In the dynamic world of container orchestration, Kubernetes (K8s) stands as a beacon of efficiency. However, the ease of managing and deploying applications comes with security challenges, particularly in access control. Role-Based Access Control (RBAC) alone is not enough to secure access to your K8s, especially when managing sensitive data or "secrets." The heart of the matter is, RBAC operates within a predefined scope of rules which, while useful, might not suffice in the face of evolving security threats and complex, dynamic Kubernetes environments. Moreover, the management of sensitive information, known as secrets, intertwines with RBAC, adding another layer of complexity to the security narrative. Let’s unravel why RBAC might not be enough to solve your Kubernetes access control challenges, and what you should be doing instead. Role-Based Access Control (RBAC) is a standard mechanism for managing who has access to the system’s resources and what actions they can perform. In Kubernetes, RBAC allows administrators to define roles with specific permissions like viewing, creating, or deleting resources, and assign these roles to users or groups. Typical configurations involve setting up roles and role bindings that tie users/groups to roles. However, common misconfigurations can occur, such as overly permissive roles, incorrect role bindings, or stale roles that remain in the system even after they are no longer needed. These misconfigurations can open up avenues for unauthorized access or actions within the Kubernetes environment, posing significant security risks. For instance, consider a scenario where an admin mistakenly binds a "delete" permission to a general user role, instead of a more restrictive admin role. This misconfiguration in role binding could potentially allow any general user to delete crucial resources within the Kubernetes environment, causing significant disruption or data loss. Secrets in Kubernetes serve as a means to store and manage sensitive information like passwords, tokens, and keys. Managing these secrets securely is paramount to ensuring the integrity and confidentiality of the system. RBAC plays a role in secrets management by controlling who can access or manage secrets. However, common misconfigurations like overly permissive access to secrets, or improperly secured secrets (e.g., storing secrets in plain text or version control systems), can lead to exposure of sensitive data. Furthermore, the intertwining of RBAC with secrets management can sometimes obscure the security landscape, making it challenging to ensure both robust access control and secure secrets management. As we delve deeper, we’ll unravel the intricacies of this interaction and how a more holistic approach can provide a robust solution to these challenges. Kubernetes provides a robust platform for orchestrating containerized applications, however, managing authorization, access, and secrets within K8s poses its own set of challenges. Here are three best practices to ensure a secure K8s environment. Advanced security solutions like Uptycs can also be used to map real-time threats to risky RBAC configurations, giving you end-to-end visibility of your Kubernetes environment and helping you remove any blind spots in your security posture. With Uptycs, you can gain insights into which users have access to what resources, as well as detect suspicious activity across all of your Kubernetes clusters in real time. In addition you can map real-time data plane threats with RBAC control plane misconfigurations. We then move to the 'RBAC Access Monitor' for this cluster, filtering by the compromised service account. It reveals excessive privileges across the cluster, including access to vulnerable pods, indicating a severe security risk. Uptycs showcases its strength in correlating real-time threats with RBAC misconfigurations, aiding in pinpointing and addressing security issues in Kubernetes. Navigating authorization, access, and secrets management in Kubernetes environments can often feel like a daunting task. RBAC provides a foundational layer of control, however, the dynamic and complex nature of K8s environments calls for a more comprehensive and proactive approach to security. Tools like Uptycs further simplify this journey by offering a unified platform equipped with the necessary capabilities to address the challenges head-on, ensuring a secure, compliant, and efficient K8s environment. As the landscape of cybersecurity continues to evolve, embracing a holistic approach to K8s security that extends beyond RBAC, and aligning with robust security solutions like Uptycs, will prove instrumental in staying ahead of threats and ensuring a resilient K8s ecosystem. Mastering Kubernetes Security Part 1: NSA Hardening Guide Mastering Kubernetes Security Part 2: Vulnerability Management Mastering Kubernetes Security Part 3: Runtime Admission ControlsRBAC in Kubernetes
Secrets management in Kubernetes
Managing authorization, access, and secrets in Kubernetes
Role-Based Access Control (RBAC) is a key pillar to Kubernetes security. RBAC allows you to assign roles and permissions to users, ensuring that only those with the correct access can view or modify data. By using RBAC, you can ensure that only authorized users are able to access sensitive data and resources, helping to protect your system from malicious actors.
This will allow you to identify any potential risks in your system and take steps to secure them before they are exploited by malicious actors. Additionally, monitoring permissions on an ongoing basis will help you quickly identify any changes in user access that could indicate a potential breach or other security issue. This is especially important when onboarding new applications and monitoring default service accounts that may have access to all permissions by default, even if assigned a specific role binding.
Advanced security solutions like Uptycs can also be used to map real-time threats to risky RBAC configurations, giving you end-to-end visibility of your Kubernetes environment and helping you remove any blind spots in your security posture. With Uptycs, you can gain insights into which users have access to what resources, as well as detect suspicious activity across all of your Kubernetes clusters in real time.Let's walk through an example:
First, in the Uptycs UI, under 'Detections', an alert highlights insecure Kubernetes kubectl access from a compromised pod. This can be risky because kubectl should typically be performed outside the cluster using a secure kubeconfig. If the kubeconfig inside the cluster is accessed it could lead to more unauthorized access to nodes, secrets, namespaces, and more.
