2019-03-16 01:17:41 Author: medium.com(查看原文) 阅读量:448 收藏
This is my second write-up, feel free to give me feedback on Twitter (@thibeault_chenu) or in the comments to help me. 🙂
Introduction
A few months ago, I conducted a voluntary security audit of a 🇫🇷French company.
This company has a website on which you can find news, a contact page or documents to download, a classic website.
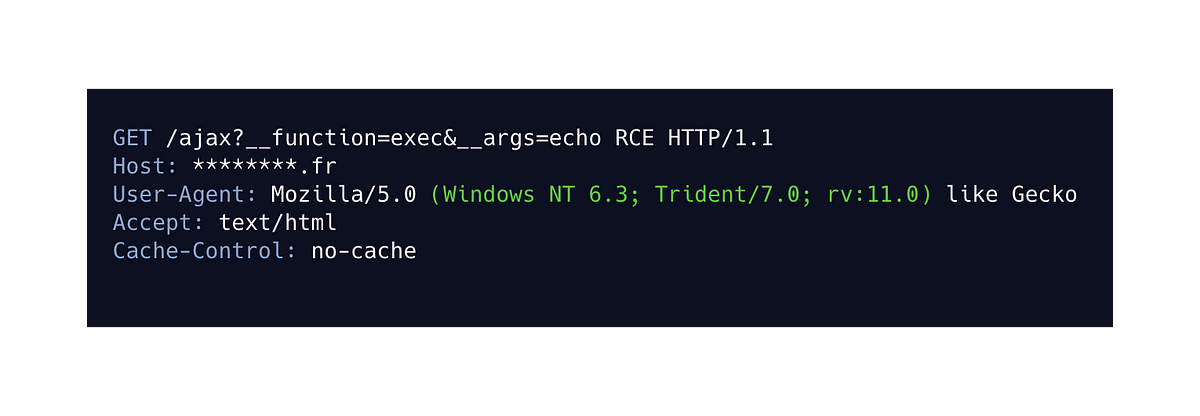
To load some content, AJAX requests are sent and they are composed of 2 parameters.
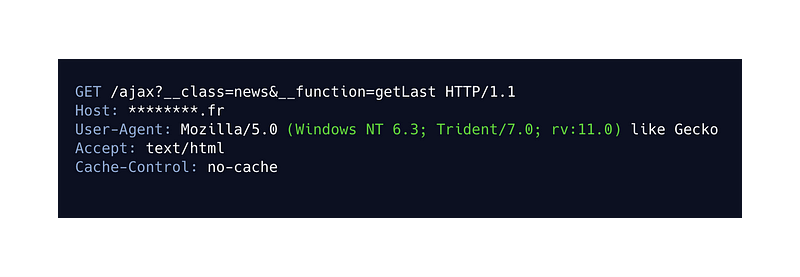
This request allows you to obtain a response containing the latest news from the site in HTML format.
Remote Code Execution
From this it is possible to understand how the site works in general. An endpoint named ajax allows you to use any method of any class.
Before finding the technique below I tried various attempts with a stdClass class and methods but nothing functional.
I then have an idea which is to simply delete the class parameter to try to display the phpinfo() function.
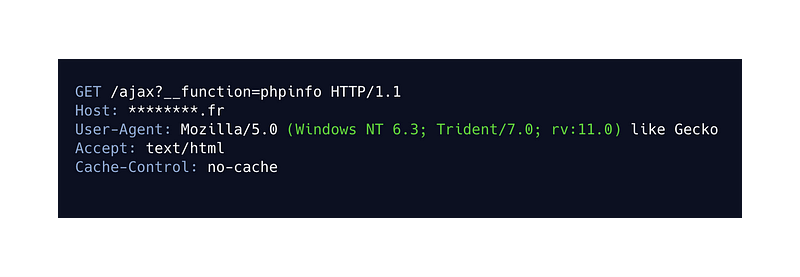
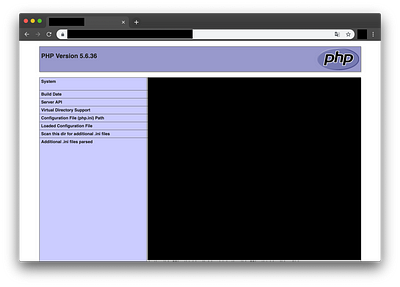
My idea works, now how can I use it more effectively? 🤔
In PHP there is a function called system (https://secure.php.net/manual/fr/function.system.php) that allows you to execute commands and return the result of this command.
