for 40 hours of runtime.
Certified Red Team Professional (CRTP)
The Certified Red Team Professional (CRTP) course provides you with a hands-on lab environment with multiple domains and forests to understand and practice cross trust attacks. This allows you to learn and understand the core concepts of well-known Windows and Active Directory attacks which are being used by threat actors around the globe.
Windows tools like PowerShell and others off the shelf features are being used for attacks to try scripts, tools and new attacks in a fully functional AD environment.
At the time of this blog post, the lab makes use of Microsoft Windows Server 2022 and SQL Server 2017 machines.
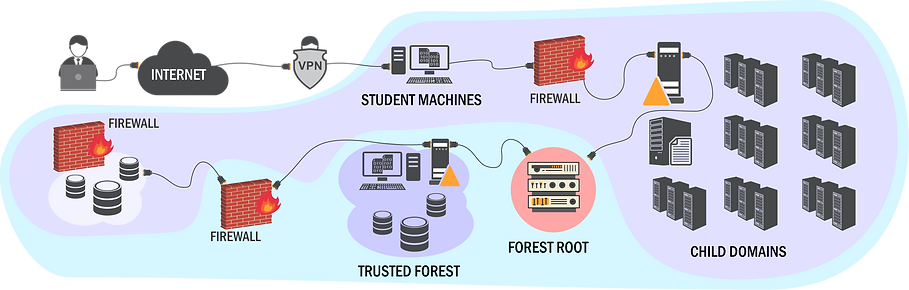
Who should take this course?
If you are new to topics like Active Directory enumeration, how to map trusts of different domain, escalate privileges via domain attacks or Kerberos-based attacks like golden and silver tickets, this course is a good bet.
Additionally, the SQL server trusts and defenses as well as bypasses of defenses are covered.
Associated costs
The price depends on the practice lab access time that is bought:
30 Days – LAB ACCESS PERIOD – 249 USD ~ 227,58 EUR (as of 05/04/2023)
60 Days – LAB ACCESS PERIOD – 379 USD ~ 346,40 EUR (as of 05/04/2023)
90 Days – LAB ACCESS PERIOD – 499 USD ~ 456,08 EUR (as of 05/04/2023)
The course mentions the following content:
23 Learning Objectives, 59 Tasks, >120 Hours of Torture
https://www.alteredsecurity.com/adlab
Please keep in mind, that the certificate has an expiry time of three years and then needs to be renewed.
Certified Red Team Expert (CRTE)
After completing the Certified Red Team Professional (CRTP) you might be looking to explore more of Microsoft features that can be implemented in customer environments. This course will allow you to play with the Local Administrator Password Solution (LAPS), Group managed service accounts (gMSA) and the Active Directory Certificate Service (AD CS).
As customers often have resources in the cloud as well, Azure AD Integration (Hybrid Identity) and the attack paths therefore are presented in this course as well.
The person taking the course will learn to understand implemented defenses and how to bypass, for example: Just Enough Administration (JEA), Privileged Access Workstations (PAWs), Local Administrator Password Solution (LAPS), Selective Authentication, Deception, App Allowlisting, Microsoft Defender for Identity and more.
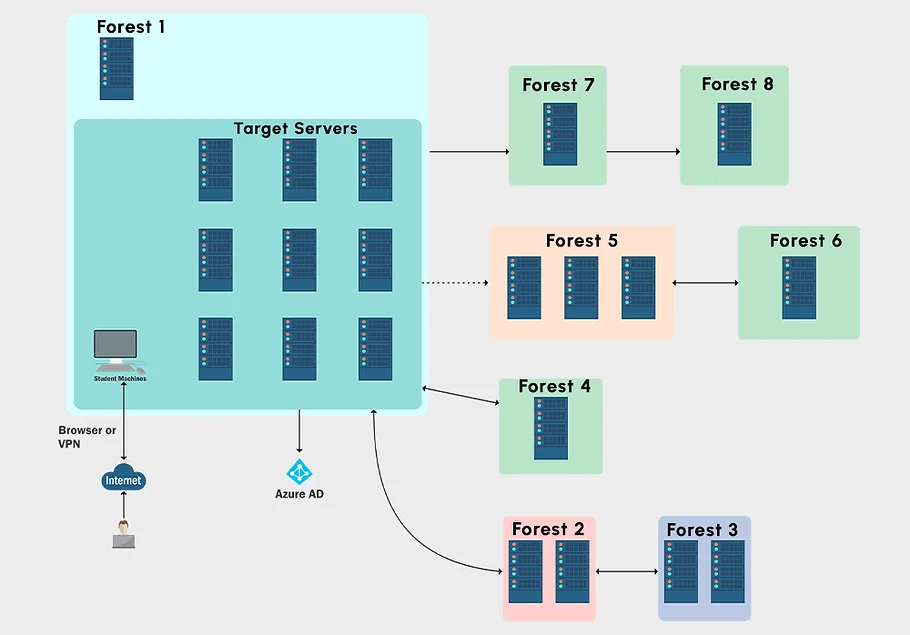
Who should take this course?
