
2023-5-25 19:0:0 Author: checkmarx.com(查看原文) 阅读量:4 收藏
-
 By
David Sopas
By
David Sopas
- and João Morais
- May 25, 2023

Research by David Sopas and João Morais
Checkmarx Security Research team reached out to Ericsson’s Responsible Disclosure Program, notifying them of the the finding on 14th March 2023. Ericsson acknowledged the finding and replied that the issue was fixed on 11th April 2023.
ASP.NET web applications that run with tracing enabled, may publicly expose sensitive information. This feature allows any user to view diagnostic information about a single request for an ASP.NET page. When this feature is enabled, Trace Viewer (Trace.axd) may be publicly accessible, without server’s root authentication. The Checkmarx Security Research team discovered this vulnerability and will explore what that means for users in this post.
This research was conducted following Ericsson Vulnerability Disclosure Program.
One of Ericsson’s subdomains is forecast.ericsson.net. However, when accessing it via a web browser it redirects to https:// forecast.ericsson.net /Login /Login. aspx. No complex reconnaissance process was required to understand that we were dealing with an ASP.NET web application.
There are several, well-known endpoints/resources of interest to check for when dealing ASP.NET web applications, and - /Trace.axd is one of them. Trace.axd is a web-page that is intended to provide extensive logging information in regard to web requests to the application. - If this is exposed, it may provide attackers unauthenticated access to the last 80 web requests made to the server. This has the potential to result in a sensitive information, such as PII data, and session details being disclosed. This information may then be used to potentially take over user accounts, and further compromise Ericsson’s applications.
After finding Trace Viewer (Trace.axd) on our target subdomain (https://forecast.ericsson.net/Trace.axd), we checked what information was available.
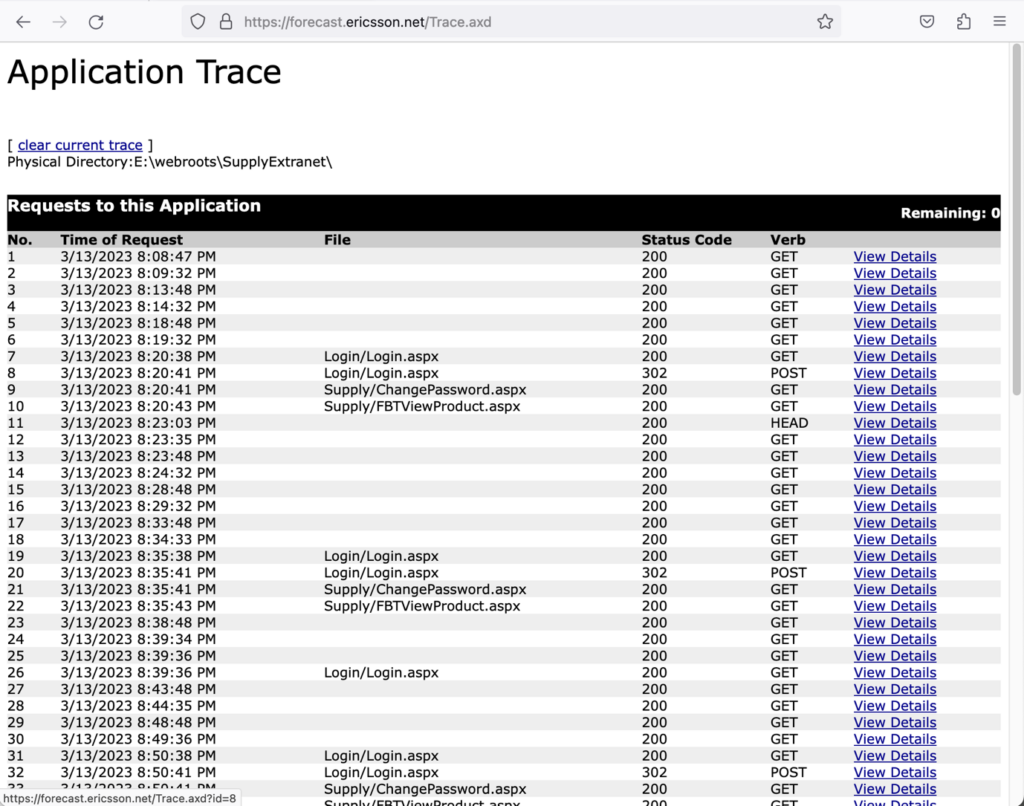
The picture above shows the Trace Viewer main page (Trace.axd), which is where the physical directory of the web application (E:\webroots\SupplyExtranet\) and the last requested web application files are printed (Supply/ChangePassword.aspx).
