Our progression into the digital age has notably changed the way we function. Everything from financial management, online purchases, virtual education, to entertainment—has been compacted into the easily-navigatable universe of apps on our handheld devices. This amplified reliance on mobile software is unavoidable, and consequently, it has led to a sharp surge in security threats, heralding an essential focal point - Augmenting the Robustness of Mobile App Security Measures.
In the realm of digital fortification, boosting the robustness of mobile app security implies the designed assembly of preventative barriers established to secure mobile interfaces from harmful components like rogue software, unsanctioned data alteration, and digital mishaps. It represents a meticulously designed series of tactics, creative strategies, and modernised protections to predict potential weak points and protect the structural integrity of mobile software systems.
<code class="language-python">class MobileAppDefender:
def launch_protection(self, threat):
# Implement security measures against the threat
pass</code>
The above Python code snippet describes a 'MobileAppDefender' class, a blueprint initiating a protective approach against an identified threat.
The perspective of amplifying the robustness of mobile app security isn't just about strengthening the shield of the app. It extends to securing the data it processes and retains. Here, we refer to aspects including, but not limited to, user sign-in details, transaction data, and other critical information, whose disclosure could trigger considerable chaos.
| Augmenting Mobile App Security Measures | Meaning |
|---|---|
| App Fortification | Pre-meditated steps to enhance the app |
| Personal Information Armor | Ensuring the safety of user's data and transaction history |
| Halting Data Intrusion | Techniques to obstruct unwanted data interference |
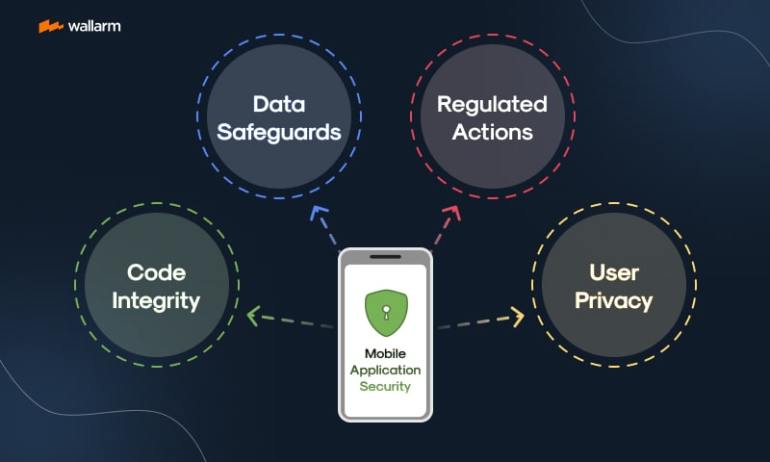
The plan to increase Mobile App Security Measures is multi-dimensional and encapsulate several pivotal points:

- Code Integrity: Assuring the trustworthiness of the base script of the mobile app to defend it from hidden security flaws.
- Data Safeguards: Shielding against unauthorised entry and tampering of the application's datastore.
- Regulated Actions: Guarantees of secure operations within the platform, crucial for apps dealing with transactions.
- User Privacy: Devotion to protect user data in a bid to respect user's confidentiality.
To wrap up, bolstering the robustness of mobile app security is critical in the expansive landscape of app design and management. It is an ongoing exercise that requires constant commitment and periodic updates to protect against evolving security threats. As we lean more towards digital ease, the demand for high-powered mobile app security measures will only surge.
Chapter 2: Grasping the Importance of Safeguarding Mobile Apps
In the contemporary digital age, smartphone apps have morphed into indispensable tools for our everyday tasks. Be it conducting banking operations, engaging in social interactions, e-shopping, or availing healthcare services, our dependence on these apps cannot be overstated. This reality, while facilitating convenience, also ushers in substantial security hazards, thereby mandating the necessity for robust mechanisms of Mobile App Safety.
In essence, Mobile App Safety constitutes the implementation of protective strategies designed to shield mobile apps from potential cyber threats and weaknesses. It comprises safeguarding the app's code, user data, and networking links which compose the application. There are manifold reasons underscoring the importance of Mobile App Safety.
Guarding Private and Confidential Information:
Smartphone apps frequently seek permission to access confidential data like credit card specifics, personal ID details, and health reports. Any security lapse in these apps could expose the data to cybercriminals.