If you feel ready to dive into the more advanced defense mechanisms mentioned above, this course will certainly help you to identify these in an environment and navigate in a more mature environment covertly.
Associated costs
The price depends on the practice lab access time that is bought:
30 Days – LAB ACCESS PERIOD – 299 USD ~ 273,28 EUR (as of 05/04/2023)
60 Days – LAB ACCESS PERIOD – 499 USD ~ 456,08 EUR (as of 05/04/2023)
90 Days – LAB ACCESS PERIOD – 699 USD ~ 638,87 EUR (as of 05/04/2023)
The course mentions the following content:
28 Learning Objectives, 62 Tasks, >300 Hours of Torture
https://www.alteredsecurity.com/redteamlab
Please keep in mind, that the certificate has an expiry time of three years and then needs to be renewed.
Certified Red Team Master (CRTM)
The goal of this course is to compromise multiple forests with a minimal footprint, while gaining full control over the starting/home forest.
As consulting is more than just attacking infrastructure, the course also includes the submission of a report that contains details of attacks on target forests and details of security controls/best practices implemented on the starting/home forest.

Who should take this course?
I would suggest this course if you want to put your technical knowledge to the test while also taking a step behind the lines of a blue team, as you need to document details of the security controls in place and how they could be mitigated best. This will help you to grow in the long term and make it possible to think like a defender in order to improve your evasion techniques.
Associated costs
The price depends on the practice lab access time that is bought:
30 Days – LAB ACCESS PERIOD – 399 USD ~ 364,68 EUR (as of 05/04/2023)
60 Days – LAB ACCESS PERIOD – 599 USD ~ 547,47 EUR (as of 05/04/2023)
90 Days – LAB ACCESS PERIOD – 749 USD ~ 684,57 EUR (as of 05/04/2023)
The course mentions the following content:
46 Challenges and >450 Hours of Torture
https://www.alteredsecurity.com/gcb
Please keep in mind, that the certificate has an expiry time of three years and then needs to be renewed.
Certified Az Red Team Professional (CARTP)
The Azure Active Directory is nowadays often used as an Identity and Access Management platform using the hybrid cloud model. It also allows on-prem Active Directory applications and infrastructure to be connected to the Azure AD. This step brings some very interesting opportunities to the plate, but with these also risks.
When talking about red teaming and penetration testing, these risks can be mapped onto the following phases: Discovery, Initial access, Enumeration, Privilege Escalation, Lateral Movement, Persistence and Data exfiltration. All of these phases are covered in the course. The most value for the customers results from not just identifying and abusing vulnerabilities in the environment, but also making clear suggestions for mitigations that can be implemented in the short or long term in the customer environment.

Who should take this course?
If you are a security professional trying to strengthen your skills in Azure cloud security, Azure Penetration testing or Red teaming in Azure environments, this is the right course for you!
Associated costs
The price depends on the practice lab access time that is bought:
30 Days – LAB ACCESS PERIOD – 449 USD ~ 410,38 EUR (as of 05/04/2023)
60 Days – LAB ACCESS PERIOD – 649 USD ~ 593,17 EUR (as of 05/04/2023)
90 Days – LAB ACCESS PERIOD – 849 USD ~ 775,97 EUR (as of 05/04/2023)
The course mentions the following content:
26 Learning Objectives, 77 tasks, 7 Live Azure Tenants, >140 hours of fun!
https://www.alteredsecurity.com/azureadlab
Please keep in mind, that the certificate has an expiry time of three years and then needs to be renewed.
Trainings
Malware on Steroids
https://0xdarkvortex.dev/training-programs/malware-on-steroids/
The course is dedicated to building your own C2 Infrastructure and Payload. To achieve that, an introduction towards Windows Internals which is followed by a full hands-on experience on building your own Command & Control architecture with different types of Initial Access payloads and their lifecycle such initial access, in-memory evasions, different types of payload injections including but not limited to reflective DLLs, shellcode injection, COFF injections and more, is being offered.
The course is offered in a time span of 4 days with 6-7 hours per day in an online interactive environment.

Who should take this training?