As you can see, it is possible to view additional details for each request. This potentially can allow malicious actors access to sensitive information. The body of POST requests, especially those to the Login/Login.aspx endpoint, are good candidates to monitor for disclosure sensitive information, including usernames and passwords. We can see this scenario, where user account credentials, username and password, are both shown in plaintext in the figure below.
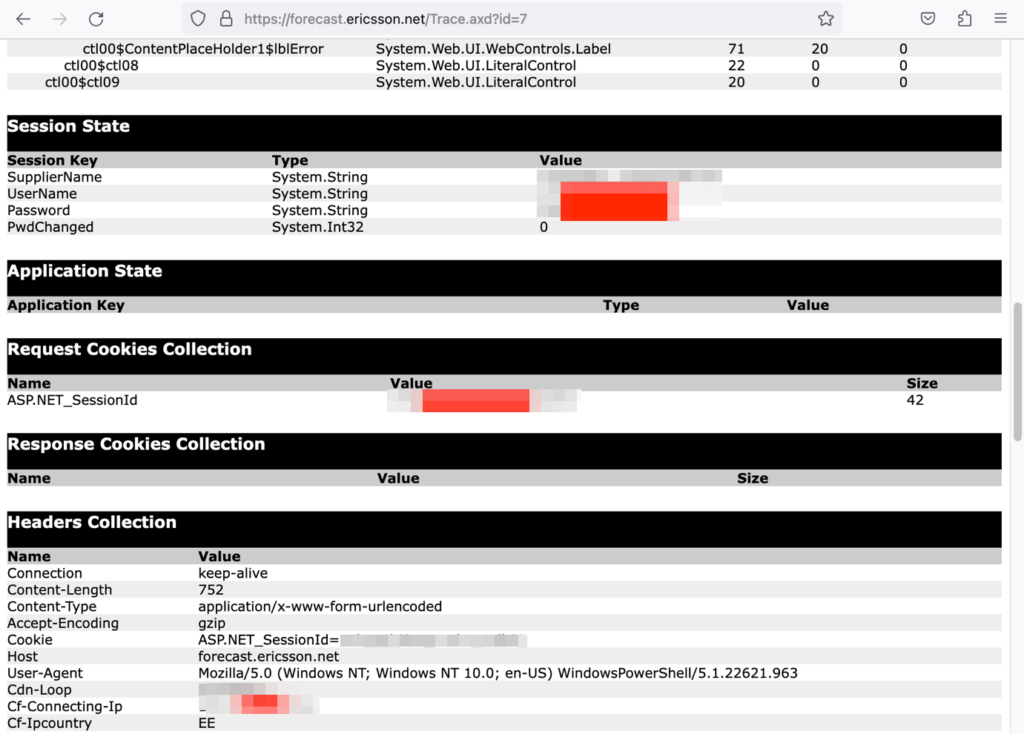
Information disclosure via Trace Viewer (Trace.axd) for ASP.NET web applications is a high severity security issue that can lead to the compromise of sensitive information and online systems. This feature should not be enabled in production environments.
![]()
David Sopas
David Sopas is an AppSec Research team leader at Checkmarx and co-founder of Char49. Google, Yahoo!, eBay, Microsoft, US Dept. of Defense and many other companies and organizations have acknowledged his work. As a former part-time bounty-hunter, he's still top5 on Cobalt and top100 on HackerOne. These days, David enjoys breaking IoT devices and hacking his life as much as possible.
![]()
David Sopas
David Sopas is an AppSec Research team leader at Checkmarx and co-founder of Char49. Google, Yahoo!, eBay, Microsoft, US Dept. of Defense and many other companies and organizations have acknowledged his work. As a former part-time bounty-hunter, he's still top5 on Cobalt and top100 on HackerOne. These days, David enjoys breaking IoT devices and hacking his life as much as possible.
Never miss an update. Subscribe today!
By submitting my information to Checkmarx, I hereby consent to the terms and conditions found in the Checkmarx Privacy Policy and to
the
processing of my personal data as described therein. By clicking submit below, you consent to allow Checkmarx
to store and process the personal
information submitted above to provide you the content requested.
More Resources to Consider
如有侵权请联系:admin#unsafe.sh