2023-10-15 15:37:38 Author: securityboulevard.com(查看原文) 阅读量:21 收藏
Introduction
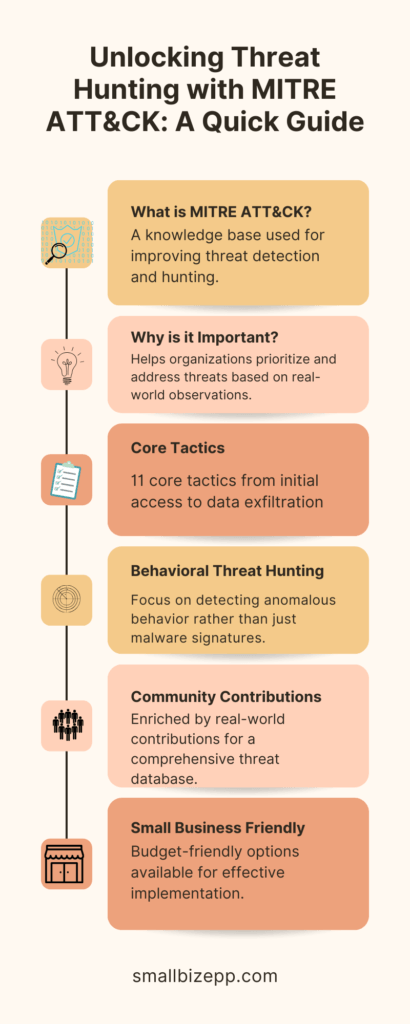
In today’s rapidly evolving cyber landscape, proactive threat hunting is no longer a luxury—it’s a necessity. Gone are the days when traditional security measures could fully protect your network. Now, you need to actively seek out potential threats before they wreak havoc. That’s where the MITRE ATT&CK framework comes into play. Designed as a robust knowledge base, MITRE ATT&CK equips you with the insights needed to identify and counteract threats effectively. As such, this article will help equip you to use MITRE ATT&CK for threat hunting.
For a quick grasp of this powerful tool, check out the infographic below. It distills the essence of MITRE ATT&CK and its pivotal role in modern threat hunting.
If you’re already familiar with the basics of MITRE ATT&CK from my previous article, this post will take you a step further. We’ll delve deeper into how you can leverage this framework for effective threat hunting, especially tailored for small businesses. So, let’s dive in.
Why MITRE ATT&CK is Crucial for Effective Threat Hunting
MITRE ATT&CK serves as a comprehensive knowledge base that revolutionizes threat hunting. With its detailed matrix of tactics, techniques, and procedures (TTPs), it provides a structured approach to identifying adversarial behavior. This is invaluable for IT personnel, especially those with limited cybersecurity knowledge, as it simplifies the complex landscape of threat hunting.
Real-World Applications
- APT29 (Cozy Bear) Attack: MITRE ATT&CK’s TTPs were instrumental in identifying and understanding the tactics of APT29, a Russian cyber espionage group. The group used spear-phishing techniques to gain initial access and later moved laterally across the network. The ATT&CK framework helped cybersecurity experts to trace the attack tactics and respond effectively.
- WannaCry Ransomware Attack: The infamous WannaCry ransomware attack affected hundreds of thousands of computers worldwide. MITRE ATT&CK helped in understanding the ransomware’s propagation methods, which included exploiting Windows SMB vulnerabilities. This understanding aided in quicker incident response and mitigation.
By understanding these real-world applications, it becomes evident that MITRE ATT&CK is not just theoretical but a practical tool for effective threat hunting.
Understanding the MITRE ATT&CK Matrix
The MITRE ATT&CK Matrix is more than just a table; it’s a roadmap for understanding adversary behavior. Below, you’ll find a breakdown of the matrix and its 11 core tactics that guide effective threat hunting.
The 11 Core Tactics
- Initial Access: The first step an adversary takes to infiltrate your network. This could be through spear-phishing, exploiting public-facing applications, or using valid accounts.
- Execution: Once inside, the attacker executes their code to gain control or extract data. This could involve running a malicious script or command.
- Persistence: Ensuring they maintain their foothold even if the system restarts. Methods include creating startup items or scheduled tasks.
- Privilege Escalation: Gaining higher-level permissions to access restricted areas. This often involves exploiting system vulnerabilities.
- Defense Evasion: Techniques to avoid detection. This could involve disabling security software or obfuscating malicious code.
- Credential Access: Stealing login information, often through keylogging or credential dumping.
- Discovery: Gathering information about the system or network to further the attack. This could involve identifying running processes or network connections.
- Lateral Movement: Moving through the network to reach the desired data or system. Techniques include using Remote Desktop Protocol (RDP) or SSH.
- Collection: Aggregating the data they plan to extract. This could involve compressing files or taking screenshots.
