2023-10-17 14:46:47 Author: blog.qualys.com(查看原文) 阅读量:8 收藏
Runtime Software Composition Analysis with the Qualys Cloud Agent
In a blog post published last week, we discussed the importance of managing risk across software developed in-house. A great deal of that risk is introduced by vulnerabilities in open-source packages like Log4Shell, OpenSSL, etc.
Regretfully, even though zero-day threats pose a great deal of risk at the point of production, there never has been a solution that truly solves this problem head-on.
Until now…
Qualys is excited to launch Runtime Software Composition Analysis (Runtime SCA). Qualys Cloud Agent is taking software composition to the next level to solve OSS-related and software supply chain risks. But before we dive into Runtime SCA, let us discuss the challenges associated with OSS and existing software composition tools.
What Is Open-Source Software (OSS) and the Risks Associated With Using Open-Source Components
Open-source software components are at the core of modern software development. A sizable portion of codebases in contemporary applications comprises these packages, and studies have shown that:
- 96% of code bases contained open-source software (OSS), and 48% included high-risk vulns.
- 91% of packages had OSS with no development activity in the last two years.
- The average code base incorporates 56 vulnerable open-source packages per asset, and 41% had an exploitable vulnerability.
Embracing open-source methodologies enables developers to bring products to market faster and with greater functionality by leveraging pre-existing, community-vetted code, eliminating the need to reinvent the wheel.
However, the surge in the use of open-source components during application development has increased the risk of exploitation of vulnerabilities within the application. Related risks for the software supply chain are now a significant concern, as evidenced by recent attacks on MOVEit, 3CX, Log4j, SolarWinds, and others.
The lack of visibility and transparency into proprietary and open-source dependencies within the software supply chain elevates security and compliance risks. When software package assessments are done, they rely on disjointed, standalone tools owned and managed by different teams.
As a result, effective risk management in such disparate environments becomes impossible, which means software packages are likely to be exposed to risks that are “unseen” by SecOps teams.
What is Software Composition Analysis?
Software Composition Analysis (SCA) is crucial to any robust security strategy. It focuses on identifying and managing your applications’ open-source and third-party components. While these components often bring tremendous value regarding time savings and functionality, they can also introduce hidden vulnerabilities that attackers can exploit.
SCA helps you understand the components in your software stack, empowering developers to harness the potential of open-source packages while managing the risk to your organization. At the same time, SCA ensures organizations remain shielded from avoidable vulnerabilities and legal and compliance concerns.
There are a wide variety of tools available to help with SCA today, but they come with significant challenges:
- Limitations of Traditional Vulnerability Scanners: Traditional vulnerability scanners assess software vulnerabilities only and cannot drill down into the associated software components. This leaves a huge security risk in deeply embedded open-source packages and commercial software components. Security teams face challenges comprehending the true risk, particularly in security breaches like the Log4J incident.
- No Visibility Into Production Risks: Most common solutions today cater to CI/CD workflows, focusing on detecting vulnerabilities in software components before they are put into production. This proactive approach works well for known vulnerabilities but does nothing to help find and remediate vulnerable software packages that may already be in production.
- More Noise, Less Risk Context: Many organizations experience vulnerability fatigue. Vulnerability management programs have become complicated, intricate, and challenging to follow, lacking clarity and efficiency in execution. Monitoring vulnerabilities associated with software components can make the problem worse.
- Disparate & Manual Processes: Organizations struggle to get an integrated actionable view and automation for handling their vulnerabilities. Point solutions using different resource-intensive tools are difficult and expensive to integrate into broader vulnerability management programs, creating multiple, incomplete views of risk.
Siloed products and data make it challenging to get the answers you need. Limited dashboards hinder the ability to monitor, track, and report on security vulnerabilities, IT risks, and compliance posture effectively. Without clear visibility into the risks and their potential impact on the organization, decision-makers often struggle to make informed choices and prioritize resources efficiently.
Introducing Qualys Runtime Software Composition Analysis
In response to these challenges, Qualys has added Runtime Software Composition Analysis capabilities into the Qualys Cloud Agent. This empowers the Cloud Agent to detect, manage, and reduce the risk of software supply chain vulnerabilities in the production environment without introducing new infrastructure, tools, or processes.
Runtime Software Composition Analysis offers continuous and real-time visibility of deeply embedded open-source packages and commercial software components in producing first-party and third-party applications on Windows and Linux operating systems.
It determines the associated risk of these applications with innovative threat detection, leveraging a single, powerful Qualys Cloud Agent. It provides visibility into your software supply chain, empowering security teams to address potential risks and fortifying applications against emerging threats.
It can be enabled in a single click and scans for vulnerabilities in open-source components developed for Java, Go, .NET, Python, Node JS, Rust, Ruby, PHP, and more. The addition of SCA broadens VMDR scanning capability by adding more than 15,000 new signatures covering more than 12,000 Common Vulnerabilities and Exposures (CVEs).
It’s important to note that in the SCA category, Qualys offers comprehensive coverage for the most widespread and significant vulnerabilities, including Denial of Service (DoS), Regular Expression Denial of Service (ReDoS), Privilege Escalation, Directory/Path traversal, SQL Injection, and even the deserialization of trusted data, among others.
With this advancement, you can customize the scan to meet unique environment needs, including the ability to target a specific path to crawl or expand the scope to increase coverage, and can configure separate scan intervals, CPU usage, and more
You will get seamless integration with your existing workflows for Vulnerability Management, enabling efficient and automated reporting without disrupting your existing risk management process.
Check the following tutorial video to learn how to use Qualys Cloud Agent for Runtime SCA.
Key Benefits of the Runtime Software Composition Analysis With Qualys Cloud Agent
The new Qualys platform capabilities allow teams to:
1. Identify, Prioritize & Respond to Vulnerabilities in Open-Source Embedded Packages in Production From Day Zero: Runtime SCA delivers continuous, real-time visibility into deeply embedded open-source software packages and commercial software components, such as Log4j, OpenSSL, and commercial software components leveraging the Qualys Cloud Agent.
This continuous visibility is beneficial in understanding your exposure in first and third-party applications when a zero-day notification breaks out that potentially affects a popular library

