2023-10-12 15:52:31 Author: securityaffairs.com(查看原文) 阅读量:18 收藏
Phishing, the campaigns that are targeting Italy

This post analyzed the numerous phishing campaigns targeting users and organizations in Italy.
Phishing is a ploy to trick users into revealing personal or financial information through an e-mail, Web site, and even through instant messaging. Particularly very popular is so-called brand phishing, which occurs when criminals impersonate the official website of a well-known brand of a public or private entity using a domain name, URL, logos and graphics similar to the original website: This is a real threat that can have heavy repercussions on user privacy and device security. Phishing can also be used as a precursor attack to drop malware.
The phenomenon in numbers
Numerous reports from the Italian Postal Police (https://www.commissariatodips.it/index.html) confirm CERT-AgID’s weekly data (https://cert-agid.gov.it/category/news/) on phishing campaigns involving dozens of exploited brands, including Poste Italiane, Intesa Sanpaolo, Nexi, Inps, Agenzia delle Entrate and Zimbra. Just to name a few.
Credits: https://cert-agid.gov.it/statistiche/ – Data for the past 30 days
Exprivia cybercime report also confirms that phishing is the leading type of attack with a 180% increase in the second quarter of 2023. https://www.industriaitaliana.it/report-exprivia-cybercrime-minaccia-sicurezza-talia-q2-2023/
Phishing to be successful must gain the victim’s unwitting cooperation
As mentioned, an attack can begin by sending an e-mail/sms with a link that redirects the user to a fake web page that mimics a legitimate site to steal sensitive information via forms. All the information provided is delivered to a server run by the scammers.
Fortunately, disclosure campaigns against this type of scam by public institutions and private companies are constant and frequent. However, unsuspecting users, trusting the identity of the sender and the veracity of the messages, make the usual mistake: providing credentials, pins and other personal data through channels not conventionally used by the impersonated services.
The following is a description of some of the campaigns that have targeted Italy.
Posteinfo, confirm your identity
Using spoofing techniques, a text message ostensibly from Posteinfo collected in the history of legitimate messages invites identity confirmation to avoid bank account suspension.
The link leads to a site in the guise of “Poste Italiane.” A popup invites you to proceed, and with a series of cascading pages, the scammers try to collect credentials, phone number and approximate available balance, then continue the scam over the phone (vishing).
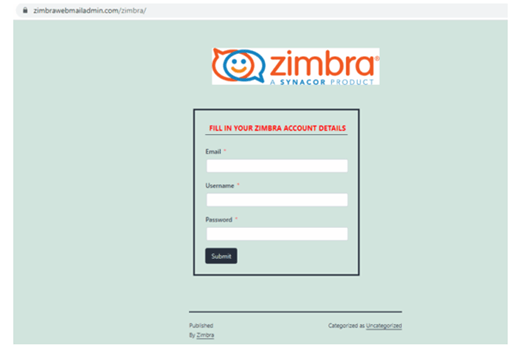
Update your Zimbra webmail
A classic example of fake technical support for urgent Zimbra application updates. In this case, the link in the message text points to a domain with a name that invokes an alleged zimbra webmail admin service.
In reality, the form with the counterfeit logos is designed to send in an HTTP POST request the e-mail address, username, and password to a listening server operated by the scammers.
Confirm the use of the Nexi card
In this case, a fake e-mail alludes to a request for confirmation of credit card use by the cardholder, to avoid blocking the same card.
In this case to resist spam filters, the link is hidden within an image that mimics the text of the message, so that interception by text recognition is difficult (you click on the image and the landing page immediately opens).
Careful analysis reveals typical elements that may indicate that this is a fake site. The URL has nothing to do with Nexi’s official portal (https://www.nexi.it/), but leads only to a web page of a fraudulent domain. The actually active part of the web page is only the embedded form titled “Confirm Use.” All other elements are non-clickable, except for the links related to the guides that actually point to parts of the legitimate Nexi site.
The form requests the holder’s name, the identification details of the payment card and its security code Key6 (the code usually made available to Nexi payment card holders).
In reality, the entered and confirmed data will be sent via a PHP page with an HTTP POST request to a DB server listening on the same domain.
Meanwhile while the victim, only as a distraction, is asked to enter an SMS code he should have received, all the data provided is delivered into the hands of the criminals.
How to protect yourself
All of these attacks always exploit people’s mistakes and naivety, which will lead to more and more people falling victim to phishing if proper measures are not taken. To protect yourself from phishing, it is advisable to combine a security solution with prudent behavior:
- read the details of the e-mail header carefully, verifying the veracity of the sender’s identity;
- check grammar and spelling in the text and subject line of messages. Spelling errors can be a red flag;
- Avoid shared and public PCs and newsletter unsubscribe links.
In addition, it is good to keep in mind that HTTPS gives no guarantee that a site is trustworthy. It is Impossible to distinguish between legitimate sites and phishing sites based only on the contents of their SSL certificates. HTTPS only indicates that the transmission of data between client and server is done by encrypting information (the letter S, the green padlock, and the certificate cannot give guarantees about the reliability of a site).
What to do in case of a scam
Unfortunately, it can happen that one falls into the trap of phishing, even with all the necessary precautions. In this case, one must act immediately, without panic or fear:
- Immediately change the password of the targeted service;
- Activate two-factor authentication, if you have not already done so;
- Contact the targeted organisation and the police.
About the author: Salvatore Lombardo
Electronics engineer and Clusit member, for some time now, espousing the principle of conscious education, he has been writing for several online magazine on information security. He is also the author of the book “La Gestione della Cyber Security nella Pubblica Amministrazione”. “Education improves awareness” is his slogan.
Twitter @Slvlombardo
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, phishing)
如有侵权请联系:admin#unsafe.sh







