2023-10-13 12:46:38 Author: riskybiznews.substack.com(查看原文) 阅读量:19 收藏
This newsletter is brought to you by Netwrix, an IT security software company that enables security professionals to strengthen their security and compliance posture across all three primary attack vectors: data, identity, and infrastructure. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Microsoft has announced plans to disable support for the NTLM authentication protocol in a future version of Windows 11.
Even if Microsoft has not put out a hard cut-off date, this is good news regardless, as it sets the stage for the protocol to be removed after 30 years of use.
Short for New Technology LAN Manager, the protocol was introduced in 1993 with the release of Windows NT 3.1. It was the primary user authentication protocol until Windows 2000, when it was replaced by Kerberos.
Since then, NTLM has been included in Windows as a backup authentication protocol for legacy purposes and in situations where Kerberos couldn't work properly. This included offline/local use or (segmented) network topologies where there was no direct line-of-sight to a Domain Controller.
Microsoft says that it is (very well) aware of these issues, and that's why instead of a hard-disable, it will first fix Kerberos' shortcomings first.
The company says it is working on two new Kerberos features named IAKerb and local KDC that will allow Kerberos to work "in more diverse network topologies" and in offline/local scenarios where there's no Domain Controller available.
These features will gradually make their way into Windows 11, but not Windows 10, which is closer to its End-of-Support than most people realize (ahem, two years and one day—October 14, 2025).
The company is also adding tools and logging capabilities to monitor NTLM usage in corporate environments, along with finer-grained group policies to disable or block NTLM.
Once NTLM usage goes down, Microsoft says it will pull the plug and announce a hard date when the protocol will be disabled in Windows 11.
"Reducing the use of NTLM will ultimately culminate in it being disabled in Windows 11. We are taking a data-driven approach and monitoring reductions in NTLM usage to determine when it will be safe to disable."
The news of NTLM's upcoming removal comes on the same week that Microsoft also took VBScript behind the shed.
3Commas hacked again: Cryptocurrency trading platform 3Commas has confirmed a security breach after hackers gained access to customer accounts and made unauthorized transactions. The company didn't reveal how many funds were stolen. This is the company's second breach in the past year. It was also hacked in October of last year after a hacker gained access to its infrastructure and stole customer API keys.
Platypus hacked for the third time: DeFi trading service Platypus has lost more than $2 million worth of crypto assets after an attacker gained access to its systems. The incident marks the third time the platform was hacked this year after suffering similar breaches in January and July. It lost $8.5 million in the first hack and just $50,000 in the second.
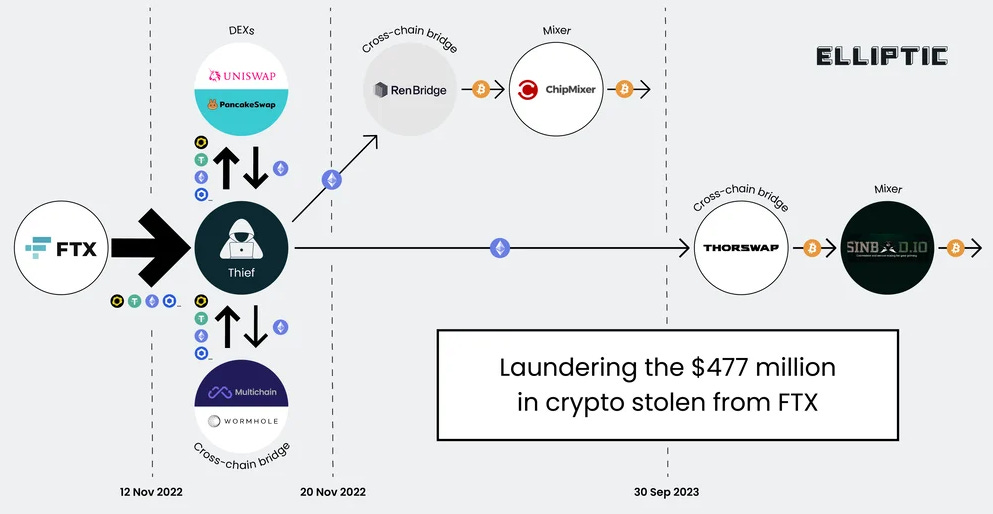
FTX hack trail leads back to Russia: An Elliptic investigation found that some of the $477 million crypto assets stolen from cryptocurrency exchange FTX lead back to money laundering accounts that have ties with the Russian cybercrime ecosystem. [Additional coverage in Wired/non-paywall]
"A Russia-linked actor seems a stronger possibility. Of the stolen assets that can be traced through ChipMixer, significant amounts are combined with funds from Russia-linked criminal groups, including ransomware gangs and darknet markets, before being sent to exchanges. This points to the involvement of a broker or other intermediary with a nexus in Russia."
