A question we frequently get from new users as they’re onboarding is: why does WordPress get hacked? Of course, this question makes sense in this context; it’s extremely frustrating to find out that your WordPress website has been compromised and you need to tackle an infection or increase security controls. Surely you’d want to understand why.
However — while all websites are susceptible to hacks, certain errors could be increasing the vulnerability of your website. In this post, we’ll delve into a few of the main reasons why WordPress sites get hacked and how it happens. This will help you to recognize potential mistakes and take measures to safeguard your site from attacks.
Why do hackers target WordPress?
First off, we need to make an important distinction: WordPress is not the only CMS platform targeted by hackers. In fact, to varying degrees all websites on the internet are prone to hacking attempts.
However, WordPress powers over 43% of all websites on the web, translating into hundreds of millions of websites worldwide. This popularity makes it a prime target for hackers, particularly websites that are not well-secured or contain known software vulnerabilities.
Understanding the hacker’s motive
Hackers have a wide range of motivations for their illicit activities. Some are merely novices learning to exploit less secure sites. Others might have more nefarious intentions, such as distributing malware, launching attacks on other websites, sending spam, or using compromised domains for black hat SEO.
Some attackers focus on stealing sensitive data such as personal information, credit card numbers, or login credentials. These can be sold on the dark web or used to commit fraud and identity theft. Others may simply be looking to disrupt services or make a political statement.
However, it’s important to note that not all hackers are motivated by illicit gains or malicious intent. Some hackers, often referred to as “white hat” hackers, exploit vulnerabilities in order to expose them and help improve the system’s security.
Regardless of the motive, the outcome of a hack is almost always detrimental to the website owner. It can lead to lost data, reputation issues, and even legal consequences if sensitive customer information is compromised.
Key reasons why WordPress gets hacked
Now that we understand the motivations behind a hack, let’s take a look at some of the key reasons why WordPress gets hacked.
- Unpatched WordPress core, plugins & themes
- Weak passwords and usernames
- Unprotected WordPress admin panels
- Improper isolation in shared server environments
- Unrestricted access to wp-config
1. Unpatched WordPress core, plugins & themes
The core WordPress CMS is secure, but only if you maintain it to the latest version and properly configure it.
Since the code base is publicly accessible, anyone can review and analyze the source code. And whenever a bug or security issue is reported by the open-source community, developers update WordPress core to patch the issue.
However, these updates don’t apply to your extensible components like plugins and themes. You’ll need to patch each piece of software individually (and on a regular basis) to mitigate risk.
Not updating your WordPress software and components can leave your site exposed to known issues. To protect your environment and mitigate risk, it’s crucial to update your WordPress core (along with all your plugins and themes) as soon as a new patch is available.
Hackers often use automated tools to quickly find and attack websites with known vulnerabilities — so it’s important to act quickly when it comes to software updates.
2. Weak passwords and usernames
Passwords are your WordPress site’s first line of defense. A weak password can be easily cracked with automated tools, giving an attacker unauthorized access to your posts, pages, files and database.
That’s why it’s so essential to use strong, unique passwords for all your accounts, including:
- WordPress admin account
- Web hosting control panel account
- FTP accounts
- MySQL databases
- Email accounts used for WordPress admin and hosting
We recommend creating unique passwords with a combination of letters, numbers, and special characters — at least 12 characters long. Password generators can make it easy to quickly create new unique credentials for your accounts.
Furthermore, steer clear of default admin usernames; it only takes a second to change admin to something unique and makes it that much harder to guess the credentials to your account.
3. Unprotected WordPress admin panels
The WordPress admin area and default login pages /wp-login.php and /wp-admin are one of the most frequently targeted areas of WordPress. Since it’s where you can control all aspects of your website, it’s also consequently where hackers can do the most damage.
By default, WordPress does not limit the number of failed login attempts (nor does it contain any native 2FA system), rendering it particularly vulnerable to brute force attacks.