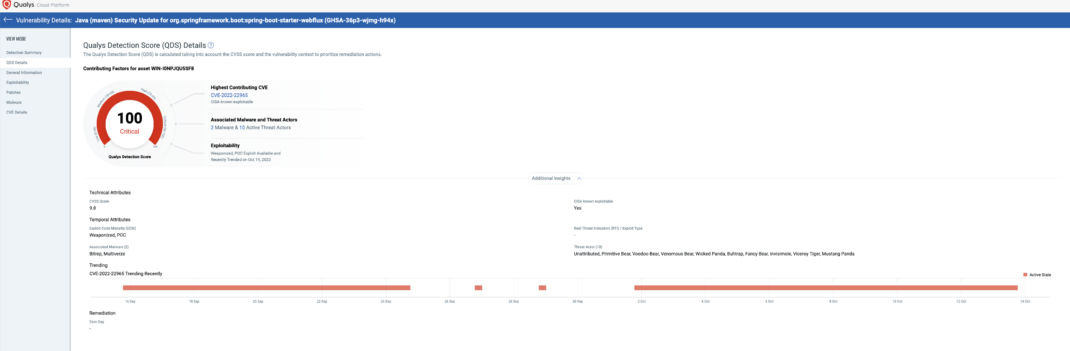
2. Actionable Insights and Risk Assessment: Generating real-time insights into every component operating in the production environment empowers security teams with the actionable insights they need to drive down risk. Runtime SCA delivers detailed reports highlighting vulnerabilities, their severity levels, their potential impact on your software ecosystem, and recommendations for remediation.

3. Reduce Vulnerability Noise and Prioritize With Confidence: Qualys TruRisk prioritizes and correlates the information based on data from over 25 threat feeds and the asset’s business criticality. This information allows security teams to rapidly mitigate the risk of high-profile security issues by crafting custom detection and responses. It significantly reduces the mean time to remediate urgent threats.

4. Effectively Communicate Risk With Unified Reporting and Dashboards: Utilize native Qualys VMDR workflow integration to effectively display a unified view of risk in first and third-party software to stakeholders through real-time dashboards. Integrating ticketing systems like ServiceNow and JIRA, the process of assigning detailed remediation tasks to the appropriate personnel is automated.
This centralized approach expedites ticket closure and risk reduction, eliminating the need for manual scripting or the challenges of identifying deeply embedded packages.
Conclusion
Qualys’s major release introduces groundbreaking solutions to help you effectively address the task of identifying and mitigating vulnerabilities in open-source packages, such as Log4Shell and OpenSSL, in production from Day Zero. By gaining visibility into your software supply chain and proactively addressing potential risks, you can fortify your applications against emerging threats.
Stay one step ahead of attackers with Qualys SCA and strengthen your software security today.
Get Started with Runtime SCA Now
To learn more on how Qualys can help with security and compliance in your organization:
- Contact your Qualys Technical Account Manager
- Start a Qualys Trial at no extra cost
如有侵权请联系:admin#unsafe.sh
