The prolific threat actor known as Scattered Spider has been observed impersonating newly hired employees in targeted firms as a ploy to blend into normal on-hire processes and takeover accounts and breach organizations across the world.
Microsoft, which disclosed the activities of the financially motivated hacking crew, described the adversary as "one of the most dangerous financial criminal groups," calling out its operational fluidity and its ability to incorporate SMS phishing, SIM swapping, and help desk fraud into its attack model.
"Octo Tempest is a financially motivated collective of native English-speaking threat actors known for launching wide-ranging campaigns that prominently feature adversary-in-the-middle (AiTM) techniques, social engineering, and SIM swapping capabilities," the company said.
It's worth noting that the activity represented by Octo Tempest is tracked by other cybersecurity companies under various monikers, including 0ktapus, Scatter Swine, and UNC3944, which has repeatedly singled out Okta to obtain elevated permissions and infiltrate targeted networks.
One of the key hallmarks is the targeting of support and help desk personnel via social engineering attacks to gain initial access to privileged accounts, tricking them into performing a reset of the victim's password and multi-factor authentication (MFA) methods.
Other approaches entail purchasing an employee's credentials and/or session token(s) on a criminal underground market, or calling the individual directly and socially engineering the user to either install a Remote Monitoring and Management (RMM) utility, visit a fake login portal using an AiTM phishing toolkit, or remove their FIDO2 token.
Initial attacks mounted by the group targeted mobile telecommunication providers and business process outsourcing (BPO) organizations to initiate SIM swaps, before graduating to monetizing the access for selling SIM swaps to other criminals and performing account takeovers of high-net-worth individuals for cryptocurrency theft.
Octo Tempest has since diversified its targeting to include email and tech service providers, gaming, hospitality, retail, managed service providers (MSPs), manufacturing, technology, and financial sectors, while simultaneously emerging as an affiliate for the BlackCat ransomware gang in mid-2023 to extort victims.
Put differently, the end goal of the attacks vary between cryptocurrency theft and data exfiltration for extortion and ransomware deployment.
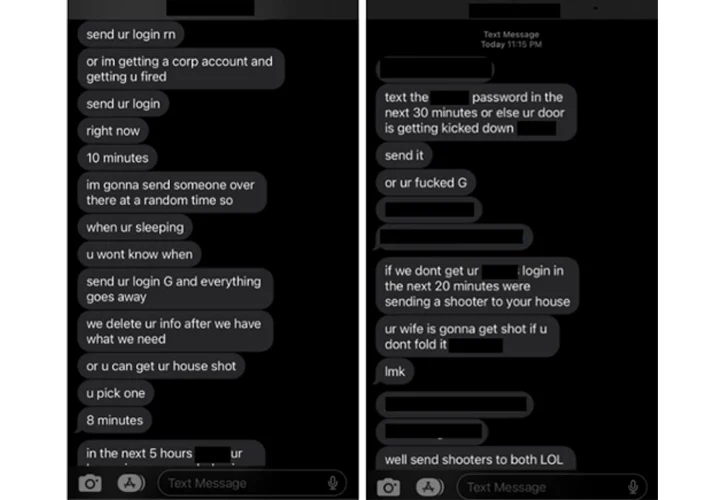
"In late 2022 to early 2023, [...] Octo Tempest started monetizing intrusions by extorting victim organizations for data stolen during their intrusion operations and in some cases even resorting to physical threats," Microsoft said.
"In rare instances, Octo Tempest resorts to fear-mongering tactics, targeting specific individuals through phone calls and texts. These actors use personal information, such as home addresses and family names, along with physical threats to coerce victims into sharing credentials for corporate access."
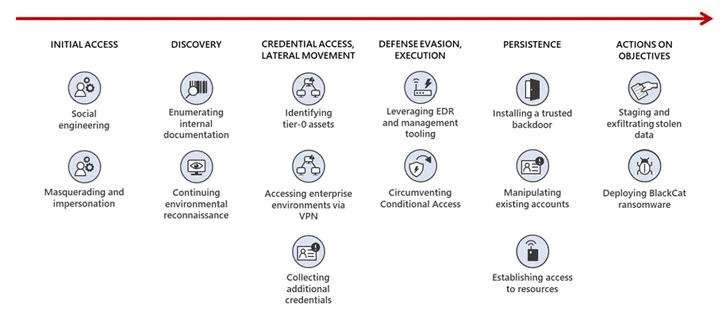
A successful foothold is followed by the attackers carrying out reconnaissance of the environment and privilege escalation, the latter of which is accomplished by means of stolen password policy procedures, bulk downloads of user, group, and role exports.
Another noteworthy tradecraft is use of compromised security personnel accounts within victim organizations to impair the functioning security products in an attempt to fly under the radar, in addition to tampering with the security staff mailbox rules to automatically delete emails from vendors.
The broad arsenal of tools and tactics employed by Octo Tempest, including enrolling actor-controlled devices into device management software to bypass controls and replaying harvested tokens with satisfied MFA claims to bypass MFA, is indicative of its extensive technical expertise and its ability to navigate complex hybrid environments, Redmond said.
"A unique technique Octo Tempest uses is compromising VMware ESXi infrastructure, installing the open-source Linux backdoor Bedevil, and then launching VMware Python scripts to run arbitrary commands against housed virtual machines," the company further explained.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.