- Exfiltration: The act of sending the collected data out of the target network. Methods include FTP transfers or cloud storage.
- Impact: The final blow, often involving data destruction or encryption for ransom.
Understanding these 11 tactics is crucial for effective threat hunting. They provide a structured approach to identifying and mitigating risks. Thus making the MITRE ATT&CK Matrix an invaluable tool for any cybersecurity strategy.
Behavioral Threat Hunting: A Practical Approach
Behavioral threat hunting goes beyond traditional methods by focusing on abnormal activities or patterns that may indicate a security threat. It’s not just about identifying known malware but about uncovering sophisticated attacks that evade traditional detection systems.
Example 1: Detecting Lateral Movement
One of the tactics in the MITRE ATT&CK Matrix is “Lateral Movement”. Behavioral analysis can spot unusual login activities across multiple systems. These activities could indicate a threat actor moving laterally inside the network.
Example 2: Unusual Data Access
Another adversarial tactic is “Collection”, where an attacker gathers data of interest. Behavioral threat hunting can identify abnormal data access patterns. Patterns like a user suddenly downloading large amounts of sensitive data, which could be a sign of data exfiltration.
By integrating MITRE ATT&CK’s comprehensive tactics and techniques into your behavioral threat hunting, you can significantly enhance your security posture. For a deeper dive into these tactics, you can visit the MITRE ATT&CK Matrix.
How Small Businesses Can Benefit
Implementing a robust cybersecurity framework like MITRE ATT&CK might seem like a daunting and expensive task, especially for small businesses. However, there are budget-friendly ways to leverage this powerful tool for enhanced security.
Open-Source Tools
Many open-source tools align with the MITRE ATT&CK framework, offering cost-effective solutions for threat hunting and incident response.
Employee Training
Investing in employee training can be a cost-effective way to implement MITRE ATT&CK. Educated staff can better recognize threats, reducing the risk of successful attacks.
Phased Implementation
You don’t have to implement the entire framework at once. Start with the most critical tactics like “Initial Access” and “Execution,” and gradually expand as your budget allows.
Managed Services
For businesses with limited in-house IT expertise, managed security services can be a cost-effective way to implement MITRE ATT&CK. Many providers offer scalable solutions tailored to small businesses.
Community Resources
MITRE itself, along with various cybersecurity communities, offers a wealth of free resources, guides, and templates to help businesses of all sizes implement the ATT&CK framework.
By adopting these budget-friendly approaches, small businesses can effectively implement the MITRE ATT&CK framework without breaking the bank.
Real-World Observations: Learning from Past Incidents
The WannaCry ransomware attack serves as a compelling real-world example of how the MITRE ATT&CK framework can be invaluable in identifying, understanding, and mitigating cyber threats at various stages.
| Timeframe | Event Description | MITRE ATT&CK Tactic | How ATT&CK Could Help |
|---|---|---|---|
| T0 | Initial Infection | Initial Access | Identifying spear-phishing emails or malicious attachments could prevent initial access. |
| T0 + 1hr | Malware Execution | Execution | Monitoring for unusual script or command-line execution could flag the ransomware. |
| T0 + 2hrs | Lateral Movement | Lateral Movement | Detecting abnormal login activities or RDP usage could indicate lateral movement. |
| T0 + 3hrs | Privilege Escalation | Privilege Escalation | Monitoring for unexpected system or file changes could detect privilege escalation. |
| T0 + 4hrs | Data Encryption | Impact | Identifying abnormal file modifications could flag the encryption process. |
| T0 + 5hrs | Ransom Note Displayed | Impact | Quick identification of ransom notes or screen changes could confirm an attack. |
| T0 + 6hrs | Data Exfiltration | Exfiltration | Monitoring network traffic for large data transfers could detect exfiltration. |
From the initial infection to data exfiltration, the framework provides actionable tactics and techniques that could have significantly altered the outcome of this devastating attack. For instance, the “Initial Access” tactic could have helped in recognizing spear-phishing emails, thereby preventing the ransomware from gaining its initial foothold.
The timeline graphic above illustrates how applying MITRE ATT&CK’s tactics could have helped at each critical juncture. It’s not just a theoretical exercise but a practical guide for businesses to understand the dynamics of cyber threats and how to counteract them effectively.
By studying past incidents through the lens of MITRE ATT&CK, organizations can better prepare for future threats, making it an essential tool in modern cybersecurity.