Consider a basic code sample that illustrates the alarming possibility of sensitive data storage in an insecure format:
<code class="language-java">public class UserInformation {
private String cardNumber;
private String SSN;
public UserInformation(String cardNumber, String SSN) {
this.cardNumber = cardNumber;
this.SSN = SSN;
}
}</code>
In the aforementioned instance, delicate data is stored in an unguarded format, thus, exposed to cyberattacks. Conversely, a safe application would encrypt this data, as demonstrated below:
<code class="language-java">public class UserInformation {
private String cardNumber;
private String SSN;
public UserInformation(String cardNumber, String SSN) {
this.cardNumber = protectData(cardNumber);
this.SSN = protectData(SSN);
}
private String protectData(String info) {
// Include encryption code here
}
}</code>
Building and Retaining User Confidence:
App users entrust their personal data to the app, operating under the assumption their data will be securely managed. Any breach can erode the users' faith, negatively impacting the app's reputation and success.
Adhering to Legally and Regulatory Mandates:
Certain sectors like finance and healthcare are bound by stringent data security rules. As a result, mobile apps that handle sensitive user data in these sectors must adhere to these regulations, making Mobile App Safety a legal compulsion.
Thwarting monetary damages:
Incidents of security breaches can cause enormous financial losses. This may occur due to financial data theft, associated costs of resolution, or fines relating to non-compliance with rules.
Let's illustrate the importance of Mobile App Safety by contrasting two hypothetical mobile apps:
| App X (Safe) | App Y (Risk-prone) | |
|---|---|---|
| Data Protection | Employs encryption and secure protocols for user data protection. | Saves user data in an unsecured format. |
| User Trust | Optimal, as a result of secure practices. | Low, due to implied security threats. |
| Regulatory Compliance | Abides by industry regulations. | Non-adherent, inviting penalties. |
| Financial Impact | Lesser risk of financial damage owing to security breaches. | High risk of financial loss due to potential breaches. |
In summation, Mobile App Safety extends beyond mere data protection; it involves winning user confidence, conforming to regulations, and averting financial damage. As mobile app usage continues to surge, so does the relevance of Mobile App Safety. Delving into Mobile Apps Security Weaknesses
Mobile apps, now deeply intertwined with our daily routines, ranging from financial transactions to social interactions, entertainment and more, are not without their security flaws. In turn, these flaws are potentially exploitable by cyber criminals. This present exposition brings to light the multitude of safety flaws in these mobile applications.
Inadequate Safeguards for Data
Among the more pervasive safety flaws is inadequately safeguarded data. Sensitive credentials such as login details, transaction records and personal data are typically stored by mobile apps. If this information isn't adequately safeguarded, it becomes a vulnerable target for ill-intentioned individuals.
For example, consider this piece of code:
<code>SharedPref sharedPref = retrieveSharedPref("clientInfo", Context.CONTEXT_IGNORE_SECURITY); SharedPref.Editor editor = sharedPref.editor(); editor.saveString("username", "JohnDoe"); editor.saveString("password", "password123"); editor.commit();</code>
Within this example, plain text is used to store the client's login information; an easy score for anyone who gains access to the device.
Feeble Server-Side Defenses

Due to data computation and storage needs, mobile apps often affiliate with servers. However, if these server-side defenses are feeble, it can lead to unauthorized data infiltration.
For example, if the server doesn't adequately scrutinize incoming requests, it prone to manipulations by malicious users to access data.
Lackluster Data Transit Safety
Data requires robust protection when transmitted over a network to prevent unauthorized interception. Yet, a number of mobile applications fail to uphold this resulting in data being transmitted without encryption.
Here's an example:
<code>URL url = new URL("http://www.samplewebsite.com/"); HttpURLConnect conn = (HttpURLConnect) url.connectTo(); conn.setBinaryStream(true); conn.useMethod("POST");</code>
In the given case, data is sent via HTTP, which is not a secure protocol. This makes it it susceptible to interceptions during data transit.
Accidental Data Exposure
Unintended data exposure is commonly seen with mobile apps due to factors like tracing, caching and background operations. This inadvertently released information is a potential goldmine for attackers who can exploit it for useful insights about the user.
Inefficient User Validation and Access Control
An assortment of mobile applications falters at setting up foolproof user identification and access authorization. This lack of security can be manipulated by ill-intentioned users by gaining unwarranted access to private data.
