
2023-8-30 22:10:27 Author: www.sentinelone.com(查看原文) 阅读量:26 收藏
Good Day ransomware, a variant within the ARCrypter family, was first observed in-the-wild in May of 2023. Between June and August of 2023, we observed an uptick in Good Day ransomware campaigns and a proliferation of new ransom note samples in public malware repositories. This new wave of Good Day attacks feature individual TOR-based victim portals for each target.
In this post, we expand on several unique Good Day ransom notes and victim portals and share our analysis of a sample associated with a URL leading to a known Cloak extortion site. By tying these recent Good Day campaigns to victims listed on the Cloak site, we can associate the Cloak data sales and leaks with Good Day through publicly viewable chats on the group’s TOR-based victim portals.
The discovery of such connections helps us chart the ever-dynamic relationships between existing and new vulnerabilities and threat actors. The more we can tie together these moving parts, the better chance that security practitioners have of reducing risk within their organizations.

Good Day Victim Portals Linked To Cloak Extortion Site
In July and August of 2023, we observed multiple new TOR-based URLs being staged for use by the Good Day group. Each portal is intended for a corresponding attack and specific victim. Similarly, each Good Day payload points to a specific victim portal.
Good Day (ARCrypter) victims are greeted with a ‘Good day’ welcome message when following the instructions provided in their ransom notes and opening the portal tied to the payload that encrypted their devices.
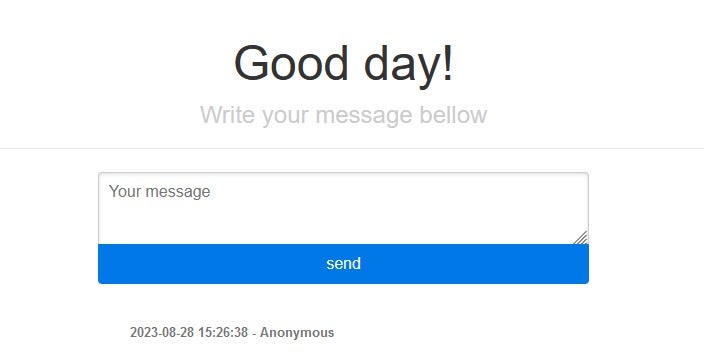
Some of the portals have been revealed in previous research by Cyble. However, analysis of a series of new ransom notes reveal that Good Day victims are also listed on the Cloak extortion blog site.
In particular, we found that a series of ransom notes that all include the email address MikLYmAklY555[@]cock[.]li, which was also previously seen in AstraLocker campaigns.
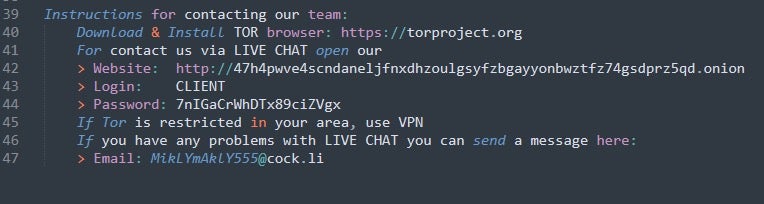
At the time of writing, victim chats on the Good Day portals remain publicly accessible. Within these publicly accessible chats, we can see the threat actors communicating data to the victim.
In the case of sample d5fba798bb2a0aaca17f17fa14f2ff240be8d34d (associated ransom note: 7cf3b23cdb8c5fd74b094f76eb4ffc38e18bd58a) the threat actor communicates the URL of the blog where they intend to leak the victim’s data, which turns out to be the URL of the Cloak blog site. They also mention specific company names that can be found on the Cloak blog site.
The Cloak leak site first appeared in August of 2023 and currently lists 23 victims. Many of these victims are marked as “sold” and their respective data is not currently accessible on the surface.