Protect your WordPress site by adding layers of authentication and restricting unauthorized access to sensitive pages like wp-login and wp-admin.
The Sucuri firewall makes it easy to implement protected pages across your website and provides options for password protection, 2FA, captcha and IP address restrictions.
4. Improper isolation in shared server environments
We deal with plenty of new clients who have “soup kitchen servers”. These are web servers with a huge number of websites, installations, and configurations all crammed into the same environment.
The issue with these environments is that a single compromised website can infect all others on the shared account or server, leading to cross-site contamination.
You can help prevent this issue by using separate cPanel instances for each website and configuring a secure VPS environment with PHP-FPM to host multiple sites.
5. Unrestricted access to wp-config
The wp-config.php file is an integral part of your WordPress website. This core file is responsible for running your site and houses important configurations such as database location details, login credentials, and advanced options for database elements, security keys, and developers.
If you’re new to WordPress, it’s crucial to start by restricting access to this file. One way to do this is by moving your wp-config file one directory level above the root folder, making it inaccessible to the internet. If the file is not found in the root folder, WordPress will automatically search for it in the directory above the root.
For those whose servers use .htaccess: you can further restrict access by adding a rule to deny anyone searching for it.
The directives for Apache 2.4 are as follows:
<FilesMatch "wp-config\.php">
Require all denied
</FilesMatch">Additional security measures: Salts and keys
The wp-config file includes a section dedicated to salts and keys that boost the security of cookies and passwords in transit between your browser and web server.
You can set up your salts and keys by adding or editing these lines after the other define statements:
define(‘AUTH_KEY’, ‘include salt here’);
define(‘SECURE_AUTH_KEY’, ‘include salt here’);
define(‘LOGGED_IN_KEY’, ‘include salt here’);
define(‘NONCE_KEY’, ‘include salt here’);Additional security measures: Set file permissions
Since the wp-config.php file contains highly sensitive information, it’s essential to configure file permissions to prevent unauthorized access or modification.
A permission level of 600 should suffice, but you can start with 400 and escalate as necessary. Always begin with the least permissive configuration and only increase permissions when required. Never set permissions to 777 unless you’re an expert or have an excellent reason.
Additional security measures: Disable plugin and theme installers
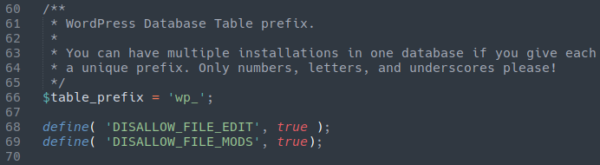
Wp-config can also define vital information about WordPress plugins and themes. For instance, you can disable the theme and plugin file editors or installers by adding the following lines to your wp-config file:
define( 'DISALLOW_FILE_EDIT', true ); //disables file editor define( 'DISALLOW_FILE_MODS', true ); //disables both file editor and installer
Bear in mind that this will also block plugin updates. You can still update plugins and themes using WP-CLI or manually via sFTP.
Attackers often exploit theme and plugin installers to install backdoors. So, this simple step can make it more challenging for them to create fake plugins for unauthorized access.
What is the best way to prevent WordPress from hacks?
The unfortunate reality is that no single security measure can provide a 100% guarantee against hackers. However, implementing a defense-in-depth strategy with a wide range of protections like the ones listed in this post, hardening your WordPress website, and leveraging a reliable website firewall can significantly improve your chances of preventing a hack.
The Sucuri firewall is designed to ward off brute force attacks, blocking any unwarranted access to your wp-admin or wp-login page and preventing automated attacks. It mitigates Distributed Denial of Service (DDoS) attacks, which try to overwhelm a server or application resources. It can also help patch known vulnerabilities in the event that you’re unable to update your website software in a timely manner.
There’s no installation necessary — just a simple switch of your DNS A Record to enable it. For further details, check out this video on how to prevent a hack with a website firewall.
如有侵权请联系:admin#unsafe.sh