![]()
This Cybersecurity Awareness Month, join GuidePoint Security for A Voyage Beyond the Horizon, a speculative exploration of possible scenarios that could be brought about if current technologies and security issues aren’t addressed. While the following short story may be far-fetched and unlikely, it’s inspired by our conversation with Kevin Woods and the issues he believes are important to address in the next one to five years.
Alex put the finishing touches on the final copy of the contract. It was always a pain when a job required documents in triplicate, but she charged a premium for the service because she had to re-check the letterblocks after every copy just to be sure nothing in the press had shifted. Everything had to be copied down exactly, and if a comma looked too much like a period it could ruin a client’s life. Alex was the best because her great-grandpa had spent so much time training her dad, and he had, in turn, trained her.
Apparently, her great-grandpa had worked in something called “cybersecurity” when he was younger, and when he started he was paid incredibly well because there was some kind of shortage of people to work those jobs. Alex had never really gotten all the details, but it sounded like her great-grandpa was in some kind of law enforcement fighting against criminals. She’d brought that up to her grandpa once and he’d tried to explain it to her, but she didn’t understand most of what he was talking about. What she did know is that as her great-grandpa got older, there were fewer and fewer people working on his side, because it was easier to make just as much money if you were willing to become a criminal.
About the time her grandpa was raising her dad, her great-grandpa had decided to teach his grandson how to survive in a world that didn’t use “computers”, whatever those were. Her grandpa thought he was losing his faculties, but her great-grandpa kept on insisting that it was too late and the world would have to go back to paper. So he taught her dad how to hand copy, how to keep papers safe, and how to transport important things discretely. Then, her dad taught her.
She had never quite figured out what a “computer” was, her dad had told her the last time he’d seen one was almost a decade before she was born. The descriptions of them in her history classes had been confusing, because as best as she could decipher, they were fancy collections of rocks that could do math and talk to each other. It sounded cool, but they were apparently what the criminals her great-grandpa fought against used to do their crimes.
Everything in the contracts looked good, so Alex carefully arranged each copy in its own folder and put them in the vault. She swung the big, iron door shut, cleared the combination lock, and twisted the large key clockwise and removed it. Her grandpa had always said that was the best way to store something securely, “Something you have, and something you know. Never just one or the other.”
She wrote a letter to her clients to let them know everything was ready and that she’d see them in a week so they could sign the documents and take over custody of them after that. She was excited for the trip, because sometimes her clients would invite her to stay and enjoy the rest of the day as thanks for her work. She would, because even though she didn’t personally know the clients beforehand, who could turn down a day at a wedding?
Okay, so that was a bit far-fetched, but imagine a major financial institution falling victim to a data breach because it lacked the manpower to detect a sophisticated malware attack. Picture a hospital held hostage by ransomware, leaving providers without access to critical medical records. These scenarios, once the stuff of dystopian fiction, could become chilling reality if we continue to disregard the importance of closing the cybersecurity skills gap.
Let’s take a look at our current situation and consider what might realistically happen if nothing changes.
The Losing Battle of Supply vs. Demand
As businesses, governments, and individuals race to adopt digital solutions, the demand for cybersecurity expertise has surged. Yet, the supply of qualified professionals remains alarmingly insufficient, dropping to 60% in the past year.
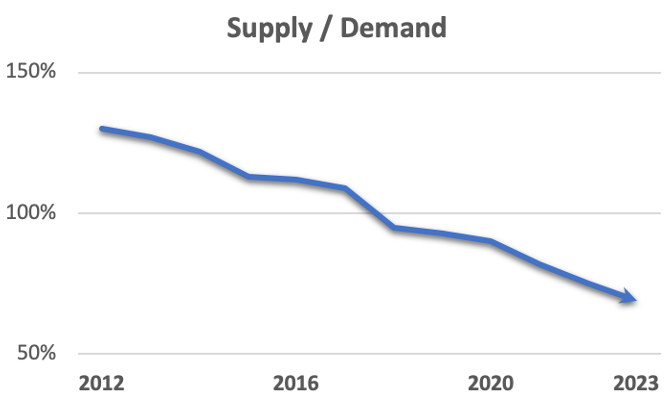
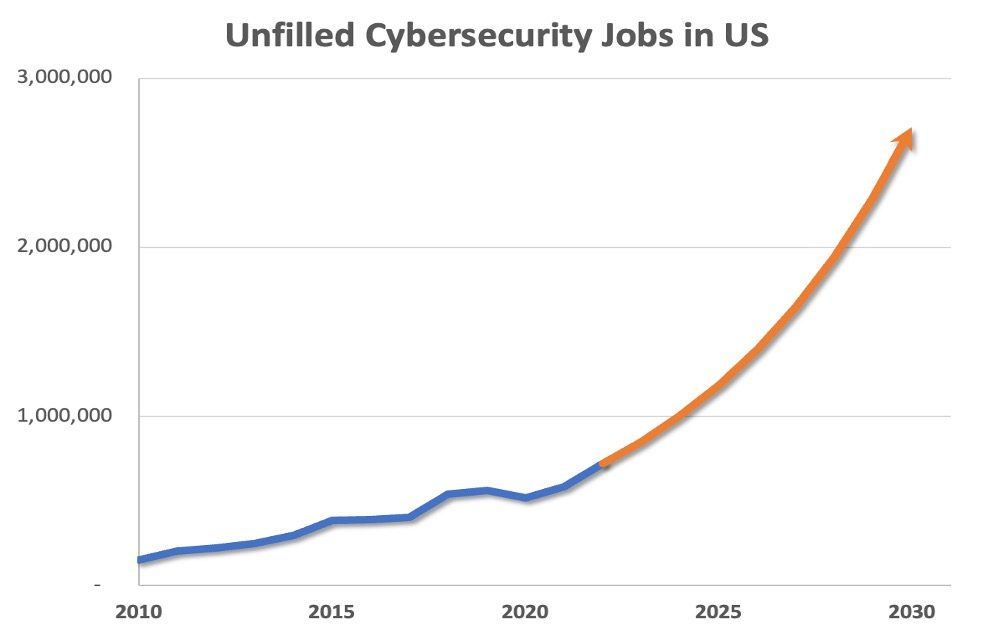
The shortage of skilled cyber defenders means that vulnerabilities in critical systems may go unnoticed and unaddressed for extended periods, leaving ample opportunities for cyber threats to take advantage. This demand problem is amplified as the industry continues to grow. Over the past decade, the number of unfilled cybersecurity jobs in the United States has more than tripled, leaving organizations more exposed than ever.
