
2023-10-2 12:0:0 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
Remember when ransomware was simply getting locked out of your files? Those seem like the good old days compared to today’s nightmare, with entire operations shut down for days or weeks.
While security teams have improved their defenses against ransomware, there’s still one gaping weak spot that attackers are targeting for initial access, persistence, lateral movement, and more—network infrastructure.
State-sponsored APT actors continue to target network appliances, notably with the recent Volt Typhoon attacks against military targets, an APT28 campaign using JaguarTooth malware to target Cisco IOS, and BlackTech campaigns against multiple types of network routers (detailed in a joint NSA and CISA cybersecurity advisory).
In addition, this summer has seen a torrent of headlines about ransomware groups Akira, CACTUS, FIN8, and LockBit 3.0 targeting network appliances:
- In August, LockBit and Akira exploited a zero-day vulnerability on Cisco VPN appliances that were not configured for multi-factor authentication. It’s easy to say MFA is the solution, but it can be challenging to ensure compliance with your security policies.
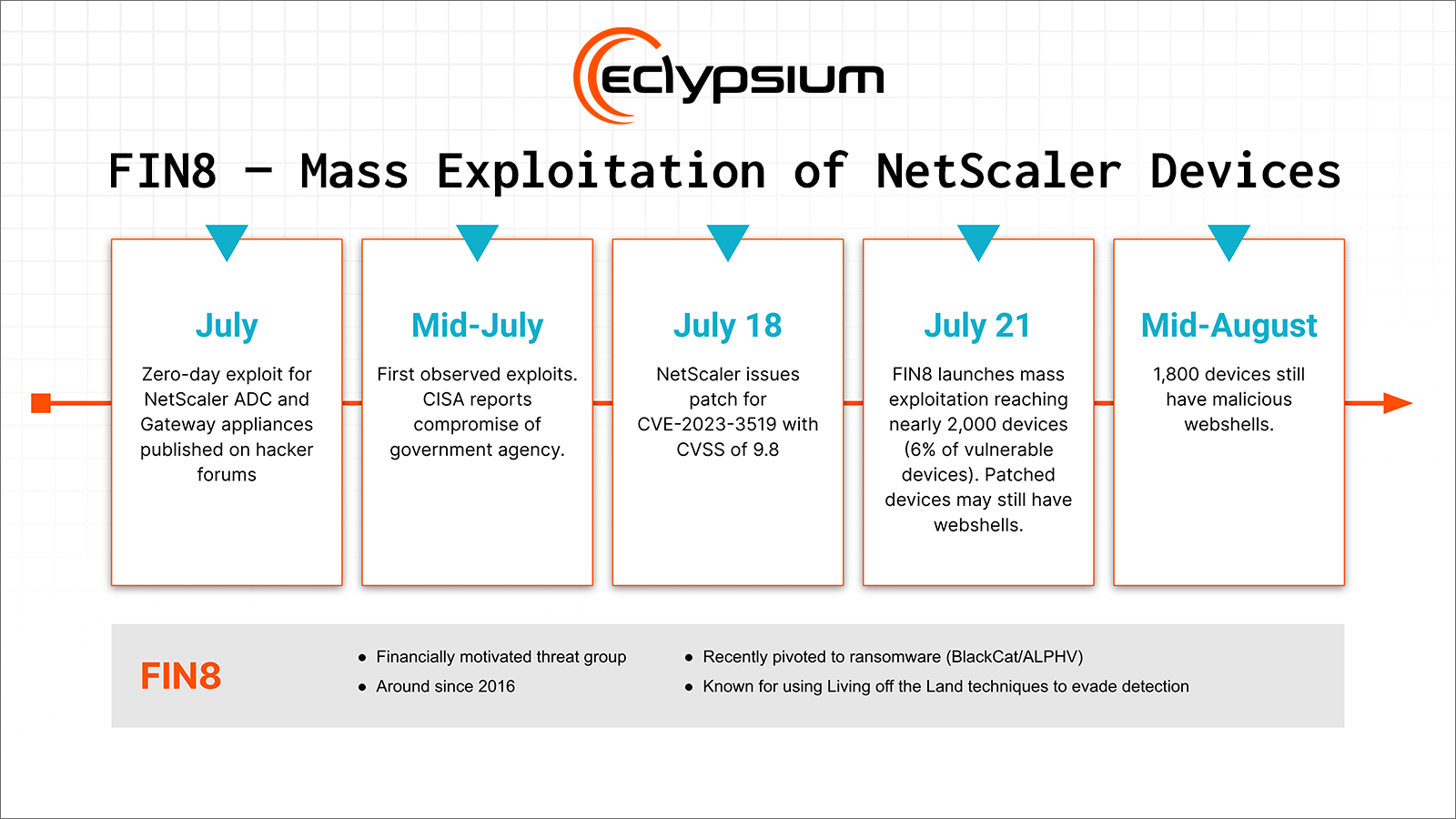
- In July, FIN8 installed webshells on nearly 2,000 unpatched Citrix NetScaler devices (6% of the vulnerable devices exposed to internet scans). It’s notable that the attackers were able to set up infrastructure for a mass exploitation campaign that outpaced defenders’ ability to patch since the update was released just days earlier. They installed webshells that persist even after the embedded OS is patched and rebooted. This last point is crucial because it requires careful investigation on the part of network administrators and security teams to inspect NetScaler access logs. FIN8 only started deploying ransomware recently, having previously been known for scraping data from point of sale systems.