Shadow PC breach: Cloud gaming PC service Shadow has disclosed [archived] a security breach after some of the company's customer data was put up for sale on an underground hacking forum. The incident took place in September after one of its employees was socially-engineered in a Discord chat. The attacker compromised the employee's computer with malware, stole access cookies from the employee's browser, and then accessed the Shadow backend and stole customer data. The company says no passwords or financial data was stolen, but the attacker made off with most user personal data, such as names, emails, billing addresses, and dates of birth.
OneinStack supply chain attacks: Threat actors have compromised the servers of OneinStack, a one-click Linux server deployment utility. In two separate incidents in April and October this year, the attackers modified the OneinStack binaries and added a code that would load and enable a secret backdoor. Chinese security firm QiAnXin says the code used in the two incidents suggests the same threat actor was behind both attacks. The OneinStack tool is very popular in China, where it is used by developers to deploy Linux servers on cloud infrastructure in various production-ready configurations.
23andMe: DNA and genetic testing service 23andMe has confirmed that hackers stole some data after initially denying they got hacked last week. The company is now resetting all user passwords. There's more to this story, but I can't tell what's b.s. and not, so I'll come back to this when things clear up. Meantime, you can read TechCrunch's coverage of what's what right now.
SEC is investigating Progress Software: The US Securities and Exchange Commission has launched a formal investigation into Progress Software, the company behind the MOVEit file-sharing server. According to a regulatory filing, Progress says the SEC has started a fact-finding investigation and is seeking documents from the company related to how the company handled a string of hacks of its MOVEit software earlier this year. Progress says the attacks have incurred $2.9 million in costs so far, but that $1.9 million has already been covered through its insurance. The company also expects to face additional losses, as it currently faces 58 class-action lawsuits, and at least 23 customers have announced their intention to ask for compensation related to the hacks. [Additional coverage in CybersecurityDive]
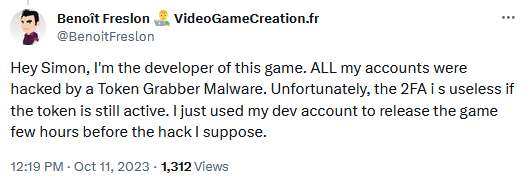
Steam malware incidents: Valve is requiring that all developers add a phone number to their account in order to publish new game updates on the Steam platform. The company made the decision after several developers had their accounts compromised and hackers pushed malware-laced game updates to some of its users. The phone number will be used for two-factor authentication. Developers will have to add a phone number by October 24, or they will be unable to update any of their games.
Microsoft IRS audit: The US Internal Revenue Service has notified Microsoft that the company owes $28.9 billion in back taxes. The decision comes following an IRS audit that looked at how Microsoft allocated profits between countries and jurisdictions between 2004 and 2013. Microsoft says it plans to appeal the decision.
TETRA code going open-source: ETSI, the organization behind the TETRA communications protocol, is considering open-sourcing some of its newer protocols and algorithms after researchers found a series of backdoors in its code in July this year.
Chrome serves propaganda in Russia: An investigation has found that Google Chrome's Discover feed is serving up state-backed propaganda to Russian users. [Additional coverage in Bloomberg/non-paywall]
Quick Chrome history deletion: Google has announced a new feature for its Chrome browser that will allow users to quickly delete the last 15 minutes of their browsing history. The feature is different from incognito windows because it allows access to information like session cookies that would not usually be available in incognito mode. The feature can be found in the same place as the normal Clear Browsing History command.
