2023-10-5 05:22:51 Author: securityboulevard.com(查看原文) 阅读量:7 收藏

As a credit union member, I find myself thwarting inbound scam attempts far more often than I used to. Between fake phone calls with deceiving caller ID, phony Google ads placed atop search results, and bogus text messages, I have noticed much more activity this past year than I’m used to. Considering the state of online brand impersonations, I’d wager I am not the only one experiencing this.
Credit unions are under attack. To spread awareness of this threat, Allure Security has prepared a unique report – the first of its kind focusing solely on credit union brand impersonations online. Through the automated examination of millions of digital assets every day, We have observed a significant jump in impersonations throughout the year.
For this report, we carved out data specifically for credit unions impersonated from August 1, 2022, to March 31, 2023. What are you waiting for? Grab your copy of Allure Security’s SPOOF 23: Trends in Online Brand Impersonations for Credit Unions now.
The state of online impersonations of credit union brands
For our analysis, we categorized credit unions by asset size using the National Credit Union Administration’s (NCUA) established asset threshold tiers. These tiers span five ranges, from less than $1 billion to more than $20 billion in total assets under management (AUM).
From August 2022 to March 2023, 92% of detected impersonations were targeting credit unions with less than $10 billion in assets under management. In a handful of instances, credit unions with only $7 million in assets were impersonated.
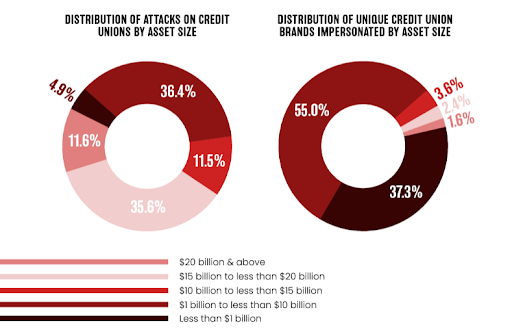
The data reveals a misconception: bigger credit unions aren’t the exclusive targets for impersonation. No credit union is immune from online brand impersonations. If you have members, you’re on a scammer’s radar.
Fraudsters in 2023 are impersonating more credit unions more often, underscoring the danger of this threat. One credit union in particular holding $15-$20 billion in assets found themselves slammed with an average of 32 brand impersonation attacks every single week.
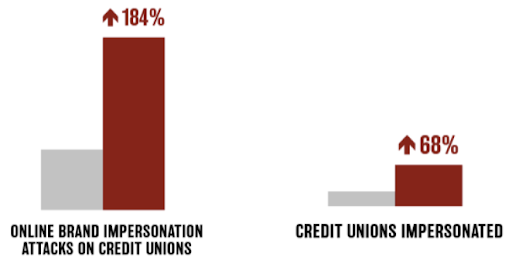
From the first quarter of 2022 to the first quarter of 2023, online credit union impersonations in general nearly tripled, increasing by 184%. The amount of individual credit unions targeted increased 68%.
Sneak peak into emerging online credit union brand threats
During the reporting period, we observed a handful of innovations scammers used to get their phishing websites in front of potential victims. While this isn’t the first time we’re seeing some of these tactics, their increase in frequency is certainly worth noting.
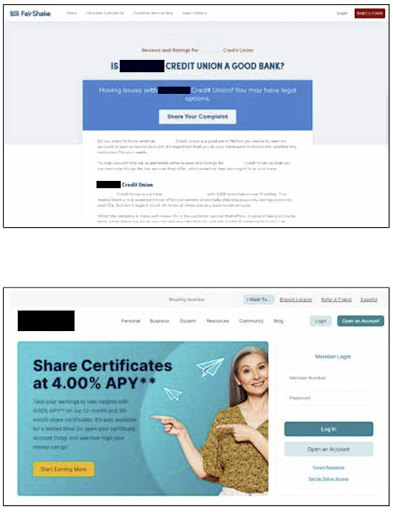
Impersonations of Fairshake brand morphing into credit union phishing sites
The scam we’ve dubbed “UnFAIRSHAKE” accounted for 40% of brand impersonations we detected in March 2023. This extended into the first week of April 2023.
It starts with fraudsters impersonating Fairshake, an organization that provides consumer rights services. Fairshake offers tips on filing complaints against companies, legal/arbitration services, and in some cases serve as a complaint repository themselves.
Fraudsters began cloning Fairshake complaint pages for a handful credit unions, as well as some regional and community banks. The Fairshake clones were hosted on domains that used permutations of the credit union’s brand name.