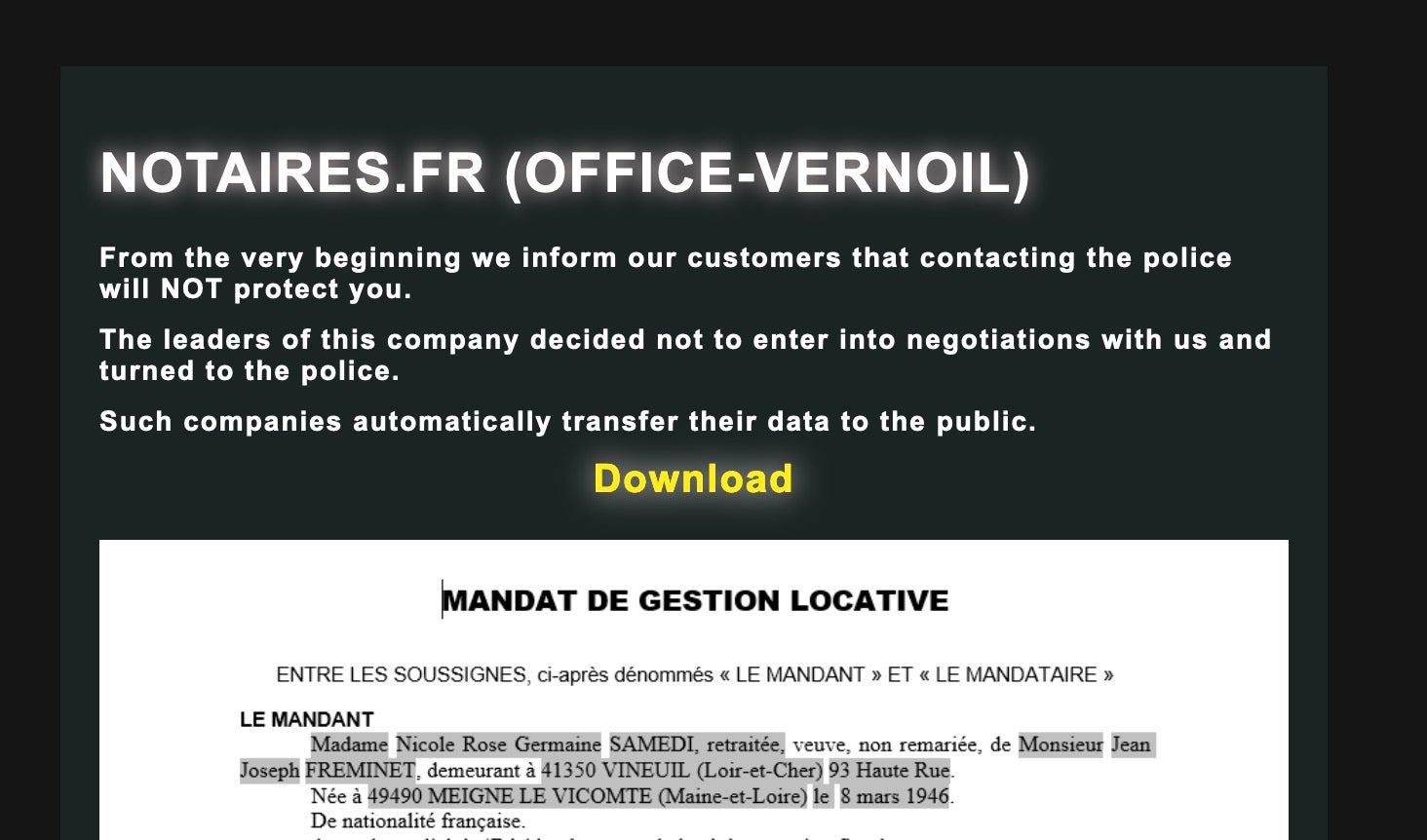
Our analysis shows that Good Day ransomware victims are being threatened with having their data leaked or sold on the Cloak website. This intimidation tactic is amplified by the daunting list of “sold” victim companies that currently appear on the site. The threat actors leverage this and other intimidation tactics to coerce the victim into paying the ransom.
Regarding targeting, we also note that victims listed on the Cloak leak site indicate some amount of geographical focus. The main countries targeted are Germany, Italy, Taiwan, and France.
Good Day Ransomware Sample Analysis
In sample d5fba798bb2a0aaca17f17fa14f2ff240be8d34d, the ransom instructions point to a TOR-based victim portal at
47h4pwve4scndaneljfnxdhzoulgsyfzbgayyonbwztfz74gsdprz5qd[.]onion.
This sample masquerades as a Microsoft Windows Update executable (WindowsUpdate.exe). The ransomware is designed to be launched via a dropper or script, aligning it with past ARCrypter activity. The /START parameter is required to fully launch the ransomware.