If you always wanted to write your own C2 and create a dropper and stagers in x64 Assembly, C this course is perfect for you. Please keep in mind, that fundamental knowledge of programming with C/C++/Python3 and the familiarity with programming concepts such as pointers, references, addresses, data structures, threads and processes is listed as a requirement.
Associated costs
2,500 USD ~ 2281,95 EUR (as of 05/05/2023)
The price includes a certificate of completion, all the training materials including course PDFs/slides, content materials, source code for payloads and a python3 C2 built during the training program.
SEC565: Red Team Operations and Adversary Emulation
https://www.sans.org/cyber-security-courses/red-team-operations-adversary-emulation/
The SEC565 is one of the courses where you get to not only improve your technical abilities to abuse vulnerabilities, but also improve your skills around the whole engagement from planning to making sure the work you deliver follows a high quality and the best benefit for the customers.
The focus of the course is to learn how to plan and execute end-to-end Red Teaming engagements that leverage adversary emulation, including the skills to organize a Red Team, consume threat intelligence to map against adversary tactics, techniques, and procedures (TTPs), emulate those TTPs, report and analyze the results of the Red Team engagement, and ultimately improve the overall security posture of the organization.
The in person course is 6 days long for a reason. From planning the emulation to infrastructure and learning about initial access and persistence, the active directory attacks and ways to move from one compromised host to another is also included. As a red team documenting the abused vulnerabilities and obtaining the requested objectives is very important and therefore has a dedicated time slot as well.
The last block will contain a capture the flag red team lab consisting of 3 domains which includes Windows servers, workstations and databases as well as the active directory infrastructure to test the skills you learned earlier.
Who should take this course?
Defensive security professionals to better understand how Red Team engagements can improve their ability to defend by better understanding offensive methodologies, tools, tactics, techniques, and procedures.
Offensive security professionals looking to improve their craft and also improve their methodology around the technical part of the engagement (adversary emulation plan, safe sensitive data exfiltration, planning for retesting and more).
Associated costs
The course is being offered On-Demand (Online) and In Person.
The On Demand course is 8,275 USD ~ 7534.24 EUR (as of 02/05/2023)
The In Person course is priced at 7,695 EUR + OnDemand Bundle (785 EUR) = 8,480€ (as of 02/05/2023)
SEC699: Purple Team Tactics – Adversary Emulation for Breach Prevention & Detection
The SEC699 is one of the more unique courses where you get detailed insights into both red & blue team.
The course contents have been created by both blue teamers and red teamers and that is reflected in the detail of the course material.
The focus of the course is to learn how to emulate threat actors in a realistic enterprise environment and how to detect those actions.
As a proper purple teaming needs to follow a proper process, suitable tooling and planning, the course makes sure that these important parts are not missing. In-depth techniques such as Kerberos Delegation attacks, Attack Surface Reduction / AppLocker bypasses, AMSI, Process Injection, COM Object Hijacking and many more are being executed during the course and in order to grow on the challenge you will build SIGMA rules to detect these techniques.
Who should take this course?
Defensive security professionals looking to gain insights in the actual operation of carrying out attacks to understand the perspective of an attacker: Which tools are being used? What does a C2 setup look like? How does an attacker communicate with the C2 infrastructure? How can I use automation to my advantage?
Offensive security professionals looking to gain insights in logging & monitoring, which footprint and events are being generated using specific techniques and how the operational security can be improved to stay stealthier.
Associated costs
The course is being offered On-Demand (Online) and In Person.
The On Demand course is 7,785 USD ~ 7148.73 EUR (as of 04/04/2023)
The In Person course is priced at 7,170 EUR + OnDemand Bundle (785 EUR) = 7,955€ (as of 04/04/2023)
RED TEAM Operator: Malware Development Essentials
Malware, similar to software you use every day, has to be developed, and this course guides you through it.
Starting with what malware development is and how PE files are being structured, it helps you to understand how to encode and encrypt your payloads as well as how to store them inside a PE file.
Remote process injection as well as using an existing binary to backdoor is also being explained with hands-on code examples to follow and customize.
Who should take this training?
If you are getting started with developing your own loaders and stagers, this course is awesome to get the fundamentals right and gives you customizable source code that you can improve and build upon.
Associated costs
199 USD ~ 181,64 EUR (as of 05/04/2023)
A virtual machine with a complete environment for developing and testing your software, and a set of source code templates are included in the price.
RED TEAM Operator: Malware Development Intermediate
After the course “RED TEAM Operator: Malware Development Essentials” you might be wondering where to go next. This course uses the build foundation to extend the tooling with more code injection techniques, how you can build your own custom reflective binary as well as how to hook APIs in memory to monitor or evade functions.
