2023-10-18 19:19:24 Author: securityboulevard.com(查看原文) 阅读量:10 收藏
The History of Cyber Security: From Simple Passwords to On-Demand Cyber Risk Quantification
In merely a few decades, technological pioneers developed an unprecedented ability for society to access and store data in immeasurable quantities. This newfound power transformed many aspects of the physical world into a digital one, taking everyday activities such as banking, gaming, shopping, and socializing online.
With this monumental shift, as with most forms of progress, also came malicious actors seeking to exploit the new avenue to privileged data, leveraging methods from phishing to ransomware. But as these cyber crooks discovered new vulnerabilities within the cyber realm, so too did experts devise increasingly sophisticated strategies to combat them.
From the humble beginnings of password protection to the more complex web of firewalls, intrusion detection systems, and predictive threat solutions illuminating the probability of an organization experiencing a cyber threat and its relatively financial impact, cybersecurity has undergone exponentially rapid changes to keep up with an ever-changing landscape.
Today, when cyberattacks reverberate through every sector, and the average data breach costs upwards of $4.45M, the importance of introducing a robust cyber risk mitigation program has never been more pronounced. By knowing this history, organizations can better equip themselves with the necessary, innovative tools that safeguard sensitive data, ensuring business continuity and economic success.
Computer Password Protection
In the early 1960s, the Massachusetts Institute of Technology (MIT) developed one of the world’s first operating systems: the Compatible Time-Sharing System (CTSS). The computer scientists working on the CTTS all shared a common mainframe and used a single disk file, giving each researcher access to the other’s data.
When they realized this liability, a team member, Fernando Corbató, proposed establishing passwords for each scientist, ensuring information privacy. Subsequently, whenever they signed into the first-generation computer, the tech wizards needed to input a unique string of characters before they could access their research.
The IBM “Hackathon”
The International Business Machines Corporation, more commonly known as IBM, introduced a state-of-the-art mainframe computer in 1967 designed to handle various tasks, from scientific calculations to business data processing. As a part of its promotional campaign, IBM invited computer science students to explore the new system.
Allegedly, during their visit, these tech-savvy visiting students uncovered vulnerabilities and discovered parts of the system the IBM team had intended to keep private. This pivotal moment served as a wake-up call for those in the computing industry, demonstrating the need for more robust measures to protect against unauthorized access and potential breaches.
Creepers, Reapers, and the Official Birth of Cybersecurity
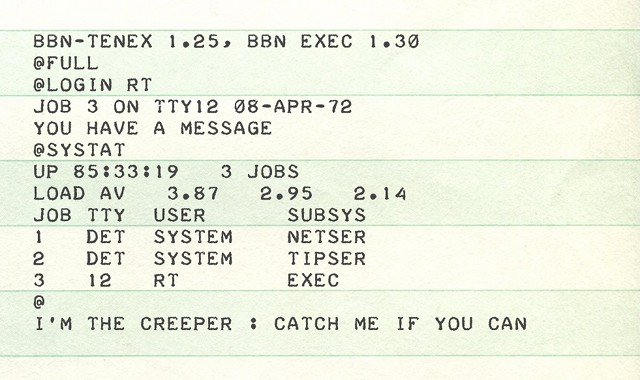
Bob Thomas coded the earliest wide-area pack-switch network in 1969, ARPANET, enabling resource sharing between remote computers. A few years after release, Thomas decided to test for any system weaknesses, developing an early version of a computer worm that crept from endpoint to endpoint, delivering the message “I’m the Creeper: Catch me if you can.”

Ray Tomlinson, Thomas’ colleague and email innovator, subsequently created the Reaper program to detect and remove the Creeper as it moved and self-replicated (an ability Tomlinson added to Thomas’ original worm) across the network. The Reaper is considered the first antivirus.
High-Profile Attacks and Commercial Antivirus Software
In the following decade, major corporations, including National CSS, AT&T, and the infamous Los Alamos National Laboratory, fell victim to cyber incidents. The 1980s also gave rise to the popular terms “Trojan Horse” and “computer virus” as these types of cyber attacks became more commonplace.