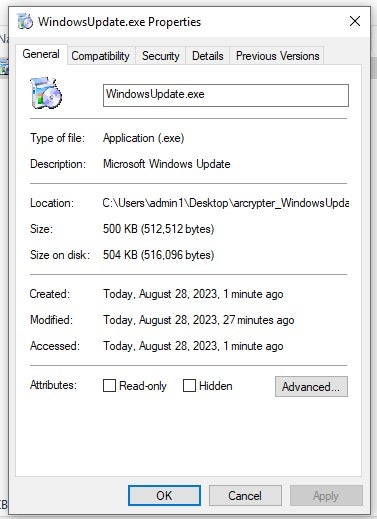
The identifying strings that we expect to see in the ARCrypter family are also visible in this sample.
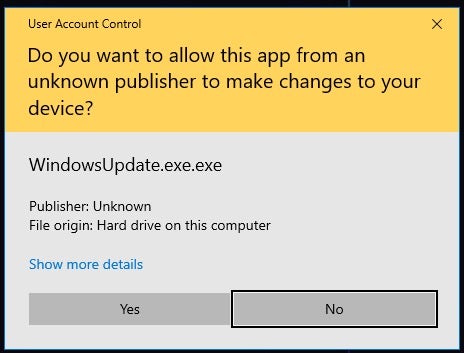
This particular payload issues a User Access Control (UAC) prompt in order to elevate privileges when launched.
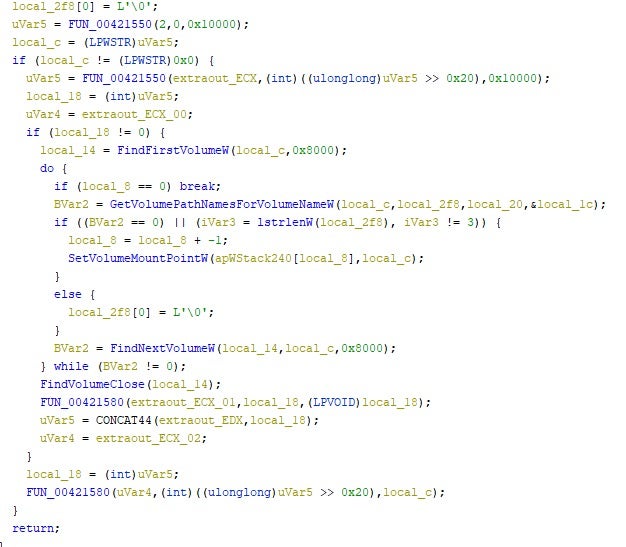
Once running, the malware will attempt to enumerate all local volumes to encrypt. This includes the use of wNetOpenEnum to identify available shares. In addition, the malware will enumerate all running processes.
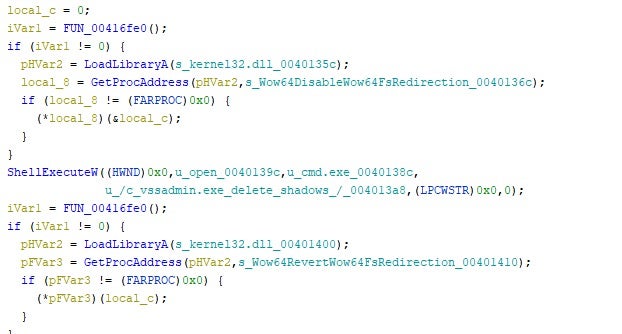
The ransomware attempts to remove volume shadow copies (VSS) using the following command:
vssadmin.exe delete shadows /all /quiet
Affected files are renamed with the .crYptA or .crYptB extensions post-encryption. This pattern can extend up to .crYptE following the alphabet in series with the final letter in the extension.