Furthermore, our nation’s security knowledge is aging out quickly. Approximately 60% of cybersecurity professionals in the United States are over the age of 40 (Zippia). Though it might be more convenient, we cannot continue to rely solely on experts already in the industry. Doing so will only exacerbate the skills gap and leave the industry defenseless when the current practitioners all retire in the next 20-30 years.
The Difficulty of Going Legitimate
Getting started in cybersecurity can be a formidable journey, marked by challenges that test one’s technical acumen, adaptability, and determination. Navigating the complex web of programming languages, network protocols, and security frameworks can be overwhelming, especially for beginners.
- Lack of Entry-Level Positions: Due to the high level of risk associated with my projects, companies are often unwilling to take chances on inexperienced talent. Many entry-level positions require a certain level of hands-on experience, which can be a catch-22 for newcomers who struggle to find initial opportunities.
- Extensive Training Costs: Acquiring the necessary education for a career in cybersecurity often comes with a significant financial investment that can be a daunting barrier for many aspiring professionals. Pursuing degrees, certifications, and training programs to build one’s resume can cost substantially more than learning hacking techniques.
- Outdated Training Programs: University programs, despite their high tuition fees, tend to have outdated curriculums that are decades behind the hackers. Even adaptable training programs are often unable to provide training on brand-name tools, due to vendor licensing issues.
The Pull of the Dark Side
The allure of becoming a hacker has grown stronger, and the pathways to this digital underworld are more accessible and more lucrative than the traditional journey to becoming a cybersecurity professional. As we explore this unsettling trend, we must confront the question: Are we inadvertently pushing talented individuals toward the dark side of the digital realm?
Let’s explore why hacking has become so alluring.
- Low Barriers to Entry: The tools and resources needed to initiate a cyber attack are more accessible than ever. With countless online forums, tutorials, and pre-packaged malware available, a curious mind with a computer can quickly transform into a budding cybercriminal.
- Potential for High Profits: Cybercrime has evolved into a sophisticated underground economy. Stolen data, ransomware attacks, and other malicious activities can yield substantial financial gains, often dwarfing the earnings of legitimate jobs.
- Counter-Culture Appeal: For some, hacking represents a rebellion against traditional norms and institutions. The notion of outsmarting corporations and governments fuels a counterculture narrative that appeals to younger generations that are disillusioned by societal structures.
Closing the Gap
Addressing the cybersecurity skills gap is a multifaceted challenge that requires a collective effort. Here are some steps that individuals, organizations, and governments can take to bridge this gap:
- Invest in Education and Training: Encourage the development of cybersecurity education programs at all levels, from middle school to college. Universities must be more willing to adapt and update curricula, while vendors should consider offering NFR licenses to training institutions.
- Create Organizational Development Programs: Start an internship or fellowship program and be willing to invest in the development of current employees and future hires. At GuidePoint Security, we started GuidePoint Security University (GPSU) to discover raw talent and develop the next wave of security consultants. Development programs like GPSU help mitigate much of the risk associated with hiring entry-level positions, while also providing a platform for upskilling current employees in new areas.
- Promote Diversity and Inclusion: Cybersecurity benefits from diverse perspectives. Encourage underrepresented groups to pursue careers in cybersecurity, ensuring a broader talent pool and fresh ideas.
- Collaboration and Information Sharing: Foster partnerships between academia, industry, and government to develop targeted solutions, share training resources, and provide practical experience for aspiring cybersecurity experts.
Summary
The truth is that it has become easier to embark on a hacking career than to pursue a legitimate one in cybersecurity. The vast pool of cybersecurity positions is well-documented, and newer talent isn’t given a chance, creating a void that hackers are more than willing to exploit. The disparity in incentives between joining the cybersecurity workforce and the illicit world of hacking has the potential to amplify the existing skills gap if no action is taken.
*** This is a Security Bloggers Network syndicated blog from The Guiding Point | GuidePoint Security authored by Kevin Woods. Read the original post at: https://www.guidepointsecurity.com/blog/cybersecurity-awareness-month-the-risks-of-ignoring-the-cybersecurity-skills-gap/