Twitter in trouble in the EU: The European Union has sent a letter to Twitter this week warning that the company was spreading disinformation in the aftermath of the Hamas attacks on Israel. The EU Commissioner for Internal Market Thierry Breton has given Twitter CEO Elon Musk 24 hours to take action and respond to the letter. The company is very likely in violation of the EU's new Digital Services Act, which entered into effect at the end of August. Several news outlets found that Twitter was flooded with graphic content and disinformation, with Musk himself promoting some of the content. [Additional coverage in CNBC]
Delete Act: California Governor Gavin Newsom has signed a bill into law that allows Californians to request that their personal data be deleted from the servers of online companies. Named the Delete Act, the law is modeled after the EU's GDPR regulation. The law also tasks the California Privacy Protection Agency with creating a single portal where individuals could order data brokers registered in the state to delete their personal data. The agency must launch the portal by January 1, 2026. [Additional coverage in The Verge]
Netherlands investigates Yandex: The Dutch Data Protection Agency is investigating Yango, the ride-hailing app owned by Russian tech group Yandex. Officials fear Russian secret services might abuse the app to gather data on EU citizens. The app is facing similar investigations in Finland and Norway. [Additional coverage in ChannelNewsAsia]
In this Risky Business News sponsor interview, Tom Uren asks Martin Cannard, VP of Product Strategy at Netwrix, how privileged access management can help defend organizations. "Advanced Persistent Teenagers" regularly use social engineering techniques to compromise highly privileged accounts, but that doesn't mean it's instantly game over.
Fair Russia is fair: Russian authorities have detained a Yekaterinburg man for including a Facebook button on the website of an NGO. The suspect was detained because Facebook is considered a terrorist organization in Russia and absolutely 100% not because he's the lead of a human rights organization that has sued the Russian government for the living conditions in its jails. Nope. Not that! [Additional coverage in Veved]
PyPI malware: DevSecOps companies Checkmarx and Phylum have discovered a series of malicious libraries on the PyPI portal, posing as the SDKs of various cloud service providers. The packages contained functional code but also included a hidden mechanism that stole any authentication tokens and credentials added by developers. So far, researchers have identified five malicious SDKs targeting AWS, Alibaba Cloud, Tencent, and Telegram services.
NuGet malware: Security researchers have found malicious NuGet packages infecting developer systems with the SeroXen RAT. Only a handful of malicious packages were discovered, all uploaded on NuGet by one developer account.
KEV update: CISA has updated its KEV database with five new vulnerabilities that are currently being exploited in the wild. The list includes the three zero-days from this week's Microsoft Patch Tuesday, a Cisco zero-day from last month, and an Adobe Reader bug that was patched back in January but is now being exploited.
LinkedIn Smart Links abuse: Threat actors are abusing a LinkedIn feature named Smart Links to bypass security email gateways. The feature is used by LinkedIn paying customers to track who clicks on their links by passing all traffic through the official LinkedIn domain. Researchers at Cofense say they've seen this feature abused for the first time in September 2022 and again in a new campaign started in July this year. The recent campaign leveraged a LinkedIn smart link but eventually redirected users to a phishing site that attempted to harvest their Microsoft credentials.
Magniber ransomware: AhnLab says the last time it detected the Magniber ransomware was on August 25, representing the longest period of inactivity for the ransomware gang since 2016.
"Since its initial appearance in 2016, Magniber has never taken a break from distribution for such a long period of time (usually resuming distribution with a new technique to bypass detection within 2 weeks to a month)."
DarkEye Stealer is back and free: CyFirma security researcher Kaushík Pał has discovered a threat actor distributing a version of the old DarkEye Stealer for free. That's exactly what we needed—free advanced malware.
Anonymous Sudan Telegram stats: Threat intel analyst Julian Botham has noticed that the follower count of the Anonymous Sudan Telegram channel has nearly doubled over the past week since the group has announced its intention to attack Israeli organizations in the aftermath of the Hamas attack on Israel.
Ransomware in Q3: CyberInt has a breakdown of ransomware operations in the third quarter of the year.
AvosLocker: CISA and the FBI have published an update for their malware report on the AvosLocker ransomware. The original report was published in March 2022, so it became outdated.
Qakbot: Blackberry looks at Qakbot, the botnet that was recently taken down by the FBI and EU authorities.
DarkGate: Trend Micro reports an uptick in campaigns distributing the new DarkGate loader via Skype and Microsoft Teams conversations.