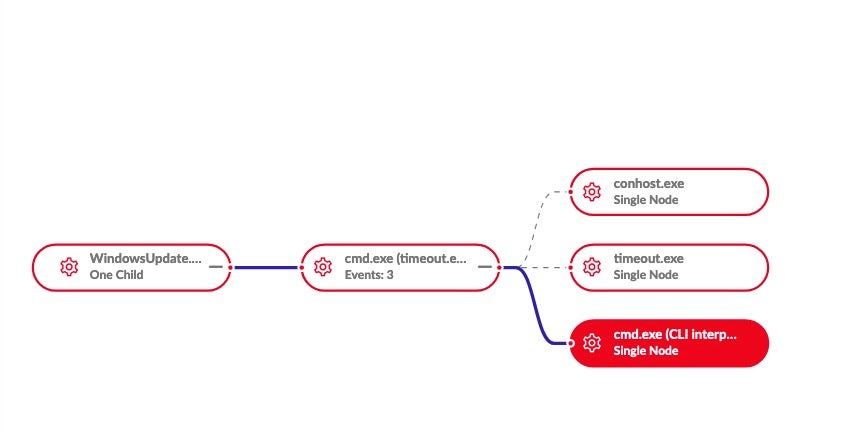
The Good Day ransomware then delays execution of the payload via the following hidden command:
¬/c TIMEOUT /T 2>NUL&START /b "" cmd /c DEL "C:\Windows\explorer.exe" &DEL "WindowsUpdate.exe.exe" &EXIT
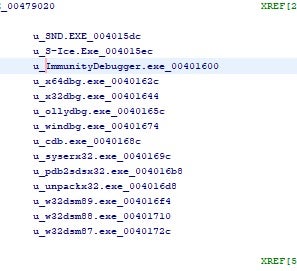
The ransomware also attempts to determine whether it is running in a specific debugger. The search list includes S-Ice.exe, ImmunityDebugger.exe, x64dbg.exe and others.
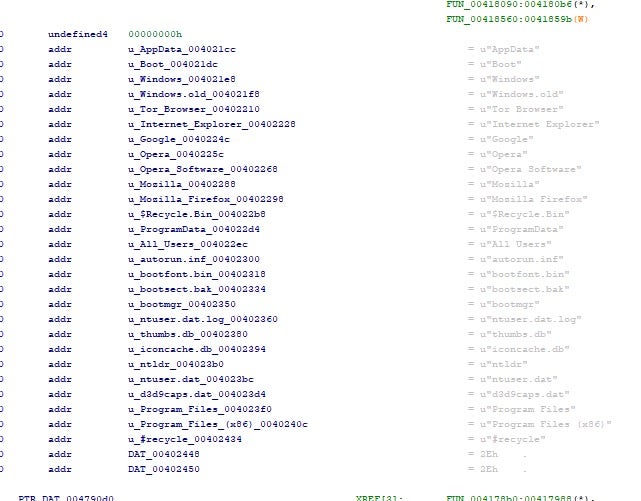
The malware contains a hardcoded list of folders and files that are to be excluded from encryption.
SentinelOne Protects Against Good Day (ARCrypter) Ransomware
The SentinelOne Singularity™ Endpoint platform detects and prevents malicious behaviors and artifacts associated with Good Day/ARCrypter ransomware.
Conclusion
Tracking the inputs and outputs of extortion groups is a significant part of the puzzle as we continue to research the growing web of threat actors. It always helps to be able to tie pieces together where they are not directly apparent.
Observing the URLs found in ransom notes and the existing structure of the victim blog sites, we are able to firmly establish the nature of the tie between Good Day and the Cloak leak site. The latest payloads for Good Day have yet to build on their ARCrypter roots, but we will continue to monitor this group and their payloads.
To learn about how SentinelOne can help protect the devices in your fleet from ransomware and other threats, contact us or request a free demo.
Indicators of Compromise
Payload
d5fba798bb2a0aaca17f17fa14f2ff240be8d34d
Ransom Notes
7cf3b23cdb8c5fd74b094f76eb4ffc38e18bd58a
7ef712604fca6ad5a368745a015354aba74f5f61
a3ff2d575adc8edb088706e1de1a18a2d789cd73
c374252e4cff08e3abcda06503998cd3d3ef8322
URLs
cloak7jpvcb73rtx2ff7kaw2kholu7bdiivxpzbhlny4ybz75dpxckqd[.]onion dcpuyivlbzx56hqwsvey33bxobxw3timjgljjy3index6qvdls5bjoad[.]onion wwwieqvblhnel7wsb6jpxeen3dbmsqyozj2gzl2oyn6swrkq27jtusqd[.]onion 47h4pwve4scndaneljfnxdhzoulgsyfzbgayyonbwztfz74gsdprz5qd[.]onion zxzs677rphmjznqgqzlsmjtqwqlydq47rwjesrt4dkkh6cc2ftlfhuqd[.]onion
如有侵权请联系:admin#unsafe.sh