- In June, Akira was discovered to be exploiting flaws in Fortinet VPN appliances including using a Python tool that chained vulnerabilities together.
- In May, CACTUS was reported to be attacking unspecified vulnerable VPN appliances.
This activity should not come as a surprise. We published research last year that warned about these types of attacks against network infrastructure and showed that:
- It was possible to use off-the-shelf C2 frameworks on load balancers
- Malware targeting these devices could persist across updates and reboots
- It was possible to infect devices so deeply that even a clean wipe and reinstall was not sufficient remediation
- These aforementioned goals were not beyond the skill of a motivated attacker who simply read through vendor documentation and used existing toolkits
Why Is Threat Detection on Network Devices So Hard?
Unfortunately, the status quo for security teams makes detecting these types of intrusions very difficult. For one thing, these appliances do not have EDR. There are limited and inconsistent detection and logging capabilities across makes and models. File integrity monitoring to alert for changes to backup and configuration files are also generally substandard or nonexistent.
Moreover, network devices are extremely varied and not well understood by security teams. These devices can be physical systems or virtual appliances deployed in a public cloud, each with their own unique firmware OS and configuration. Organizations often employ multiple types of network appliances as VPNs, gateways, firewalls, and load balancers—it’s a complex attack surface to defend! Network administrators who might be looking at the logs may not have the security expertise to understand when they are looking at an indicator of compromise.
Addressing a Major Gap in Ransomware Defenses
Over the past several months, Eclypsium has been expanding firmware OS integrity and threat detection capabilities to network devices by Cisco, F5 Networks, Fortinet, Juniper, NetScaler, and Palo Alto Networks, and will continue to expand to other network device manufacturers. The new capabilities are designed to look for compromise by known and new threats on physical and cloud (virtual) network appliances, and include monitoring for changes in firmware and OS binaries, modified configuration and backup files, reverse shells, persistence modules, and more.
The new threat detection and integrity monitoring augments our existing supply chain vulnerability and risk assessment of network devices, bringing EDR-like detection and response capabilities to network infrastructure.
The short video below shows how the Eclypsium supply chain security platform detects active compromise of a NetScaler appliance exploiting CVE-2023-3519 which was used in FIN8’s mass exploitation campaign this summer.
Network Infrastructure Has a Supply Chain Security Problem
As CISA Director Jen Easterly has said, organizations should expect IT products to ship securely by default. “We’ve normalized the fact that technology products are released to market with dozens, hundreds, or thousands of defects, when such poor construction would be unacceptable in any other critical field,” said Easterly.
That ransomware groups and APTs are seeing so much success targeting network infrastructure gear indicates a supply chain security problem with enterprise IT infrastructure in general. IT and security practitioners cannot blindly trust all manufacturers to ship these network appliances without vulnerabilities and to have well established and secure update processes. Instead, defenders need to anticipate and control the supply chain risk. The old approach of network scanning alone is neither effective nor sufficient, as security operations teams are overwhelmed and can’t keep up with constant patching of critical IT infrastructure. Eclypsium adds continuous monitoring and device integrity checks that are needed as compensating controls to detect ongoing compromise.
If you would like to take a look at our capabilities for protecting your network infrastructure, please schedule a demo. We also have a product tour that walks you through the platform (no form fill required).
The post A New Approach to Defending Network Infrastructure from Ransomware Groups and APTs appeared first on Eclypsium | Supply Chain Security for the Modern Enterprise.
*** This is a Security Bloggers Network syndicated blog from Eclypsium | Supply Chain Security for the Modern Enterprise authored by Chris Garland. Read the original post at: https://eclypsium.com/blog/a-new-approach-to-defending-network-infrastructure-from-ransomware-groups-and-apts/
如有侵权请联系:admin#unsafe.sh
