
2023-5-9 19:0:0 Author: checkmarx.com(查看原文) 阅读量:5 收藏
Research done by Teach Zornstein and Yehuda Gelb
Intro
In the evolving world of cybersecurity, attackers are always looking for new ways to exploit weaknesses and compromise systems. Attackers have been using lowercase letters in package names on the Node Package Manager (NPM) registry for potential malicious package impersonation. This deceptive tactic presents a dangerous twist on a well-known attack method -- "Typosquatting." In this blog post, we will explore the origins of this issue, the risks it poses, and the steps that were taken to address it while also examining its relationship to Typosquatting.
A Brief History of Package Naming in NPM
Prior to 2017 NPM package creators were allowed to use both upper and lowercase letters in their package names. However, in 2017, NPM changed its policy, and new packages could only be created with lowercase letters. Despite this change, existing packages with mixed-case names were allowed to remain on the registry and are still in use to this day. In fact, there are thousands of mixed-case packages still available, collectively accounting for tens of millions of downloads.
The Impersonation Threat
Bad actors can easily exploit this situation by uploading packages with names that closely resemble legitimate packages, simply by using lowercase letters to mimic uppercase letters in the original package names. This tactic is intended to trick users into downloading, and installing, the malicious package instead of the intended legitimate one.
For instance, consider these two packages:
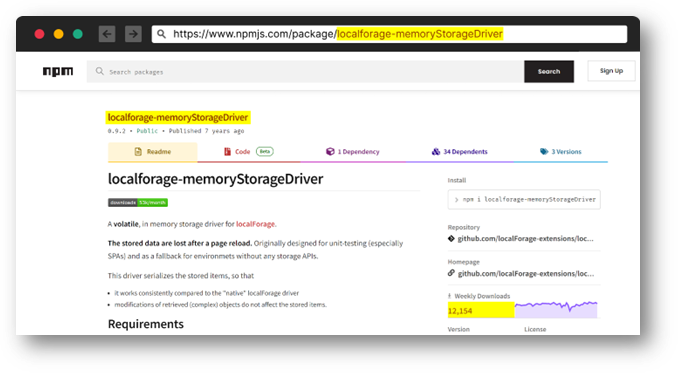
Legitimate package
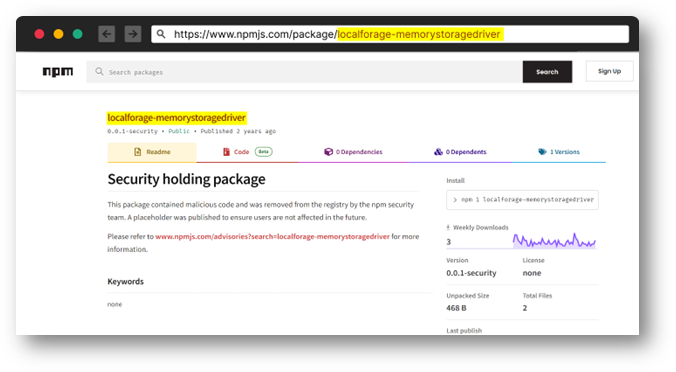
Removed for security reasons
The only difference between the two package names is the capitalization of the "S" and "D" in "memoryStorageDriver." Malicious users hope that unsuspecting users will unintentionally install the wrong package, due to the close resemblance in their names.
A stealthier approach to Typosquatting:
This malicious package impersonation takes the traditional "Typosquatting," attack method to a new level, where attackers register package names that consist of the exact same letters as the legitimate ones, with the only difference being capitalization. This makes it even harder for users to detect the deception since it can be easy to overlook the subtle differences in capitalization.
The Scope of the Problem:
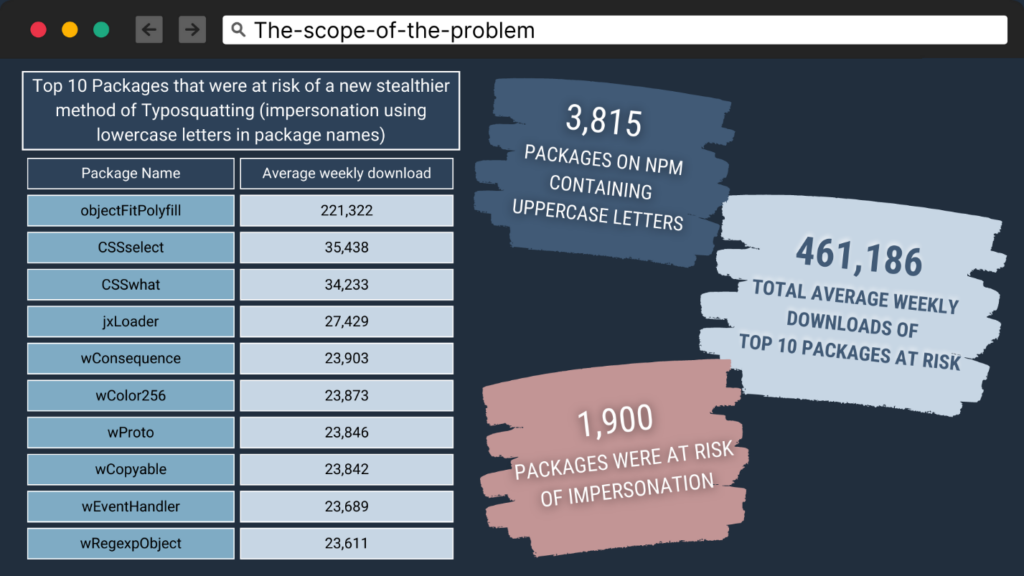
3,815 packages were found on NPM containing uppercase letters. Out of these, 1,900 packages were at risk of impersonation, meaning that someone could upload a package with the same name but with all lowercase letters. Some of the at-risk packages were quite popular, such as "objectFitPolyfill," which has hundreds of thousands of weekly downloads. In total, the download count of the packages at risk is in the tens of millions.