For more detail, download the report.
Using Google search ads as an invite vector for credit union phishing sites
In December of 2022, the FBI issued a public service announcement about online threats targeting customers of financial institutions. They warn about fraudsters impersonating brands with pay-per-click search engine advertisements which direct users to phishing websites.
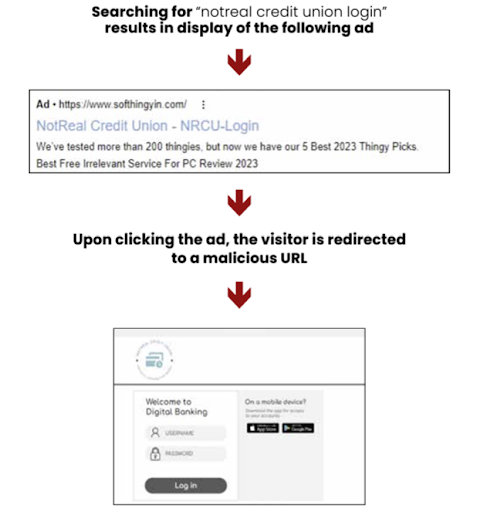
Fraudsters will set up a website that appears innocuous when accessed directly through its URL to avoid detection by brands examining deceptive variations of their domain name. However, when that same website is reached through the scammer’s Google ad, it generates a Google Click ID (GCID). This GCID tag acts as a trigger to activate the scam, redirecting the visitor to a phishing site that closely mimics the credit union brand they initially searched for. Learn more in the SPOOF23: Credit Unions report or check out our blog on the topic.
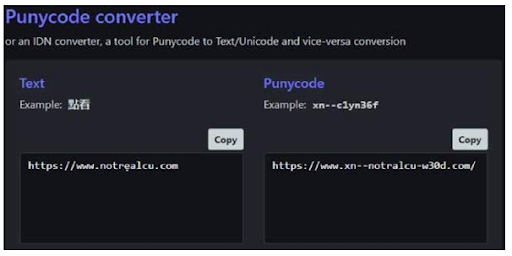
Using Punycode to create deceptive URLs to target credit union members
URLs are, for the most part, displayed using ASCII – a set of characters for computers that use primarily English. However, non-English speaking countries require the use of non-English characters. Punycode solves this problem by allowing for the display of characters not available in ASCII. Fraudsters will abuse it to create domain names that are deceptively similar to those of legitimate credit unions via non-English characters.
While this tactic isn’t exactly new, Allure Security observed an increase of Punycode related impersonations against credit unions in late December of 2022.
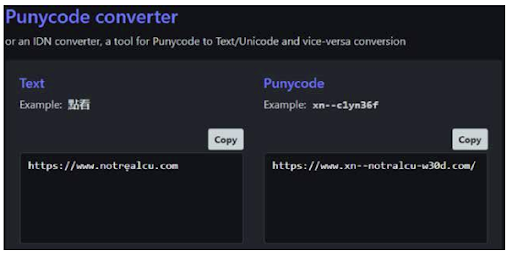
On the left, we have the PunyPhish URL as it is displayed in the browser. Note the “e” with a dot underneath. On the right is the punycode that enables the URL to use the lowercase “e” with a dot underneath.
Abusing dynamic DNS services to deceive credit union members
Dynamic DNS services help with matching the domain name system with dynamic IP addresses that change over time. Scammers have started abusing these services to create subdomains deceptively similar to that of a real credit union.

During the study period, we observed scammers consistently exploiting dynamic DNS service providers, with a noted increase in 2023.
To learn more about the methods and impact of dynamic DNS abuse for phishing purposes, check out our blog on the topic or download your copy of our one-of-a-kind 2023 Trends in Online Credit Union Impersonations report now.
WHAT YOU SHOULD DO NEXT
- Contact us if you’re ready to work with an expert to improve your visibility of and response to abuse of your brand online.
- Learn more about optimizing the people, processes, and technology driving your online brand protection with our free Busy Person’s Guide to Online Brand Protection.
Read our blog post about why Gartner® recognizes Allure Security as a provider of Digital Risk Protection Services and online brand protection.
*** This is a Security Bloggers Network syndicated blog from Allure Security authored by Mitch W. Read the original post at: https://alluresecurity.com/2023/10/04/exclusive-report-the-rise-of-credit-union-brand-impersonations-online-in-2023/
如有侵权请联系:admin#unsafe.sh