Responding to the threat, computer scientists capitalized on Tomlinson’s initial efforts and introduced commercially available antivirus software. In 1987, two German inventors released the first-ever antivirus program for Atari ST Computers. FlushShot Plus was released by Ross Greenberg, and Anti4us by Erwin Lanting shortly afterward.
That same year, British-American computer programmer John McAfee founded his eponymous company and developed VirusScan. Ultimately, 1987 proved to be a pivotal year for cybersecurity, ensuring those early purchasers of home computers could safeguard their information from malicious actors.
Upgrading the Cyber Arsenal for a Web-Based Era
The 1990s marked an era of unprecedented growth in internet usage as the World Wide Web’s protocol and code became available, royalty-free, in 1993. To protect browsers against increasingly sophisticated viruses, such as DiskKiller, engineers introduced Secure Sockets Layer (SSL), laying the groundwork for HyperText Transfer Protocol Secure (HTTPS).
These encryption-based cybersecurity protocols proliferated and matured well into the 21st century with TLS, IPSec, and WPA. Unfortunately, bad actors, too, found new vulnerabilities to exploit, such as credit card hacking, as online payment activities soared. Governments worldwide began enacting regulations to punish those failing to protect their cyber environments adequately.
Fortifying Defenses and Ensuring Anonymity for the New Millenium
The first generation of firewalls for business was distributed in 1994, but their security capabilities became more pronounced in the 2000s. On top of filtering potentially malicious packets, the second generation of this perimeter-securing technology focused on application visibility and UTM.
In 2008, Palo Alto Networks unveiled their next-generation firewalls (NGFWs) that ensured sensitive data could only be accessed by authorized parties, offering greater user identity awareness and increased protection. Their latest firewall update, released in 2020, harnesses machine learning for real-time protection.
The early 2000s also led to a more widespread use of virtual private networks (VPNs). Although first harnessed by large-scale corporations, individuals soon began to adopt this technology, hoping to protect their online privacy. In 2023, roughly 1.5 people worldwide use a VPN for business and personal use to safeguard their identities and access geo-specific content.
Nowadays, organizations typically adopt a multi-layered approach and take advantage of the plethora of cybersecurity tools available, including but not limited to:
- Intrusion Detection and Prevention Systems (IDS and IPS)
- Endpoint Security Solutions
- Security Information and Event Management (SIEM) Systems
- Data Loss Prevention (DLP) Software
- Network Security Scanners
- Multi-Factor Authentication (MFA)
- Patch Management Software
The Rise of Cyber Risk Quantification in the 21st Century
As the digital landscape expanded, organizations, particularly those most susceptible to wide-scale, expensive data breaches, began realizing they needed to take more proactive steps to protect their operations against attacks. To do so, security teams employed risk quantification, a mathematical model first harnessed during World War II.
The ultimate goal of these early forms of cyber risk quantification (CRQ) was to provide businesses with a comprehensive, data-driven understanding of the likelihood of experiencing cyber incidents and their respective operational impacts.
Leveraging Modern Financial CRQ Assessments for Robust Cybersecurity Programs
Today, CRQ providers such as Kovrr employ techniques, such as probabilistic modeling, that leverage real-world data to produce highly accurate assessments of annual cyber incident vulnerabilities.
These assessments likewise give businesses insights into how much financial loss they are expected to suffer from cyber activities and what cost-effective mitigation actions they can take to mitigate these implications. Financial CRQ helps organizations prioritize resources for the most pressing issues, ensuring long-term success.
To learn more about financial CRQ and how to calculate cyber risk, read “What Is Cyber Risk Quantification (CRQ)?”.
Preparing for the Future of Cyber With Quantification
Cybersecurity has made a remarkable journey from the humble beginnings of simple passwords and impromptu hackathons to the more sophisticated financial cyber risk quantification realm. Along the way, the industry has witnessed the birth of antivirus software, robust encryption protocols, and the constant battle against evolving threats.
In today’s dynamic cyber landscape, enterprises must take proactive (compared to reactive) measures to counteract the most significant potential threats. A financial CRQ reveals which of these potential incidents should be attended to first, allowing security teams to make data-driven decisions that safeguard the organization in the coming year.
Schedule a free demo today to learn more about how Kovrr’s financial CRQ assessment harnesses historical data to equip your organization for the future.
如有侵权请联系:admin#unsafe.sh
