2023-10-2 14:44:46 Author: securityaffairs.com(查看原文) 阅读量:11 收藏
North Korea-linked Lazarus targeted a Spanish aerospace company

North Korea-linked APT group Lazarus impersonated Meta’s recruiters in an attack against a Spanish company in the Aerospace industry.
ESET researchers linked the North Korea-linked Lazarus APT Group to a cyber attack targeting an unnamed Spanish aerospace firm. The cyberspies impersonated Meta’s recruiters to lure employees with trojanized coding challenges.
The state-sponsored hackers deployed several tools, including a previously undocumented backdoor dubbed LightlessCan. The researchers identified four different attack chains, delivering three types of payloads via DLL side-loading.
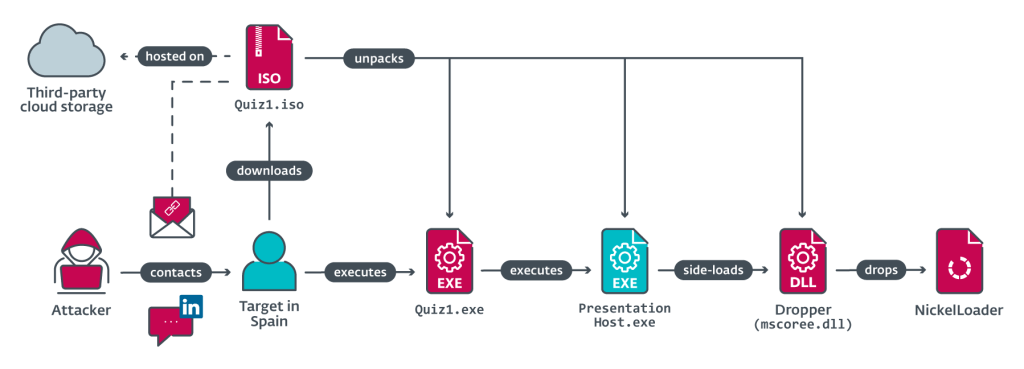
Threat actors sent two coding challenges to employees of the targeted organization tricking them into opening the malicious executable file.
“The fake recruiter contacted the victim via LinkedIn Messaging, a feature within the LinkedIn professional social networking platform, and sent two coding challenges required as part of a hiring process, which the victim downloaded and executed on a company device.” reads the analysis published by ESET. “The first challenge is a very basic project that displays the text “Hello, World!”, the second one prints a Fibonacci sequence – a series of numbers in which each number is the sum of the two preceding ones.”
ESET believes that this attack is part of a long-running cyber espionage campaign tracked as Operation DreamJob.
The LightlessCan implant is more sophisticated and stealth than its predecessor, BlindingCan. In 2020, US CISA published an alert related to the North Korean malware BLINDINGCAN used in attacks on the US defense and aerospace sectors. LightlessCan mimics the functionalities of a wide range of native Windows commands to avoid detection.
The malware authors implemented another mechanism to make sure the payload can only be decrypted on the intended victim’s machine to prevent the analysis by researchers.
The malicious executables, Quiz1.exe and Quiz2.exe, employed in the attack on the Spanish firm were delivered via the Quiz1.iso and Quiz2.iso images. Both images were hosted on a third-party cloud storage platform and both executables are very simple command-line applications asking for input.
The challenge for the targeted developer consists of understanding the logic of the program and rewriting it in the C++ programming language.
After the output of the two programs is printed, both executables start installing additional payloads from the ISO images onto the target’s system.
The attack chain leads to the deployment of an HTTP(S) downloader, named NickelLoader, to the victim’s computer. Then the downloader is used to deploy additional malicious payloads into the memory of the victim’s system, including the LightlessCan RAT and miniBlindingCan that is a simplified version of the BlindingCan RAT.
LightlessCan was designed to support for up to 68 distinct commands, but the current version, 1.0 analyzed by ESET only supports 43 of those commands.
“The remaining commands are present but have a formal implementation in the form of placeholders, lacking actual functionality. The project behind the RAT is definitely based on the BlindingCan source code, as the order of the shared commands is preserved significantly, even though there may be differences in their indexing.” continues the report.

ESET’s analysis concludes that the most worrying aspect of the attack is the use of the LightlessCan RAT which exhibits a high level of sophistication in its design and operation.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Lazarus)
如有侵权请联系:admin#unsafe.sh