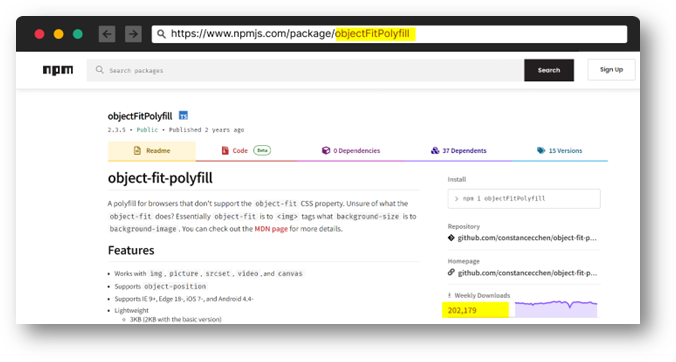
Popular vulnerable package on NPM (capital letters used in the package name)
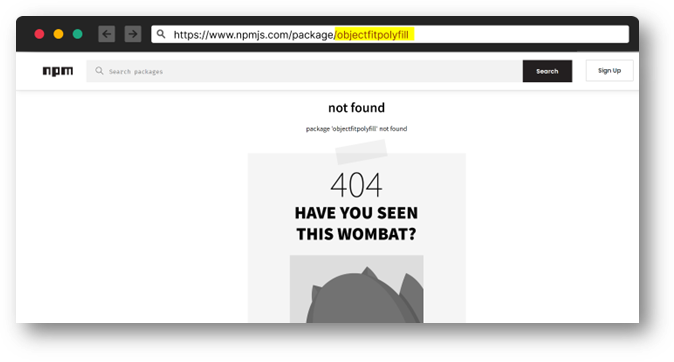
Package name “objectFitPolyfill” in all lowercase letters available for anyone to use in a new package
How do other Package Managers compare with NPM?
To better understand the malicious package impersonation issue in NPM, let's compare how other popular package managers, such as PyPI and NuGet, handle this issue.
Both PyPI and NuGet adopt more robust strategies for dealing with package names containing uppercase and lowercase letters. For example, let’s take a package named "ExamplePackage" published on PyPI or NuGet. Unlike NPM, these package managers allow package creators to upload packages with names containing both upper and lowercase letters. Once "ExamplePackage" is published, PyPI and NuGet will restrict anyone else from uploading a package with the same name, regardless of the capitalization of letters. This means that a package named "examplepackage" or "Examplepackage" cannot be uploaded by someone else, preventing bad actors from exploiting package name variations.
In addition, PyPi and NuGet have implemented an automatic typo-correction mechanism to assist users who accidentally type package names with incorrect capitalization. By employing these measures, PyPI and NuGet significantly reduce the chances of users falling victim to deceptive tactics. This approach provides a more secure environment for package distribution and installation.
Addressing the Issue
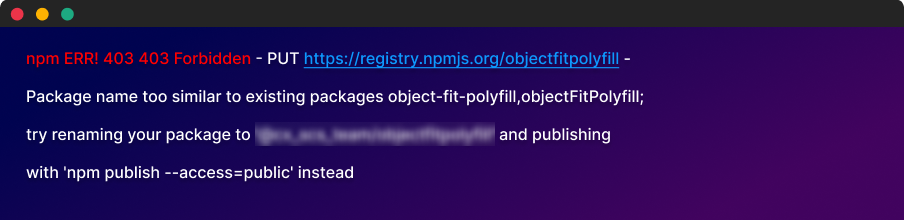
The issue was brought to the attention of the NPM security team, who promptly acknowledged and effectively addressed the concern. Now, if anyone attempts to upload packages that use all lowercase letters to imitate existing uppercase letters, they will be met with an error message that reads, "Package name too similar to existing package."
Package health checks: Users can check package health prior to installation. For example, Overlay Browser Extension can alert you if a package has known security issues or vulnerabilities, based on the latest advisories from trusted sources. By using tools like this, you can ensure that the package you are installing is secure and reliable.
Raising awareness: We are dedicated to spreading awareness about attacks such as these and their potential impacts. By sharing our findings with the community, we aim to educate users and developers about the risks involved and the precautions they can take.
Conclusion
It is important to emphasize how easy it is to fall for this type of attack. It’s as simple and subtle as a change in capitalization. This vulnerability highlights the importance of staying vigilant and being aware of evolving tactics employed by bad actors. By understanding the risks, users can take appropriate precautions. The matter was reported to the NPM security team, who quickly recognized and efficiently resolved the issue.
如有侵权请联系:admin#unsafe.sh