system ( string $command [, int &$return_var ] ) : string
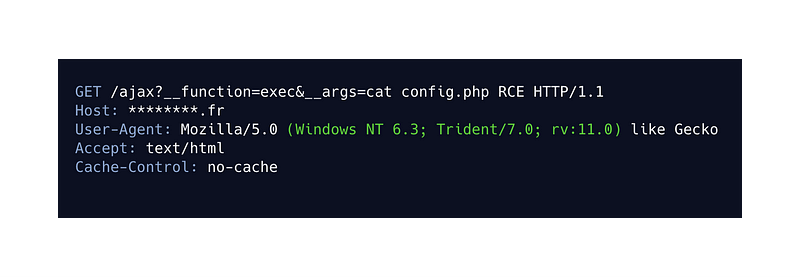
As you can see, however, I need a parameter that allows me to place the command of my choice. For that I will use a parameter that I have seen on some pages, this parameter is called args (not very difficult, i know).

Now that I know that I can execute any UNIX command, there are a number of things that are possible. In this case I will search further because I can now access the list of folders and files and their contents.
LDAP Server
The most interesting thing is to find configuration files in which I can find information about databases credentials.
Unfortunately / fortunately this is what I was able to find, a configuration file containing a set of login and passwords to databases (20 databases) and an LDAP server.

But why an LDAP server ? First of all, let’s remember what an LDAP server is.
We will be more interested in the LDAP server than the databases. I was able to connect to even though they are inaccessible outside localhost thanks to a version of phpMyAdmin installed on the server. 🙄
The Lightweight Directory Access Protocol (LDAP /ˈɛldæp/) is an open, vendor-neutral, industry standard application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network.[1] Directory services play an important role in developing intranet and Internet applications by allowing the sharing of information about users, systems, networks, services, and applications throughout the network.[2] As examples, directory services may provide any organized set of records, often with a hierarchical structure, such as a corporate emaildirectory. Similarly, a telephone directory is a list of subscribers with an address and a phone number.
Source: https://en.wikipedia.org/wiki/Lightweight_Directory_Access_Protocol
To simplify the understanding of what an LDAP is, it is important to remember that it is a directory of users. This directory can be used to allow users to connect only once and have access to various applications and websites. This directory also allows the opening of Windows sessions.
To answer the question “Why are there LDAP accesses in a website configuration file?”, these accesses allow you to define rights to authenticated users on the site.
To connect to the company’s LDAP server under MacOS I found few free applications, I personally used LDAPSoft.
If you ever have an open-source alternative I’m interested because using the Terminal to connect to an LDAP server is annoying when there are about 40 fields for each user.
The LDAP credentials had access to was restricted to reading rights, it was impossible for me to modify a user’s data.
Thanks to Wikipedia and the LDAP server I was able to know that the security breach concerned 40,000 people.
For each person I was able to access:
- First and last name,
- Personal email address,
- Date of birth,
- Telephone number,
- Password in clear (a random number…),
- Information about a RFID tag (MiFare),
- Personal directory for starting the Windows session.
The RFID tag of each employee allows access to the company’s building, it is possible to buy blank RFID tags to enter the information present in the LDAP server and thus fraudulently access the building.
I know that this type of tag is not expensive and is easily programmable.
SMS Emergency Alerts
The company in question has a system that I had never seen before in a company, the system in question made it possible to send an alert SMS to all employees of the company in case of intrusion into the building (😏) or a terrorist attack.
Indeed, by searching in one of the configuration files I was able to obtain an API key from an SMS sending service.
A simple HTTP request with this key would have allowed me to send an SMS to the whole company.
Conclusion
- Access to the information of 40,000 former employees or employees,
- Possibility to access about twenty databases,
- Possibility of access to the company’s buildings with RFID tag (?),
- Possibility to obtain the password of each user and thus obtain other access (?).
The company was alerted and corrected the RCE flaw.
如有侵权请联系:admin#unsafe.sh