Sooner or later, you have to migrate between processes that have loaded your shellcode so the section on how to migrate between 32- and 64-bit processes comes to the rescue. Finally, the course guides you on how to use IPC to control your payloads.
Who should take this training?
If you completed the course “RED TEAM Operator: Malware Development Essentials” and you are ready to take your skills to the next level, this course helps you to extend the kit you built in the first course.
Associated costs
229 USD ~ 209,03 EUR (as of 05/04/2023)
A virtual machine with a complete environment for developing and testing your software, and a set of source code templates are included in the price.
RED TEAM Operator: Malware Development Advanced – Vol.1
As the name of the course suggests, after the essentials and the intermediate course, the advanced course will teach you how to enumerate processes the modules and handles in order to identify a suitable process for injection. Payloads can not only be hidden in PE files and, as such, the course covers how to hide payloads in different parts of the NTFS, in the registry and in memory.
It demonstrates how any API (with any number of params) in a remote process can be called by using a custom “RPC” and how exception handlers can be abused.
You will learn how to build, parse, load and execute COFF objects in memory and much more.
Who should take this training?
After completing the Essentials and Intermediate course of the malware development series of Sektor7, I can only recommend this training to further strengthen your knowledge of how the Windows internals work and give you ideas for how to exploit them in the future.
Associated costs
239 USD ~ 218,15 EUR (as of 05/04/2023)
A virtual machine with a complete environment for developing and testing your software, and a set of source code templates are included in the price.
Corelan “BOOTCAMP” – stack exploitation
One thing to start with, the 2021 edition of the course is based on Windows 10/11 and contains an introduction to x64 stack-based exploitation in case you care for up-to-date material and operating systems.
Although the training is based on Windows 10/11, you have to start with the fundamentals by explaining the basics of stack buffer overflows and exploit writing.
The training provides you with a solid understanding of current stack-based exploitation techniques and memory protection bypass techniques. The training provider mentions that the course material is kept updated with current techniques, previously undocumented tricks and techniques, and details about research that was performed by the training author.
A small excerpt of the training contents:
- The x86 environment
- Stack Buffer Overflows
- Egg hunters
- ASLR
- DEP
- Intro to x64 stack-based exploitation
Who should take this training?
If you do like challenges, this training is for you. Anyone interested in exploit development or analysis is the target audience of this training.
The training itself does not provide solutions for any of the exercises that you will work through but instead provides help either during the course or after the course (via the student-only support system).
Associated costs
The In-Person training is listed at 2,500 EUR + 525 EUR VAT.
At the time of 05/04/2023 this is equal to 2738,89 USD + 575,17 USD VAT.
The path I chose to walk on
I started as a penetration tester / security consultant with a lot of self gained knowledge from home projects ranging from active directory setups at home to self built network attached storage and this helped me to have a good base with how to debug problems and general operating system usage.
During my security consulting path I then chose to start with the Offensive Security Certified Professional (OSCP) certification as this allowed me to understand some basic exploitation techniques and also get in contact with report writing and evidence collection.
Then there was a slight change in paths for dedicating my life to mobile security, but I always kept an eye on infrastructure security and did some projects in the mix.
After some years in the field, I knew I wanted a new challenge and decided to complete my CRTO1 certification.
I approached NVISO and after joining and the first larger projects I was hungry for more and completed my CRTO2 certification.
There are so many more trainings I have on my list, so keep it coming!
Education at NVISO
ARES assembles highly skilled expert professionals. This pool consists of people having 5+ years of experience in penetration testing and red team exercises, as well as blue team experts with knowledge on threat hunting and SOC operations.
The ARES team together currently holds the following certifications:
- GPEN / GRID / GXPN / GCTI / GDAT / GCIA / GMOB
- OSCP / OSEP / OSED / OSEE / OSWE / OSCE
- CRTO1 / CRTO2
- CRTP / CRTE / PACES / CARTP
- eCPPTv2 / eWPTXv2

Our ARES team at NVISO is dedicated to offer red team services to customers around the globe in order to identify gaps in the incident and response handling to improve the security posture of the companies many of us interact with daily.
See the ARES homepage for more information.

Steffen Rogge
Steffen is a Cyber Security Consultant at NVISO, where he mostly conducts Purple & Red Team assessments with a special focus on TIBER engagements.
This enables companies to evaluate their existing defenses against emulated Advanced Persistent Threat (APT) campaigns.
如有侵权请联系:admin#unsafe.sh