To sum up, comprehending the varied security flaws riddling mobile apps is the first stride towards fortifying them. By acknowledging these flaws, developers can ideate and implement fitting safety maneuvers to shield the apps and their data. Lets take a look at some ways to enhance mobile app security in the succeeding chapter.Chapter Title: Bolstering Security Measures for Mobile Software Infrastructure
The evolution of our digital age places significant importance on reinforcing security for mobile applications used by both private users and organizations. Our deepening dependence on mobile technologies necessitates devising dynamic plans to uphold application security. The goal is to construct a strategic plan that incorporates solid methods and suggestions to protect mobile software from looming threats.
`
`
Intensify Application Security through Comprehensive Validation & Authentication:
Enhancement of mobile software security can be obtained by strengthening the processes of affirmation and validation. This involves formulating complex passwords, leveraging biometric validation mechanisms, and implementing multi-level authentication processes.
<code class="language-java">// Java Example for Multi-Level Authentication
public class UltimateMultiLevelAuthentication {
public boolean authenticate(String username,
String password, String token) {
// Verify username and password
if (!confirmUser(username, password)) {
return false;
}
// Validate token
if (!confirmToken(token)) {
return false;
}
return true;
}
}</code>
Advocate for Robust Defense of Personal Information:
Mobile software often processes user-specific data, thus becoming an enticing target for cybercriminals. Hence, implementing effective data defense strategies like encryption of stored and circulated data is critical.
<code class="language-python"># Python demonstration: encryption using AES from Crypto.Cipher import AES cipher_instance = AES.new(secret_key, AES.MODE_ECB) ciphertext = cipher_instance.encrypt(plain_text)</code>
Commit to Periodic Improvements and Maintenance:
Routine software updates, accompanied by scheduled maintenance tasks, play a crucial role in bolstering the robustness of mobile applications. They include enhancing existing defense systems and rectifying identified vulnerabilities.
Adhere to Exemplary Coding Standards:
Maintaining high-caliber coding standards can help mitigate risks associated with mobile software. This includes efficient validation of input/output data and apt management of exceptions and errors.
<code class="language-javascript">// JavaScript: Validating user input
function examineUserInput(input) {
const permitted_input_pattern = /^[a-zA-Z0-9]*$/;
if (!permitted_input_pattern.test(input)) {
throw new Error('Invalid input received');
}
}</code>
Emphasize Network-Based Security:
Crafting a comprehensive network-based security strategy aids in shielding mobile software from threats like data leakage. Enhanced networking protocols such as HTTPS and SSL/TLS can support this cause.
<code class="language-csharp">// C# demonstration: Implementing HTTPS HttpClient secureClient = new HttpClient(); secureClient.BaseAddress = new Uri ("https://exampleSite.com");</code>
Implement Routine Security Evaluations:
Frequent security audits are vital for identifying and rectifying potential vulnerabilities in mobile software. These may include activities like white-hat hacking, vulnerability assessments, and in-depth code analysis.
Recognize the Value of Mobile Software Protection Frameworks:
Customized protection frameworks can enhance the security of your mobile software. They provide an assemblage of tools and top-notch defense scripts, aiding developers in constructing secure applications. OWASP's Mobile Security Project, Android's Security Improvements, and iOS's Security Framework are worth considering.
Boosting the security reliability of mobile software necessitates a strategic amalgamation of sturdy validation procedures, secure data defense mechanisms, continuous software adjustments, stringent coding standards, network-focused security plans, regular security audits, and proficient utilization of protection frameworks. By adhering to this blueprint, both corporations and personal users can substantially enhance the overall security of their mobile software, drastically reducing the likelihood of security breaches.Chapter: Case Studies on Mobile Application Security Breaches
Mobile applications have become an integral part of our daily lives, but with this increased usage comes an elevated risk of security breaches. This chapter will delve into some real-world case studies of mobile application security breaches, providing a comprehensive understanding of the vulnerabilities and potential consequences.
Snapchat: The Snappening
In 2014, Snapchat, a popular photo-sharing app, fell victim to a massive security breach known as "The Snappening". Hackers exploited a vulnerability in the app's API, allowing them to access and leak around 200,000 private photos and videos.
<code class="language-python"># Hypothetical code snippet showing the API vulnerability
def get_snap(user_id):
# No authentication check
return database.get('snaps', 'user_id')</code>
This breach highlighted the importance of securing APIs and ensuring proper authentication checks are in place.