Nexus: Two security researchers have found an SQLi vulnerability in the Nexus Android botnet and used it to gain access to its backend and gather intelligence on its operations. The botnet is a variant of the old SOVA Android botnet that launched earlier this year, advertised on underground hacking forums.
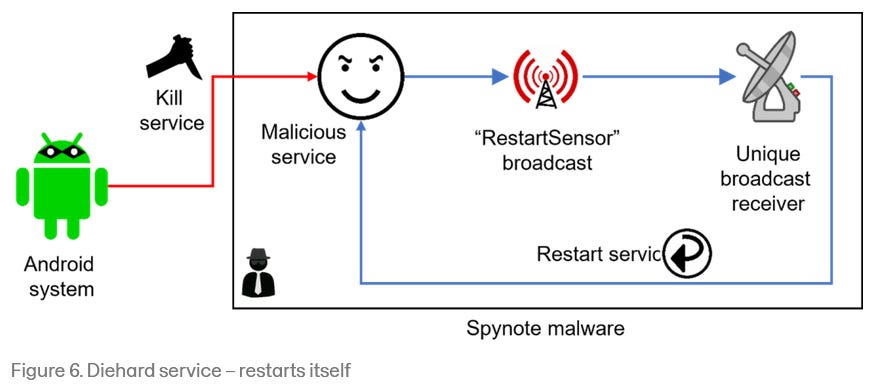
SpyNote: WithSecure has published a report on the SpyNote Android malware and its Diehard service that makes shutting down and removing the malware from infected hosts as difficult as possible.
To protect your business, you need to understand and measure your attack surface and then implement a continuous, comprehensive approach to reducing it. Read Netwrix's guide to learn how to reduce your privileged attack surface and adopt a Zero Trust approach.
Storm-0062: A suspected Chinese cyber-espionage group is behind the recent attacks that have exploited a zero-day vulnerability in Atlassian Confluence servers. Tracked as CVE-2023-22515, the vulnerability was patched last week, but Microsoft says the group has been exploiting it since mid-September. Microsoft linked the attacks to a group the company tracks as Storm-0062. While the company didn't formally link the attacks to China, it says the same group is also known as DarkShadow and Oro0lxy. In 2020, the US Justice Department indicted an employee of China's Ministry of State Security named Li Xiaoyu, who operated using the "Oro0lxy" nickname and had been involved in MSS hacking campaigns for at least ten years.
ToddyCat: Check Point and Kaspersky have seen the ToddyCat APT executing a persistent hacking and cyber-espionage campaign against the telecom industry in Asia. The campaign has been active since 2021 and has targeted telecoms located in Vietnam, Uzbekistan, Pakistan, and Kazakhstan. The group has been previously linked to Chinese espionage interests.
Patching priority confusion: A survey of 1,000 IT professionals found that vulnerability scanning and management tools often produce different results that confuse DevOps teams. Nearly three-quarters of respondents say their organizations can take anywhere from two weeks to a month to patch known critical vulnerabilities. Respondents say they spend too much time determining what needs to be fixed first, which has impacted their delivery schedules throughout the past year and even their bottom lines.
cURL security update: The cURL library has patched a rare security vulnerability in its code. The bug is tracked as CVE-2023-38545, and it's a heap buffer overflow in the library's SOCKS5 proxy handshake. The library's author has a write-up here.
Magento patch: A major vulnerability has been fixed in the Adobe Commerce platform and the Magento open-source project. The vulnerability allows threat actors to bypass authentication procedures and hijack any Magento customer account. Patches have been released this week as part of Adobe's Patch Tuesday updates. A technical analysis of the bug will be available via SanSec.
Apple security updates: Apple has backported its recent patches against two zero-days to its older iOS 16.x branch. Initial patches for the iOS 17.x branch were delivered last week.
Squid vulnerabilities: Security researcher Joshua Rogers has discovered 55 vulnerabilities in the highly popular Squid caching proxy. The vulnerabilities were found during a security audit that began in February 2021. Of the 55 vulnerabilities, Rogers says the Squid Team only managed to patch 20. Rogers blamed the lack of patches for all issues on the team's understaffing. The Squid proxy is one of today's most ubiquitous apps, with more than 2.5 million instances available online.
"The Squid Team have been helpful and supportive during the process of reporting these issues. However, they are effectively understaffed, and simply do not have the resources to fix the discovered issues. Hammering them with demands to fix the issues won't get far."