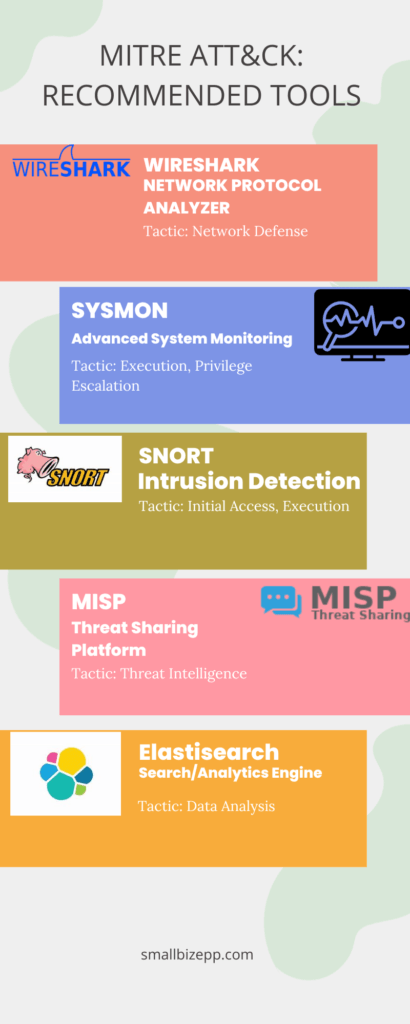
Tools and Resources for Implementing MITRE ATT&CK
Navigating the complexities of the MITRE ATT&CK framework becomes significantly easier with the right tools and resources. The open-source community, in particular, offers invaluable support.
Open-Source Tools
Open-source tools are a cornerstone for implementing the MITRE ATT&CK framework effectively. Let’s delve into some of the tools featured in the infographic above:
- Wireshark: This network protocol analyzer is indispensable for network defense. Wireshark aligns well with MITRE ATT&CK’s Network Defense tactic, helping you monitor and analyze your network traffic in real-time.
- Sysmon: A go-to for advanced system monitoring, Sysmon is particularly useful for tactics like Execution and Privilege Escalation. Sysmon provides detailed information about system activities, aiding in quicker threat detection.
- Snort: As an intrusion detection system, Snort is crucial for countering Initial Access and Execution tactics. It monitors network traffic and can detect various types of attacks, making it a versatile tool.
- MISP: The Malware Information Sharing Platform (MISP) is a community-driven threat sharing platform. It aligns with the Threat Intelligence tactic, allowing you to share and receive information about current threats.
- Elasticsearch: This search and analytics engine is excellent for Data Analysis, helping you sift through large datasets to identify anomalies or patterns that could indicate a security threat.
Community Contributions
Beyond tools, the cybersecurity community offers a wealth of resources. GitHub repositories, forums, and specialized groups provide templates, advice, and scripts that can help you tailor the MITRE ATT&CK framework to your specific needs.
By utilizing these open-source tools and tapping into community contributions, you’re well on your way to implementing a robust, cost-effective MITRE ATT&CK strategy.
Common Pitfalls and How to Avoid Them
Implementing the MITRE ATT&CK framework for threat hunting is a complex task, and it’s easy to make mistakes along the way. Being aware of these pitfalls can save you time, resources, and potentially, your network’s security.
Overlooking Initial Access
Pitfall: Many organizations focus on later stages of an attack, neglecting the Initial Access tactic.
Tip: Prioritize monitoring entry points like email and web traffic to catch threats before they escalate.
Ignoring Data Analysis
Pitfall: Failing to properly analyze collected data can lead to missed threats.
Tip: Use tools like Elasticsearch to sift through data and identify anomalies effectively.
Inadequate Staff Training
Pitfall: Without proper training, even the best tools are ineffective.
Tip: Invest in regular staff training sessions that align with MITRE ATT&CK tactics and techniques.
Not Leveraging Community Resources
Pitfall: Many organizations don’t take advantage of the wealth of community-contributed resources.
Tip: Engage with online forums, GitHub repositories, and other platforms to stay updated and get community support.
Failing to Update
Pitfall: Cyber threats evolve, but your implementation of MITRE ATT&CK may not.
Tip: Regularly update your tactics and tools to align with the latest version of the MITRE ATT&CK framework.
By being aware of these common mistakes and taking proactive steps to avoid them, you can implement the MITRE ATT&CK framework more effectively and securely.
Conclusion and Next Steps
In summary, the MITRE ATT&CK framework serves as an invaluable resource for effective threat hunting. From understanding its matrix and tactics to leveraging open-source tools and community contributions, implementing this framework can significantly bolster your cybersecurity efforts. However, it’s crucial to be aware of common pitfalls and continuously update your approach to stay ahead of evolving threats.
We encourage you to share your thoughts, experiences, and questions in the comments section below. Your insights could be the missing piece someone else needs to effectively implement MITRE ATT&CK in their organization.
Thank you for reading, and we look forward to engaging with you in the comments!
The post Unlock Threat Hunting with MITRE ATT&CK: A 2023 Guide You Can’t Miss appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/threat-hunting-with-mitre-attck/?utm_source=rss&utm_medium=rss&utm_campaign=threat-hunting-with-mitre-attck
如有侵权请联系:admin#unsafe.sh
