2023-8-8 07:23:13 Author: www.horizon3.ai(查看原文) 阅读量:19 收藏
A key differentiator of the NodeZero platform is that it autonomously navigates through your environment, choosing which exploit to run next depending on what it encounters, just as a threat actor does. It’s dynamic, not prescripted.
Here is the detailed description of a NodeZero autonomous attack that leveraged two weaknesses to achieve domain compromise in 33 minutes, 9 seconds.
NodeZero:
- Details each step in the attack path and lets you drill down to the specifics
- Provides proof of its exploits, meaning there are no false positives
- Prioritizes weaknesses and their impact to your organization, so you know what to fix first
- Guides your remediation, with fix actions for each weakness
- Identifies systemic issues to help you eliminate numerous weaknesses with a single change
In this attack path, these are the steps NodeZero took to compromise the domain.
NodeZero was launched from host 10.0.222.200
NodeZero discovered the host 10.0.4.4.
NodeZero discovered the Java service on 10.0.4.4 port 1099
NodeZero discovered H3-2020-0022: Insecure Java JMX Configuration affecting the Java service on 10.0.4.4 port 1099
The C:\Windows\win.ini file was retrieved via the RCE vulnerability
NodeZero loaded a Remote Access Tool on host 10.0.4.4 to enable post-exploitation of H3-2020-0022: Insecure Java JMX Configuration
NodeZero leveraged the Remote Access Tool running as administrator on 10.0.4.4 to discover H3-2021-0042: Credential Dumping – Security Account Manager (SAM) Database
NodeZero discovered an NTLM Hash for cbr-user by exploiting H3-2021-0042: Credential Dumping – Security Account Manager (SAM) Database
NodeZero discovered Domain Controller 10.0.4.1 (dc01.pod04.h3airange.internal)
NodeZero discovered the SMB service on domain controller 10.0.4.1 (dc01.pod04.h3airange.internal) port 445
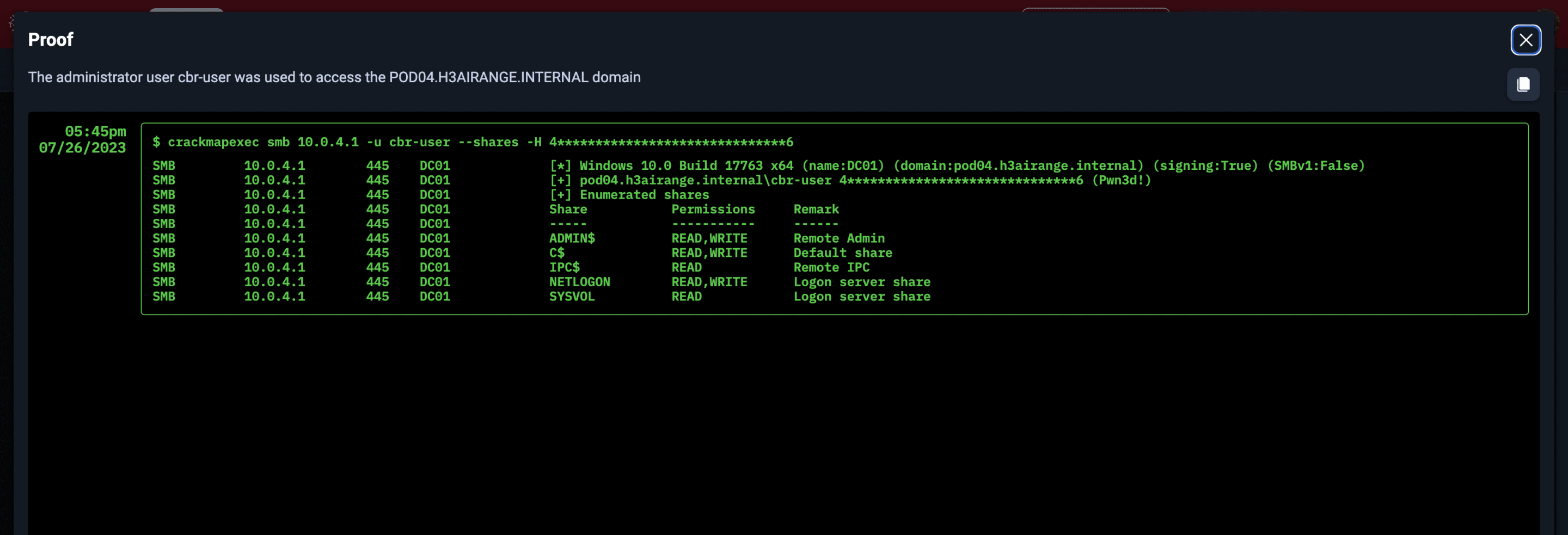
NodeZero verified the credential for domain admin cbr-user in domain POD04.H3AIRANGE.INTERNAL on the SMB service on domain controller 10.0.4.1 (dc01.pod04.h3airange.internal) port 445
Proof NodeZero achieved domain compromise and domain user compromise after 33 minutes, 9 seconds.
During the attack NodeZero leveraged 2 weaknesses:
- H3-2020-0022: Insecure Java JMX
- H3-2021-0042: SAM Dump
The attack path involved 1 compromised credential:
- Domain Admin cbr-user
The attack spanned 2 hosts:
- 10.0.4.4
- Domain Controller 10.0.4.1
Once a domain is fully compromised, all hosts, domain user accounts, data, infrastructure, and applications tied to that domain should be considered fully compromised. Additionally, applications running on a domain-joined machine or any application that uses Active Directory integration to authenticate users should be considered fully compromised.
Key Takeaway
Remediating the Insecure Java JMX Configuration weakness would potentially eliminate 28% of critical impact paths. NodeZero provides the guidance to remediate the issues identified.
Discover the attack paths in your environment.
Start your 30-day NodeZero free trial now.
如有侵权请联系:admin#unsafe.sh