Yifan vulnerabilities: Cisco Talos researchers have discovered ten vulnerabilities in Yifan YF325, a cellular router used in industrial networks. All ten vulnerabilities are rated critical and have a severity score of 9.8/10. All ten remain unpatched after the vendor has failed to respond to Cisco's disclosure attempt.
OctoPrint vulnerability: Numen Labs has found a vulnerability (CVE-2023-41047) in the OctoPrint 3D printer that can be abused to execute arbitrary commands.
WS_FTP exploitation: SentinelOne has a write-up of the recent attacks targeting WS_FTP servers.
Windows zero-day report: Google Project Zero has a technical write-up on CVE-2023-36802, a zero-day in the Windows Kernel Streaming Server that Microsoft patched last month in September. IBM published a similar report earlier this week.
Microsoft AI Bug Bounty Program: Microsoft has announced a new bug bounty program that will pay bug hunters for issues in the company's Bing AI system. Rewards can go up to $15,000.
Acquisition news: Cybersecurity firm Arctic Wolf has announced plans to acquire security orchestration, automation, and response (SOAR) platform Revelstoke.
New tool—CCB Browser Extension: The Belgian government has developed a Chrome browser extension that shows trustworthiness scores for websites and warns users of phishing attempts.
New tool—machofile: Security researcher Pasquale Stirparo has open-sourced machofile, a tool for parsing Mach-O binary files.
Useful tool: OSINT threat analyst Cipher387 has put together a list of APIs that can be used for OSINT investigations.
Useful tool: Another useful tool is Dangerzone, a tool from the Freedom of the Press Foundation that takes suspicious PDFs and converts them into safe-to-view documents.
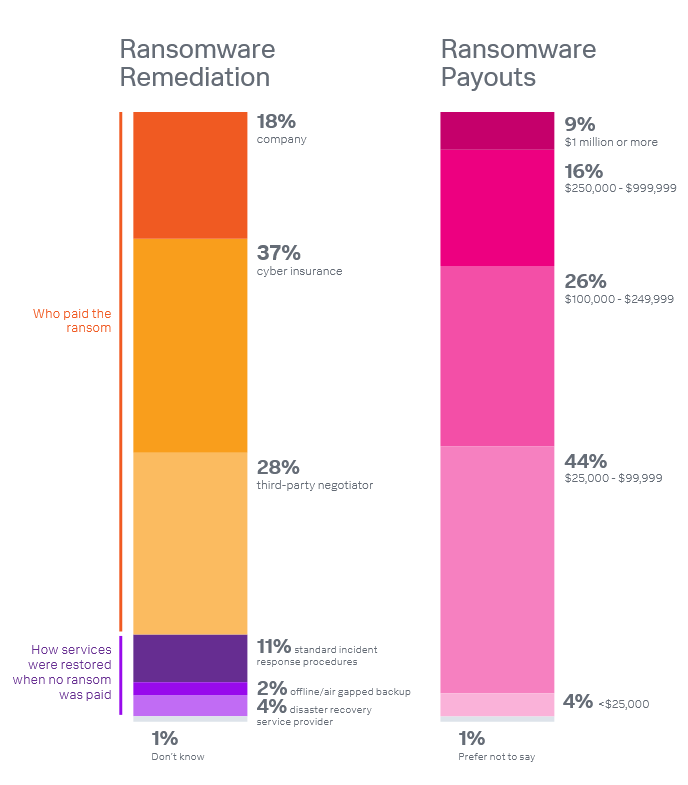
Ransomware payments: A Splunk survey of 350 CISOs found that 96% worked for companies that got hit by ransomware over the past year, and a whopping 83% ended up paying the attackers. The survey found that the vast majority paid the attackers through an intermediary, such as a negotiator or their cyber insurance provider. A quarter of all paid ransoms were above $250,000, making the attacks a very lucrative business for ransomware gangs. [Additional coverage on the Splunk website]
"The cyber insurance process has changed over the past few years. It is getting to the point where we are wondering if it is worth our time."
In this edition of Between Two Nerds, Tom Uren and The Grugq examine the opportunities that ransomware gangs and business email compromise/romance scammers have to collaborate.
如有侵权请联系:admin#unsafe.sh