Uber: Unauthorized Access
In 2016, Uber experienced a significant security breach where hackers gained unauthorized access to the personal information of 57 million users and drivers. The breach occurred due to a flaw in Uber's third-party cloud-based service, where login credentials were mistakenly left in a GitHub repository accessible to the public.
<code class="language-javascript">// Hypothetical code snippet showing the exposed credentials
const AWS = require('aws-sdk');
AWS.config.update({
accessKeyId: 'AKIAIOSFODNN7EXAMPLE',
secretAccessKey: 'wJalrXUtnFEMI/K7MDEN
G/bPxRfiCYEXAMPLEKEY',
});</code>
This case underscores the importance of secure credential management and the risks associated with third-party services.
Facebook: Cambridge Analytica Scandal
In 2018, Facebook was embroiled in a scandal when it was revealed that data analytics firm Cambridge Analytica had harvested the personal data of millions of Facebook users without their consent. The breach was made possible due to a loophole in Facebook's app permissions, allowing third-party apps to access not just a user's data, but also the data of their friends.
<code class="language-javascript">// Hypothetical code snippet showing the app
permissions loophole
FB.login(function(response) {
// handle the response
}, {scope: 'user_friends'});</code>
This case study emphasizes the need for stringent app permission policies and user data protection.
Comparison Table: Key Takeaways from the Case Studies
| Case Study | Vulnerability | Key Takeaway |
|---|---|---|
| Snapchat | API Security | Secure APIs and ensure proper authentication |
| Uber | Credential Management | Securely manage credentials and be cautious with third-party services |
| App Permissions | Implement stringent app permission policies and protect user data |
These case studies serve as a stark reminder of the potential vulnerabilities in mobile application security and the importance of implementing robust security measures. They also underscore the need for continuous monitoring and updating of security protocols to safeguard against evolving threats.Chapter: Exploring Modern Progressions in Smartphone Application Safeguarding
With the electronic sphere ameliorating unceasingly, the significance of smartphone application safeguarding is being amplified. The present-day progressions in this domain mirror the escalating cyberspace menace silhouette and imaginative countermeasures birthed to counter these hazards. This chapter aims to elucidate these progressions, offering a fraction of enlightenment about the contemporary scenario of application security in smartphones and what might be the outlook.
Escalation in the Adoption of Synthetic Intellect and Autodidactic Equipments
In the field of smartphone application safeguarding, the pervasion of Synthetic Intellect (SI) and Autodidactic Equipments (AE) is blooming. These advancements are being employed to prophesy and pinpoint plausible security hazards proactively. To illustrate, SI can scrutinize trends in user conduct to discern deviations signifying a possible security compromise.
<code class="language-python"># Code snippet demonstrating SI application in smartphone security from sklearn.ensemble import IsolationForest model = IsolationForest(contamination=0.012) model.fit(user_activity_dataset) forecasts = model.predict(fresh_activity_dataset)</code>
Biometric Verification
Biometric verification, which calls for the utilization of unique biological attributes like fingerprints or facial recognition to authenticate a user's credibility, is steadily gaining popularity. It scores over traditional password systems as it is more challenging to duplicate or filch biometric details.
Security in Build
Incorporating security steps precisely during the creation process rather than appending them afterward — known as security in build — is a forward-looking approach to smartphone application safeguarding. Its popularity is growing due to its enhanced efficacy in averting security breaches.
Distributed Ledger Mechanism
Enhancing the security of smartphone applications is also seeing the contribution of distributed ledger mechanisms or blockchains. It's decentralized features render it cumbersome for cyber attackers to meddle with data. Alongside, blockchains' openness allows effortless detection and track down of unsanctioned alterations.
Elevated Attention towards Confidentiality
Emergence of regulations such as the General Data Protection Regulation (GDPR) spotlight the importance of privacy in smartphone app safety. The present trends show apps being constructed with an increased emphasis on privacy, such as implementing end-to-end encryption as a norm.
Advent of 5G
The dawn of 5G technology could significantly influence smartphone application security. Despite offering unprecedented speed with negligible latency, it also ushers in an array of security conundrums. Specifically, the surge in the multitude of linked gadgets could offer a broader canvas for cyber infiltrators.