The threat is mapped to the MITRE ATT&CK Framework with details like the default service account used, pod's namespace, and source IP. Navigating to the detection graph, we see the service account attempted a deployment. 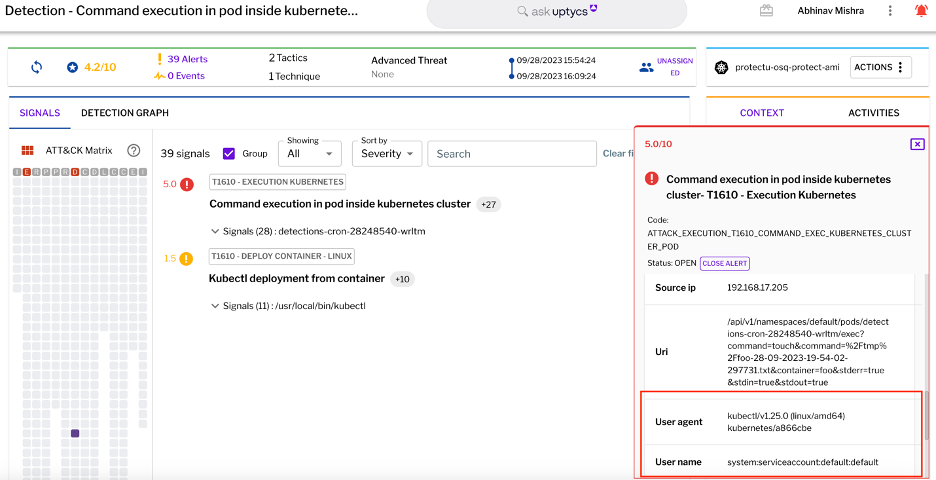 Figure 1 - Detection of insecure Kubernetes kubectl access in Uptycs
Figure 1 - Detection of insecure Kubernetes kubectl access in Uptycs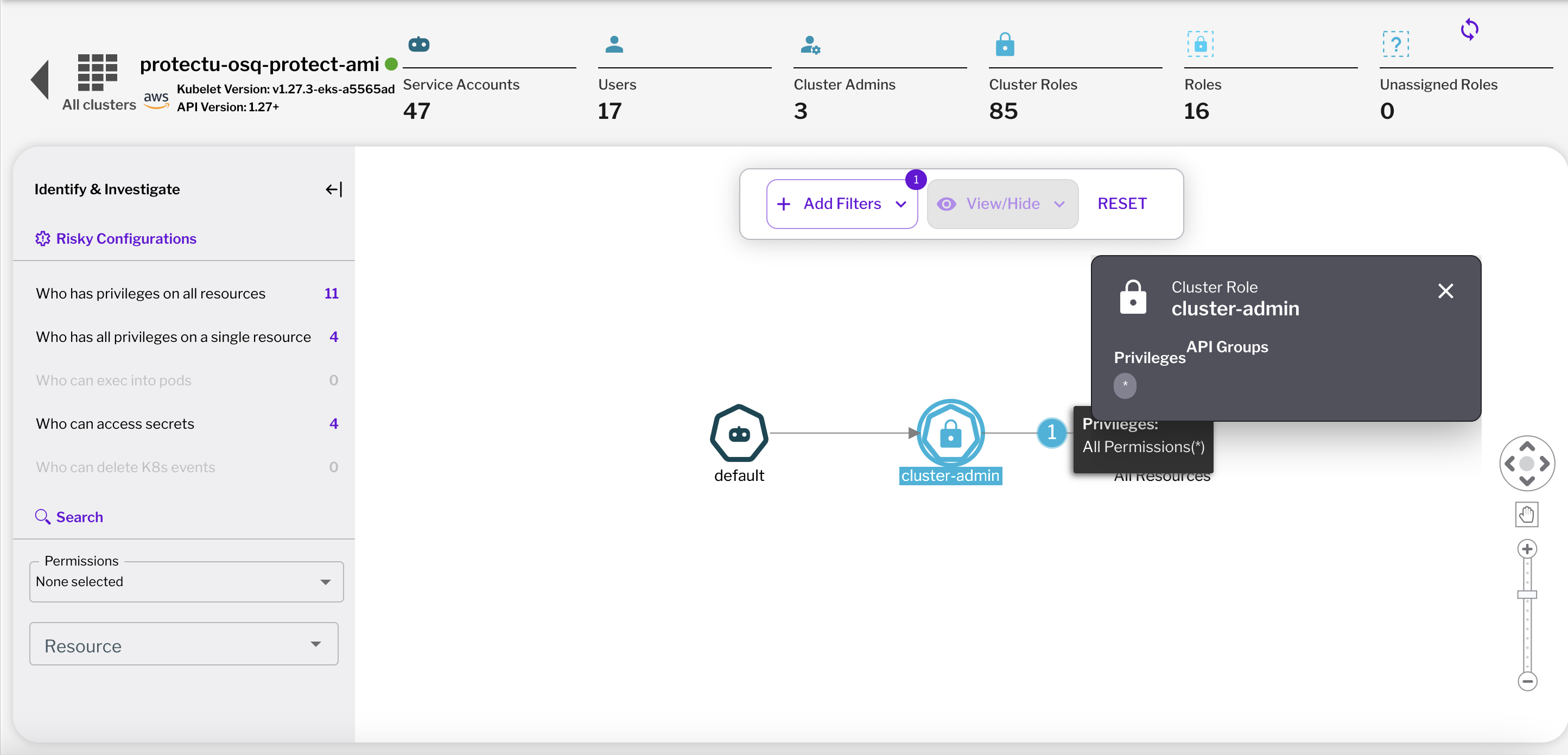 Figure 2 - Excessive privileges revealed in Uptycs’ RBAC Access Monitor
Figure 2 - Excessive privileges revealed in Uptycs’ RBAC Access MonitorConclusion
More from this series
Authorization, Access & Secrets: Mastering Kubernetes Security Part 4
2023-10-26 20:0:0 Author: www.uptycs.com(查看原文) 阅读量:19 收藏
2023-10-26 20:0:0 Author: www.uptycs.com(查看原文) 阅读量:19 收藏
文章来源: https://www.uptycs.com/blog/kubernetes-rbac-role-based-access-control
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh