October marked the beginning of the 20th-annual Cybersecurity Awareness Month whereas each year, the National Cybersecurity Alliance partners with the U.S. Department of Homeland Security to provide organizations with resources they need to promote digital safety. This year’s theme–Secure Our World–emphasizes the role everyone plays in cybersecurity.
While advances in technology and automated security measures play a crucial role in fortifying cyber defenses, the human element remains an indispensable part of an effective cybersecurity program. Cybersecurity is not just about deploying firewalls, encryption, or endpoint software. It’s about empowering individuals within an organization to make informed decisions regarding security policies and practices. These decisions directly impact the security posture and resilience of the organization.
Understanding the Human Element in Cybersecurity
Human involvement is essential because, despite improved security controls, human error remains the primary cause of security breaches, contributing to over 95% of incidents. This year’s campaign emphasizes the best practices individuals should follow to follow basic security hygiene standards, including:
- Use strong passwords.
- Turn on multifactor authentication (MFA).
- Recognize and report phishing attacks.
- Regularly update software.
Security teams are at the forefront of this human element, responsible for understanding the organization’s unique risks and developing strategies to mitigate them. They assess the threat landscape, design security policies, and educate employees to adhere to these policies.
However, implementing policies is only the first step; enforcing them is equally crucial. That’s where continuous controls monitoring (CCM) capabilities play a complementary role. CCM not only aids in policy implementation, but also in enforcing measures that significantly reduce the attack surface.
Continuous controls monitoring (CCM) involves real-time monitoring of security controls to ensure they are working effectively and in compliance with established security policies, offering a proactive approach to identifying and addressing potential exposures promptly.
Let’s explore the core capabilities of implementing CCM with the help of cyber asset attack surface management (CAASM) technology.
- Continuous Monitoring and Alerts
Phishing has now become the most common cyber-attack vector, now responsible for 16% of all data breaches [1]. Yet, one-third [2] of us either lack the know-how, never, or rarely report phishing.
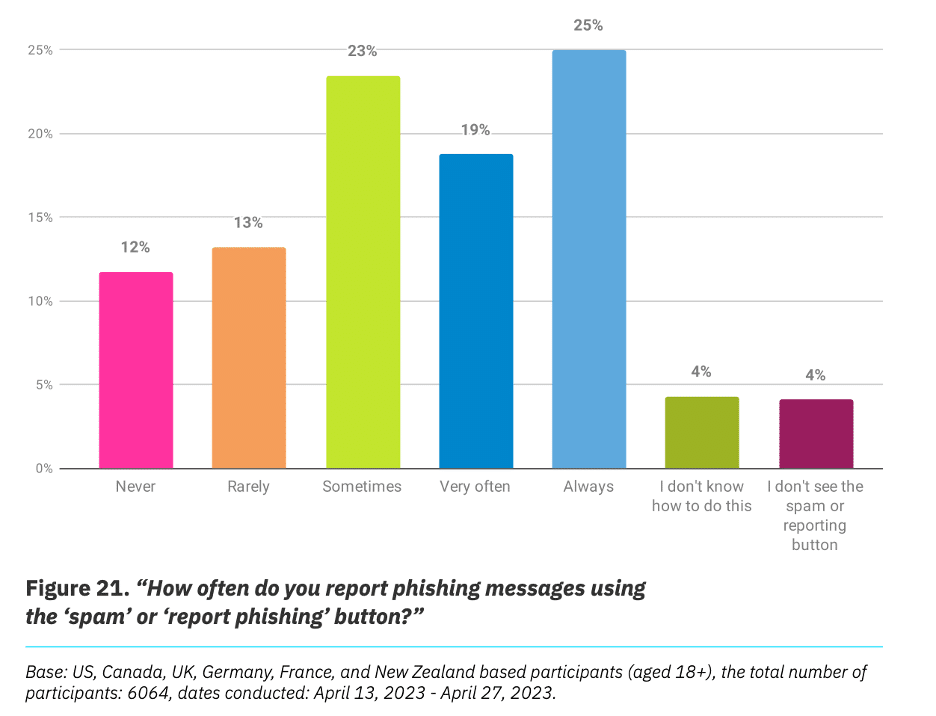
Source: NSA, 2023 Cybersecurity Attitudes and Behaviors Report
Fortunately, CCM can be used to continuously review the effectiveness of the organization’s email security filters, anti-malware, and other technical control barriers. Additionally, CAASM tools can identify where users have administrative accounts without MFA enabled, and/ or incomplete security training. This limits the likelihood of a phishing attack being successful, thereby reducing the risk of unauthorized access to sensitive information.
- Dynamic Risk Assessment
Breaches that originate via stolen or compromised credentials and malicious insiders go undetected the longest. According to IBM’s Cost of a Data Breach report, it takes an average of nearly 11 months to identify and contain breaches initiated using stolen credentials, and about 10 months to resolve those from a malicious insider.
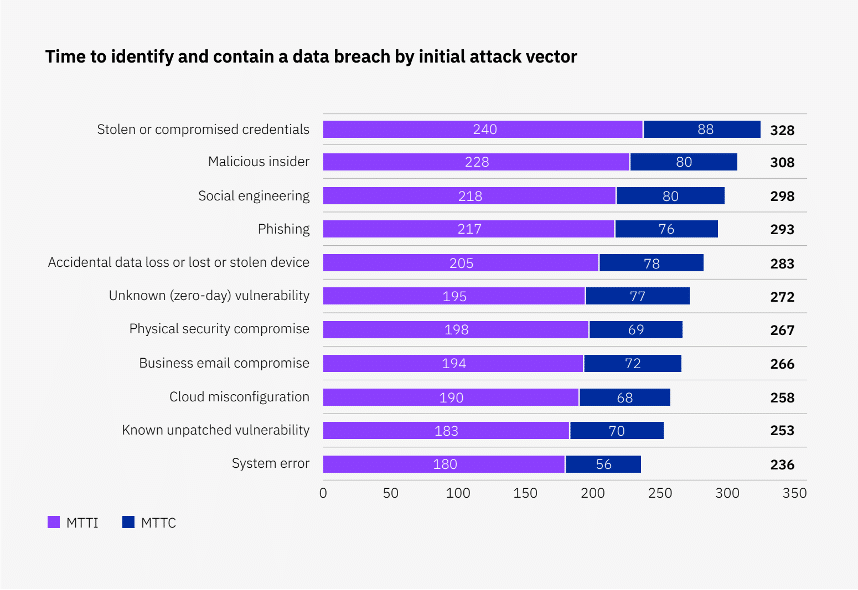
Source: IBM, 2023 Cost of a Data Breach Report
The dynamic relationship maps generated by CAASM can be leveraged alongside tools such as Privileged Account Management (PAM) software, enabling organizations to continuously monitor user access rights and permissions. If a user’s access privileges exceed what is necessary for their role, alerts can be generated, prompting a review and adjustment of permissions to maintain a least-privileged access approach.
- Policy Adherence and Reporting
Despite most companies now having a multi-factor authentication (MFA) policy in place, a staggering 33% of employees [2] admit they do not use MFA at all. Security policies, guidelines, and procedures are only as effective as their adoption and adherence by personnel.
By continuously monitoring security controls, CCM can assess whether employees are complying with security policies. It generates detailed reports, highlighting any deviations from established policies. These reports help security teams identify areas of improvement and reinforce policy adherence.
- Automated Mitigation & Response
The WannaCry ransomware epidemic and the massive LastPass data breach both serve as painful reminders of the consequences of ignoring or procrastinating when it comes to system updates. Yet, 26% of people [2] surveyed by the National Cybersecurity Alliance state they ‘never’, ‘rarely’, or simply don’t have the know-how to update their systems.
CCM tools can monitor and enforce policies related to timely software updates and patches. Any devices found to be non-compliant can be flagged, ensuring that security vulnerabilities are promptly addressed and reducing the attack surface.
The human element is indispensable in cybersecurity. People are the architects, enforcers, and responders in the battle against cyber threats. Continuous controls monitoring empowers the human element by providing real-time insights and automated enforcement of security policies. Through CCM, organizations can reduce their attack surface, strengthen security measures, and foster a culture of proactive security awareness among their employees. It’s a symbiotic relationship—technology and human expertise working together to protect our digital world.
*** This is a Security Bloggers Network syndicated blog from Noetic: Cyber Asset Attack Surface & Controls Management authored by Alexandra Aguiar. Read the original post at: https://noeticcyber.com/human-element-in-cybersecurity/