Distinction Table: Conventional vs. Contemporary Progressions in Smartphone Application Security
| Conventional Safeguarding Measures | Contemporary Progressions |
|---|---|
| Password-based verification | Biometric verification |
| After-the-fact security steps | Security in build |
| Centralized data hold | Distributed ledger mechanism |
| Restricted concern for privacy | Elevated attention towards confidentiality |
| 4G technology | Advent of 5G |
To conclude, the current-day progressions in smartphone application security signify a shift towards more pre-emptive and intricate safeguarding actions. As the whirligig of technology perseveres, these progressions will keep on molding the smartphone app security landscape.Transforming the Status Quo: The Journey of Mobile Applications' Protection
With the ceaseless march of the digital age, the cruciality for shoring up defenses for mobile applications against plausibly harmful forces is climbing higher up the priority list. As we augment our reliance on mobile apps for a myriad of services, amplified fortification of their safeguards is vital. Here, we traverse through potential advancements in the realm of mobile applications' safety, inspecting everything from emerging inclinations to possible roadblocks and delving into visionary protection schemes.
Emerging Safety Inclinations in Mobile Apps
Within the realm of mobile apps' safety, several groundbreaking inclinations could play a critical role. An inspection of these provides valuable insight:
- AI and ML Applications: These have the potential to revolutionize the safety protocols for mobile applications. With the ability to detect and neutralize digital threats immediately, AI and ML strengthen the defenses of mobile apps. For instance, AI can assess user activity to pinpoint irregular patterns, which could be an indication of a lurking threat.
<code class="language-python"># The role of AI in boosting application safety
import tensorflow as tf
from tensorflow import keras
# Utilize a pre-established model for examining
user behavior
model = keras.models.load_model(
'behavioral_analysis_model.h5')
# Predict possible threats based on user activity data
def calculate_risk(user_activity_data):
risk_value = model.predict(user_activity_data)
if risk_value > 0.5:
print("Potential risk detected!")
else:
print("No threat detected.")</code>
-
Capitalizing on Blockchain: Blockchain technology could be greatly instrumental in enhancing mobile application security. The distributed nature of blockchain promotes data reliability and combats unsanctioned entry.
-
Influx of 5G: The debut of 5G technology illuminates the possibilities of enhanced data transfer speeds and reduced lag time. Nevertheless, it also ushers in novel safety challenges that will need to be addressed. The defense systems of mobile applications will need to evolve continuously against looming threats related to 5G.
Looming Challengers in the Landscape of Mobile Apps Protection
The journey of safety evolution for mobile applications won't be smooth. Anticipated complexities may include:
-
Growing Sophistication of Digital Threats: As the techno-sphere expands, so does the complexity and finesse of digital risks. Mobile applications will constantly need to upscale their defenses to meet these advancing threats head-on.
-
Concerns Related to Privacy: With the escalating storage of personal data on mobile apps, anxiety over privacy is proliferating. Apps need to ensure that, besides being secure, they respect user privacy.
`
`
Innovative Approaches to Fortify Mobile Apps
Even amidst these stumbling blocks, there are many innovative methodologies in the offing to enhance the safety of mobile apps:
-
Incorporating security at the genesis: This innovative approach suggests the inclusion of safety measures right from the outset of the app's development, rather than attaching it as an afterthought. This may enable early identification and resolution of potential safety vulnerabilities.
-
Continual Surveillance and Renovation: Persistent monitoring and periodic updates of mobile applications can aid in swift detection and management of digital risks. Regular safety checks and incorporation of the latest safety patches should be prioritized.
<code class="language-python"># An overview of continuous monitoring in application safety
import os
import time
# Constant watch over the application for modifications
def monitor_app(app_directory):
initial_state = dict([(f, None) for f in os.listdir
(app_directory)])
while True:
time.sleep(10)
updated_state = dict([(f, None) for f in os.listdir
(app_directory)])
additions = [f for f in updated_state if f not in
initial_state]
removals = [f for f in initial_state if f not in
updated_state]
if additions: print("New Files Added: ", ", ".join
(additions))
if removals: print("Files Removed: ", ", ".join
(removals))
initial_state = updated_state</code>
In conclusion, the dawn of a new era for mobile application safety will be the consequence of a marriage of emerging trends, potential challenges, and innovative strategies. As our dependence on mobile applications intensifies, the prominence of securing them will also grow.
如有侵权请联系:admin#unsafe.sh